Trust Region Based Adversarial Attack on Neural Networks

Trust Region Based Adversarial Attack on Neural Networks CVPR 2019 Poster

Outline • What is trust region algorithm and how does it work ? • How to change adversarial attack in to an optimization problem ? • Experiments
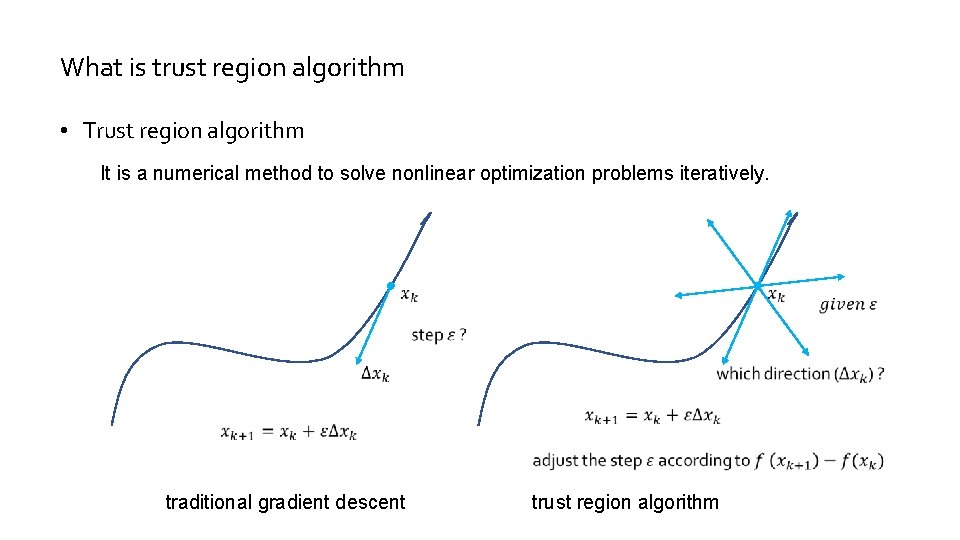
What is trust region algorithm • Trust region algorithm It is a numerical method to solve nonlinear optimization problems iteratively. traditional gradient descent trust region algorithm
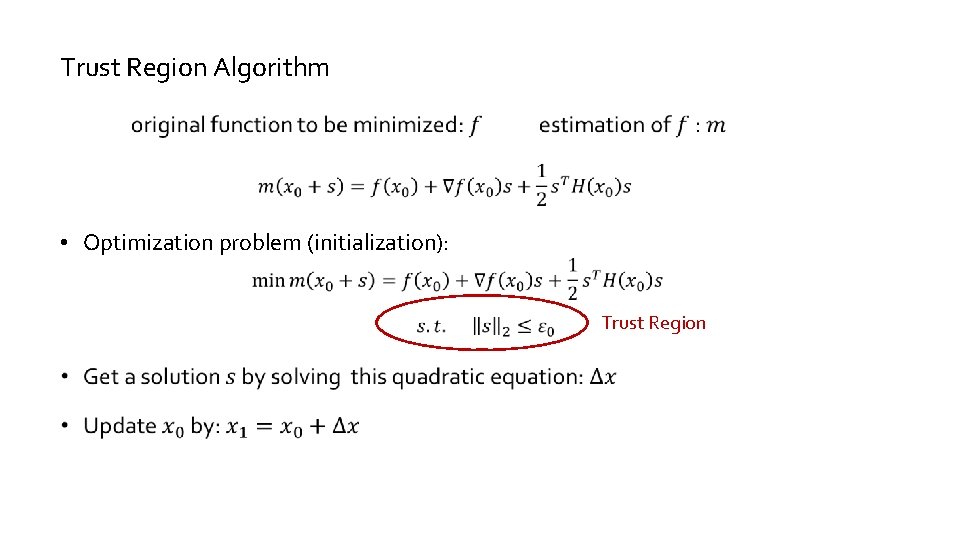
Trust Region Algorithm • Optimization problem (initialization): Trust Region
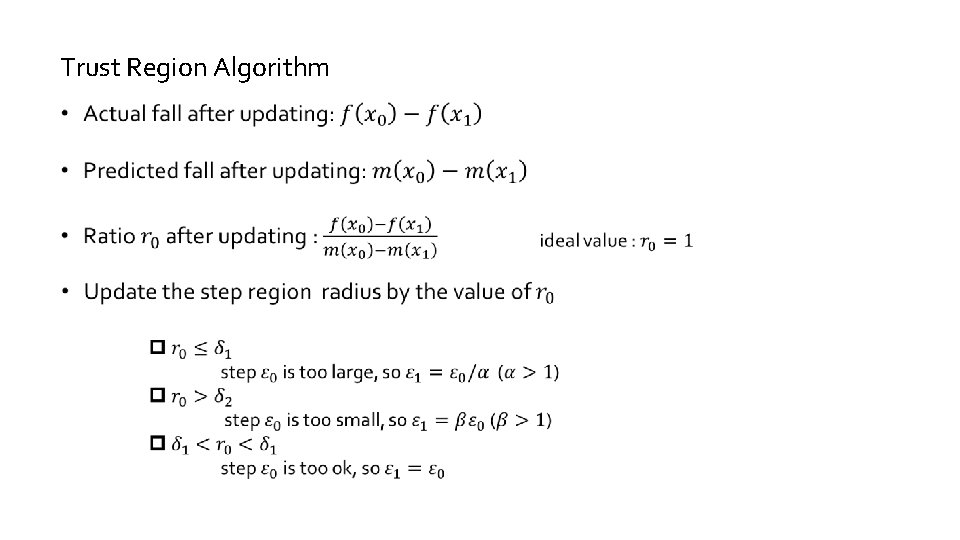
Trust Region Algorithm
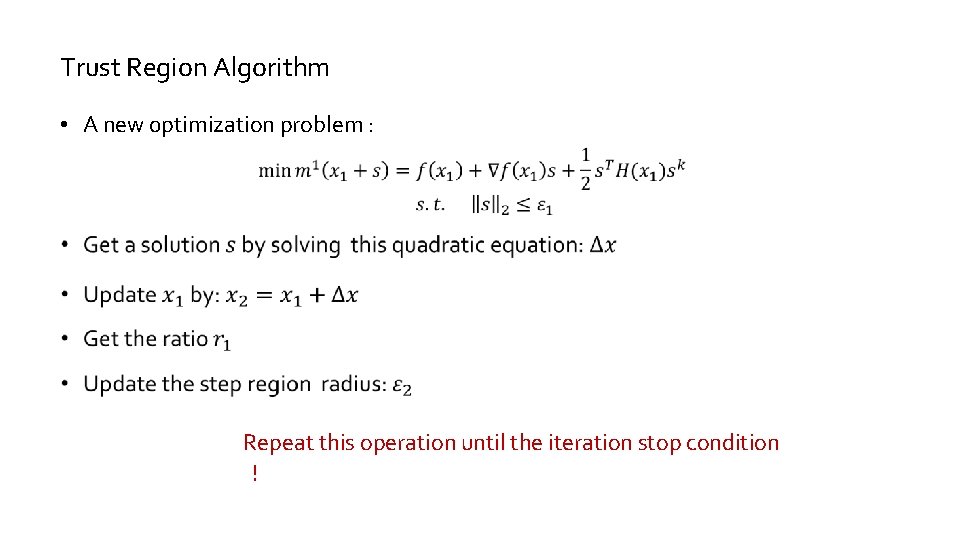
Trust Region Algorithm • A new 0 ptimization problem : Repeat this operation until the iteration stop condition !
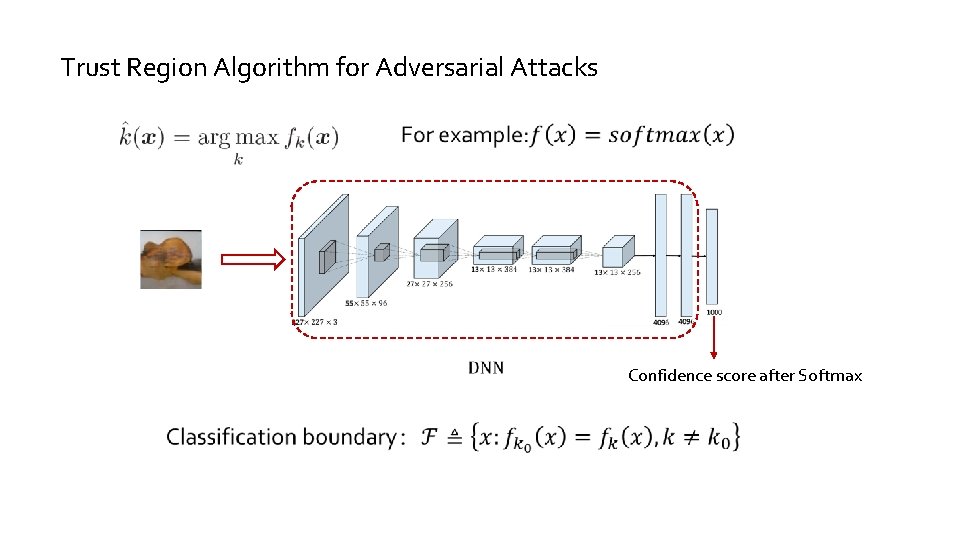
Trust Region Algorithm for Adversarial Attacks Confidence score after Softmax
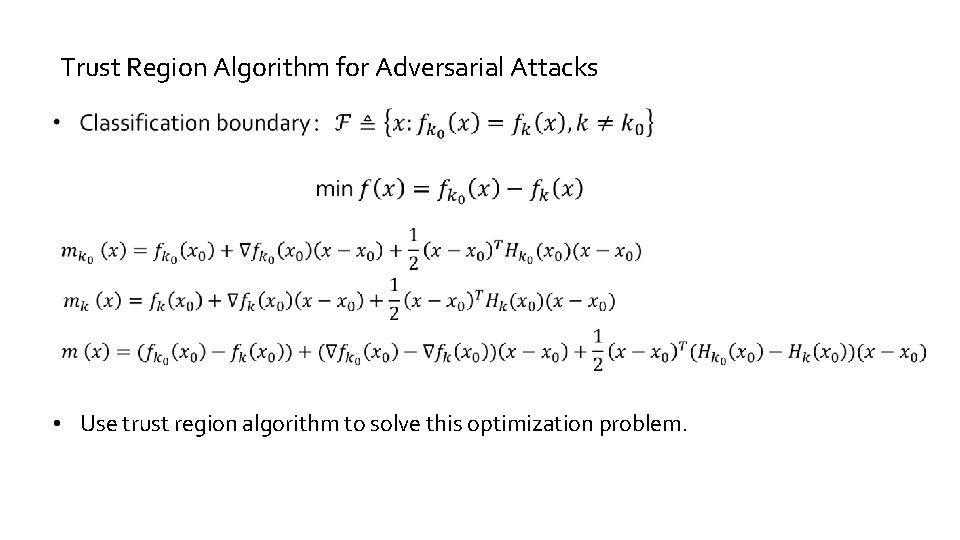
Trust Region Algorithm for Adversarial Attacks • Use trust region algorithm to solve this optimization problem.
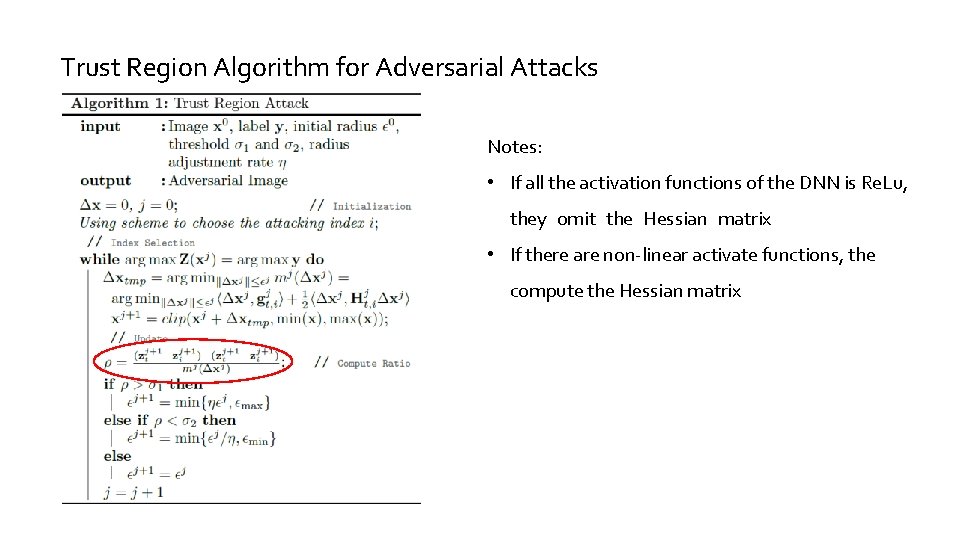
Trust Region Algorithm for Adversarial Attacks Notes: • If all the activation functions of the DNN is Re. Lu, they omit the Hessian matrix • If there are non-linear activate functions, the compute the Hessian matrix
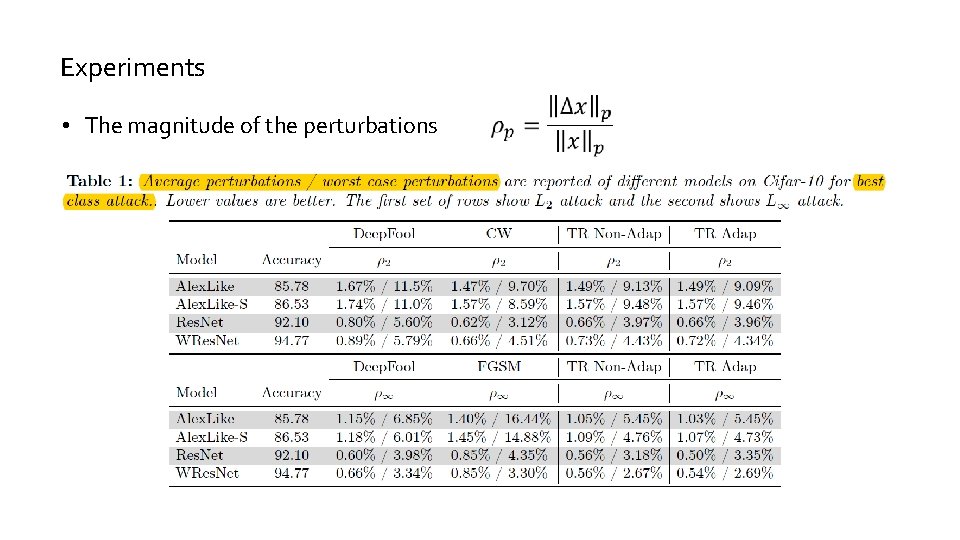
Experiments • The magnitude of the perturbations
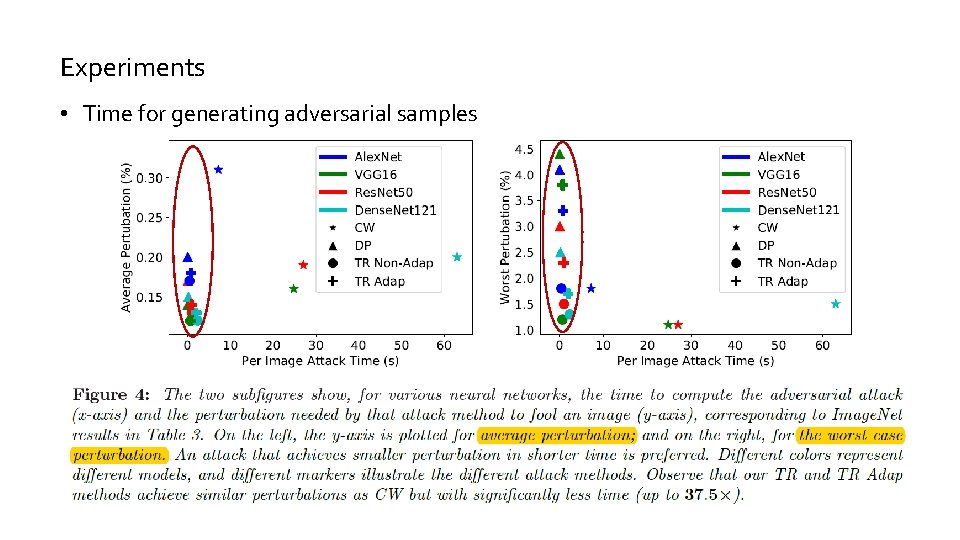
Experiments • Time for generating adversarial samples
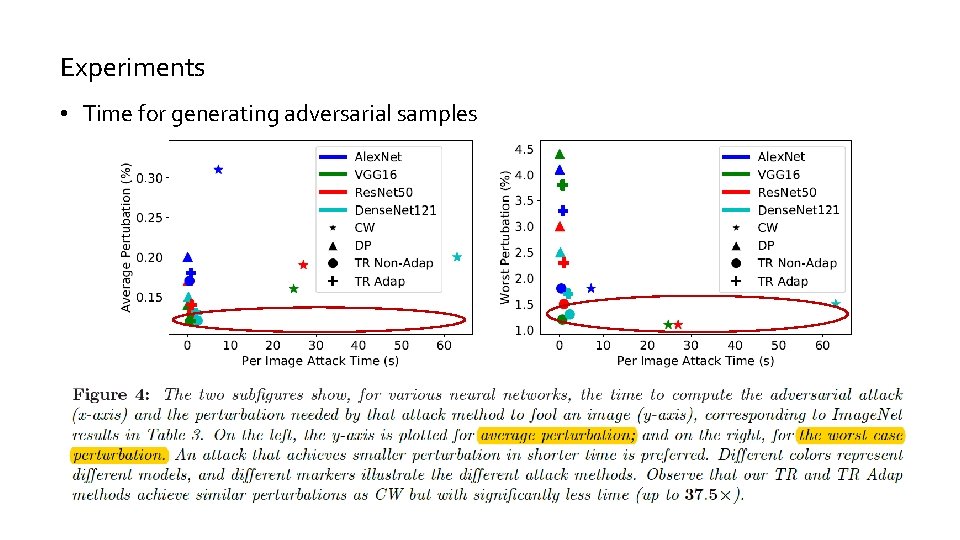
Experiments • Time for generating adversarial samples
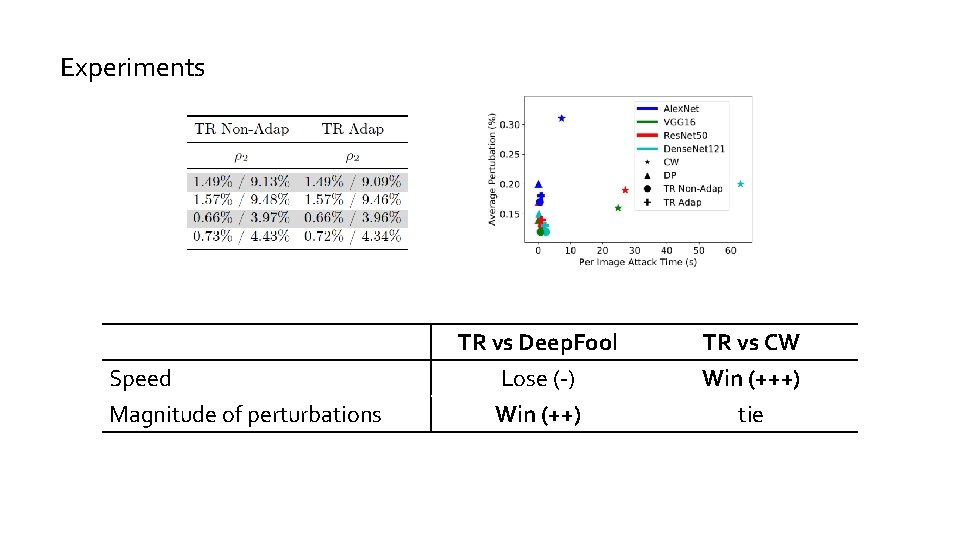
Experiments Speed Magnitude of perturbations TR vs Deep. Fool Lose (-) Win (++) TR vs CW Win (+++) tie
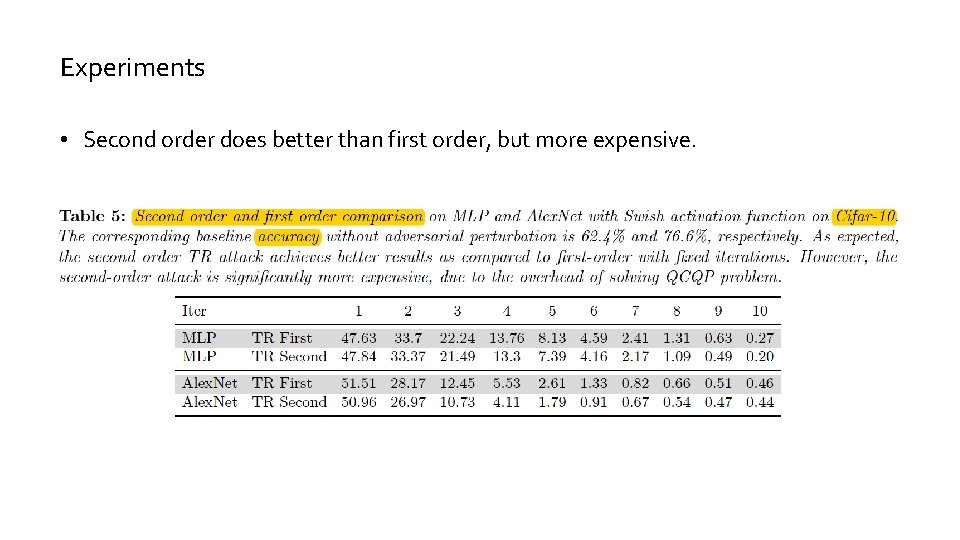
Experiments • Second order does better than first order, but more expensive.

Conclusion • This work casts the adversarial attack problem into the optimization framework of TR methods. • TR-based attack methods can adaptively choose the perturbation magnitude in every iteration. • TR-based attack method can easily be extended to second-order TR attacks.

Comments + This method can generate adversarial samples quickly and efficiently with very small perturbations + Maybe traditional numerical optimization methods are appropriate for adversarial attacks - Little novelty - Hessian computation is expensive - Bad writing
- Slides: 16