Troubleshooting Federation AD FS 2 0 and More

Troubleshooting Federation, AD FS 2. 0, and More… John Craddock, Federation and Security Architect, XTSeminars

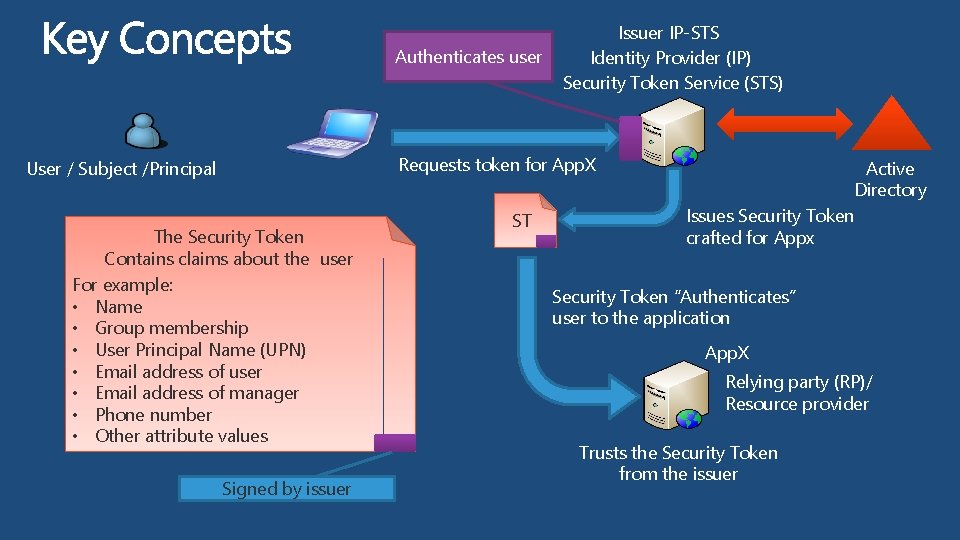
Authenticates user Issuer IP-STS Identity Provider (IP) Security Token Service (STS) Requests token for App. X User / Subject /Principal The Security Token Contains claims about the user For example: • Name • Group membership • User Principal Name (UPN) • Email address of user • Email address of manager • Phone number • Other attribute values Signed by issuer ST Active Directory Issues Security Token crafted for Appx Security Token “Authenticates” user to the application App. X Relying party (RP)/ Resource provider Trusts the Security Token from the issuer
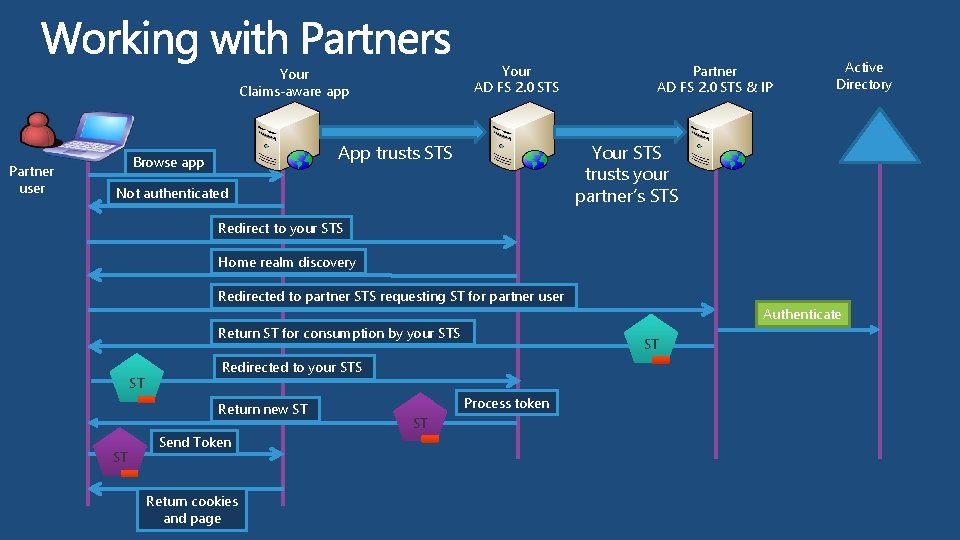
Your AD FS 2. 0 STS Your Claims-aware app Partner user App trusts STS Browse app Partner AD FS 2. 0 STS & IP Active Directory Your STS trusts your partner’s STS Not authenticated Redirect to your STS Home realm discovery Redirected to partner STS requesting ST for partner user Return ST for consumption by your STS ST ST ST Redirected to your STS Return new ST Send Token Return cookies and page Process token ST Authenticate

demo Federation in action
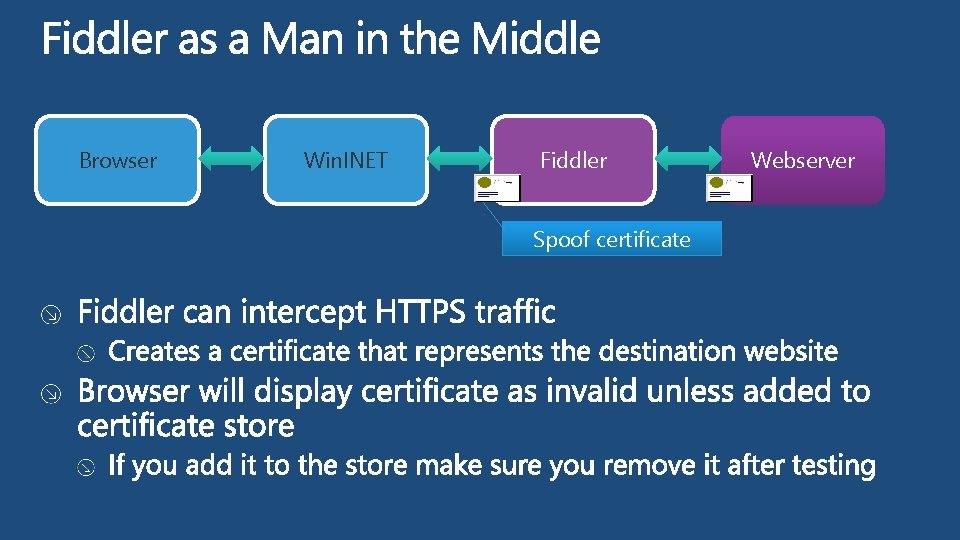
Browser Win. INET Fiddler Spoof certificate Webserver
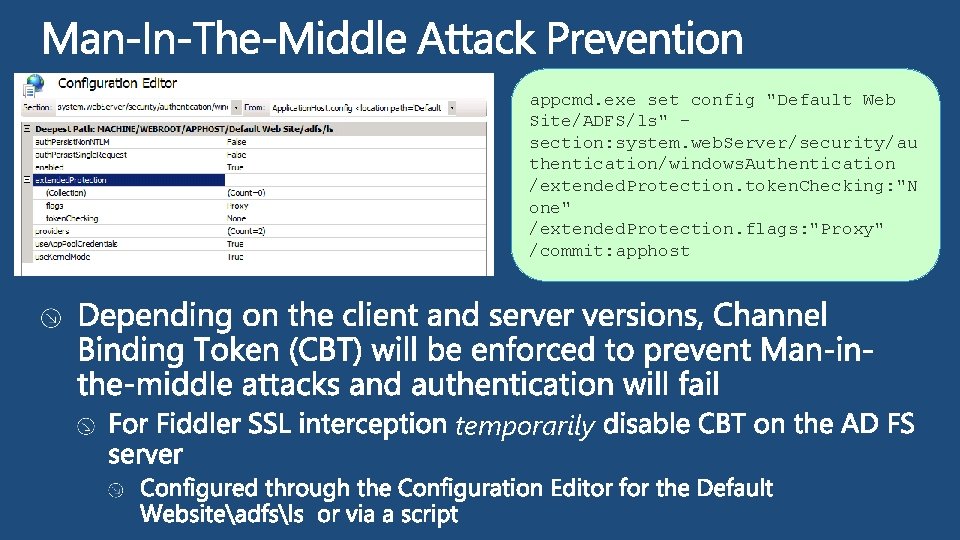
appcmd. exe set config "Default Web Site/ADFS/ls" section: system. web. Server/security/au thentication/windows. Authentication /extended. Protection. token. Checking: "N one" /extended. Protection. flags: "Proxy" /commit: apphost temporarily
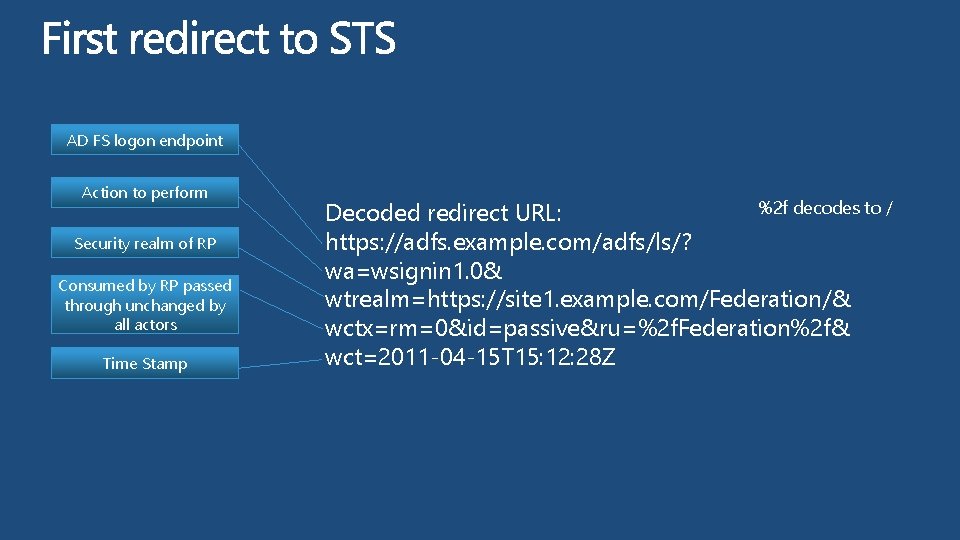
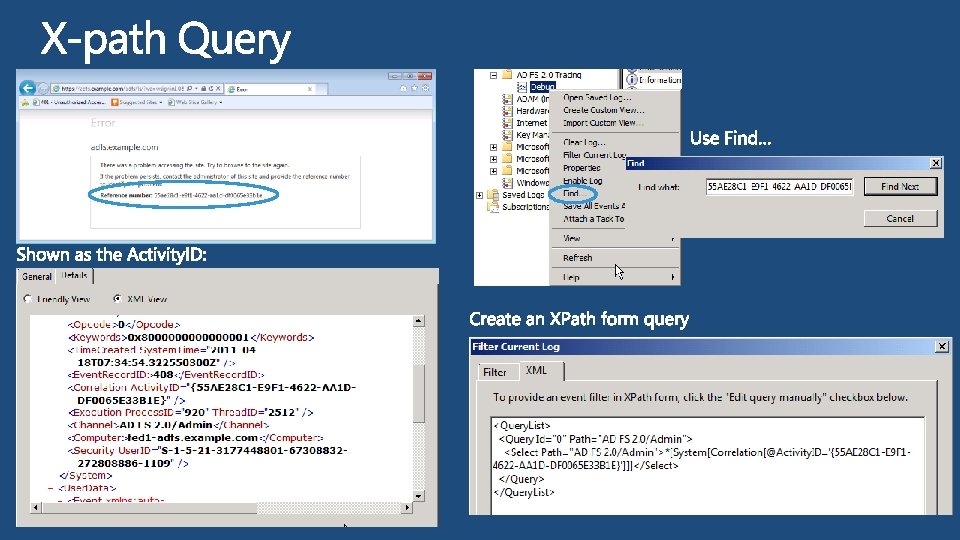
AD FS logon endpoint Action to perform Security realm of RP Consumed by RP passed through unchanged by all actors Time Stamp %2 f decodes to / Decoded redirect URL: https: //adfs. example. com/adfs/ls/? wa=wsignin 1. 0& wtrealm=https: //site 1. example. com/Federation/& wctx=rm=0&id=passive&ru=%2 f. Federation%2 f& wct=2011 -04 -15 T 15: 12: 28 Z

Begins / ends with saml: Assertion Hidden form with POST method POST back URL defined via RP configuration in ADFS SAML claims Signature X. 509 Certificate of signing party (includes public key) Unchanged since initial request

AD FS

Application

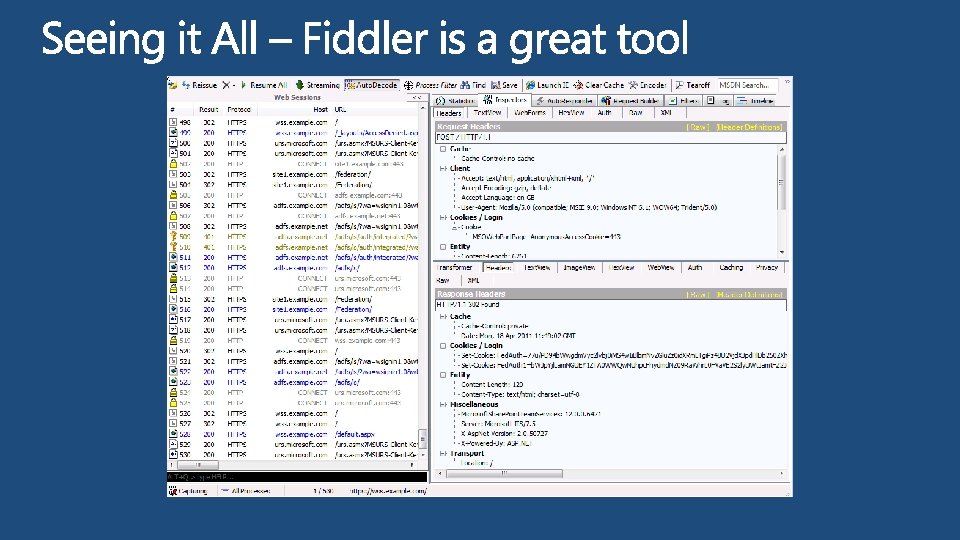
demo Tracing with Fiddler

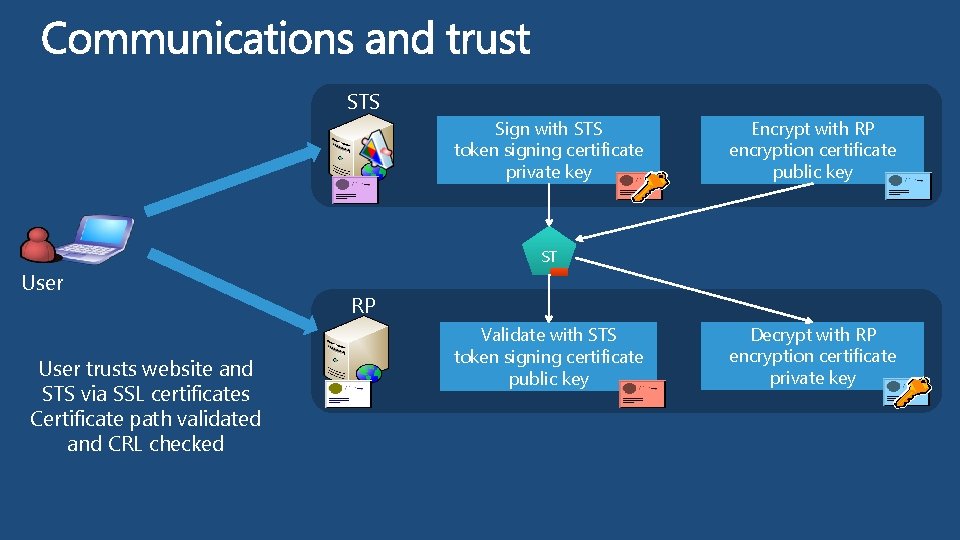
STS Sign with STS token signing certificate private key Encrypt with RP encryption certificate public key ST User trusts website and STS via SSL certificates Certificate path validated and CRL checked RP Validate with STS token signing certificate public key Decrypt with RP encryption certificate private key

Run “certutil –viewstore –v My > cert. txt” and look for Keyspec=0 if the certificate is a version 3 template

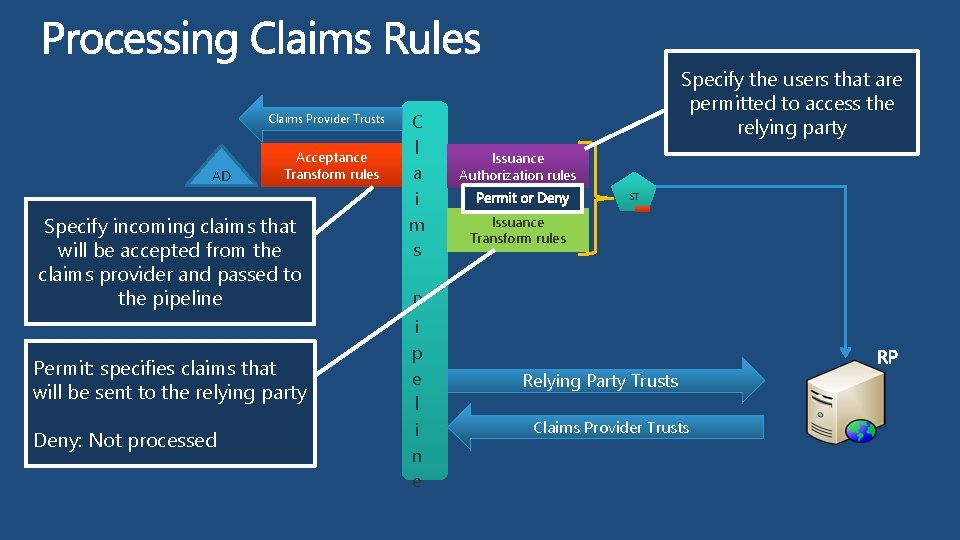
Claims Provider Trusts AD Acceptance Transform rules Specify incoming claims that will be accepted from the claims provider and passed to the pipeline Permit: specifies claims that will be sent to the relying party Deny: Not processed C l a i m s P i p e l i n e Specify the users that are permitted to access the relying party Issuance Authorization rules ST Issuance Transform rules Relying Party Trusts Claims Provider Trusts
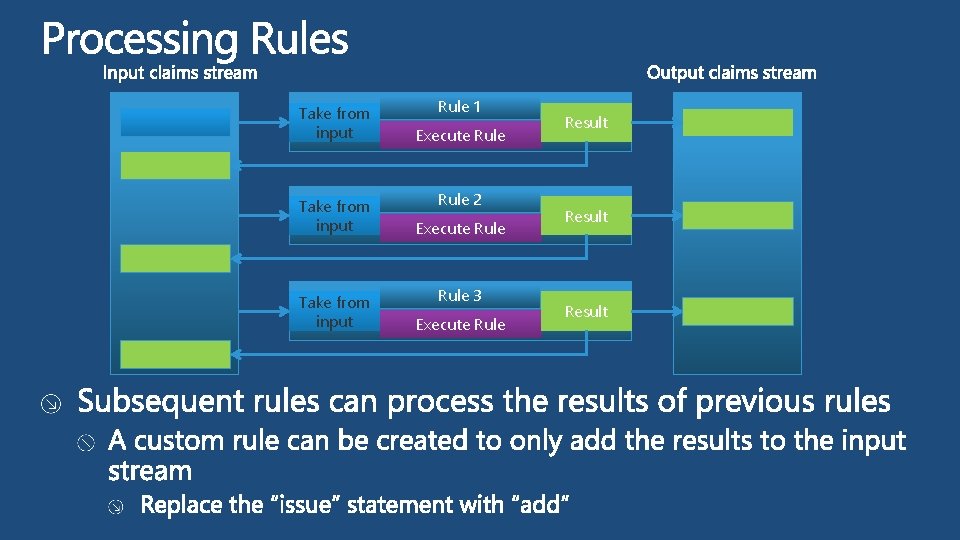
Take from input Rule 1 Execute Rule 2 Execute Rule 3 Execute Rule Result
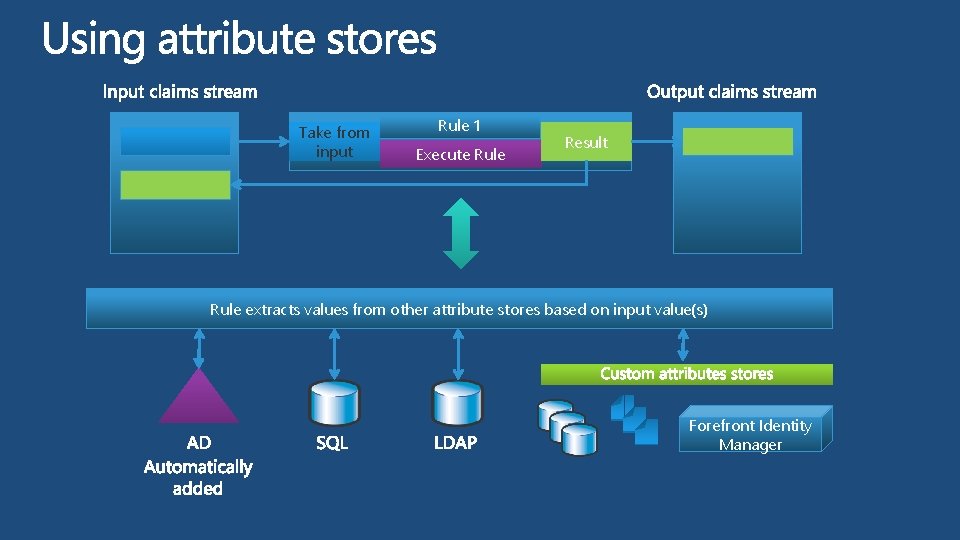
Take from input Rule 1 Execute Rule Result Rule extracts values from other attribute stores based on input value(s) Forefront Identity Manager

Step 3 (on AD FS 2. 0 server):
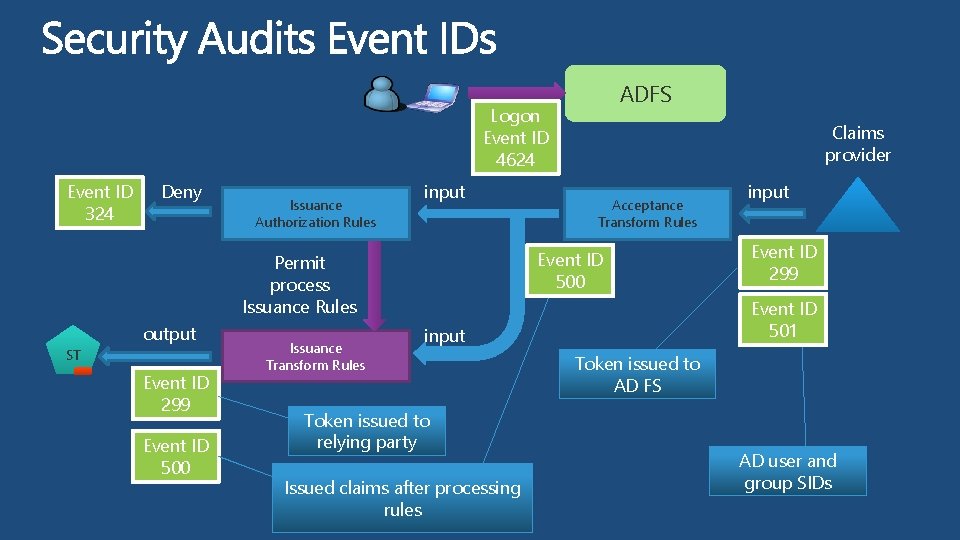
ADFS Logon Event ID 4624 Event ID 324 Deny Issuance Authorization Rules input ST Event ID 299 Event ID 500 Issuance Transform Rules Acceptance Transform Rules Event ID 500 Permit process Issuance Rules output Claims provider Issued claims after processing rules Event ID 299 Event ID 501 input Token issued to relying party input Token issued to AD FS AD user and group SIDs
demo Auditing Name Title Group


AD FS 2. 0 update rollup 2 AD FS 2. 0 troubleshooting guide AD FS 2. 0 SDK AD FS 2. 0 content map


John has designed and implemented computing systems ranging from high-speed industrial controllers through to distributed IT systems with a focus on security and high-availability. A key player in many IT projects for industry leaders including Microsoft, the UK Government and multi-nationals that require optimized IT systems. Developed technical training courses that have been published worldwide, co-authored a highly successful book on Microsoft Active Directory Internals, presents regularly at major international conferences including Tech. Ed, IT Forum and European summits. John can be engaged as a consultant or booked for speaking engagements through XTSeminars. www. xtseminars. co. uk

Learning Connect. Share. Discuss. Microsoft Certification & Training Resources http: //europe. msteched. com www. microsoft. com/learning Tech. Net Resources for IT Professionals Resources for Developers http: //microsoft. com/technet http: //microsoft. com/msdn

Evaluations Submit your evals online http: //europe. msteched. com/sessions


- Slides: 33