TRANSPOSITION CIPHERS Transposition Cipher Rail Fence Cipher Route

- Slides: 16

TRANSPOSITION CIPHERS

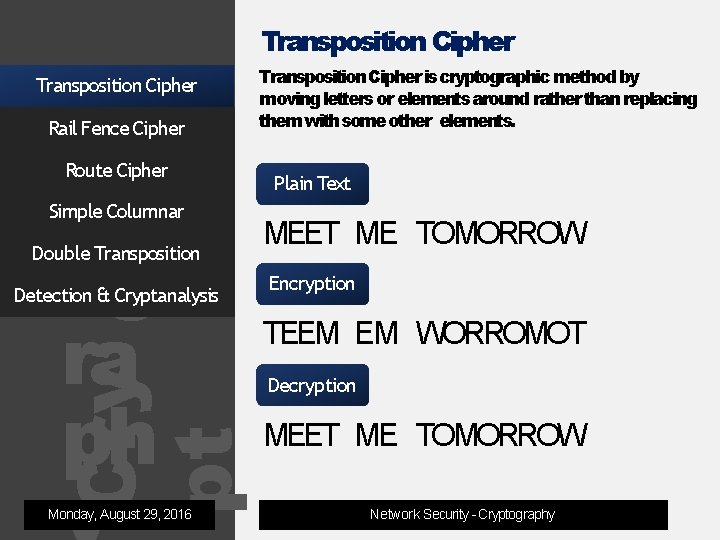
Transposition Cipher Rail Fence Cipher Route Cipher Simple Columnar og ra ph Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 Transposition Cipher is cryptographic method by moving letters or elements around rather than replacing them with some other elements. Plain Text MEET ME TOMORROW Encryption TEEM EM WORROMOT Decryption MEET ME TOMORROW Network Security - Cryptography

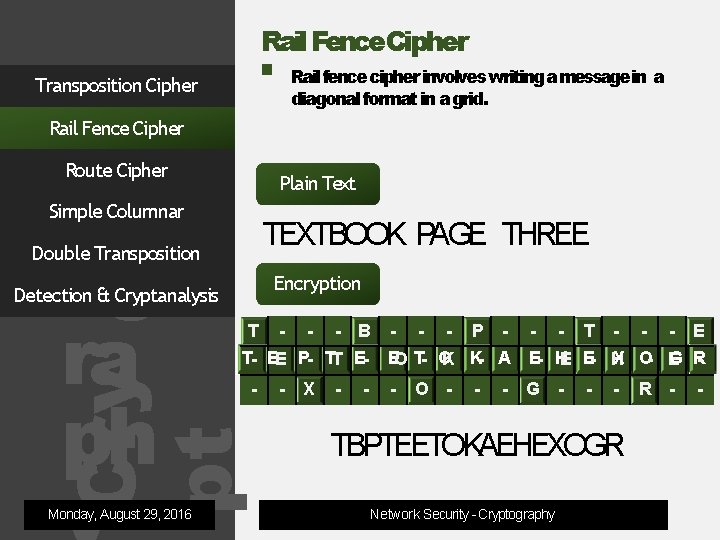
Rail Fence. Cipher Transposition Cipher Rail fence cipher involves writing amessage in a diagonal format in a grid. Rail Fence Cipher Route Cipher Plain Text Simple Columnar og ra ph TEXTBOOK PAGE THREE Double Transposition Encryption Detection & Cryptanalysis T - - B T- BE P- TT E- Cry pt Monday, August 29, 2016 - - - X - - - P - - - T - - - E EO T- O X O- E G R K K- A E- HE E- H - O - - - G - - - TBPTEETOKAEHEXOGR Network Security - Cryptography R - -

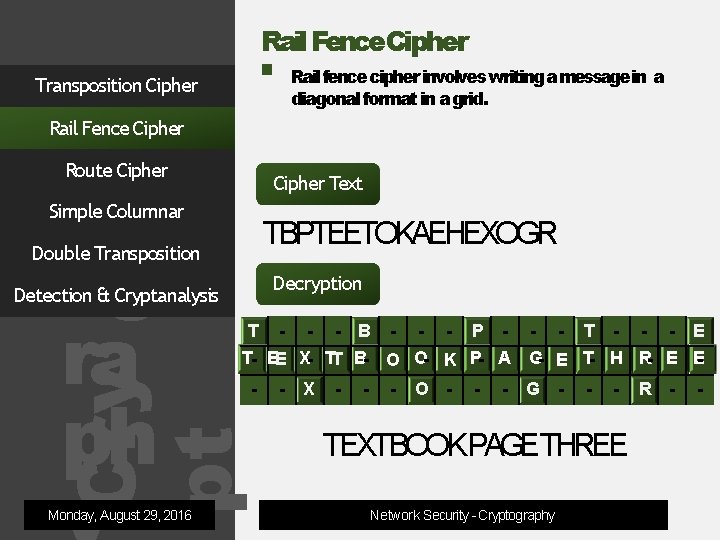
Rail Fence. Cipher Transposition Cipher Rail fence cipher involves writing amessage in a diagonal format in a grid. Rail Fence Cipher Route Cipher Text Simple Columnar og ra ph TBPTEETOKAEHEXOGR Double Transposition Decryption Detection & Cryptanalysis T - - B - - - P - T- EE X- TT B- O O- K P- A Cry pt Monday, August 29, 2016 - - - X - - - O - - T - - - E G- E T- H R- E E- - G - - - TEXTBOOKPAGETHREE Network Security - Cryptography R - -

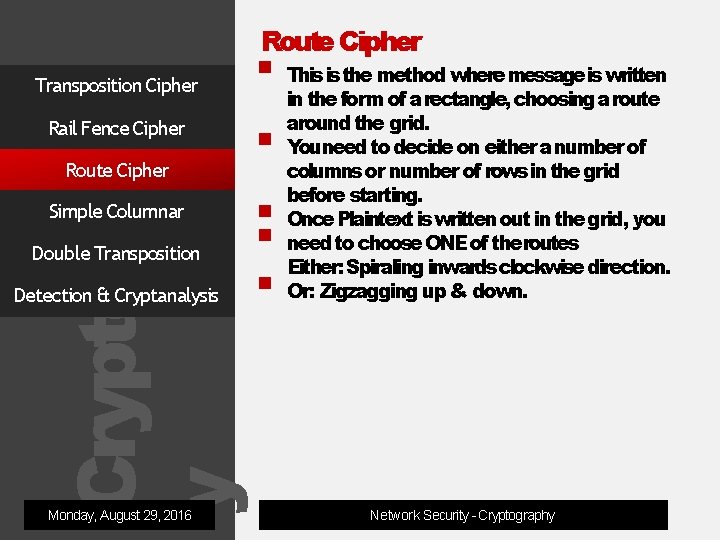
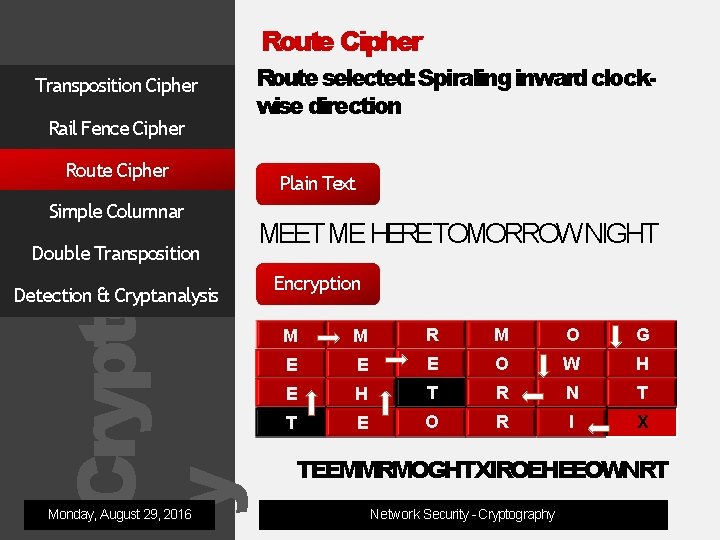
Cryptograph y Route Cipher Transposition Cipher Rail Fence Cipher Route Cipher Simple Columnar Double Transposition Detection & Cryptanalysis Monday, August 29, 2016 This is the method where message is written in the form of arectangle, choosing aroute around the grid. Youneed to decide on either anumber of columns or number of rows in the grid before starting. Once Plaintext is written out in the grid, you need to choose ONE of theroutes Either: Spiraling inwards clockwise direction. Or: Zigzagging up & down. Network Security - Cryptography

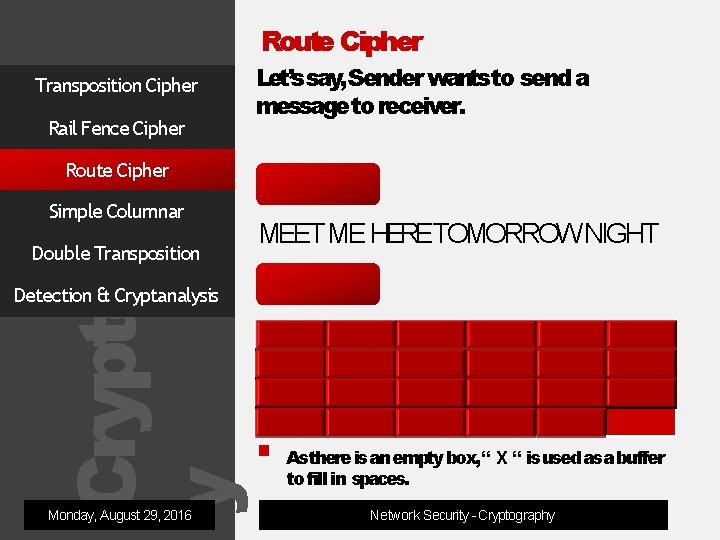
Cryptograph y Route Cipher Transposition Cipher Rail Fence Cipher Let’s say, Sender wantsto send a message to receiver. Route Cipher Simple Columnar Double Transposition Plain Text MEET ME HERETOMORROW NIGHT Encryption Detection & Cryptanalysis Monday, August 29, 2016 M M R M O G E E E O W H E H T R N T T E O R I X Asthere is an empty box, “ X “ is used asa buffer to fill in spaces. Network Security - Cryptography

Cryptograph y Route Cipher Transposition Cipher Rail Fence Cipher Route Cipher Simple Columnar Double Transposition Detection & Cryptanalysis Monday, August 29, 2016 Route selected: Spiraling inward clockwise direction Plain Text MEET ME HERETOMORROW NIGHT Encryption M M R M O G E E E O W H E H T R N T T E O R I X TEEMMRMOGHTXIROEHEEOWNRT Network Security - Cryptography

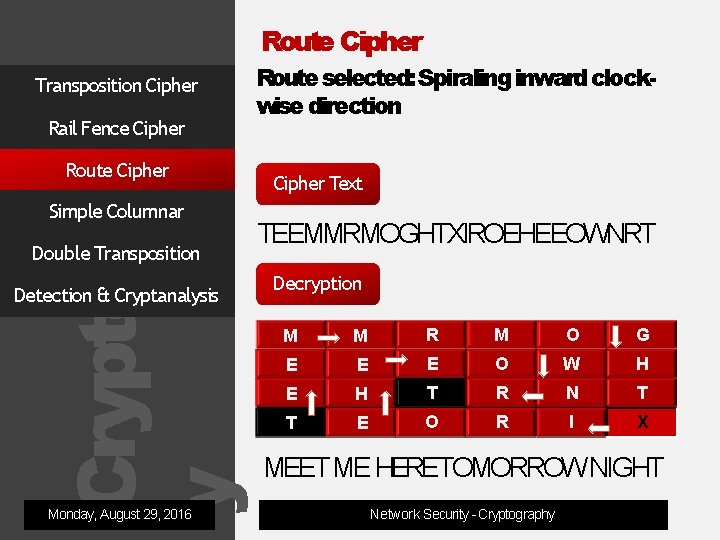
Cryptograph y Route Cipher Transposition Cipher Rail Fence Cipher Route Cipher Simple Columnar Double Transposition Detection & Cryptanalysis Monday, August 29, 2016 Route selected: Spiraling inward clockwise direction Cipher Text TEEMMRMOGHTXIROEHEEOWNRT Decryption M M R M O G E E E O W H E H T R N T T E O R I X MEET ME HERETOMORROW NIGHT Network Security - Cryptography

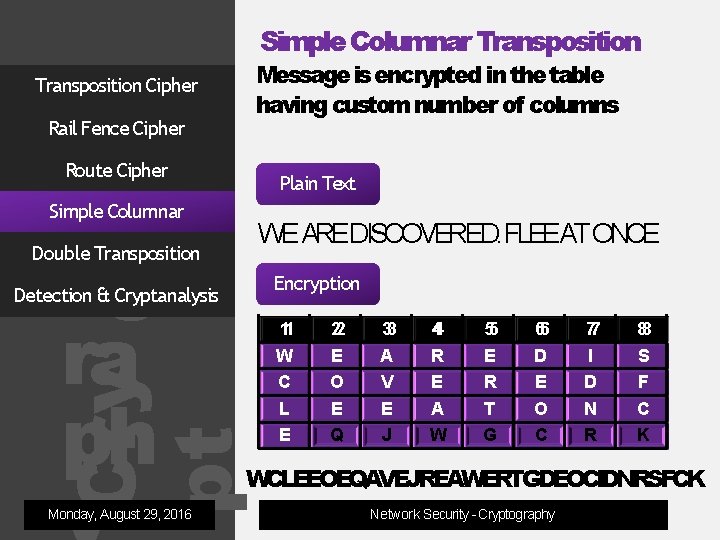
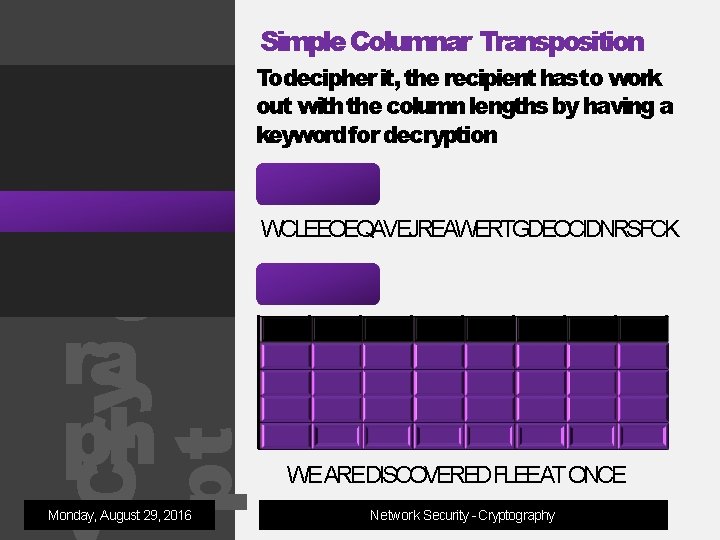
Simple Columnar Transposition Message is encrypted in the table having custom number of columns Transposition Cipher Rail Fence Cipher Route Cipher Plain Text Simple Columnar og ra ph WE AREDISCOVERED. FLEEAT ONCE Double Transposition Encryption Cry pt Detection & Cryptanalysis Monday, August 29, 2016 11 W C L E 22 E O E Q 33 A V E J 44 R E A W 55 E R T G 66 D E O C 77 I D N R 88 S F C K WCLEEOEQAVEJREAWERTGDEOCIDNRSFCK Network Security - Cryptography

Simple Columnar Transposition Cipher Rail Fence Cipher Route Cipher Simple Columnar og ra ph Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 Todecipher it, the recipient has to work out with the column lengths by having a keyword for decryption Cipher Text WCLEEOEQAVEJREAWERTGDEOCIDNRSFCK Decryption 11 W C L E 22 E O E Q 33 A V E J 44 R E A W 55 E R T G 66 D E O C 77 I D N R WE AREDISCOVEREDFLEEAT ONCE Network Security - Cryptography 88 S F C K

Simple Columnar Transposition Cipher Rail Fence Cipher Route Cipher Simple Columnar Transposition is Simple Columnar og ra ph Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 quite simple that it may be hacked easily. Toprevent this danger, wecan transpose our message in this method by repeating it again and again. We canuse our nth cipher text asa plain text to re-encrypt our message to (n+1)th cipher text. Network Security - Cryptography

Double Transposition Cipher Single columnar transposition canbe Rail Fence Cipher Route Cipher Simple Columnar og ra ph Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 hacked by guessing number of column lengths. When it is decrypted in an irregular form. It canbe cleared by looking for possible anagrams to re-order the message. Double Columnar Transposition was often used to make. Columnar Transposition. Network Security - Cryptography

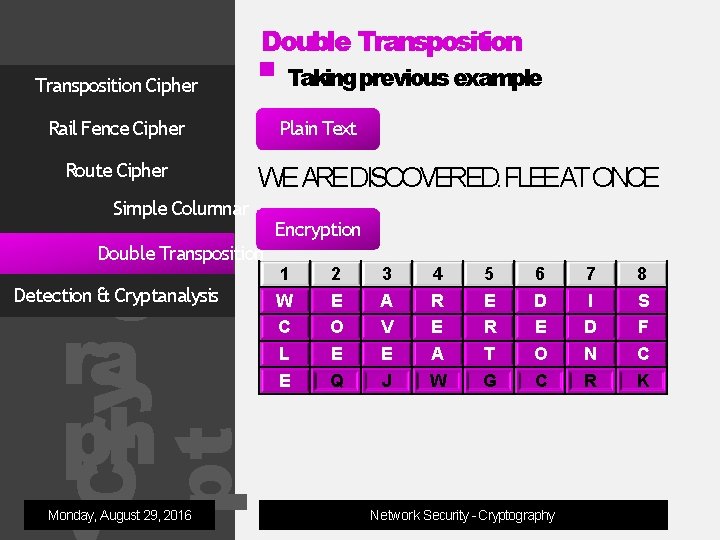
Double Transposition Cipher Takingprevious example Rail Fence Cipher Route Cipher Plain Text WE AREDISCOVERED. FLEEAT ONCE Simple Columnar og ra ph Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 Encryption 1 W C L E 2 E O E Q 3 A V E J 4 R E A W 5 E R T G 6 D E O C Network Security - Cryptography 7 I D N R 8 S F C K

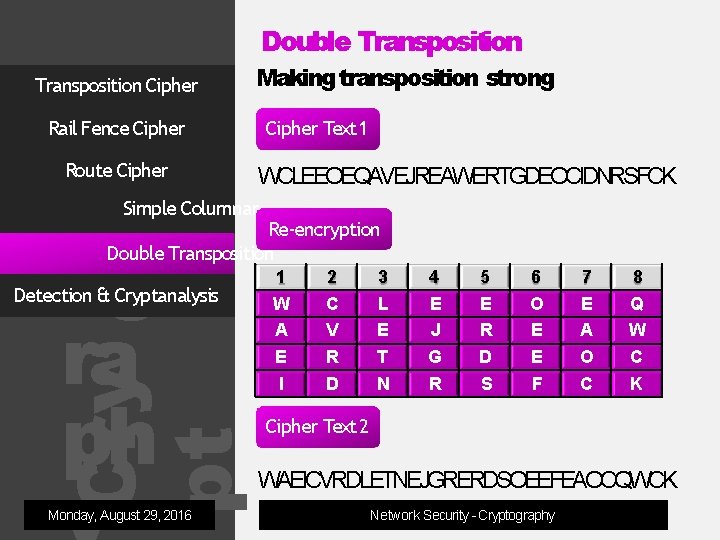
Double Transposition Cipher Making transposition strong Rail Fence Cipher Route Cipher Text 1 WCLEEOEQAVEJREAWERTGDEOCIDNRSFCK Simple Columnar og ra ph Re-encryption Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 1 W A E I 2 C V R D 3 L E T N 4 E J G R 5 E R D S 6 O E E F 7 E A O C 8 Q W C K Cipher Text 2 WAEICVRDLETNEJGRERDSOEEFEAOCQWCK Network Security - Cryptography

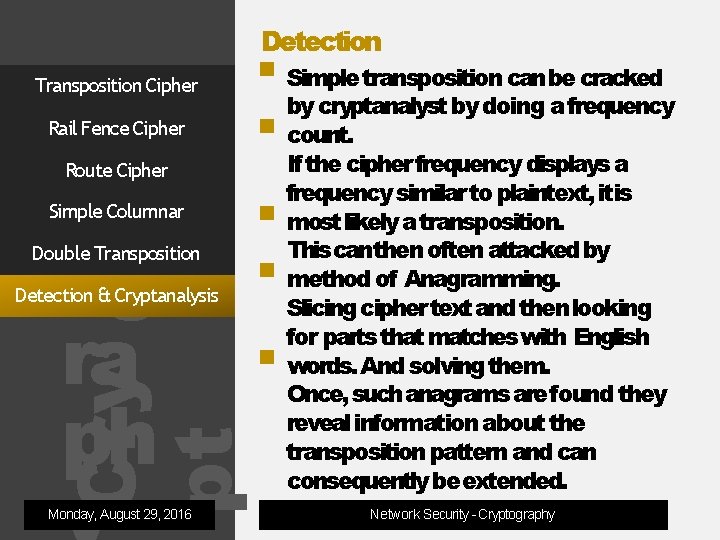
Detection Transposition Cipher Rail Fence Cipher Simple transposition canbe cracked by cryptanalyst by doing a frequency count. Route Cipher Simple Columnar og ra ph Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 If the cipher frequency displays a frequency similar to plaintext, itis most likely a transposition. This canthen often attacked by method of Anagramming. Slicing cipher text and then looking for parts that matches with English words. And solving them. Once, such anagrams are found they reveal information about the transposition pattern and can consequently beextended. Network Security - Cryptography

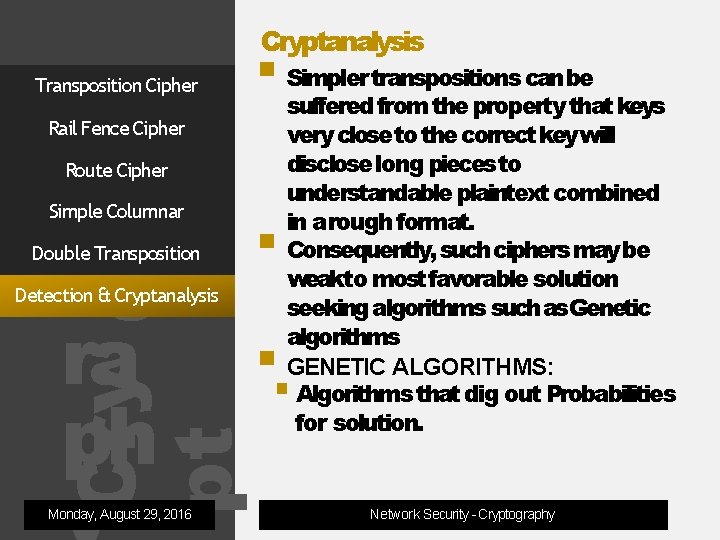
Cryptanalysis Transposition Cipher Rail Fence Cipher Route Cipher Simple Columnar og ra ph Double Transposition Cry pt Detection & Cryptanalysis Monday, August 29, 2016 Simpler transpositions canbe suffered from the property that keys very close to the correct keywill disclose long pieces to understandable plaintext combined in arough format. Consequently, such ciphers may be weakto most favorable solution seeking algorithms such as. Genetic algorithms GENETIC ALGORITHMS: Algorithms that dig out Probabilities for solution. Network Security - Cryptography