UMTS Network Level Security Investigation on Security Improvements



















- Slides: 33

UMTS Network Level Security; Investigation on Security Improvements Thesis Author: Yue Feng Supervisor: Professor Sven-Gustav Häggman Instructor: Lic. Tech Michael Hall

Dedicate this thesis to my parents, Diwei Feng and Shuhua Yang for being the best parents can be 2

Presentation outline n n n n Background Thesis objectives Thesis scope Network level security of mobile systems Introduction to UMTS network level security Proposals for secuity impovements Conclusions 3

Background n n n 3 G era is coming, e. g. , UMTS Security is becoming more and more concerned for 3 G cellular systems, since they are wireless, much more complex than 2 G cellular systems, and especially more sophisticated attacking means are available It is believed that attacks against mobile systems will not cease, as motives are as usual – for fun, criminality, Premium rate mobile services, unintentional attacks Network level security attacks can be mainly categoried into Do. S (location update spoofing, and radio jamming), masquerade, man -in-the-middle, replay, hijacking Network level security focuses on confidentiality, authentication, integrity protection, user and location confidentiality, and availability 4

Thesis objectives n n n To present GSM network level security features retained in UMTS To present UMTS network level security features in 3 GPP Release 1999, and MAPsec and IPsec based Network Domain Security (NDS) To present network level security features specific for UMTS, prior to GSM network level security features Proposals for mitigating unintentional radio jamming in uplink in UMTS – such proposals can not totally cancel such radio jamming Proposals for interoperation in terms of security between UMTS and cdma 2000 1 X roaming users 5

Thesis scope n n Focuses only on the UMTS network level security specified in 3 GPP Release 1999, and MAPsec and IPsec based Network Domain Security (NDS), i. e. , system level security and protocol level security Application security, operating system security, and physical facilities security are out of the scope 6

Network level security of mobile systems n In 400 B. C, ancient Greeks already mastered the encryption skill called as “skytals” n n A big leap during World War II Network level security of 1 G cellular systems was nothing Identities transfer over air cloning Ø No encryption interception Ø n Lesson was learned that security has to be desgined from the beginging phase of the design of the whole system, for what ? 7

GSM network level security 1 n GSM network level security features: Ø Subscriber identity and location confidentiality Ø Subscriber identity authentication Ø n n Signalling data and user data confidentiality Security features are realized by security mechanisms GSM network level security mechanisms: Ø Subscriber identity and location confidentiality mechanism Ø GSM Authentication and Key Agreement (AKA) mechanism Ø GSM signalling data and user data confidentiality mechanism 8

GSM network level security 2 n GSM network level security relies on: International Mobile Subscriber Identity (IMSI) Temporary Mobile Subscriber Identity (TMSI); note in exceptional cases GSM subscriber can be only identified by IMSI transferred over the air interface Ø Subscriber Authentication Key Ki (128 bits) only secured in Subscriber Identity Module (SIM) and Authentication Center (Au. C) Ø COMP-128 based Authentication Algorithm A 3 and Ciphering Key Generating Algorithm A 8 only secured in SIM and Au. C; RES(32 bits)=A 3 Ki(RAND); Kc(64 bits)=A 8 Ki(RAND) Ø Stream cipher based Ciphering Algorithm A 5 secured in all Mobile Equipments (MEs) and Base Station Transceivers (BTSs); Ciphering. Stream(114 bits)=A 5(Kc, Frame Number); note ME is the terminal part of Mobile Station (MS)! Ø n Authentication of a user implies authenticating the right knowledge of Subscriber Authentication Key 9

Weaknesses of GSM network level security 1 n Weaknesses of GSM Network Level Security Threats against GSM network level security cf. Section 2. 3. 3 Ø Ø Ø Ø Unilateral authentication of MS towards network can cause for active attacks from a false BTS An Authenticaion Vector (AV) may be indefinately used Encryption is provided between the MS and the BTS, but not further into the network GSM only provides access security but not Network Domain Security (NDS) and security data is transmitted in plain text between mobile networks No cryptographic integrity protection provided leaves a door for man-in-themiddle and hijacking attacks; note Cyclic Reduncy Checking (CRC) is not the cryptographic integrity protection Therefore, protection against the man-in-the-middle and hijacking attacks can partialy rely on the encryption; unfortunately GSM encryption can be disabled To be continued 10

Weaknesses of GSM network level security 2 Cryptographic algorithms are lack of confidence 64 -bit Ciphering Key (Kc) is short; COMP 128 base A 3/A 8 algorithms are poor (published on Internet in 1998 by Briceno and Goldberg); Ciphering Algorithm A 5/2 is the deliberately weakened version of Ciphering Algorithm A 5/1 for export control regulations; Biryukov, Shamir, and Wagner demonstrated how A 5/1 could be cracked less than one second on a Personal Computer (PC) Ø Interfaces of law enforcement was not included in the design of GSM could be only considered as an afterthought Ø 11

cdma 2000 1 X network level security 1 n n n For the later proposals for interoperation in terms of security between UMTS and cdma 2000 1 X roaming users Two-level network level security hierachy: wireless network security and RADIUS/AAA Wireless network security includes cdma 2000 1 X RAN Authentication Mechanisms: Initial registration mechanism (Global challenge authentication) Ø SSD update mechanism (when SSD is shared) is a mutual authentication mechansim Ø n n n Wireless network security also includes cdma 2000 1 X user identity and location confidentiality mechanism and cdma 2000 1 X signalling data and user data confidentiality mechanism cf. Section 2. 4. 1 and Section 2. 4. 2. 2 in thesis RADIUS/AAA authenticates user access to Packet Switched (PS) services by Challenge Handshake Authentication Protocol (CHAP), after a successful cdma 2000 1 X RAN Authentication procedure; it is not the interest in thesis To be continued 12

cdma 2000 1 X network level security 2 n cdma 2000 1 X RAN Authentication Mechanisms rely on: Ø Ø Ø User Authentication Key A-Key (64 bits) and Electronic Serial Number (ESN 32 bits) only secured in Mobile Terminal (MT) and Authentication Center (AC) Algorithm Cellular Authentication and Voice Encryption (CAVE) Shared Secret Data (SSD 128 bits) is the cornerstone of cdma 2000 1 X wireless network security; SSD(128 bits)=CAVE(A-Key, ESN, RANDSSD) SSD(128 bits) Temporary User Authentication Key (SSD-A 64 bits), i. e. , the first 64 -bit part; SSD-A is for the initial registration mechanism and SSD update mechanism – more precisely unique challenge authentication of SSD update mechanism since the SSD update procedure is a mutual authentication procedure Moreover, SSD(128 bits) Temporary User Confidentiality Key (SSD-B 64 bits), i. e. , the second 64 -bit part; SSD-B can generate ciphering keys for signalling data and user data confidentiality mechanisms, cf. Section 2. 4. 2. 2 in thesis 13

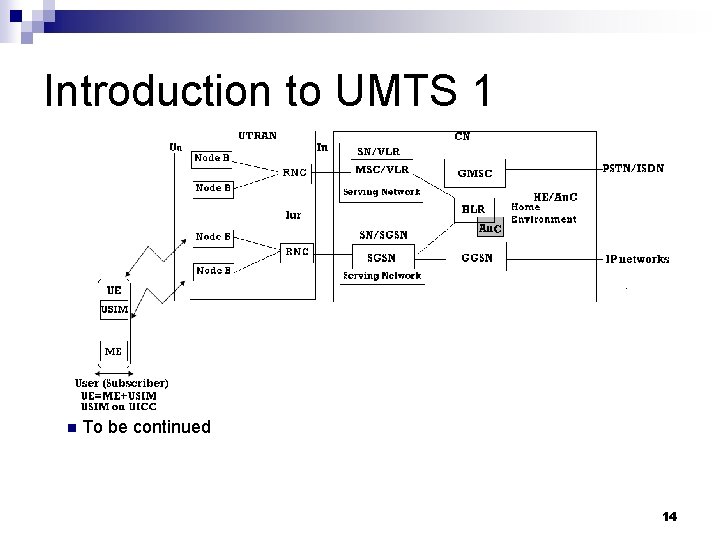
Introduction to UMTS 1 n To be continued 14

Introduction to UMTS 2 n n UMTS employs Wideband Code Division Multiple Access (WCDMA) as the radio access technology with 5 MHz channel bandwidth, i. e. , a DS-CDMA technology, and hence many say WCDMA instead of UMTS, although it is only a radio access technology Channel types defined in WCDMA/UMTS are: Logical channels answer what type of data to be transferred Transport channels answer how and with which characteristics with the transferred data Ø Physical channels answer exact the physical characteristics of the radio channels Ø Ø n UMTS Terrestrial Radio Access Network (UTRAN) protocol can be further divided into three layers: physical layer, link layer, and network layer Medium Access Control (MAC) sublayer belongs to the link layer, which coverts the logical channels to the transport channels Ø To be continued Ø 15

Introduction to UMTS 3 Radio Link Control (RLC) sublayer belongs to the link layer, which provides services to upper layers Ø Radio Resource Control (RRC) sublayer is the lowest sublayer of the network layer and terminates in Radio Network Controller (RNC); it provides encryption control; it performs integrity protection of both the RRC-level signalling and higher layers signalling Ø 16

UMTS network level security n 3 G security principle defined in 3 GPP TS 33. 210: 3 G security is built on the security of 2 G systems; security elements within GSM and other 2 G systems which have proved to be needed and robust shall be adopted for the 3 G security Ø 3 G security improves the security of 2 G systems by correcting the real and perceived weaknesses Ø New 3 G security features are defined as necessary to secure the new services offered by 3 G Ø n n n Requirements capture of UMTS network level security is based on the weaknesses analysis pp 9 -10 and threat analysis cf. Section 2. 3. 3 in thesis UMTS retains certain network level security features from the 2 G systems In the following part, network access security (3 GPP Release 1999) will be addressed; MAPsec (3 GPP Release 4) and IPsec (3 GPP Release 5) based Network Domain Security (NDS) will be addressed 17

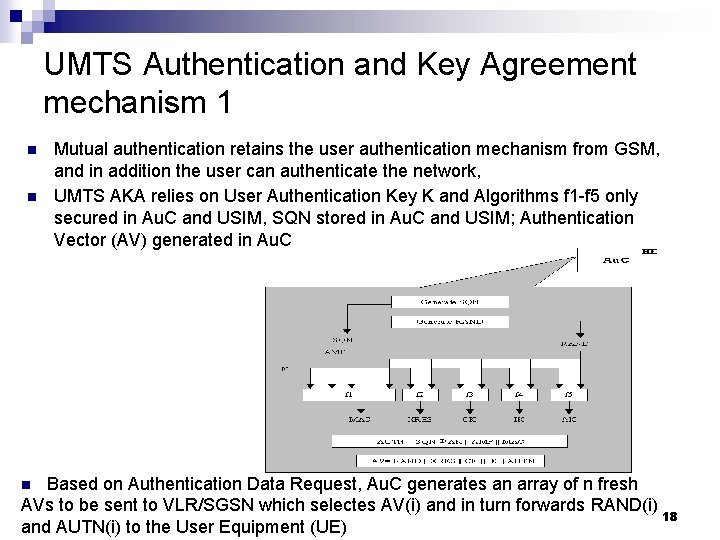
UMTS Authentication and Key Agreement mechanism 1 n n Mutual authentication retains the user authentication mechanism from GSM, and in addition the user can authenticate the network, UMTS AKA relies on User Authentication Key K and Algorithms f 1 -f 5 only secured in Au. C and USIM, SQN stored in Au. C and USIM; Authentication Vector (AV) generated in Au. C Based on Authentication Data Request, Au. C generates an array of n fresh AVs to be sent to VLR/SGSN which selectes AV(i) and in turn forwards RAND(i) 18 and AUTN(i) to the User Equipment (UE) n

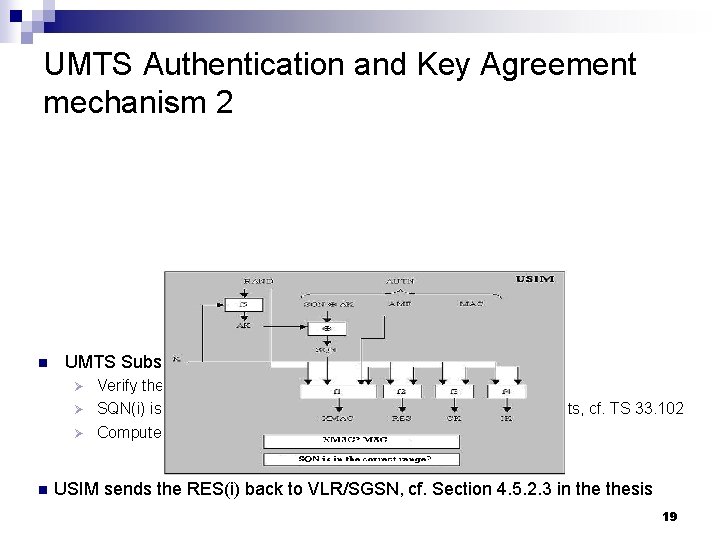
UMTS Authentication and Key Agreement mechanism 2 n UMTS Subscriber Identity Module (USIM) embeded in UE can Verify the received AUTN(i) – XMAC(i) ? = MAC(i) Ø SQN(i) is in correct range? If not, resynchronization procedure starts, cf. TS 33. 102 Ø Compute RES(i), and establish CK(i), and IK(i) Ø n USIM sends the RES(i) back to VLR/SGSN, cf. Section 4. 5. 2. 3 in thesis 19

UMTS user identity and location confidentiality mechanism n International Mobile Subscriber Identity (IMSI) Temporary Mobile Subscriber Identity (TMSI) for services provided by Circuit Switched (CS) domain; IMSI Packet TMSI (P-TMSI) for services provided by Packet Switched (PS) domain; note in exceptional cases UMTS user can be only identified by IMSI over the air interface n n n UMTS user may also be identified by Radio Network Temporary Identity (RNTI) IMSI, TMSI, and P-TMSI are CN-level identities for the UE in idle mode – such as power up, authentication RNTI is UTRAN-level identity for the UE in connected mode such as UTRAN integrity protection 20

UTRAN encryption mechanism n n n n Using Cipheing Algorithm f 8, a stream cipher based on a block cipher KASUMI; publicly evaluated Under the control of the Ciphering Key CK (128 bits) established during the AKA procedure MAC sublayer performs the encryption in transparent RLC mode – in case of Circuit Switched (CS) services RLC sublayer performs encryption in both acknowledged mode and unacknowledged mode Different from the GSM encryption, UTRAN encryption protects the communications between a ME and the RNC UTRAN encryption procedure is optional UTRAN encryption procedure is initiated by security mode setup procedure cf. Section 4. 5. 6. 3 in thesis 21

UTRAN integrity protection of RRC signalling n n n Threats against integrity is claimed to be most severe The purpose of the UTRAN integrity protection of Radio Resource Control (RRC) signalling, is to authenticate individual control messages. RRC sublayer executes the integrity protection of both RRC-level and higher layer signalling, by using Integrity Algorithm f 9 under the control of the Integrity Key IK (128 bits) established during the AKA procedure Similar to the Ciphering Algorithm f 8, the Integrity Algorithm f 9 is based on the block ciphering KASUMI; publicly evaluated Not all UTRAN signalling is integrity-protected Most of RRC signalling is integrity-protected; such UTRAN integrity protection does not apply for signalling before the Integrity Key IK is in place, e. g. , RRC Connection Request in the security mode setup procedure 22

UMTS Network Domain Security (NDS 1) n n SS 7 -based Network Domain Security (NDS) was not considered in GSM, since only a limitted number of well-established entities can access Situation is getting changed Telecommunication industry is getting deregulated Ø In case AVs and sensitive information are modified in the network domain or between networks of diffrent mobile operators, what a desaster! Ø IP-based network is the trend Ø n n MAP security (MAPsec) is introduced in 3 GPP Release 4, however why only Mobile Application Part (MAP) signalling is protected? IP security (IPsec) is introduced in 3 GPP Release 5. 23

MAPsec (NDS 2) n n n n n MAPsec has three modes, mode 0 – no protection, mode 1 – integrity protection only, mode 2 – encryption with integrity protection Borrows the notion of Security Association (SA) from IPsec for security keys and other relevant information 3 GPP Release 4 does not specify how to exchange SAs Automatic Key Management can be an option, which has the Key Administration Centre (KAC) as the basis All SAs are stored in a SAD and Network Elements (NEs) must access it All SAs are valid on a PLMN-level basis, as a PLMN can only address another PLMN not its individual NE Each KAC maintains a SA Database (SAD) and Security Policy Database (SPD); each NE has similar databases KACs agree on SAs between themselves by using the Internet Key Exchangement (IKE) and MAPsec Domain of Interpretation (Do. I) KAC distributes security policies and SAs to NEs over the Ze-interface A NE must get a valid SA and security policy to address a NE in anohter PLMN 24

IPsec (NDS 3) n n n IPsec is defined at the network layer to protect IP packets IPsec three components: Authentication Header (AH), Encapsulation Security Payload (ESP), and IKE; only the ESP is talked in detail ESP has two modes: transport mode and tunnel mode The former fits in better with end-to-end communications; provides both encryption and integrity protection; but only protects the payload Ø The latter fits in better between two nodes, e. g. , Gateways; provides both encryption and integrity protection; protects the whole IP packet; the implication of the same function as the former has; UMTS NDS prefers using the latter for signalling protection Ø n Security Gateway (SEG) is the basis of NDS IP-based network (NDS/IP) Each SEG contains both the SAD and SPD Ø SEG uses the IKE to exchage IPsec SAs Ø Main difference from the KAC is that SEG also uses the negotiated SAs, while KAC can only agree SAs over the Zd-interface Ø 25

Proposals for mitigating unintentional radio jamming in uplink 1 n Proposals for mitigating unintentional radio jamming in uplink Radio jamming is an ongoing threat to any cellular system and hardly to be totally canceled in practice Ø Unintentional radio jamming is met in civilian cellular systems, and may be caused by co-existing wireless systems – Personal Handyphone System (PHS), radar systems and broadcasting systems operating on Ultra High Frequency (UHF) Ø Radio jamming in uplink may be very severe, since the Base Station (BS) is visible, static, and open Ø Smart antenna is the big hope Review of results Ø GSM is relatively resistant to radio jamming thanks for its digital features Ø Power Control (PC) and rescue handover mechanisms can further ease radio jamming Ø WCDMA/UMTS has even better radio jamming resistance ability; more sophisticated PC and handover mechanisms are introduced Ø Moderate radio jamming can not make WCDMA/UMTS network deaf Ø n 26

Proposals for mitigating unintentional radio jamming in uplink 2 n n n In case of high radio jamming environments, Capital Expenditures (CAPEX) have been invested on countermeasures, otherwise Operating Expense (OPEX) would be critical for UMTS operators in long run Mitigating unintentional radio jamming in uplink shall set about Identifying radio jamming sources, analyzing radio jamming reasons, figuring out radio jamming characteristics, and evaluating radio jamming impacts before making further countermeasures; network trial is essential for optimizing countermeasures and for balancing against the costs Based on the above efforts, proposals for effectively mitigating unintentional radio jamming in uplink in UMTS are made: Ø In case of static jamming sources such as a power plant or a broadcasting system, switched beam smart antennas shall be adopted around the jamming area; network trial can help UMTS operator further select Butler matrix or Blass matrix; the latter performs better while being complex, heavy, and expensive; switched beam smart antenna may cause for intra-cell handover and call loss; in general some areas are more severely influenced than others. Therefore, cell splitting and more Node Bs shall be introduced, while in turn pushing up the costs Ø To be continued 27

Proposals for mitigating unintentional radio jamming in uplink 3 In case of dynamic radio jamming sources such as radar arrays, airport and harbor radio equipments, or co-existing systems in the same building or along highways, adaptive array smart antennas shall be adopted, since such smart antennas can dynamically track UEs and can simultaneously adjust beams to desired signals while nulling out radio jamming signals; Sample Matrix Inversion (SMI) DSP performs better especially in WCDMA/UMTS, since the SMI DSP can take advantage of pilot signal in uplink and the SMI algorithm has fast convergence rate, but the SMI DSP is complex and expensive; Least Mean Square (LMS) DSP is simple and cheap Ø In case of pervasive jamming environments of high power, unintentional radio jamming in uplink may be mitigated by means of implementing adaptive array smart antennas and minimizing cell size; UMTS operators shall adopt lines such as copper lines or optical fiber, other than radio, to be the backbone network transmission medium Ø In addition, UMTS operators shall adopt antennas with lower side lobes and use electrical down-tilt antennas Ø UMTS operators must cooperate with authorities or legal forces, which would be an easy way to prevent the occurrences of radio jamming, or to be compensated in case of radio jamming damage Ø 28

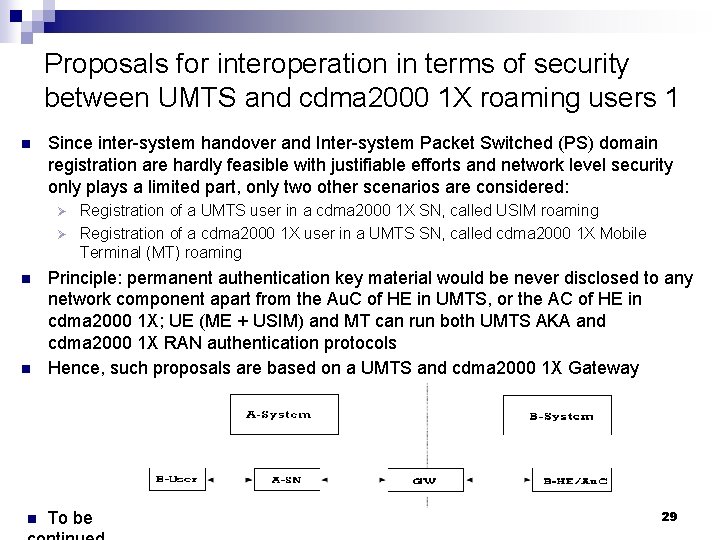
Proposals for interoperation in terms of security between UMTS and cdma 2000 1 X roaming users 1 n Since inter-system handover and Inter-system Packet Switched (PS) domain registration are hardly feasible with justifiable efforts and network level security only plays a limited part, only two other scenarios are considered: Registration of a UMTS user in a cdma 2000 1 X SN, called USIM roaming Ø Registration of a cdma 2000 1 X user in a UMTS SN, called cdma 2000 1 X Mobile Terminal (MT) roaming Ø n n n Principle: permanent authentication key material would be never disclosed to any network component apart from the Au. C of HE in UMTS, or the AC of HE in cdma 2000 1 X; UE (ME + USIM) and MT can run both UMTS AKA and cdma 2000 1 X RAN authentication protocols Hence, such proposals are based on a UMTS and cdma 2000 1 X Gateway To be 29

Proposals for interoperation in terms of security between UMTS and cdma 2000 1 X roaming users 2 n n n The necessary adaptation has to be mainly facilitated by the features on the user side and the Gateway In case B-user is roaming in A-SN, to A-SN the Gateway acts like the HE of A -SN, while to B-HE the Gateway acts like a B-SN Proposal for USIM roaming – relatively simple as no SQN is involved Gateway in addition acts as the HE of USIM Ø Gateway in a predefined way converts the received UMTS AKA authentication data for the purpose of a cdma 2000 1 X SSD update procedure with the UMTS user ( Set SSD=IK, RANDSSD=RAND). Ø Gateway runs cdma 2000 1 X SSD update procedure with the USIM via the cdma 2000 1 X SN Ø n Proposal for cdma 2000 1 X Mobile Terminal (MT) roaming Gateway in addition acts as the HE of cdma 2000 1 X MT Ø Gateway requests a cdma 2000 1 X SSD update procedure by abusing the message with especially reserved parameters to the cdma 2000 1 X AC of HE Ø Gateway in a predefined way converts the received cdma 2000 1 X authentication data to a UMTS AV (RAND=RANDSSD||RD, 0, 0) and set K=SSD Ø To be continued Ø 30

Proposals for interoperation in terms of security between UMTS and cdma 2000 1 X roaming users 3 Gateway authenticates the cdma 2000 1 X user by abusing Resynchronization procedure (0, AUTS) Ø Only from this point forward, Gateway generates a UMTS authentication quintuple (RAND, XRES, CK, IK, AUTN), by using Algorithms f 1 -f 5, under the control of SSD as the substitute for the UMTS User Authentication Key K Ø The new UMTS authentication quintuple is sent to UMTS SN for further security matters, e. g. , mutual authentication, integrity protection and so on Ø cdma 2000 1 X does not have SQN approach, hence a special manner has to be arranged, every time a cdma 2000 1 X MT attempts to register in UMTS, the SQN in both the cdma 2000 1 X MT and the Gateway are forced to 1; it is incremented by 1 for the generation of a new UMTS authentication quintuplet under the condition of same SSD Ø 31

Conclusions n n UMTS network level security addresses and corrects GSM network level securtiy real and perceived weaknesses UMTS has more robust network level security than cdma 2000 1 X UMTS network level security can be the pattern for the development of such security matters for future cellular systems Future work Ø Ø Ø Avoid IMSI transfer over the air interface Integrity-protect all types of signalling in network domain Is it possible to introduce public key mechanism for UMTS network level security Prevent a Base Station (BS)/handset from camping on a false handset/ Base Station (BS) Firewall shall be introduced to protect network domain 32

Thanks 33