Trusted Computing for the GRID Dirk Kuhlmann dirk
![Trusted Computing for the GRID Dirk Kuhlmann [dirk. kuhlmann@hp. com] Trusted Systems Lab, HPLabs, Trusted Computing for the GRID Dirk Kuhlmann [dirk. kuhlmann@hp. com] Trusted Systems Lab, HPLabs,](https://slidetodoc.com/presentation_image_h/20a6f55a16396ea289eb1aa78277b9a1/image-1.jpg)








- Slides: 20
![Trusted Computing for the GRID Dirk Kuhlmann dirk kuhlmannhp com Trusted Systems Lab HPLabs Trusted Computing for the GRID Dirk Kuhlmann [dirk. kuhlmann@hp. com] Trusted Systems Lab, HPLabs,](https://slidetodoc.com/presentation_image_h/20a6f55a16396ea289eb1aa78277b9a1/image-1.jpg)
Trusted Computing for the GRID Dirk Kuhlmann [dirk. kuhlmann@hp. com] Trusted Systems Lab, HPLabs, Bristol © 2004 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice

Platform security concerns for GRID Large number of dynamically managed nodes • − − − Reliably identify a particular node Get reliable information about runtime status Protect user data and programs OS and hardware in GRID scenarios • − − − Commercial ‘off the shelve’ elements to save costs Subjected to COTS vulnerabilities ‘Script kiddies’ and worms don’t care whether they attack a private platform or a GRID node Trusted platforms • − Next-generation hardware and software Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 2

Trusted Nodes as building blocks for Trusted Infrastructure • • • Are the IT systems on my network the ones I intended to be part of the infrastructure? Is the software and configuration on IT systems what they are intended it to be? Is the software I deploy on my IT systems going to behave as intended? Trusted Computing could become a foundational component to address the first two question. TC hardware is no silver bullet! • Secure product development must address the third issue. • Main challenges concern software, in particular OS! Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 3

Trusted Computing and HPLabs • Trusted Computing Platform Alliance - TCPA − Founded October 1999 − Compaq, HP, IBM, Intel, Microsoft − Created Embedded Security chip Specification v 1. 1 b • Trusted Computing Group - TCG − Founded April 2003 − Build on TCPA − Expands Trusted Computing to other platform categories and infrastructure • HPLabs held HP’s Technical Committee chair for TCPA and now for TCG. Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 4

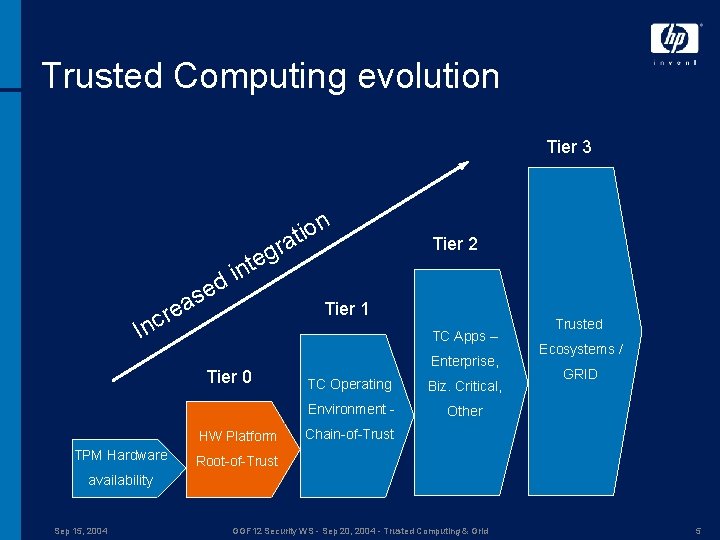
Trusted Computing evolution Tier 3 n d e s a e r g e t in Tier 2 Tier 1 Inc TC Apps – Tier 0 HW Platform TPM Hardware io t a r Enterprise, TC Operating Biz. Critical, Environment - Other Trusted Ecosystems / GRID Chain-of-Trust Root-of-Trust availability Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 5

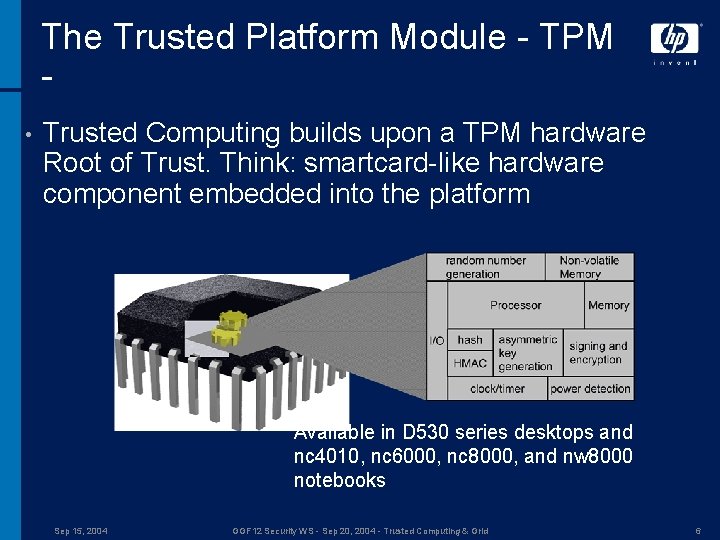
The Trusted Platform Module - TPM • Trusted Computing builds upon a TPM hardware Root of Trust. Think: smartcard-like hardware component embedded into the platform Available in D 530 series desktops and nc 4010, nc 6000, nc 8000, and nw 8000 notebooks Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 6

Main value-proposition for GRID today: platform authentication • With Trusted Computing Platforms, network resources can be restricted for access from approved devices as well as approved users • Access granted to devices authenticated using the Trusted Platform Module (TPM – or Embedded Security Chip) • To grant access to sensitive applications and services • To control access to file servers and databases • To control access from peers or remote clients through VPN and segment portions of the network Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 7

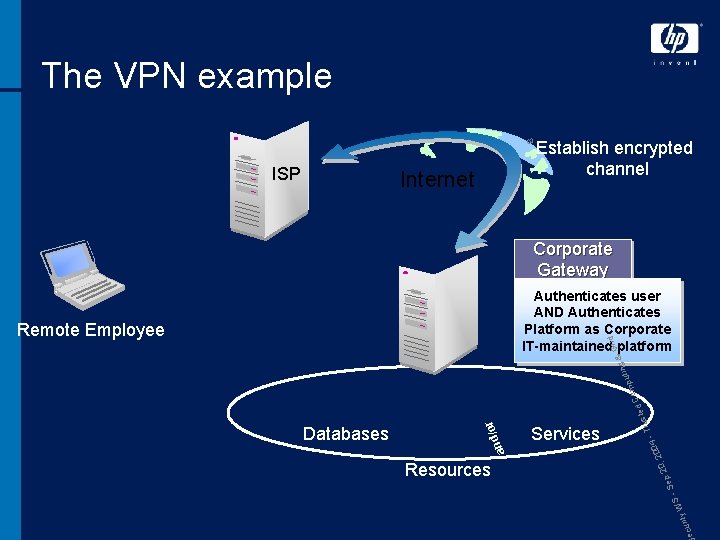
8 The VPN example ISP Internet Establish encrypted channel Corporate Gateway Authenticates user AND Authenticates Platform as Corporate IT-maintained platform - ste Tru S ity W r ecu Resources Services 004 0, 2 2 p - Se and Databases /or d. C om ing put &G rid Remote Employee

Authentication of users and devices User Authentication Device Authentication + Trusted Computing • Creates a Trusted Entity on the network − Provides enhanced network rights, roles, and responsibility − Can be introduced with no disruption to existing IT infrastructure − allows IT managers to dynamically assign granular access control • The device can also now be used as an authentication factor with: − Ease of Use – for the mobile professional − Reduced Total Cost of Ownership – for the IT department Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 9

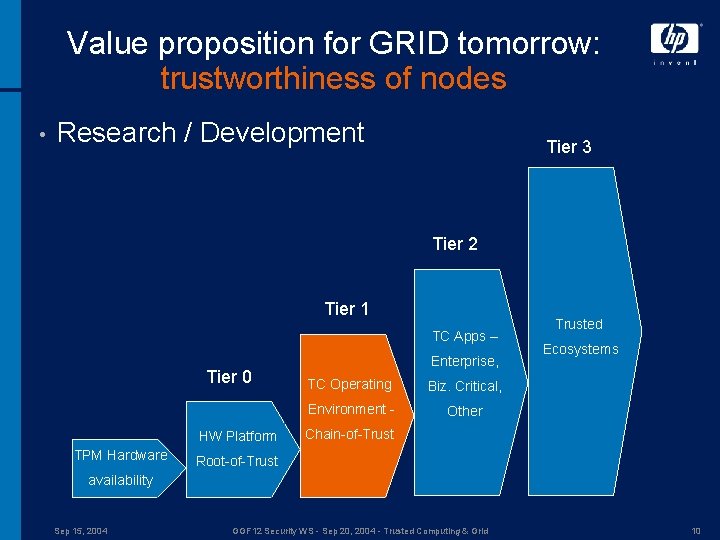
Value proposition for GRID tomorrow: trustworthiness of nodes • Research / Development Tier 3 Tier 2 Tier 1 TC Apps – Tier 0 HW Platform TPM Hardware Enterprise, TC Operating Biz. Critical, Environment - Other Trusted Ecosystems Chain-of-Trust Root-of-Trust availability Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 10

Trusted Node Requirements • Allow for device authentication • Monitor software integrity during boot-up and runtime • Keep node alive and manageable • Support standard operating systems • Current operating systems: − Integrity measurements as such do not enhance security − Typically not geared towards ‘keep alive’ Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 11

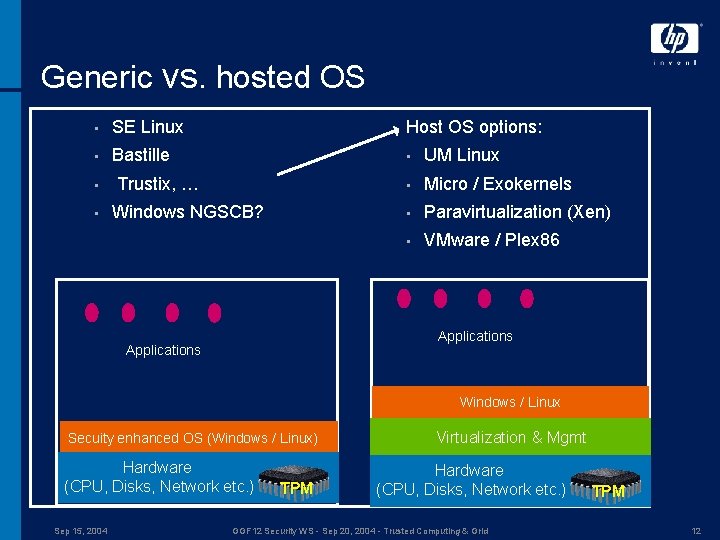
Generic vs. hosted OS • SE Linux Host OS options: • Bastille • UM Linux • Micro / Exokernels • Paravirtualization (Xen) • VMware / Plex 86 • • Trustix, … Windows NGSCB? Applications Windows / Linux Secuity enhanced OS (Windows / Linux) Hardware (CPU, Disks, Network etc. ) Sep 15, 2004 TPM Virtualization & Mgmt Hardware (CPU, Disks, Network etc. ) GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid TPM 12

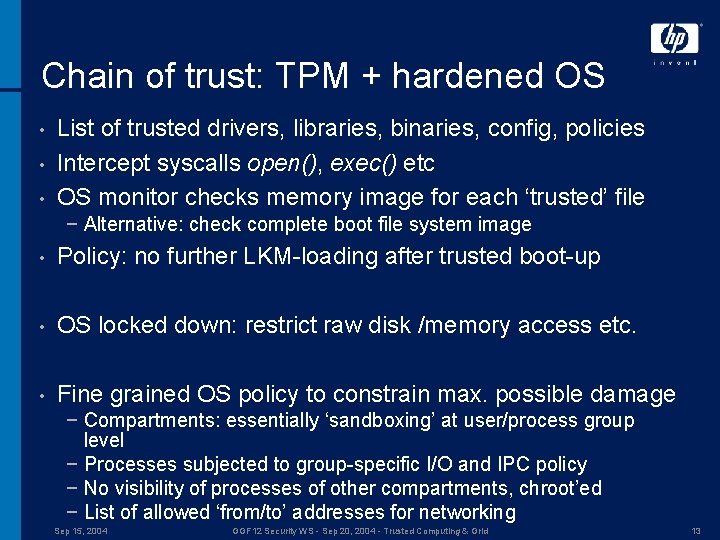
Chain of trust: TPM + hardened OS • • • List of trusted drivers, libraries, binaries, config, policies Intercept syscalls open(), exec() etc OS monitor checks memory image for each ‘trusted’ file − Alternative: check complete boot file system image • Policy: no further LKM-loading after trusted boot-up • OS locked down: restrict raw disk /memory access etc. • Fine grained OS policy to constrain max. possible damage − Compartments: essentially ‘sandboxing’ at user/process group level − Processes subjected to group-specific I/O and IPC policy − No visibility of processes of other compartments, chroot’ed − List of allowed ‘from/to’ addresses for networking Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 13

TPM + hardened host OS for UM-Linux • Use hardened OS as host OS − Host OS integrity check supported by TC hardware − Guest OS integrity checked by trusted SW in host OS • think tripwire • Guest OS launched inside host OS compartment − Guest OS ‘inherits’ compartment rules − network policy enforced outside the guest OS − can be restricted further, e. g. by netfilter on guest OS • Option: dedicated hosted instances − packet filtering, firewall local to platform or guest OS − monitor, audit, report Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 14

Challenges • Weak TC notion of ‘expected behaviour’ − SW integrity checking (essentially signed binaries) • Could be extended to binary + policy − No notion of actual runtime behaviour • Borrow concepts: anomaly detection, proof carrying code • Further extension: runtime + policy + runtime signature • ‘Contractual Programming’? ‘Commpacts’? • • Management overhead: is it worth it? Main concern: size of Trusted Computing Base − Huge TCB for User Mode Linux scenario − Who does the validation for OSS? − Favours microkernel/virtualization layer, minimal code base Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 15

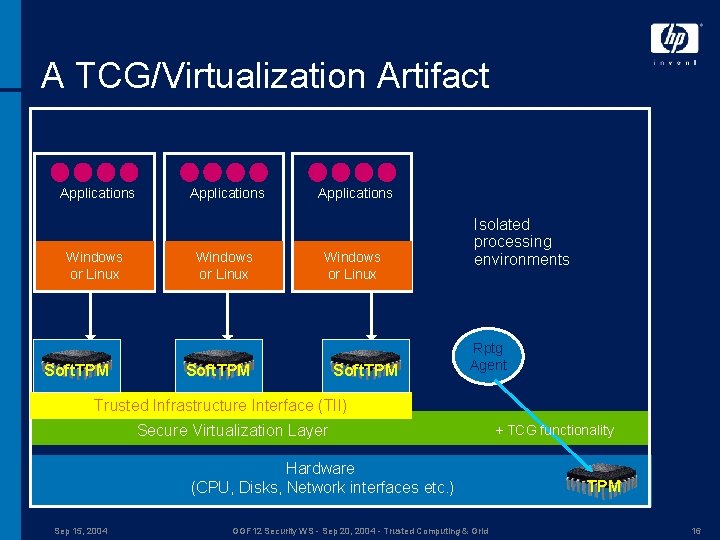
A TCG/Virtualization Artifact Applications Windows or Linux Soft. TPM Isolated processing environments Rptg Agent Trusted Infrastructure Interface (TII) Secure Virtualization Layer Hardware (CPU, Disks, Network interfaces etc. ) Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid + TCG functionality TPM 16

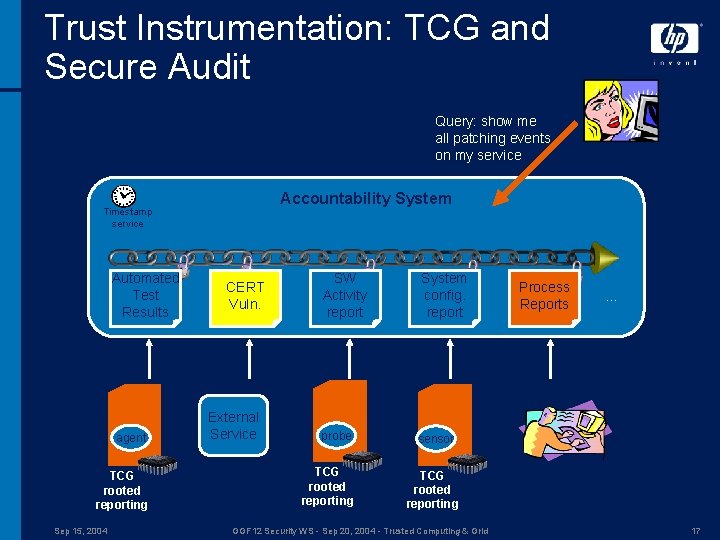
Trust Instrumentation: TCG and Secure Audit Query: show me all patching events on my service Accountability System Timestamp service Automated Test Results agent TCG rooted reporting Sep 15, 2004 CERT Vuln. External Service SW Activity report System config. report probe sensor TCG rooted reporting Process Reports … TCG rooted reporting GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 17

Trusted Virtualization Layer: Proprietary or Public/Open? • There is a lot of effort going into proprietary solutions, esp. Windows NGSCB … • So far, little complementary efforts in the Open Source field − General scepticism about Trusted Computing approach − Problem space beyond ‘typical’ OSS developer community • Controversial discussion about OSS security in general • Co-ordinated effort for Open Source is necessary − International approach − Academia, industry, and OSS communities − Validation as important as design & implementation ! Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 18

Conclusions • Today’s TCG hardware can be the stepping stone for innovative security capabilities. • Trusted Computing is a journey and we are seeing the first technology components appear on the market • It will be a long and difficult way towards trusted GRID nodes and infrastructure. The main challenges are in the area of software: operating systems and management. • Trustworthiness requires peer-review, replicable validation: Open Trusted Computing Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 19

HP logo Sep 15, 2004 GGF 12 Security WS - Sep 20, 2004 - Trusted Computing & Grid 20