Tutorial 6 Internet Security Objectives Session 6 1

Tutorial 6: Internet Security

Objectives • Session 6. 1 – Explore basic security concepts and countermeasures – Study how encryption works – Learn about phishing and digital watermarking – Understand denial-of-service attacks and how to prevent them – Recognize and prevent identity theft – Explore security concerns for users of social networks New Perspectives on the Internet, 9 th Edition 2

Objectives • Session 6. 2 – Understand security threats to Web clients and how to prevent them – Investigate the use of programs that detect and remove malware – Recognize the potential security issues that arise from electronic tracking devices – Study how a firewall is used to block communication – Learn how to secure a Web server New Perspectives on the Internet, 9 th Edition 3

Session 6. 1 Overview Physical and Logical Security New Perspectives on the Internet, 9 th Edition 4

Security Basics • Security is broadly defined as the protection of assets from unauthorized access, use, alteration, or destruction • Any act or object that endangers an asset is known as a threat • Logical security threats are generally classified in three categories: – Secrecy threat – occurs when data is disclosed to an unauthorized party – Integrity threat – results in unauthorized data modification – Necessity threat – causes data delays or denials New Perspectives on the Internet, 9 th Edition 5

Security Basics • A countermeasure is a physical or logical procedure that recognizes, reduces, or eliminates a threat • The countermeasure that an individual or organization chooses often depends on the expected types of threats – The best way to safeguard against a threat is to prevent it from occurring in the first place – In some cases, need to plan for losses in service or theft by purchasing insurance or installing backup systems • The process of risk management focuses on identifying threats and determining available and affordable countermeasures New Perspectives on the Internet, 9 th Edition 6
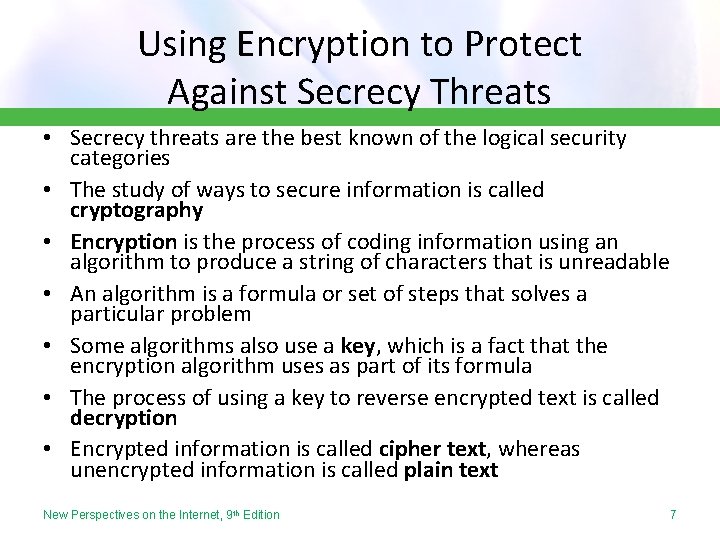
Using Encryption to Protect Against Secrecy Threats • Secrecy threats are the best known of the logical security categories • The study of ways to secure information is called cryptography • Encryption is the process of coding information using an algorithm to produce a string of characters that is unreadable • An algorithm is a formula or set of steps that solves a particular problem • Some algorithms also use a key, which is a fact that the encryption algorithm uses as part of its formula • The process of using a key to reverse encrypted text is called decryption • Encrypted information is called cipher text, whereas unencrypted information is called plain text New Perspectives on the Internet, 9 th Edition 7
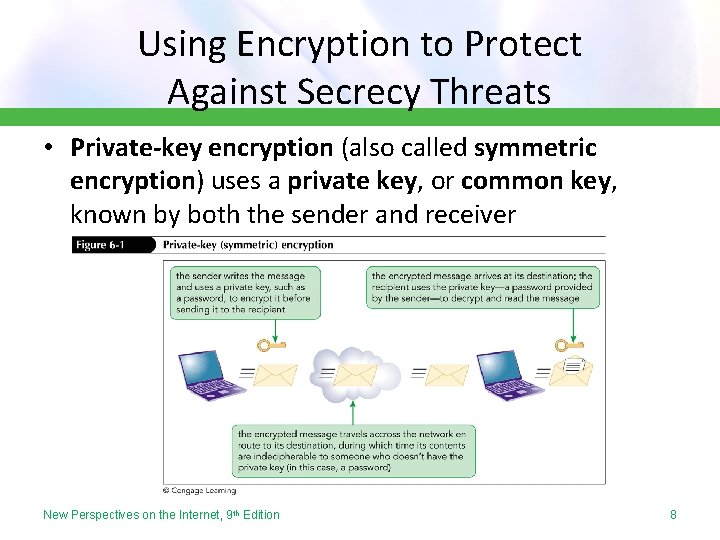
Using Encryption to Protect Against Secrecy Threats • Private-key encryption (also called symmetric encryption) uses a private key, or common key, known by both the sender and receiver New Perspectives on the Internet, 9 th Edition 8
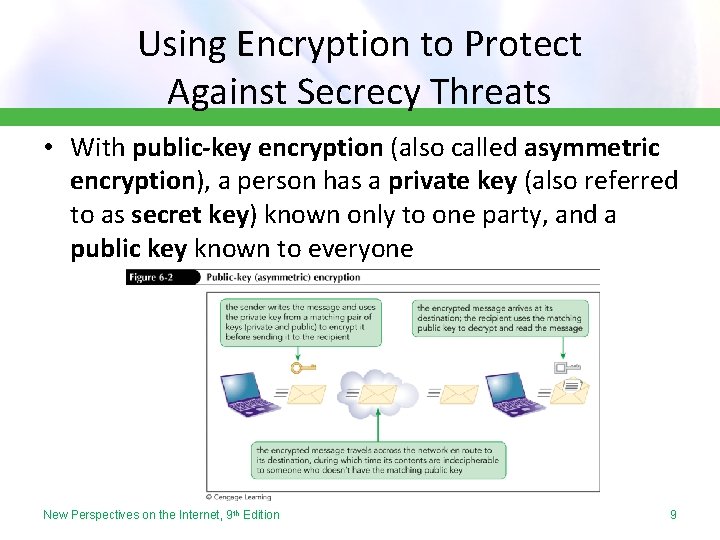
Using Encryption to Protect Against Secrecy Threats • With public-key encryption (also called asymmetric encryption), a person has a private key (also referred to as secret key) known only to one party, and a public key known to everyone New Perspectives on the Internet, 9 th Edition 9

Using Encryption to Protect Against Secrecy Threats • Encryption is considered weak or strong based on its algorithm and the number of characters in the encryption key • Resistance of an encrypted message to attack attempts depends on the size of the key used – A 40 -bit key provides a minimal level of security – 128 -bit and 256 -bit keys are commonly called strong keys • As computers become faster and more powerful, the length of keys must increase to prevent computers from being used to break encrypted transmissions New Perspectives on the Internet, 9 th Edition 10
Protecting the Integrity of Electronic Data • Data integrity threats can change the actions an individual or organization takes by altering the content of a message or transaction • Occurs when an unauthorized party alters data during its transfer or while it is stored on a drive or server • In a man-in-the-middle exploit, the contents of an email are changed in a way that negates the message’s original meaning • Phishing Attacks – An email that includes the name of someone you know in the message’s From line, a tactic called spoofing – Often spoofed email from banks, online services, credit card companies, etc. – When individuals open the email and follow a hyperlink, they are taken to a form that illicitly collects personal information – Called phishing because it “fishes” for information New Perspectives on the Internet, 9 th Edition 11
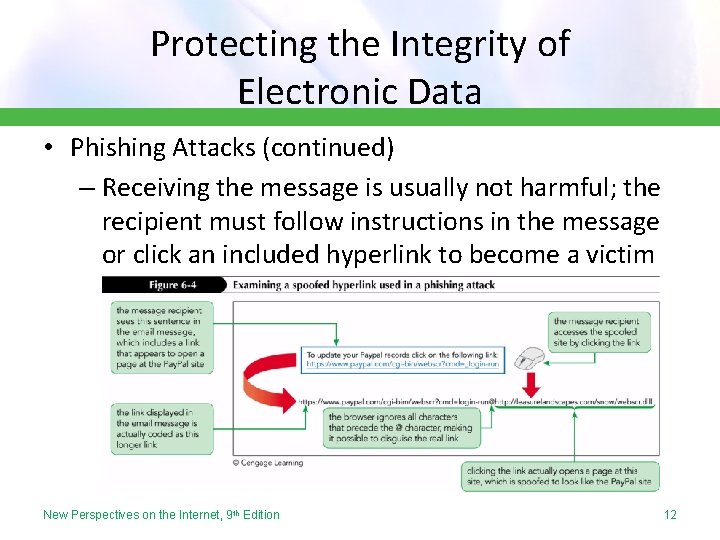
Protecting the Integrity of Electronic Data • Phishing Attacks (continued) – Receiving the message is usually not harmful; the recipient must follow instructions in the message or click an included hyperlink to become a victim New Perspectives on the Internet, 9 th Edition 12

Protecting Copyrighted Materials Using Digital Watermarks • A digital watermark is a digital pattern containing copyright information that is inserted into a digital image, animation, or audio or video file – The watermark is inserted using a software program so that it is invisible and undetectable – To view the watermark, a software program unlocks it, retrieving the information it stores • Steganography is a process that hides encrypted messages within different types of files New Perspectives on the Internet, 9 th Edition 13

Preventing Denial-of-Service Attacks • The most common necessity attack, called a denial of service (Do. S) attack, occurs when an attacker floods a computer, server, or network with so many messages that the network’s bandwidth resources are consumed disabling its services and communications • In a distributed denial of service (DDo. S) attack, the attacker uses a large number of computers that each launch a Do. S attack on a server at the same time • Often computers used in a DDo. S attack are ones that have been hijacked by a Trojan horse; these computers are often called bots or zombies New Perspectives on the Internet, 9 th Edition 14
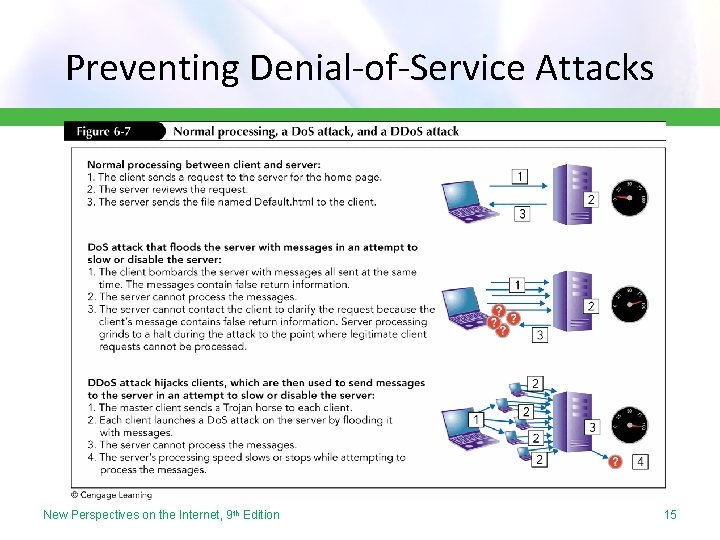
Preventing Denial-of-Service Attacks New Perspectives on the Internet, 9 th Edition 15

Preventing Denial-of-Service Attacks • To prevent an attack, different types of hardware and software can be installed that monitor and detect problems early and prevent attacks – A company can defend its Web server by installing a denial-of-service filter, or Do. S filter – Do. S filter functions are often included as part of a network software tool called a packet sniffer, which examines the structure of the data elements that flow through a network New Perspectives on the Internet, 9 th Edition 16

Recognizing and Preventing Identity Theft • A thief can potentially steal a person’s entire identity • In this type of crime, called identity theft, a thief can: – Use the victim’s personal information to open bank accounts, obtain new credit cards, and buy expensive goods on credit – Damage the victim’s credit rating – Make transactions for which the victim is responsible • It can take a long time for victims to clear their records and restore their credit New Perspectives on the Internet, 9 th Edition 17
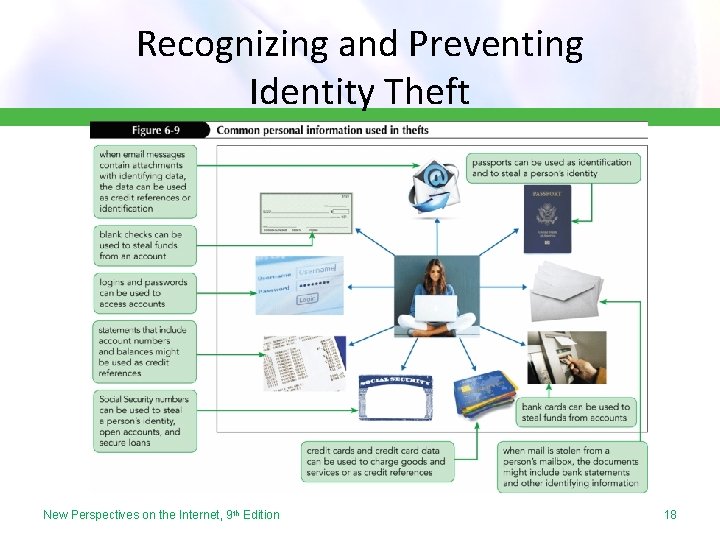
Recognizing and Preventing Identity Theft New Perspectives on the Internet, 9 th Edition 18

Security Concerns for Social Network Users • As use of social networks increase, individuals and business must implement appropriate security strategies to protect themselves from problems and threats • Carefully control the information posted on a social networking site and use security settings that offer the most protection • Rely on common sense to protect identity, property, and privacy; many hoaxes and scams start on social networking sites • Be alert for the potential security problems that a shortened URL can cause New Perspectives on the Internet, 9 th Edition 19

Session 6. 2 Overview Enhancing Security New Perspectives on the Internet, 9 th Edition 20

Web Client Security • One of the most important Web client security risks arises from the existence of active content • Active Content: Java, Java. Script, and Active. X – One of the most dangerous entry points for Do. S attacks is from programs that travel with applications to a browser and are executed on the user’s computer – These programs, often called active content, include Java, Java. Script, and Active. X components that can run programs on a Web client – Active content components can: • Make Web pages more useful by providing interactive content (i. e. , calculating shipping costs, creating mortgage payment tables, creating animation) • Be used for malicious purposes New Perspectives on the Internet, 9 th Edition 21

Web Client Security • Active Content: Java, Java. Script, and Active. X (cont. ) – A Java applet is a program written in the Java programming language which can execute and consume computer resources – A Java. Script program can pose a threat because it can run without being compiled – Active. X controls are Microsoft’s technology for writing small applications that perform some action in Web pages; these controls have access to a computer’s file system – Internet Explorer secures Active. X controls with a digital signature which provides verification of the contents of the file and identifies its author or developer – When a digital signature authenticates an Active. X control’s developer or source, it is called a signed Active. X control New Perspectives on the Internet, 9 th Edition 22

Detecting and Removing Malware • Malware, a term that means “malicious software, ” is a category of software that is installed without the user’s consent • A virus is a program that replicates itself with the goal of infecting other computers • A Trojan horse is a program hidden inside another program • A worm is a self-replicating and self-executing program that sends copies of itself to other computers over a network New Perspectives on the Internet, 9 th Edition 23

Detecting and Removing Malware • Adware (short for “ad-supported software”) is a category of software that includes advertisements to help pay for the program in which they appear • When adware is installed on a computer without the user’s knowledge and consent it becomes a form of malware called spyware • Spyware works much like adware except that the user has no control over of knowledge of the ads and other monitoring features the ads contain • Internet security software can prevent the spread of malware by blocking them from being downloaded from the server New Perspectives on the Internet, 9 th Edition 24

Detecting and Removing Malware • Two vendors that provide a full range of products are Norton and Mc. Afee • Because malware is often hidden in other programs, running an Internet security program might not adequately protect your computer • You can purchase a separate software program that scans your entire hard drive for malware and includes tools to remove it • Lavasoft Ad-Aware Free is a popular program for scanning for adware New Perspectives on the Internet, 9 th Edition 25

Blocking Tracking Devices in Electronic Communications • A Web bug is a small, hidden graphic on a Web page or in an email message; it is designed to: – Work in conjunction with a cookie to obtain information about the person viewing the page or message – Send that information to a third party • Because a Web bug is usually created with a GIF file, it is sometimes called a clear GIF or a transparent GIF; it is designed to be hidden on the Web page in which it appears New Perspectives on the Internet, 9 th Edition 26

Blocking Tracking Devices in Electronic Communications • Double. Click is a division of Google that develops tools for Internet marketing and advertising • When a user loads a Web page that contains a Web bug, their IP address, the last Web site visited, and other information about the use of the site in which the clear GIF has been embedded can be recorded • The GIF file is not visible because it is transparent New Perspectives on the Internet, 9 th Edition 27

Blocking Tracking Devices in Electronic Communications • When you first access a Double. Click member’s Web site, Double. Click uses a cookie to assign you a number and record it • When you visit any Double. Click member’s Web site in the future, Double. Click reads the cookie and gets your identification number • As you use your browser, Double. Click can use its cookie to collect information and sell this to its members so they can customize their Web sites with tailored advertising • A Web bug is an example of spyware because the clear GIF and its actions are hidden from the user; while not illegal but it does create privacy concerns • You can prevent Web sites from writing cookies by changing your browser’s settings; when you disable cookies, you lose some of the positive attributes that cookies can provide New Perspectives on the Internet, 9 th Edition 28
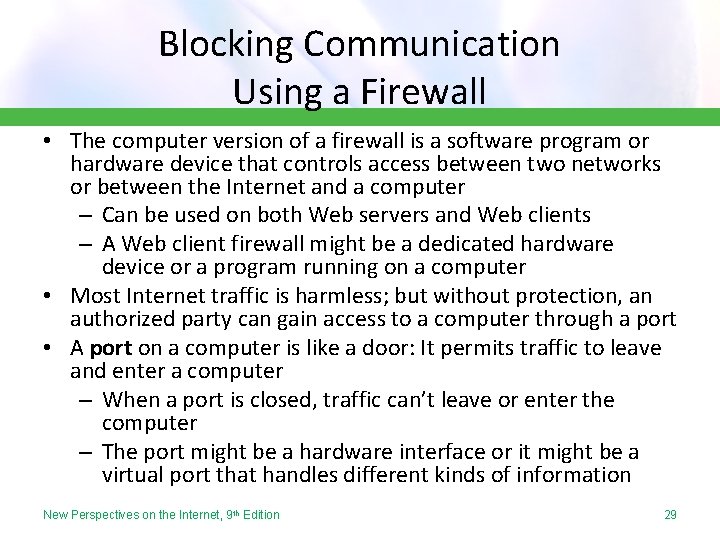
Blocking Communication Using a Firewall • The computer version of a firewall is a software program or hardware device that controls access between two networks or between the Internet and a computer – Can be used on both Web servers and Web clients – A Web client firewall might be a dedicated hardware device or a program running on a computer • Most Internet traffic is harmless; but without protection, an authorized party can gain access to a computer through a port • A port on a computer is like a door: It permits traffic to leave and enter a computer – When a port is closed, traffic can’t leave or enter the computer – The port might be a hardware interface or it might be a virtual port that handles different kinds of information New Perspectives on the Internet, 9 th Edition 29
Blocking Communication Using a Firewall • Virtual ports use numbers to isolate traffic by type • A computer has more than 65, 000 virtual ports for different processes such as: – HTTP/World Wide Web traffic (port 80) – FTP traffic (port 21) – SMTP email (port 25) – POP 3 email (port 110) – SSL (port 443) • To connect to the Internet, you must open port 80 • If port 80 is not properly protected, an authorized party can use port 80 or other virtual ports to access your computer New Perspectives on the Internet, 9 th Edition 30

Blocking Communication Using a Firewall • A firewall can control incoming traffic by rejecting it unless you have configured it to accept the traffic • During a port scan, one computer tests all or some of the ports of another computer to determine whether its ports are: – Open – traffic is not filtered and the port permits entry through it – Closed – the port does not accept traffic, but a cracker could use this port to gain entry to and analyze your computer – Stealth – the port might be open or closed, but permits no entry through it • You can run a port scan by visiting a Web site that offers this service. New Perspectives on the Internet, 9 th Edition 31

Blocking Communication Using a Firewall • Most firewalls are installed to prevent traffic from entering the network, but firewalls can also prevent data from leaving the network • Especially useful for controlling the activities of hidden programs that are designed to compromise the security of a computer • Because the primary function of a firewall is to block unwanted traffic from reaching the network it protects, each organization that installs a firewall needs to determine what kind of traffic to block and what kind of traffic to permit New Perspectives on the Internet, 9 th Edition 32

Communication Channel Security • Authentication is a general term for the process of verifying the identity of a person, computer, or server with a high degree of certainty • To help keep track of their login information for different computers and Web sites, some people use a program called a password manager, which stores login information in an encrypted form • A brute force attack occurs when a hacker uses a program to enter character combinations until the system accepts a user name and password New Perspectives on the Internet, 9 th Edition 33
Communication Channel Security • The combination of a user login plus a password is called single-factor authentication because it uses one factor; in this case, something the user knows • Multifactor authentication relies on more than one factor • Another approach that banks and financial institutions use to add security to online transactions is multiple layers of control • Multiple layers of control can be implemented by using more than one authentication method New Perspectives on the Internet, 9 th Edition 34

Communication Channel Security • Digital and Server Certificates – A digital certificate is an encrypted and passwordprotected file that contains sufficient information to authenticate and prove a person’s or an organization’s identity – Usually, a digital certificate contains the following information: • The certificate holder’s name, address, and email address • A key that “unlocks” the digital certificate • The certificate’s expiration date or validity period • Verification from a trusted third party, called a certificate authority (CA) New Perspectives on the Internet, 9 th Edition 35
Communication Channel Security • Digital and Server Certificates (continued) – There are two types of digital certificates • Individuals can purchase one type called a digital ID; purchasers of digital IDs can use them to identify themselves to other people and to Web sites that are set up to accept digital certificates • A server certificate is installed on a Web server to prove the identity of the server to Web clients that connect to it to conduct transactions New Perspectives on the Internet, 9 th Edition 36

Communication Channel Security • Assurance Providers – An assurance provider is a third party that, for a fee, will certify that a person or an organization has met some criteria for conducting safe transactions and ensuring privacy before issuing the right to use the assurance provider’s seal on a Web site – Examples include: • The Better Business Bureau’s BBB Accredited Business Seal (formerly BBBOn. Line) certification program • The TRUSTe program focuses on privacy issues • The Norton Secured Seal (formerly Veri. Sign) provides a range of services to electronic commerce Web sites New Perspectives on the Internet, 9 th Edition 37
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) • Secure Sockets Layer (SSL) was the first widely used protocol for establishing secure, encrypted connections between Web browsers and Web servers on the Internet – SSL was revised several times and is still used today – In 1999, SSL version 3 was improved and reissued by the Internet Engineering Task Force – This improved protocol is called Transport Layer Security (TLS) • Both SSL and TLS automatically provide a security “handshake” when a browser and the server to which it is connected want to participate in a secure connection New Perspectives on the Internet, 9 th Edition 38
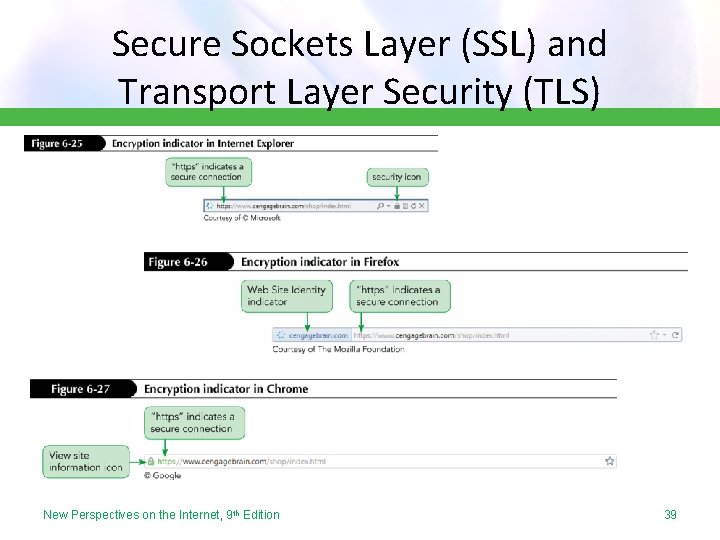
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) New Perspectives on the Internet, 9 th Edition 39
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) • SSL and TLS both use a public key to encrypt a private key and send it from the Web server to the browser • Once the browser decrypts the private key, it uses that private key to encrypt information sent to the Web server during the SSL/TLS connection because privatekey encryption is faster than public-key encryption • When the user leaves the secure Web site, the browser terminates the SSL/TLS connection and discards these temporary keys, or session keys • Session keys exist only during a single connection (session) between a browser and a server New Perspectives on the Internet, 9 th Edition 40
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) • A growing concern that fraudulent Web sites might have obtained SSL certificates led a group of certificate authorities to develop a more stringent set of verification steps • In 2008, this development led to the establishment of stricter criteria and an assurance of a more consistent application of verification procedures • Certificate authorities that followed these more extensive verification procedures were permitted to issue a new type of certificate called Secure Sockets Layer-Extended Validation (SSL-EV) New Perspectives on the Internet, 9 th Edition 41
- Slides: 41