Tutorial TCP 101 The Transmission Control Protocol TCP







- Slides: 36

Tutorial: TCP 101 • The Transmission Control Protocol (TCP) is the protocol that sends your data reliably • Used for email, Web, ftp, telnet, p 2 p, … • Makes sure that data is received correctly: right data, right order, exactly once • Detects and recovers from any problems that occur at the IP network layer • Mechanisms for reliable data transfer: sequence numbers, acknowledgements, timers, retransmissions, flow control. . . CPSC 441 Copyright © 2005 Department of Computer Science 1

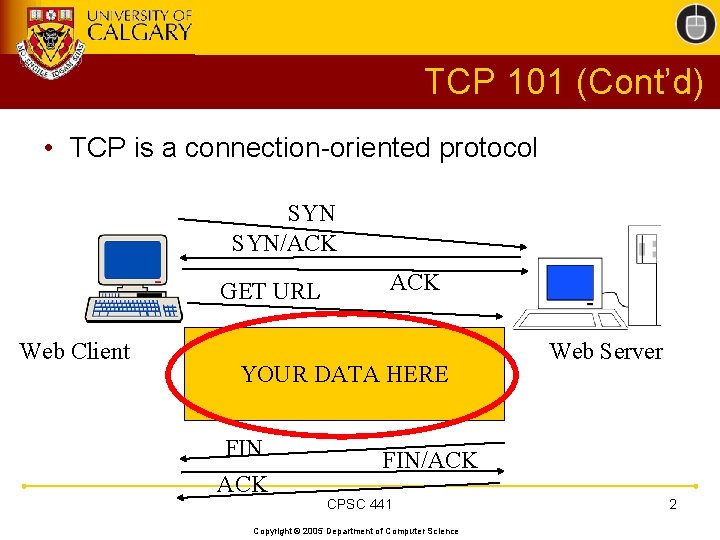
TCP 101 (Cont’d) • TCP is a connection-oriented protocol SYN/ACK GET URL Web Client ACK YOUR DATA HERE FIN ACK Web Server FIN/ACK CPSC 441 Copyright © 2005 Department of Computer Science 2

TCP 101 (Cont’d) • TCP slow-start and congestion avoidance ACK CPSC 441 Copyright © 2005 Department of Computer Science 3

TCP 101 (Cont’d) • TCP slow-start and congestion avoidance ACK CPSC 441 Copyright © 2005 Department of Computer Science 4

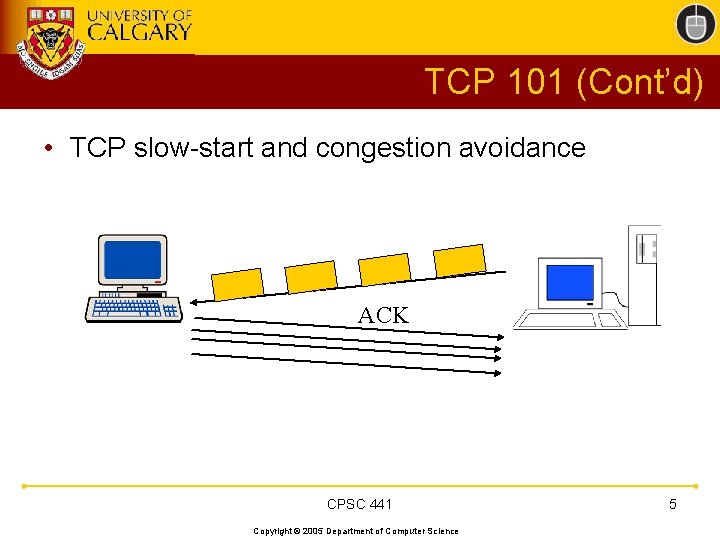
TCP 101 (Cont’d) • TCP slow-start and congestion avoidance ACK CPSC 441 Copyright © 2005 Department of Computer Science 5

TCP 101 (Cont’d) • This (exponential growth) “slow start” process continues until either: – packet loss: after a brief recovery phase, you enter a (linear growth) “congestion avoidance” phase based on slow-start threshold found – limit reached: slow-start threshold, or maximum advertised receive window size – all done: terminate connection and go home CPSC 441 Copyright © 2005 Department of Computer Science 6

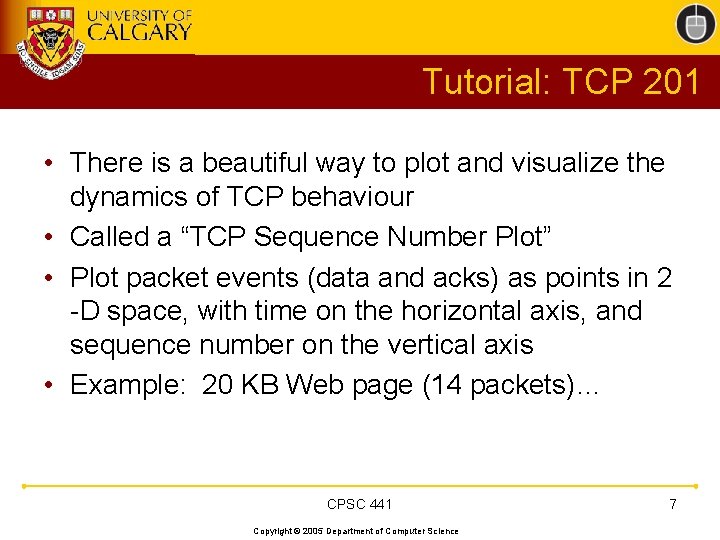
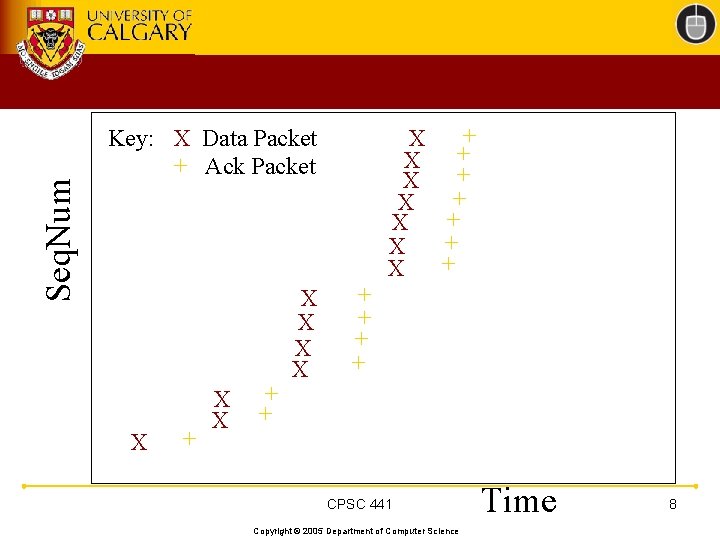
Tutorial: TCP 201 • There is a beautiful way to plot and visualize the dynamics of TCP behaviour • Called a “TCP Sequence Number Plot” • Plot packet events (data and acks) as points in 2 -D space, with time on the horizontal axis, and sequence number on the vertical axis • Example: 20 KB Web page (14 packets)… CPSC 441 Copyright © 2005 Department of Computer Science 7

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science Time 8

So What? • What can it tell you? • Everything!!! CPSC 441 Copyright © 2005 Department of Computer Science 9

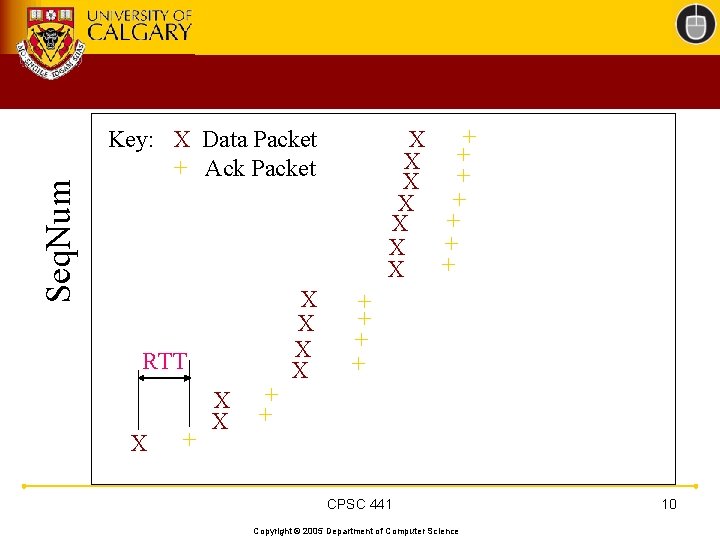
Seq. Num + X + X Key: X Data Packet + Ack Packet RTT X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 10

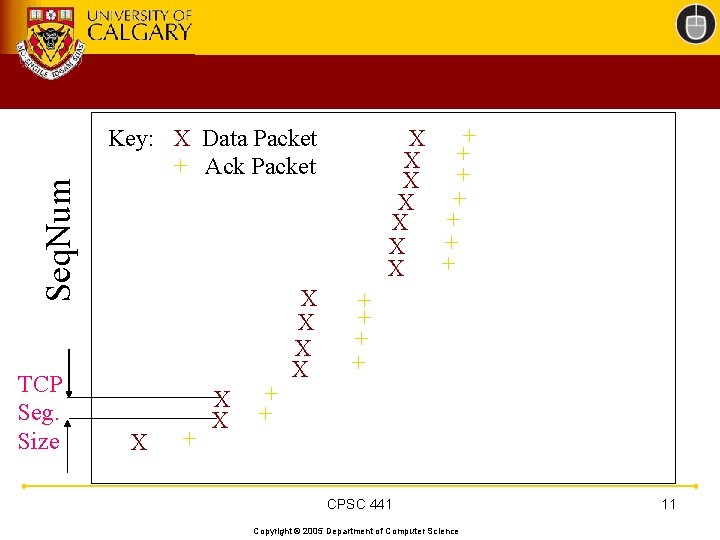
Seq. Num TCP Seg. Size + X + X Key: X Data Packet + Ack Packet X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 11

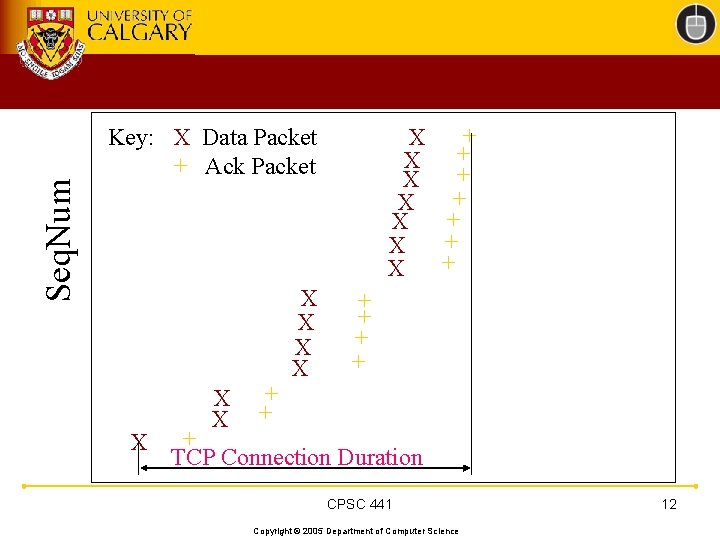
Seq. Num + X + X Key: X Data Packet + Ack Packet X X X + + + TCP Connection Duration CPSC 441 Copyright © 2005 Department of Computer Science 12

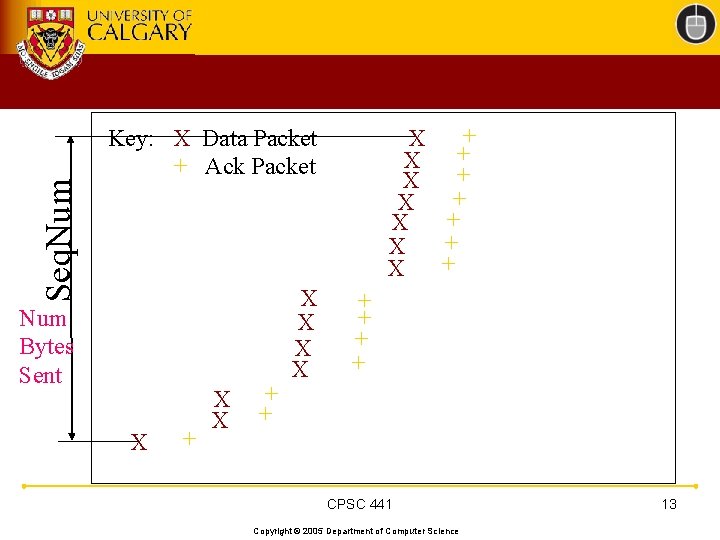
Seq. Num + X + X Key: X Data Packet + Ack Packet Num Bytes Sent X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 13

Seq. Num + X + X ) X + c e + X /S s te + X y + (B X Bytes t u p X h + g + X ou r + X Th + X vg A X + X + Sec Key: X Data Packet + Ack Packet CPSC 441 Copyright © 2005 Department of Computer Science 14

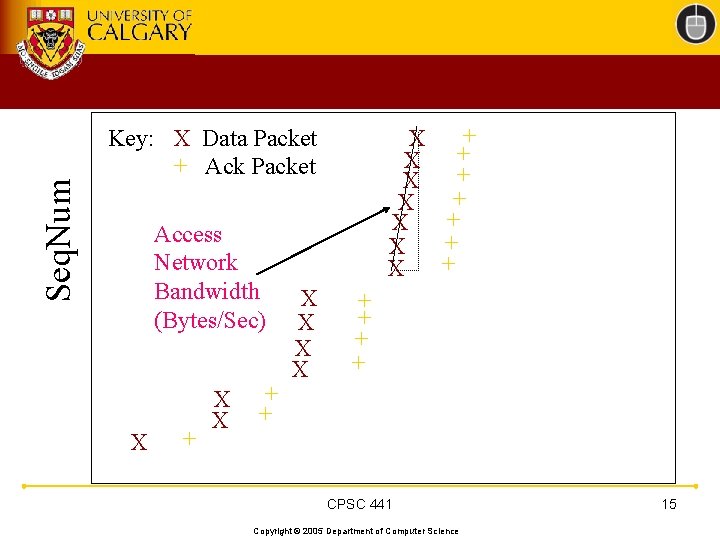
Seq. Num + X + X Key: X Data Packet + Ack Packet Access Network Bandwidth (Bytes/Sec) X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 15

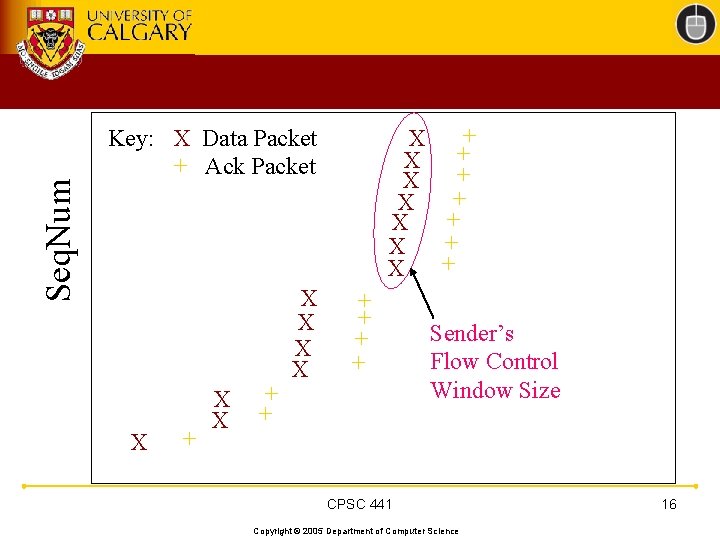
Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Sender’s Flow Control Window Size CPSC 441 Copyright © 2005 Department of Computer Science 16

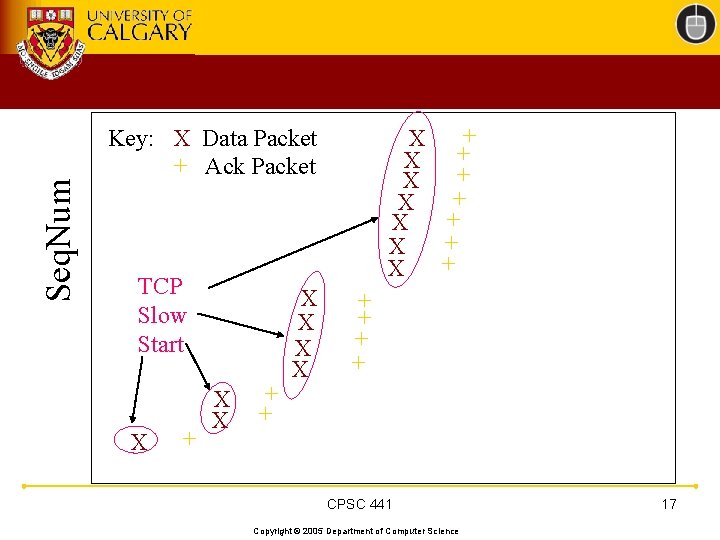
Seq. Num + X + X Key: X Data Packet + Ack Packet TCP Slow Start X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 17

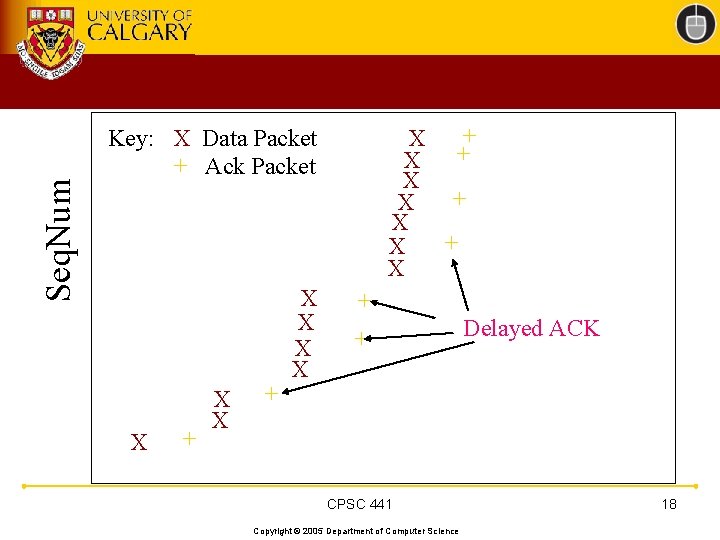
Seq. Num + X X Key: X Data Packet + Ack Packet X + X X X X + + CPSC 441 Copyright © 2005 Department of Computer Science Delayed ACK 18

Seq. Num Key: X Data Packet + Ack Packet X Packet Loss X X X + + X X ++ + + + CPSC 441 Copyright © 2005 Department of Computer Science Duplicate ACK 19

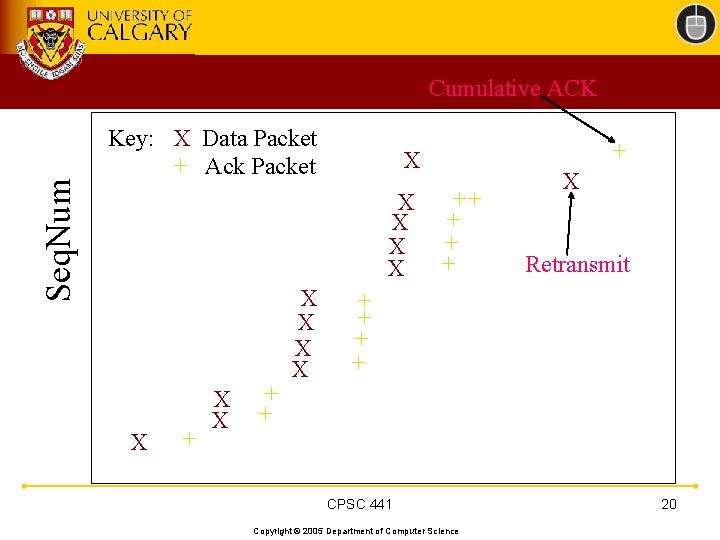
Seq. Num Cumulative ACK Key: X Data Packet + Ack Packet X X X + + X X + X ++ + X Retransmit + + CPSC 441 Copyright © 2005 Department of Computer Science 20

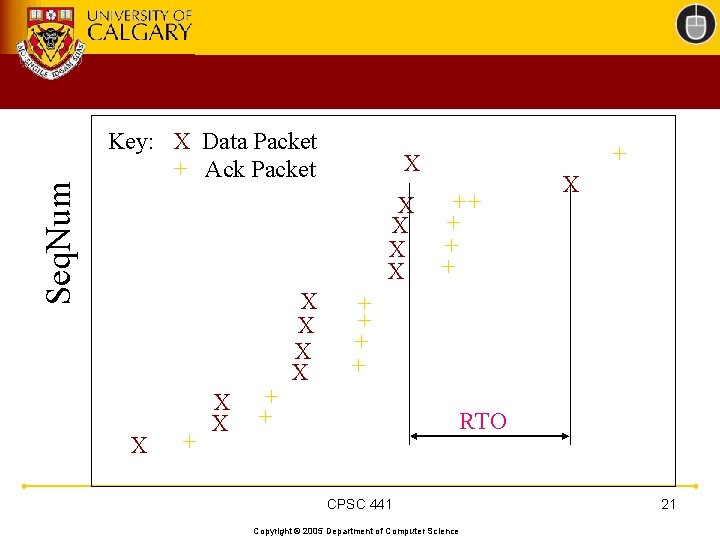
Seq. Num Key: X Data Packet + Ack Packet X X X + + X X + X ++ + X + + RTO CPSC 441 Copyright © 2005 Department of Computer Science 21

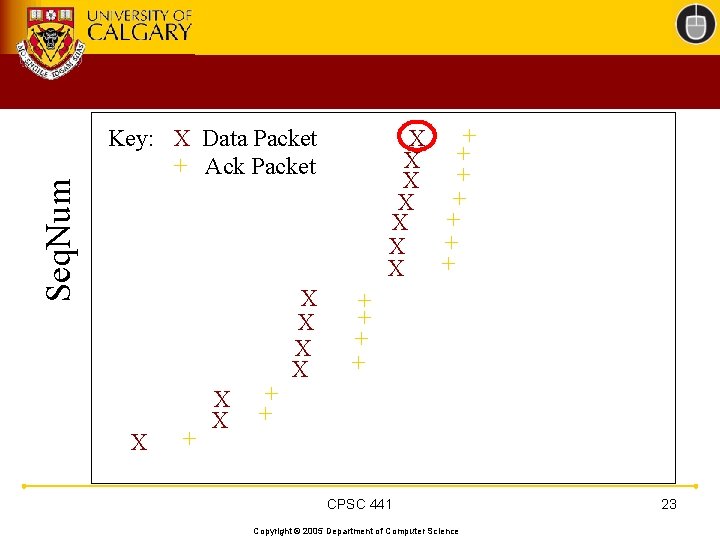
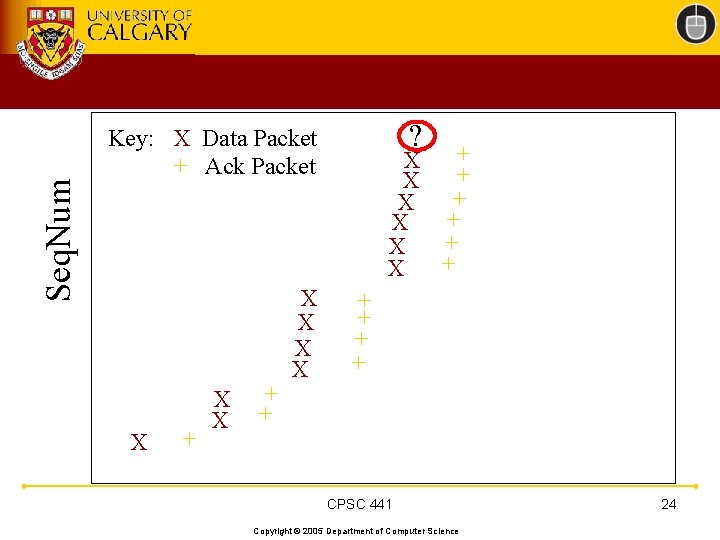
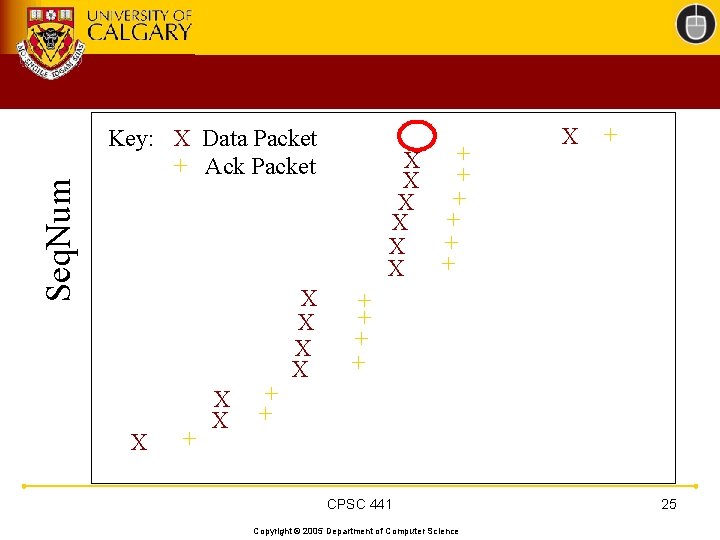
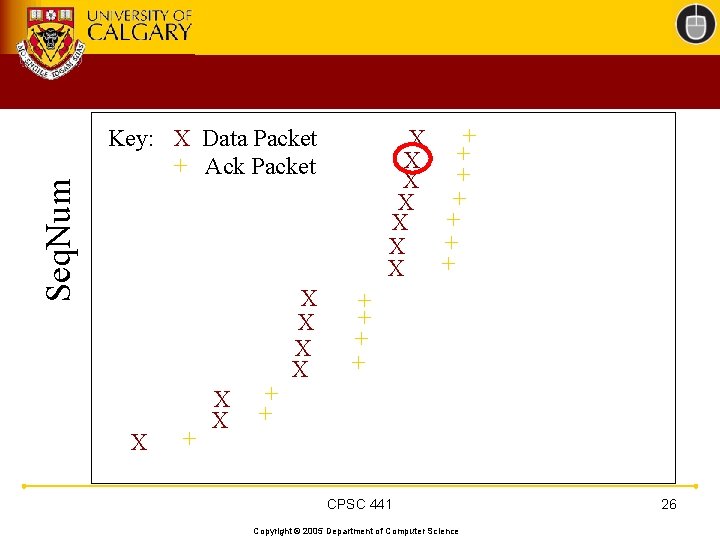
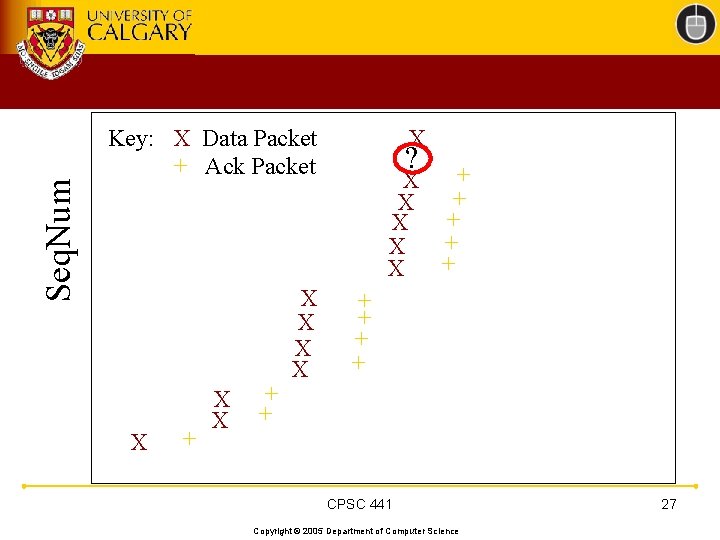
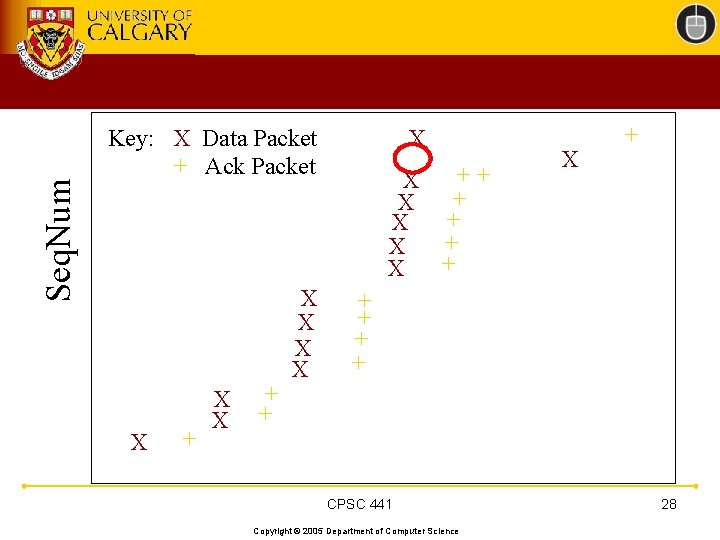
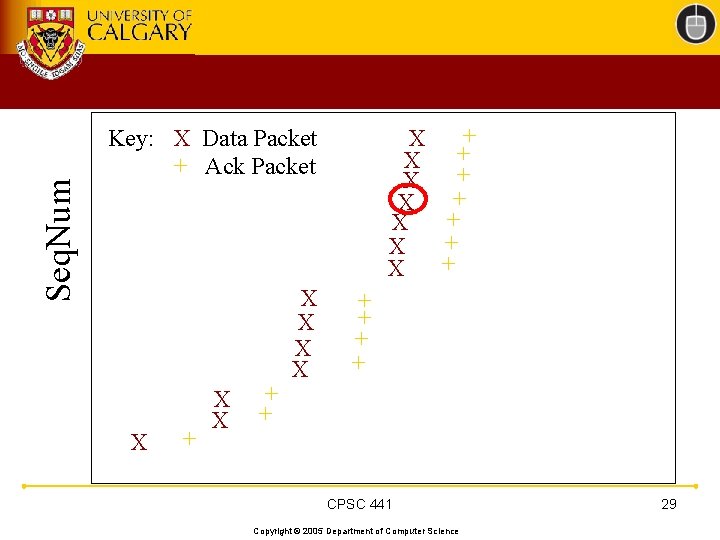
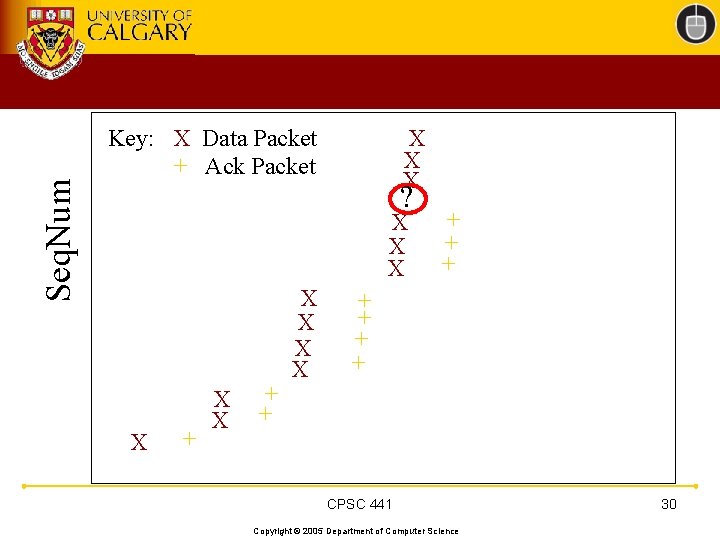
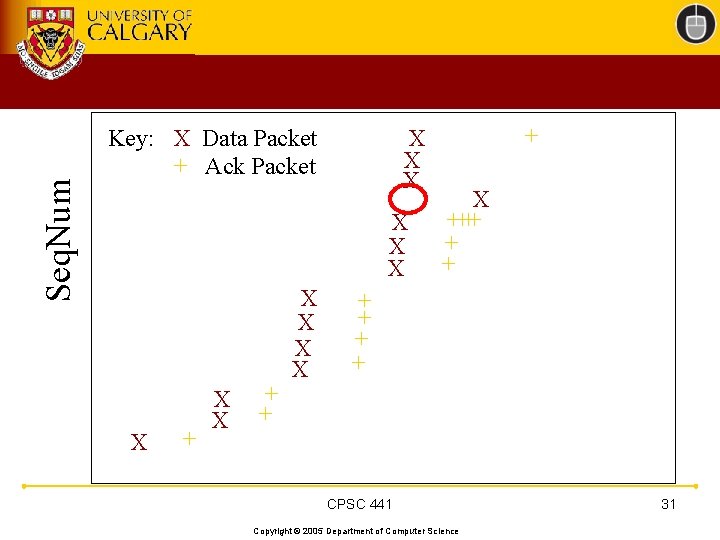
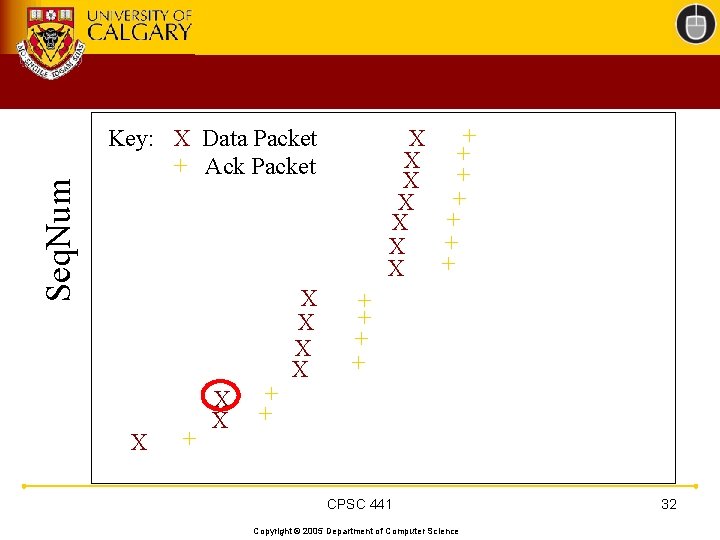
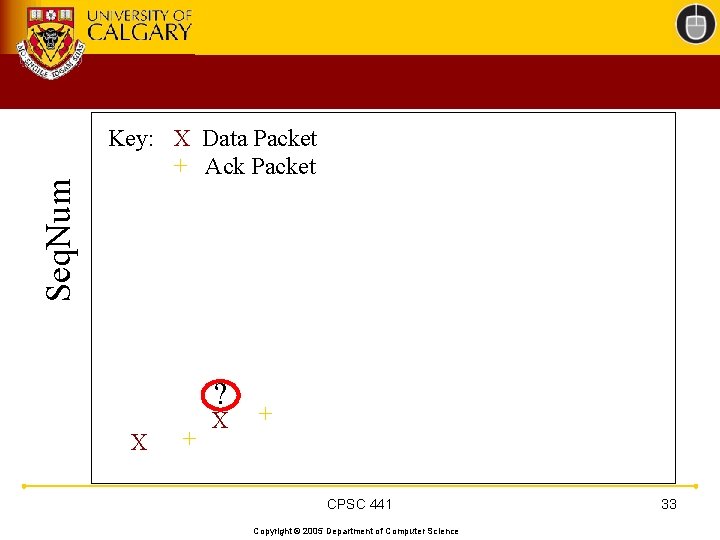
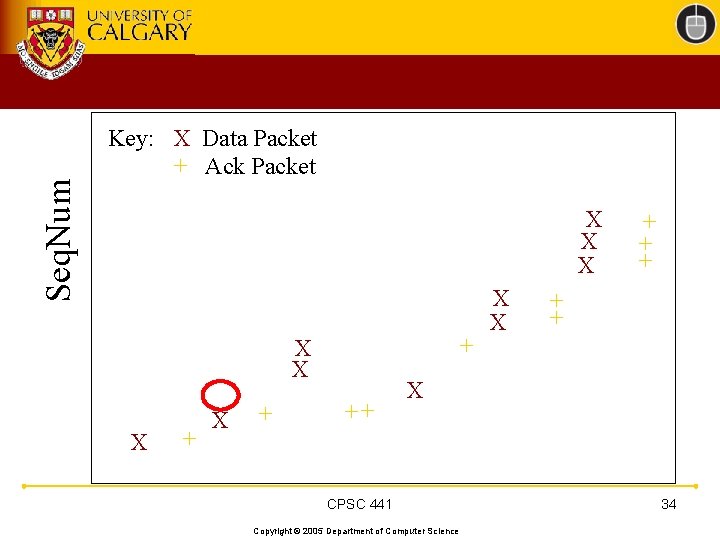
TCP 201 (Cont’d) • What happens when a packet loss occurs? • Quiz Time. . . – Consider a 14 -packet Web document – For simplicity, consider only a single packet loss CPSC 441 Copyright © 2005 Department of Computer Science 22

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 23

Seq. Num ? Key: X Data Packet + Ack Packet X + X X + X + X + X + + CPSC 441 Copyright © 2005 Department of Computer Science 24

Seq. Num Key: X Data Packet + Ack Packet X + X X + X + X + X X + + + CPSC 441 Copyright © 2005 Department of Computer Science 25

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 26

Seq. Num Key: X Data Packet + Ack Packet X + X X + + X X X ? + X + X + X + + CPSC 441 Copyright © 2005 Department of Computer Science 27

Seq. Num Key: X Data Packet + Ack Packet X + X X + + X X X ++ X + X + X X + + + CPSC 441 Copyright © 2005 Department of Computer Science 28

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 29

Seq. Num Key: X Data Packet + Ack Packet X X X ? X X + + X X + + + + CPSC 441 Copyright © 2005 Department of Computer Science 30

Seq. Num Key: X Data Packet + Ack Packet X X X X + + X X + X +++ + + + CPSC 441 Copyright © 2005 Department of Computer Science 31

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + CPSC 441 Copyright © 2005 Department of Computer Science 32

Seq. Num Key: X Data Packet + Ack Packet ? X + CPSC 441 Copyright © 2005 Department of Computer Science 33

Seq. Num Key: X Data Packet + Ack Packet X X X + X + ++ X X + + + X CPSC 441 Copyright © 2005 Department of Computer Science 34

TCP 201 (Cont’d) • Main observation: – “Not all packet losses are created equal” - CLW 2002 • Losses early in the transfer have a huge adverse impact on the transfer latency • Losses near the end of the transfer always cost at least a retransmit timeout • Losses in the middle may or may not hurt, depending on congestion window size at the time of the loss CPSC 441 Copyright © 2005 Department of Computer Science 35

Congratulations! • You are now a TCP expert! CPSC 441 Copyright © 2005 Department of Computer Science 36