Troubleshooting Security Issues Troubleshoot Identity and Access Issues

Troubleshooting Security Issues • • • Troubleshoot Identity and Access Issues Troubleshoot Attacks Troubleshoot Other Security Issues Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 1
Authentication Issues • • • First determine if the problem is truly authentication and not some other problem with the cloud network, the device, or the application. See if someone else can authenticate. If no one can authenticate by using one method, then see if users can authenticate by using some other method. Also try, if available, a different authentication protocol, such as Kerberos, NTLM, smart card/token, MS-CHAP v 2 (for remote access), and more. Check the Event Viewer logs or error messages to see if there is any indication of the problem. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 2
Authorization Issues Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 3

Federation and SSO Issues There are some potential issues with SSO and federation that you need to consider before implementing these systems. • How the system will provision and de-provision user accounts. • How a user is allowed to reset their passwords. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 4
Certificate Issues Issue Description Unencrypted credentials Credentials are sent over the network unencrypted, or they are stored in cleartext form. Certificate issues Digital certificates are invalid, insecure, or non-functional. Key management issues Encryption keys are inaccessible to authorized personnel or accessible to unauthorized personnel. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 5
Incorrect Identity and Access Hardening Settings • • Personnel: The most common use for IAM is to define identities for organizational employees. Likewise, personnel identities are among the most popular attack vectors. Endpoints: The devices that people use to gain legitimate access to your network are varied and often difficult to account for in an IAM system. This is especially true of mobile devices like smartphones, tablets, and laptops. Software: Like servers, applications and services can be uniquely identified in the organization through digital certificates. One unique issue with applications is how to determine which other entities are allowed to run certain apps. Roles: Roles support the identities of various assets by defining the resources an asset has permission to access based on the function that asset fulfills. Role-based identity can have poorly defined roles that can lead to privilege creep. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 6

Guidelines for Troubleshooting Identity and Access Issues • • • When users experience authentication issues, first try to determine if the issue is related to something else instead. When an issue occurs, determine if it affects other users or just one. Consider how the system will provision and de-provision user accounts when using SSO and federation before implementing these systems. Consider how users will reset their passwords when using SSO before implementing these systems. Consider how non-user assets in your organization fit into your IAM scheme. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 7
Activity: Troubleshooting Identity and Access Issues • Your manager at Rudison Technologies poses different scenarios to you and asks what troubleshooting steps you would take to troubleshoot identity and access issues. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 8
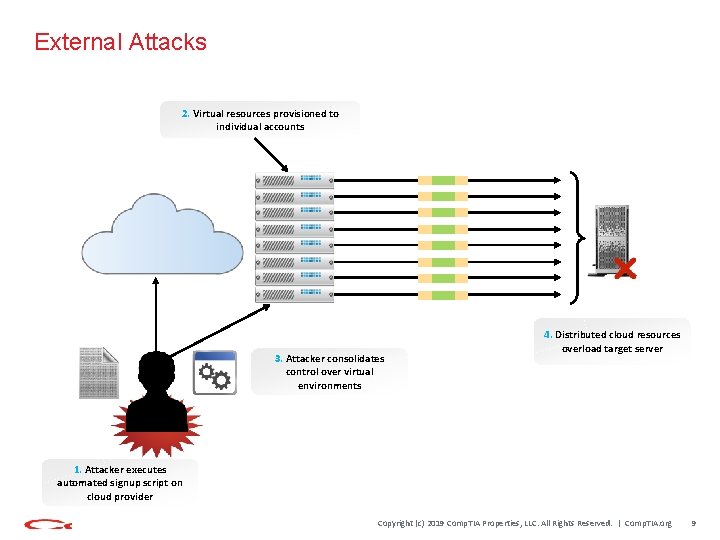
External Attacks 2. Virtual resources provisioned to individual accounts 3. Attacker consolidates control over virtual environments 4. Distributed cloud resources overload target server 1. Attacker executes automated signup script on cloud provider Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 9
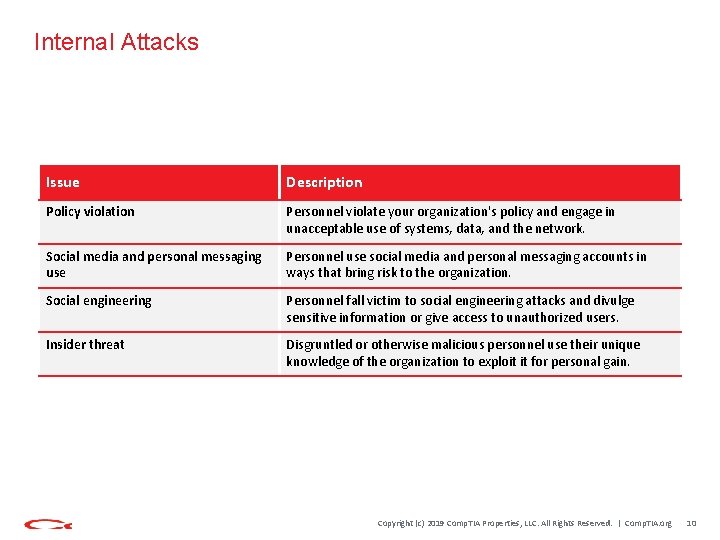
Internal Attacks Issue Description Policy violation Personnel violate your organization's policy and engage in unacceptable use of systems, data, and the network. Social media and personal messaging use Personnel use social media and personal messaging accounts in ways that bring risk to the organization. Social engineering Personnel fall victim to social engineering attacks and divulge sensitive information or give access to unauthorized users. Insider threat Disgruntled or otherwise malicious personnel use their unique knowledge of the organization to exploit it for personal gain. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 10
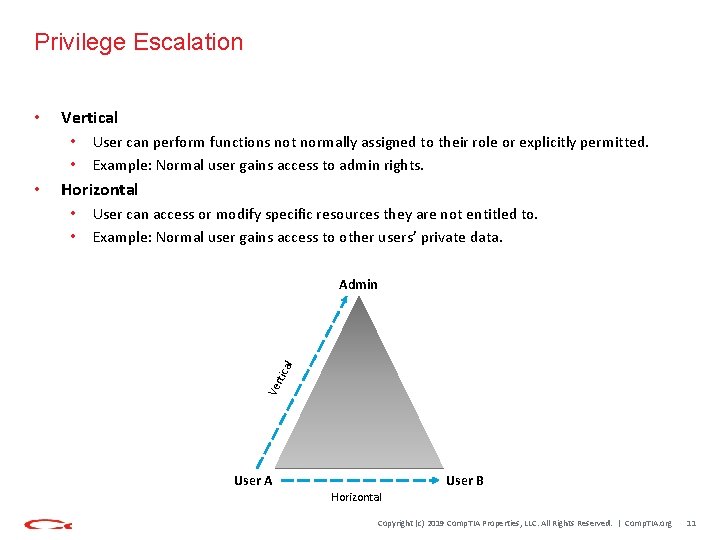
Privilege Escalation Vertical • • Horizontal User can access or modify specific resources they are not entitled to. Example: Normal user gains access to other users’ private data. Admin al • • rtic • User can perform functions not normally assigned to their role or explicitly permitted. Example: Normal user gains access to admin rights. Ve • User A User B Horizontal Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 11
Attack Vectors Related to Configuration Although the paths that attackers take are diverse, there are three general elements that can contribute to an attack vector: • Vulnerabilities: Attackers will almost always search for holes within your systems and networks. • Exploits: These almost always depend on vulnerabilities to be effective. When the gap in security is identified, the attacker can launch a tool or utility to take advantage of that gap. • Techniques: An attack's technique provides more detail about the path it takes, as well as how it operates. It can also help categorize the effects of an exploit payload. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 12

Guidelines for Troubleshooting Attacks • • Consider familiarizing yourself with different types of attacks on clouds so that you will be better prepared to recognize and troubleshoot them. Remember that attacks don't come from outside your organization only; they can come from inside your organization as well. User accounts can be a source of multiple attacks, so ensure you have good user management in place to mitigate this. Understand the vectors that attackers take as this is a crucial step in security because it helps the practitioner identify the how of an attack. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 13
Activity: Troubleshooting Attacks • Your manager at Rudison Technologies poses different scenarios to you and asks what troubleshooting steps you would take to troubleshoot attack issues. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 14
Unencrypted Communication Some steps to help encrypt communications are: • Ensure that you are using secure remote protocols like SSH. • Ensure that you are using SSL/TLS to secure web-based communications. • Ensure that users know not to store passwords in unencrypted text, spreadsheet, or database files. • Ensure that any custom apps you develop employ encryption for data at rest, in transit, and in use. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 15
Unauthorized Physical Access Physical Resource Vulnerabilities Building and grounds • • Location Physical access control Devices • • Servers Laptops and tablets Mobile phones Other wireless devices Communications • • • Telecommunications Service providers Wireless cells Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 16
Unencrypted Data Unencrypted data is vulnerable regardless of where it is located. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 17

Weak or Obsolete Security Technologies • • Securing your environment is a good accomplishment but only if it is done well and maintained. When implementing security, ensure that you are following best practices and using settings that provide adequate security. Even when you implement good security, you may still not maintain the level of protection you want. You need to periodically review your security settings and also review new vulnerabilities so that you can then implement changes to keep your environment safe. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 18

Insufficient Security Controls and Processes • • Having insufficient security controls can leave your environment open to attacks. These can range from physical controls such as locks, to technical controls such as anti-malware or firewalls. Having insufficient security processes can leave your environment open to attacks even if you have good security controls in place. Security processes include items such as security governance, policy management, awareness and education, identity and access management, vulnerability management, and incident response. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 19

Tunneling or Encryption Issues • • • Tunneling with a protocol such as SSH, or using a VPN, can provide access to your cloud from another network. While these provide a useful service they can also create potential issues. Tunneling can be used to "sneak through" a firewall by wrapping a protocol that the firewall would normally block inside a protocol that the firewall does not block. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 20
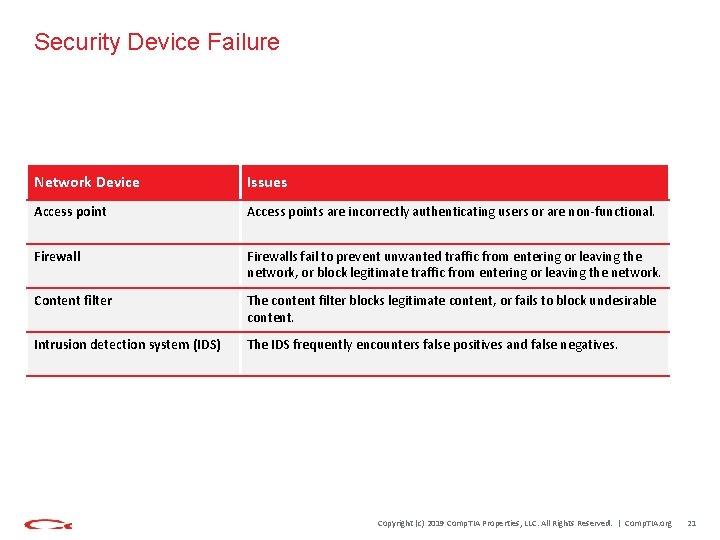
Security Device Failure Network Device Issues Access points are incorrectly authenticating users or are non-functional. Firewalls fail to prevent unwanted traffic from entering or leaving the network, or block legitimate traffic from entering or leaving the network. Content filter The content filter blocks legitimate content, or fails to block undesirable content. Intrusion detection system (IDS) The IDS frequently encounters false positives and false negatives. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 21

Guidelines for Troubleshooting Other Security Issues • • Always encrypt your communications to prevent attackers from gaining important information like account passwords. Remember that your physical security is as important as your virtual security as it will keep intruders from gaining access to your organization and your staff. Remember that unencrypted data is vulnerable regardless of where it is located. Ensure you are implementing adequate security settings when you secure your environment so that you have the level of security you require. Review your security settings and new vulnerabilities on a periodic basis to discover new attack vectors that you can then implement security for. Ensure that your security controls are adequate for your environment to avoid additional security issues. Ensure that you implement adequate security controls to further protect your organization and avoid security or potential legal issues. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 22
Activity: Troubleshooting Other Security Issues • Your manager at Rudison Technologies poses different scenarios to you and asks what troubleshooting steps you would take to troubleshoot other security issues. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 23

Reflective Questions 1. What types of attacks have you had to deal with in your environment? How did you detect them and stop them? 2. What other security issues have you identified in your environment? Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 24
- Slides: 24