Trust Boundary Exploitation State of the Exploit Matt

Trust Boundary Exploitation State of the Exploit Matt Miller / mmiller@leviathansecurity. com Vulnerability

What is the state of the exploit? § Where do generic exploitation techniques stand in 2008? Ø Formidable mitigations exist (ASLR, NX, GS) Ø Many techniques impractical or impossible Ø Exploits are more reliant on vuln-specific qualities § How can we evaluate the relevance & feasibility of current & future techniques? Ø Exploitability analysis

Exploitability analysis § Studying the qualities that influence exploitation Ø If a vulnerability exists, how exploitable would it be? § Research directions Ø Exploitation properties Ø Simulating exploitation
Exploitation Properties

What are exploitation properties? § Specific qualities that enable or inhibit exploitation techniques Ø Objectively derived from a program Ø Vulnerability independent § Intuitively known, but not formally defined Ø Exploits have always relied on exploitation properties

Relating to exploitation techniques § Exploitation techniques have pre-conditions that must be satisfied Ø SEH overwrite must be able to overwrite EH record § Exploitation properties help determine the satisfiability of those pre-conditions Ø Function called in EH scope == TRUE
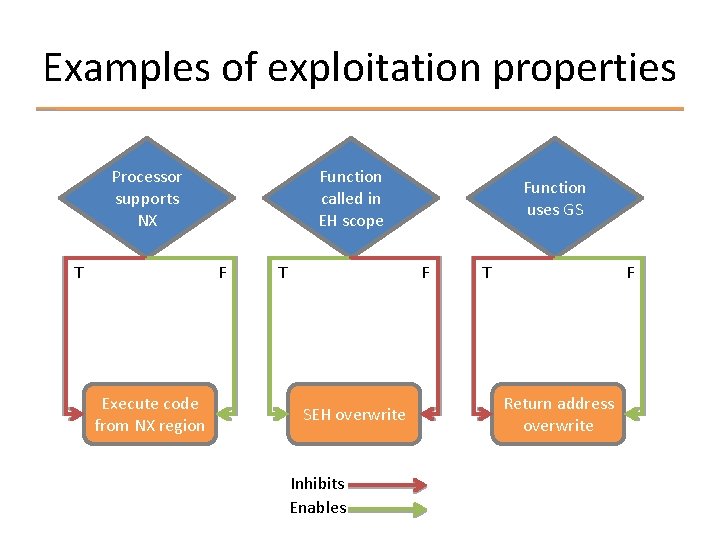
Examples of exploitation properties Processor supports NX T Function called in EH scope F Execute code from NX region T Function uses GS F SEH overwrite Inhibits Enables T F Return address overwrite
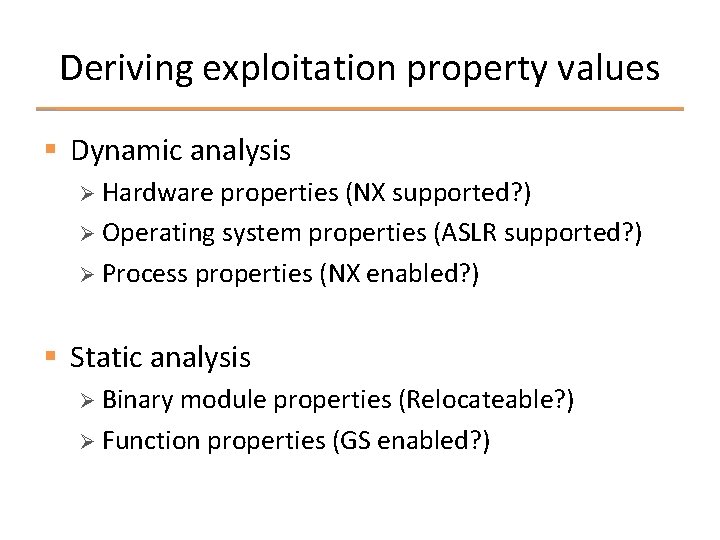
Deriving exploitation property values § Dynamic analysis Ø Hardware properties (NX supported? ) Ø Operating system properties (ASLR supported? ) Ø Process properties (NX enabled? ) § Static analysis Ø Binary module properties (Relocateable? ) Ø Function properties (GS enabled? )

Case study: MS 07 -017 (ANI) § Animated cursor vulnerability found by Alexander Sotirov in late 2006 Ø Stack-based buffer overflow § First highly exploitable issue to affect Vista § Why was it so exploitable?
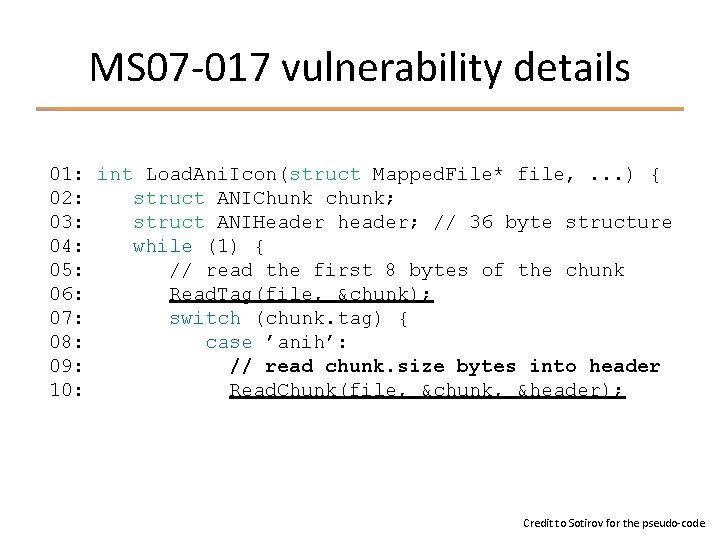
MS 07 -017 vulnerability details 01: int Load. Ani. Icon(struct Mapped. File* file, . . . ) { 02: struct ANIChunk chunk; 03: struct ANIHeader header; // 36 byte structure 04: while (1) { 05: // read the first 8 bytes of the chunk 06: Read. Tag(file, &chunk); 07: switch (chunk. tag) { 08: case ’anih’: 09: // read chunk. size bytes into header 10: Read. Chunk(file, &chunk, &header); Credit to Sotirov for the pseudo-code
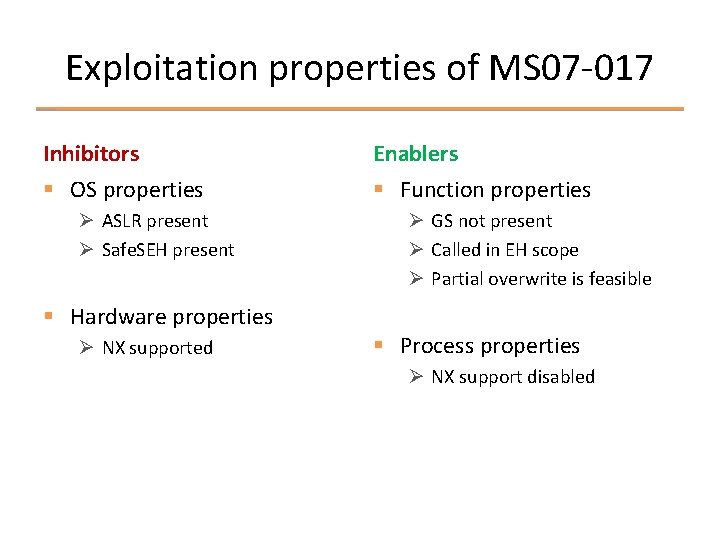
Exploitation properties of MS 07 -017 Inhibitors Enablers § OS properties § Function properties Ø ASLR present Ø Safe. SEH present § Hardware properties Ø NX supported Ø GS not present Ø Called in EH scope Ø Partial overwrite is feasible § Process properties Ø NX support disabled

Statically detecting MS 07 -017 § MS 07 -017 could have been found with the help of exploitability analysis § Find instances of code enabling reliable exploitation techniques Ø No GS, EH scope, partial overwrite feasible, etc § Resultant set would include the function containing the ANI vulnerability Ø Vulnerability analysis can narrow this set

Automatically assessing exploitability § Recap Ø Exploitation techniques have pre-conditions that must be satisfied Ø Exploitation properties provide objective values for these pre-conditions § How can we better assess exploitability with this information?
Simulated Exploitation
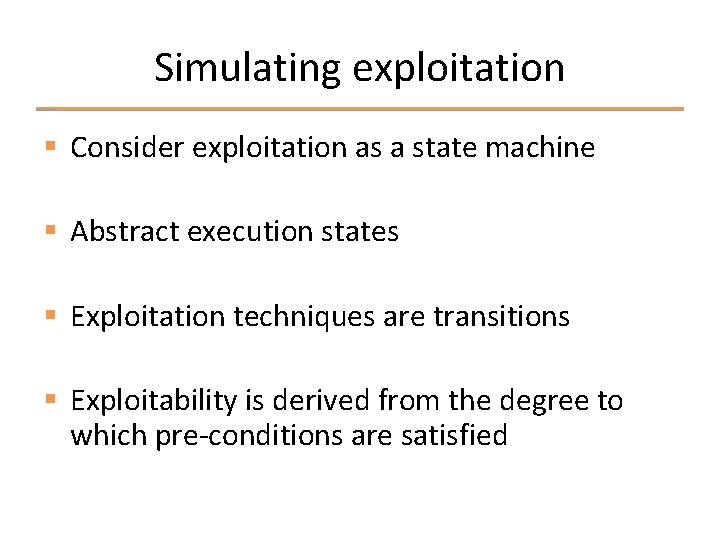
Simulating exploitation § Consider exploitation as a state machine § Abstract execution states § Exploitation techniques are transitions § Exploitability is derived from the degree to which pre-conditions are satisfied
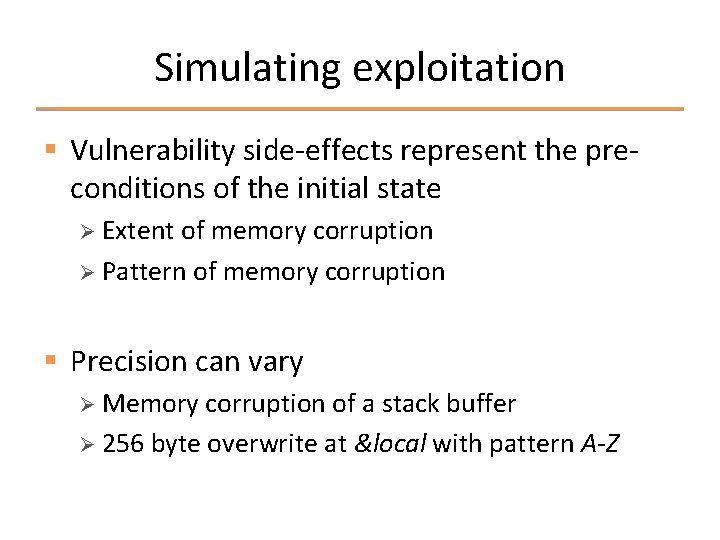
Simulating exploitation § Vulnerability side-effects represent the preconditions of the initial state Ø Extent of memory corruption Ø Pattern of memory corruption § Precision can vary Ø Memory corruption of a stack buffer Ø 256 byte overwrite at &local with pattern A-Z
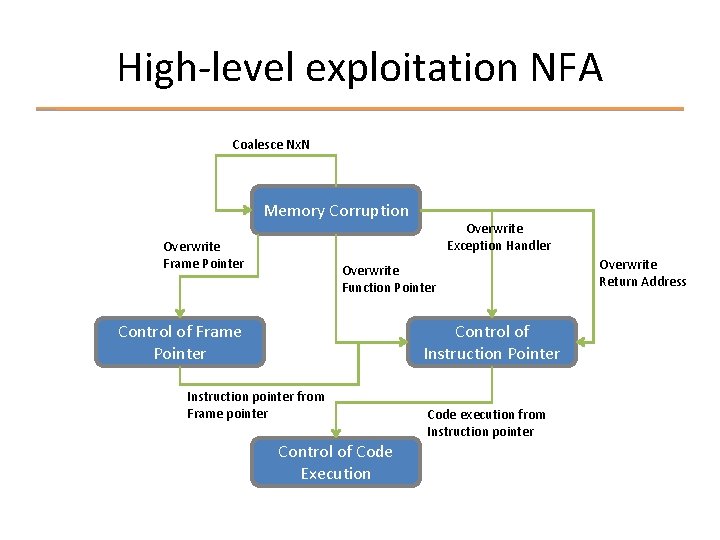
High-level exploitation NFA Coalesce Nx. N Memory Corruption Overwrite Frame Pointer Overwrite Exception Handler Overwrite Function Pointer Control of Frame Pointer Control of Instruction Pointer Instruction pointer from Frame pointer Control of Code Execution Code execution from Instruction pointer Overwrite Return Address
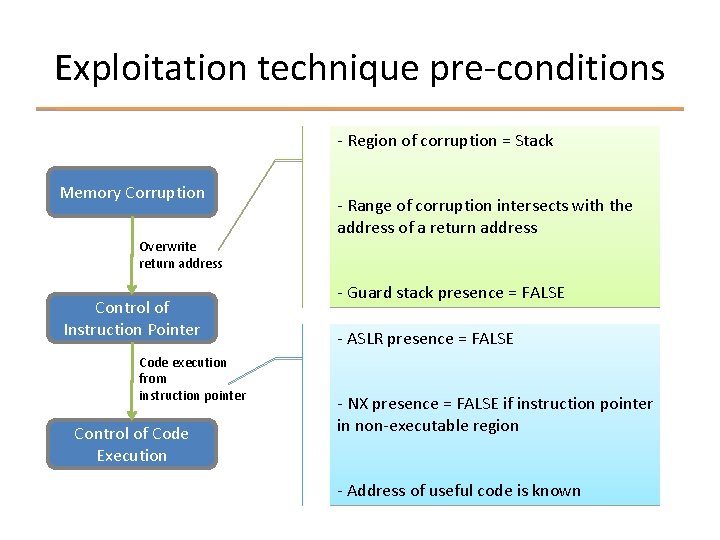
Exploitation technique pre-conditions - Region of corruption = Stack Memory Corruption Overwrite return address Control of Instruction Pointer Code execution from instruction pointer Control of Code Execution - Range of corruption intersects with the address of a return address - Guard stack presence = FALSE - ASLR presence = FALSE - NX presence = FALSE if instruction pointer in non-executable region - Address of useful code is known
Conclusion
Uses for exploitability analysis § Identify regions of code that may be highly exploitable given the presence of a vulnerability Ø Program risk assessment § Evaluate the effectiveness of exploitation techniques & mitigations § Automatic exploit generation using postconditions from simulated exploitation Ø Unlikely to compete with human talent
Future work § Research additional exploitation properties § Further develop analysis tools Ø Dynamic analysis of hardware, OS, and process state § Further develop exploitation simulator Ø Basic exploit generator using post-conditions
Thanks! Trust Boundary Exploitation Vulnerability Additional reading on exploitation properties http: //uninformed. org/? v=9&a=4
- Slides: 22