UFCE 95 20 3 Information Systems in Society












- Slides: 18

UFCE 95 -20 -3: Information Systems in Society Lecture 8: Theorizing surveillance Reading: –Lyon, 2002, Everyday Surveillance: Personal data and social classifications

Surveillance theory • Totalitarianism – 1984, Brave New World – 20 th century fascist and communist states • Panopticism – “all-seeing place” – Social discipline through utilitarian social contract – Evidence in growth of workplace and data surveillance • The Surveillant Assemblage – – Realized as inevitable by-product of ICT diffusion “Rhizomic surveillance” - information trails and traces Non-heirarchical and problematic for rulers and ruled Evidence in ‘disappearing body’, growth of computer use and ‘function creep’.

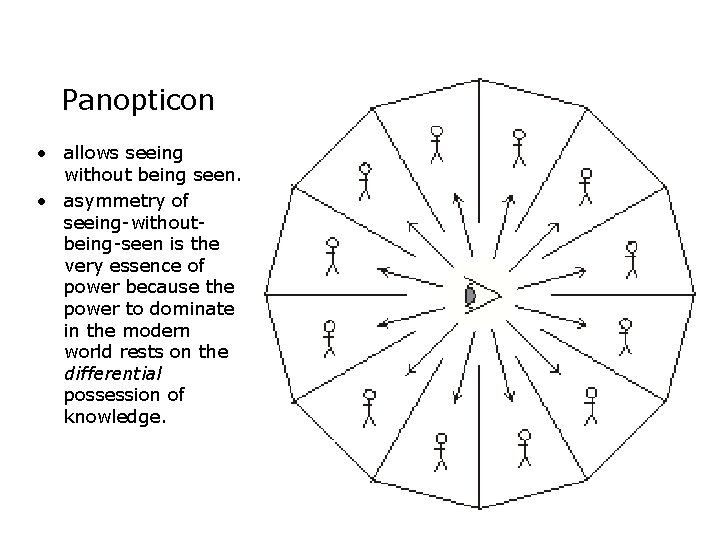
Panopticon • allows seeing without being seen. • asymmetry of seeing-withoutbeing-seen is the very essence of power because the power to dominate in the modern world rests on the differential possession of knowledge.

The modern panopticon: Shenzhen city Purpose built for the 2008 Olympics 12. 4 million people 2 million CCTVs movements are tracked through national ID cards with scannable computer chips and photos that are instantly uploaded to police databases and linked to their holder's personal data of names, photos, residency information, work history and biometric data.

Panopticon in popular culture Big Brother Truman show The Sims Second Life

The 21 st century panopticon • What you’ve done – Archived data • What you’re doing – Real-time data and media • What you’ll do – Profiling

Surveillant Assemblage convergence and integration

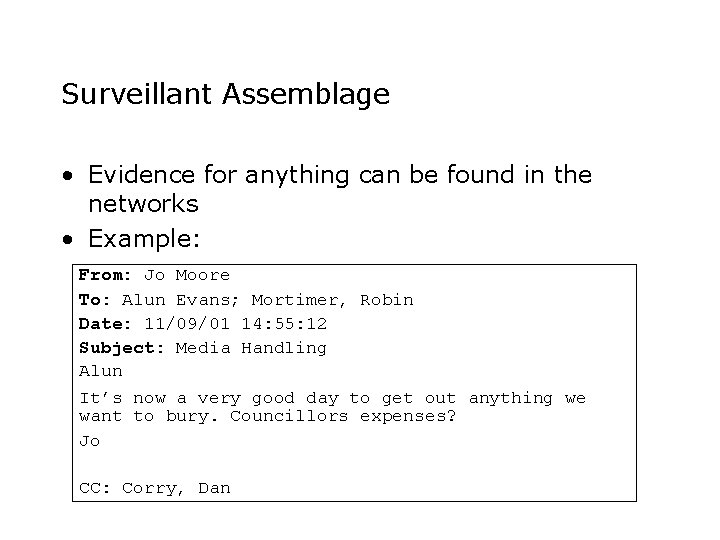
Surveillant Assemblage • Evidence for anything can be found in the networks • Example: From: Jo Moore To: Alun Evans; Mortimer, Robin Date: 11/09/01 14: 55: 12 Subject: Media Handling Alun It’s now a very good day to get out anything we want to bury. Councillors expenses? Jo CC: Corry, Dan





Surveillance and Control Information systems make activities, events and objects, and - people- more visible • Negative effects: • Positive effects: – “information panopticon” – improved efficiency and – Surveillance of human effectiveness behaviour – increased insight and – resistance overview over – Limits of freedom and organisational processes autonomy (e. g. Work-flow systems) – influence on the appropriation of IT – Unpredictable patterns of use can emerge

Data Surveillance • the systematic use of personal data systems in the investigation or monitoring of the actions or communications of one or more persons. • significantly less expensive than physical and electronic surveillance, because it can be automated. • the economic constraints on surveillance are diminished, and more individuals, and larger populations, are therefore monitored. • possibilities enhanced by digital convergence and integration

Data Surveillance • Personal data surveillance • Mass data surveillance – both may be used for its deterrent effects. – comprises a wide range of techniques: • Front-End Verification. • Computer Matching. • Profiling

Profiling • Template created for a particular class of person from past experience • Data-holdings are then searched for digital personae with a close fit to that set of characteristics – used by government agencies to construct models of classes of person, eg. , deviant or vunerable. – used by corporations to identify markets and consumers, but also staff-members and job-applicants relevant to vacant positions.

Function Creep • Definition: – Function Creep occurs when a technology, a system, or personal data is lawfully and systematically expanded for unintended or unforeseen purposes. • Often demonstrates Surveillant Assemblage

Function creep example: The UK national DNA Database 1. Originally focused on convictions for murder, burglary, sexual assault and GBH 2. All individuals charged, reported, cautioned or convicted of any recordable offence 3. DNA data to be stored indefinitely, regardless of acquittal or innocence 4. Short - medium term political goal of identifying all individual’s characteristics from DNA