Type of Computer Viruses What is a computer


















- Slides: 30


Type of Computer Viruses

What is a computer virus? • Exist over the past few years • There are over 10, 000 known computer viruses • Over 200 new viruses are being discovered every month • hidden program, which invades your computer • Has the potential to cause damage and/or perform unwanted/unauthorized functions.

How does a virus work? • A computer virus performs two basic functions – It copies itself from machine to machine (self reproducing) – It executes the instructions the perpetrator has planned.

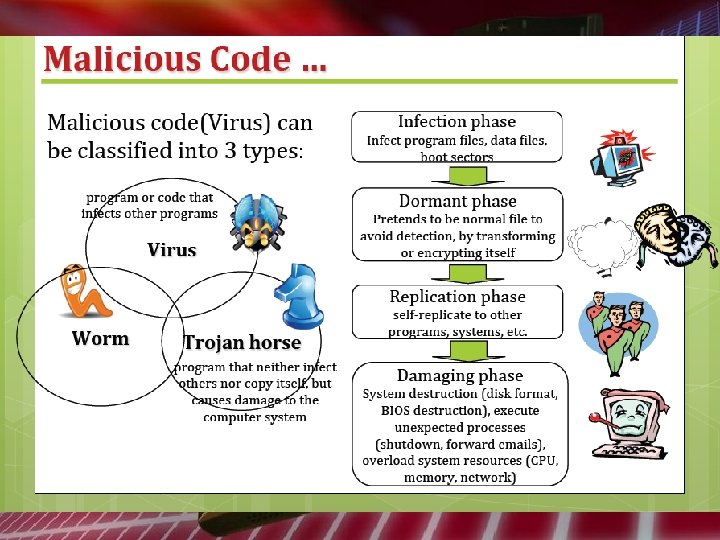
A computer virus exhibits three characteristics: • a replication mechanism • an activation mechanism • an objective

What damage can a virus do? • • • computer virus can cause unwanted alteration computer virus can loss of data annoy the user destroy all your data files your machine can even be rendered unusable

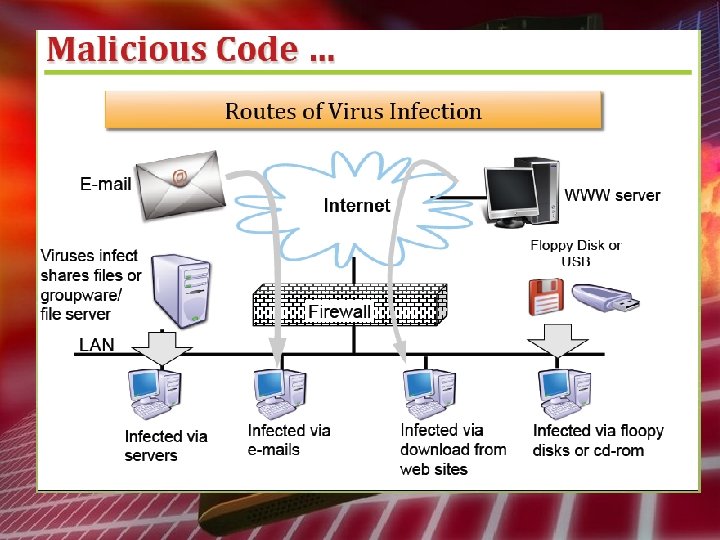
How do they spread? Viruses are usually spread by media/programs swapped.

Kind of viruses • Encrypted Viruses : most difficult kind of bug to detect and the most difficult to stop • Secret Viruses : make changes to files on your computer, or completely replace files • Time Delay Viruses • The Anti-Virus • The Multi-Headed Virus

Kind of viruses (continue) • • • The Misdirection Virus A Cloning Virus The Author Virus The Bad Penny Virus Rewriting Virus The Melissa Virus End Type of Viruses

How to Know if Your Computer is Infected with a Virus

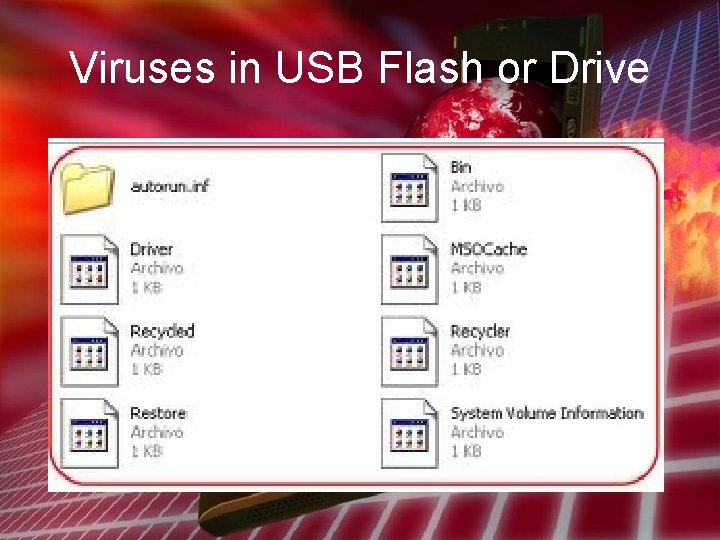
Viruses in USB Flash or Drive

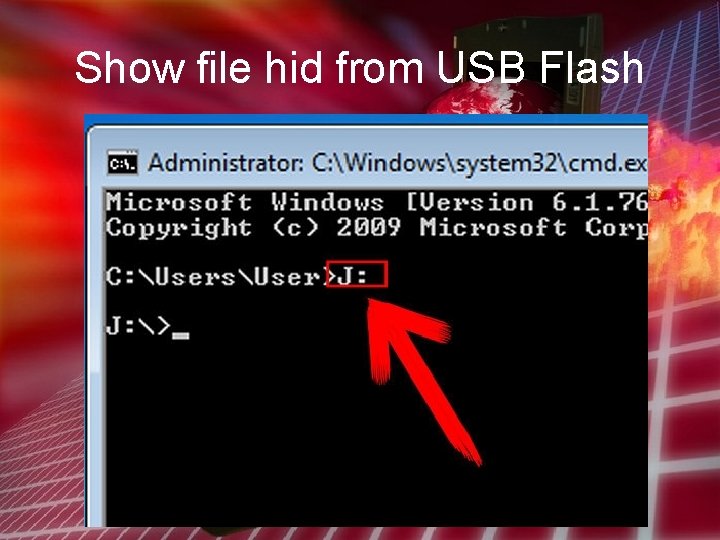
Show file hid from USB Flash To unhide file in USB Flash • Run=> cmd. exe • F: or G: (Drive USB Flash) : => hit Enter • F: > attrib -s -h /s /d *. * => hit Enter

Show file hid from USB Flash

Attack Techniques

What is attack ? In computer and computer networks an attack is any attempt to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset

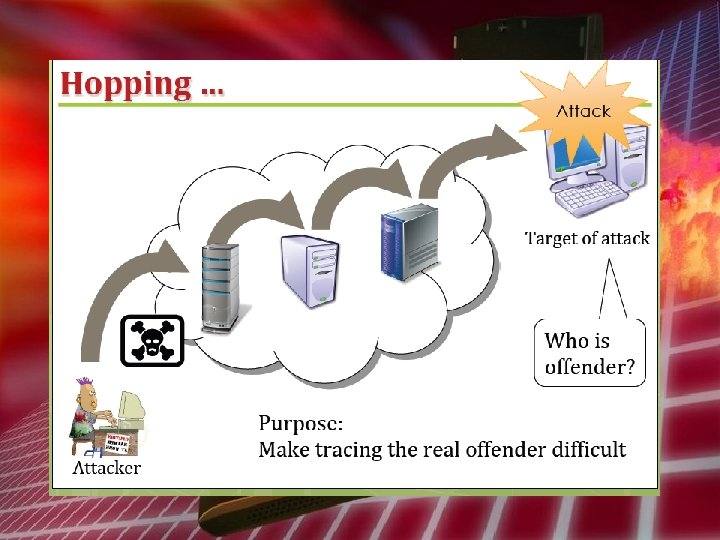
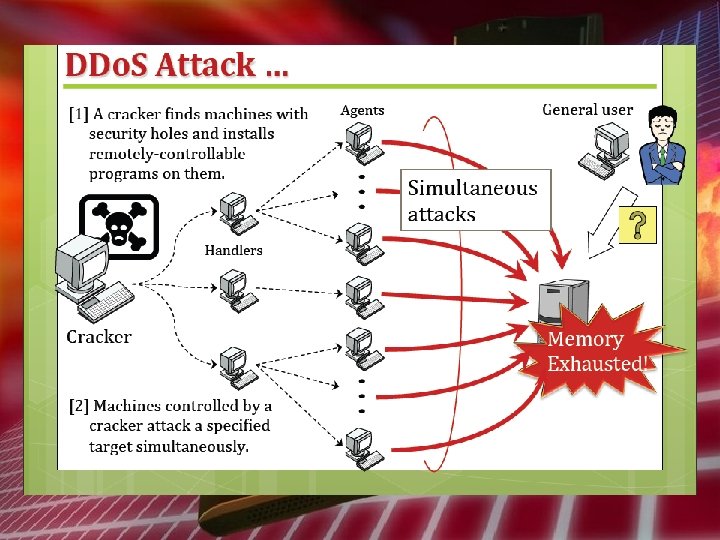
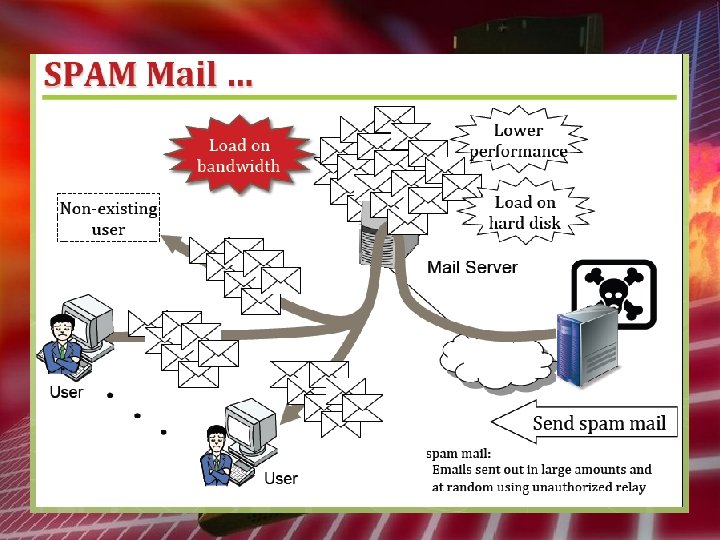
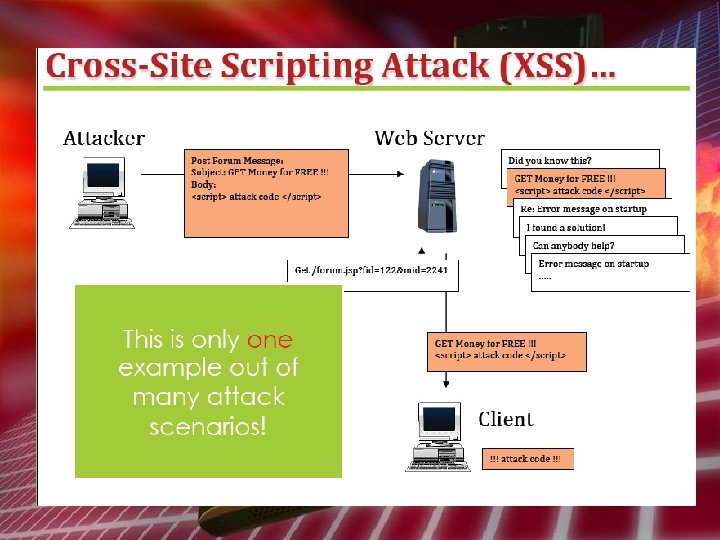
Unauthorized Access Attack • • Spoofing Hopping Do. S DDo. S Spam Mail Malicious Code Cross Site Scripting Attack

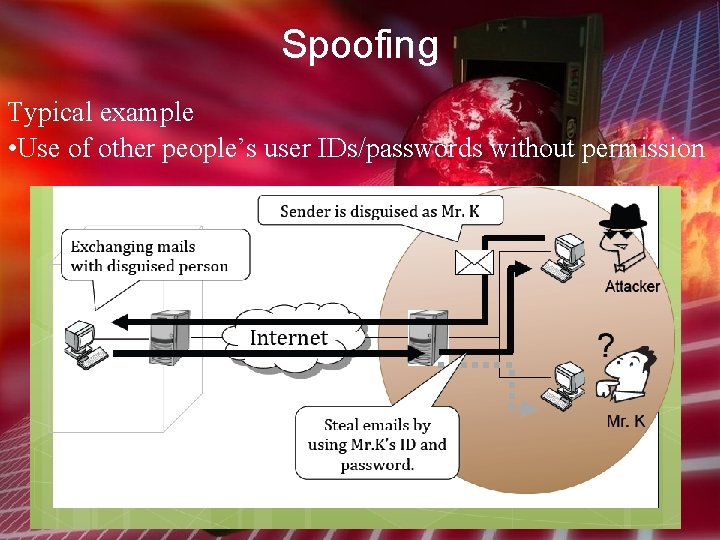
Spoofing Typical example • Use of other people’s user IDs/passwords without permission


Dos Attack








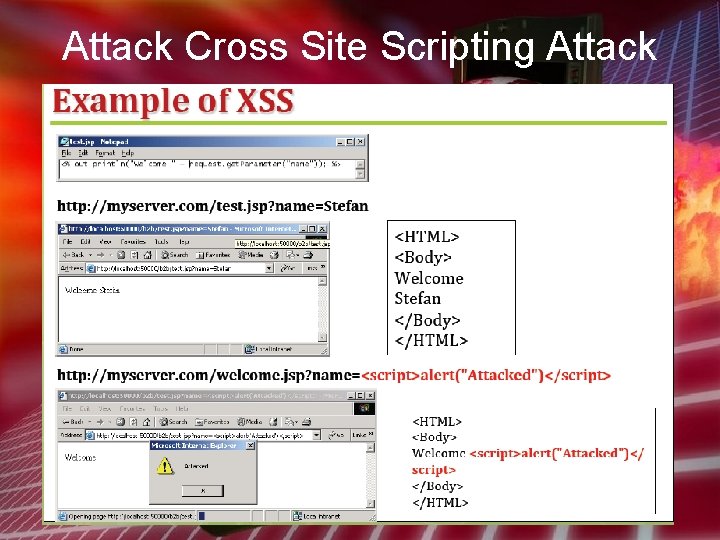
Attack Cross Site Scripting Attack

Resource : • • http: //en. wikipedia. org http: //www. secudemy. com http: //www. google. com Chapter 03 -Unauthorized. Access. Method

Q&A

Thank You For Listening And Join This Event !. . Good Luck !