Trusted Operating Systems What is a trusted operating














- Slides: 15

Trusted Operating Systems

What is a trusted operating system n Four aspects of a trusted OS – Information compartmentalization – Role compartmentalization – Least privilege – Kernel level enforcement n “if it’s easy to administer, it’s probably easy to break into”

Pros and cons Pros – Difficult to compromise – One compromise will not lead to another – Useful for mission critical applications – Protects against inside attacks Cons – Software compatibility – Difficulty in administration – Performance overhead – More cumbersome for users

Information Compartmentalization Information restricted without regard to user ID or “owner” n No user, even administrators, can see or modify information they are not cleared to see n Compromised applications cannot be used for further access, since they cannot see information unrelated to their task n

Mandatory Access Control n In DAC (Discretionary Access Control), users own files – User can determine if a file is readable, writable, executable, etc, and by whom n In MAC, restrictions are based on the sensitivity of information – All objects have Sensitivity Labels which define a level or range of levels encompassing the information – SLs cannot be overruled by the owner of a file or even a system administrator

Sensitivity Labels n Two components – – Classification Compartment n Dominant n Equal n Disjoint – Top Secret SL can read but not write Confidential SL – Only time modification is permitted – Prevents equal classifications from accessing other compartments – Top Secret A cannot read Secret A B, since Top Secret A does not have access to the B compartment

Role Compartmentalization No user can perform all system tasks n There is no “root”, administrators are limited in their privileges n Important system actions must be confirmed by multiple administrators n Execution of a privileged program is still limited by privilege of user n

Least Privilege n Processes only have access to the minimum amount of information and privilege required to perform their task – Mail server cannot modify web pages – Web server cannot send email – Even if running as an administrator n Permissions are strictly limited in scope and type

Kernel Level Enforcement Security related operations happen in kernel mode, where they cannot be circumvented by any amount of user level action n However, operations happen at the highest level possible, limiting potential damage as much as possible n Application cannot override kernel decisions n

Trusted OS Implementations n Trusted Solaris – – n Password generator enforces strong passwords MAC Trusted symbol prevents spoofing Full system auditing Trusted IRIX – – MAC Mandatory Integrity Trusted Networking MAC labeling of input and output

Trusted OS Implementations n n n Trusted BSD – Based on Free. BSD – Fine grained auditing – Fine grained policy SELinux – Patches to Linux published by the NSA Argus Pitbull LX – Trusted environment that runs on top of Linux, Solaris, or AIX – Domain Based Access Control – Has root, but restricted – Allows trusted applications to be run in alongside nontrusted applications, providing flexibility

“Orange Book” standards Levels of security policies and accountability mechanisms n Certification to use in given situations n – C 2: Controlled Access Protection (5) – B 1: Labeled Security Protection (7) – B 2: Structured Protection (1) – B 3: Security Domains (1) – A 1: Verified Design (0)

Common Criteria • Supercedes “Orange Book” • Worldwide effort, combines international criteria • Broken into functional requirements: Ø Ø Ø Audit Cryptographic support Communications User Data Protection Identification and Authentication Security Management Ø Ø Ø Privacy Protection of the TOE Security Functions Resource Utilization TOE Access Trusted Path/Channels

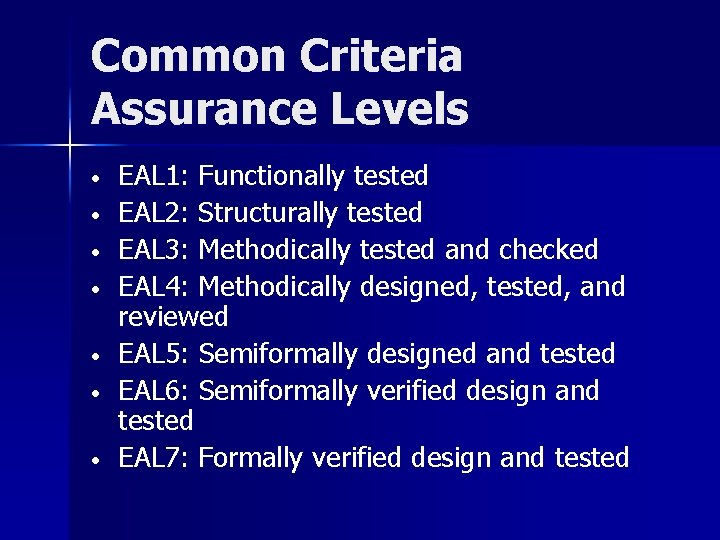
Common Criteria Assurance Levels • • EAL 1: Functionally tested EAL 2: Structurally tested EAL 3: Methodically tested and checked EAL 4: Methodically designed, tested, and reviewed EAL 5: Semiformally designed and tested EAL 6: Semiformally verified design and tested EAL 7: Formally verified design and tested

References n n n n n http: //www. argus-systems. com/product/white_paper/pitbull/oss/2. shtml http: //rr. sans. org/securitybasics/trusted_OS. php http: //www. sei. cmu. edu/str/descriptions/trusted_body. html http: //www. computerworld. com/cwi/story/0, 1199, NAV 47_STO 53293, 00. html http: //www. commoncriteria. org http: //www. securityhorizon. com/whitepapers/archives/tos. html http: //rr. sans. org/securitybasics/trusted_OS. php http: //www. nsa. gov/selinux/index. html http: //wwws. sun. com/software/solaris/trustedsolaris/ts_tech_faq/