Transmission Security via Fast Time Frequency Hopping PI







- Slides: 14

Transmission Security via Fast Time -Frequency Hopping PI: Eli Yablanovich Co-PIs: Rick Wesel Ingrid Verbauwhede Ming Wu Bahram Jalali UCLA Electrical Engineering Department

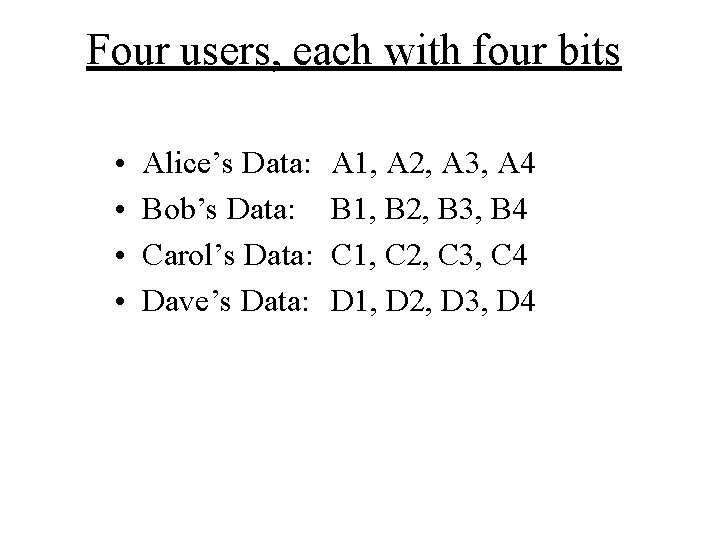
Four users, each with four bits • • Alice’s Data: Bob’s Data: Carol’s Data: Dave’s Data: A 1, A 2, A 3, A 4 B 1, B 2, B 3, B 4 C 1, C 2, C 3, C 4 D 1, D 2, D 3, D 4

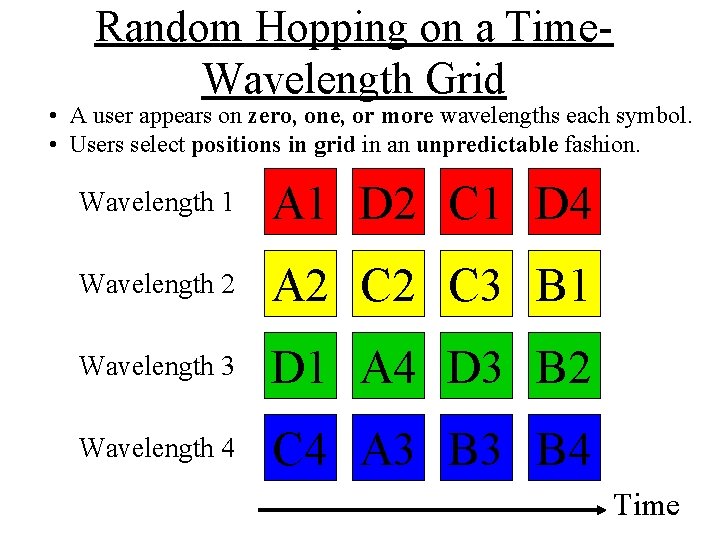
Random Hopping on a Time. Wavelength Grid • A user appears on zero, one, or more wavelengths each symbol. • Users select positions in grid in an unpredictable fashion. Wavelength 1 A 1 D 2 C 1 D 4 Wavelength 2 A 2 C 3 B 1 Wavelength 3 D 1 A 4 D 3 B 2 Wavelength 4 C 4 A 3 B 4 Time

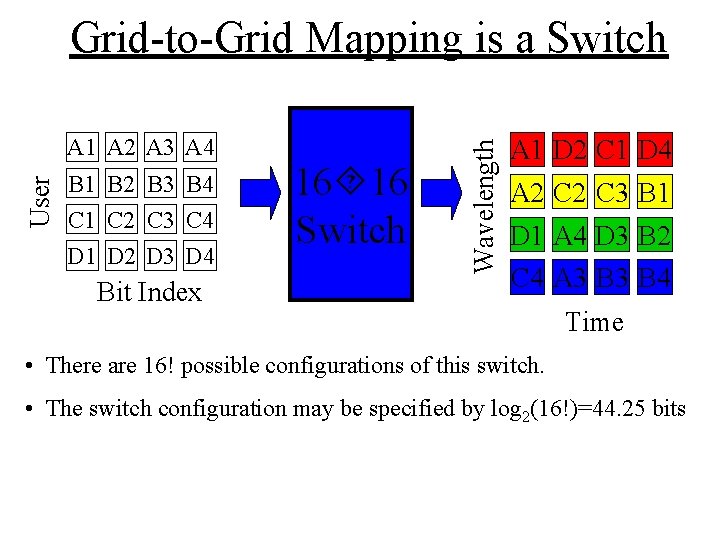
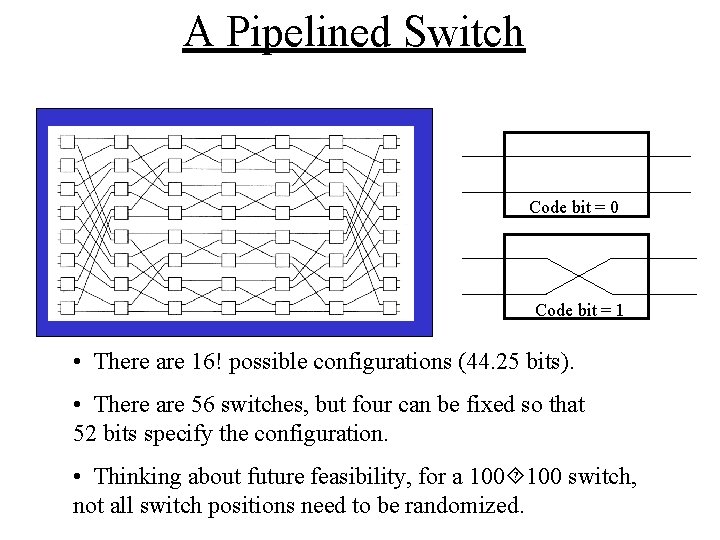
User A 1 A 2 A 3 A 4 B 1 B 2 B 3 B 4 C 1 C 2 C 3 C 4 D 1 D 2 D 3 D 4 Bit Index 16 16 Switch Wavelength Grid-to-Grid Mapping is a Switch A 1 D 2 C 1 D 4 A 2 C 3 B 1 D 1 A 4 D 3 B 2 C 4 A 3 B 4 Time • There are 16! possible configurations of this switch. • The switch configuration may be specified by log 2(16!)=44. 25 bits

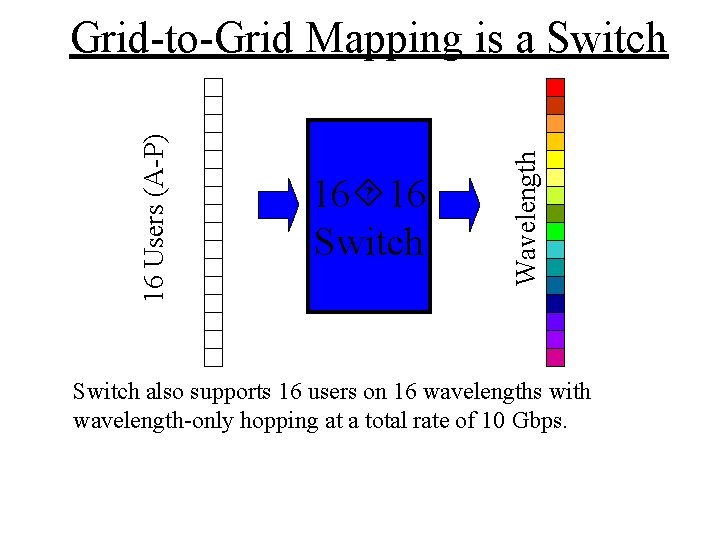
16 16 Switch Wavelength 16 Users (A-P) Grid-to-Grid Mapping is a Switch also supports 16 users on 16 wavelengths with wavelength-only hopping at a total rate of 10 Gbps.

A Pipelined Switch Code bit = 0 Code bit = 1 • There are 16! possible configurations (44. 25 bits). • There are 56 switches, but four can be fixed so that 52 bits specify the configuration. • Thinking about future feasibility, for a 100 switch, not all switch positions need to be randomized.

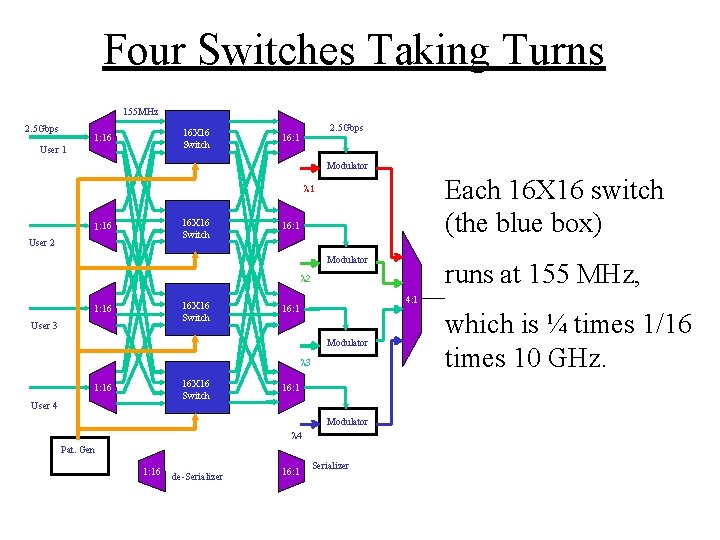
Four Switches Taking Turns 155 MHz 2. 5 Gbps 16 X 16 Switch 1: 16 User 1 2. 5 Gbps 16: 1 Modulator Each 16 X 16 switch (the blue box) l 1 16 X 16 Switch 1: 16 User 2 16: 1 Modulator runs at 155 MHz, l 2 16 X 16 Switch 1: 16 User 3 4: 1 16: 1 Modulator l 3 16 X 16 Switch 1: 16 User 4 16: 1 Modulator l 4 Pat. Gen 1: 16 de-Serializer 16: 1 Serializer which is ¼ times 1/16 times 10 GHz.

User A 1 A 2 A 3 A 4 B 1 B 2 B 3 B 4 C 1 C 2 C 3 C 4 D 1 D 2 D 3 D 4 Bit Index 16 16 Switch Wavelength The Big Picture A 1 D 2 C 1 D 4 A 2 C 3 B 1 D 1 A 4 D 3 B 2 C 4 A 3 B 4 Time We need 52 bits or 9 Gbits/sec (We can do about 20 Gbits/sec) Advanced Encryption Standard Random bit generator (initially just a linear feedback shift register)

What Kinds of Security Are Possible? • Security by Obscurity – This is no security at all. Obscurity is fleeting. • Security by computational difficulty – Standardized systems like DES and AES rely on this. – Must consider attacks where plain-text is known. • The one-time pad that nobody else knows – Perfect as long as the pad remains secret.

Hopping versus Spreading • Our technique focuses on the addition of cryptographic security in the context of relatively straightforward frequency-hopped CDMA. • Certainly, similar techniques could be applied to the other OCDMA techniques described during this meeting. • However, in every case, the real security comes from (high speed) cryptographic security rather than obscure optical techniques.

Network Security • Most sophisticated security techniques add security at the source only (application layer). • Our technique adds security at the physical layer (or at the network layer).

Why Have Network Security? • Increase the difficulty of attack, even with plaintext available. (The ciphertext of an individual stream is now difficult to identify. ) • Adds security with minimal latency (the latency inherent in the timespan of the permutation) because AES processing is not in the real-time path. .

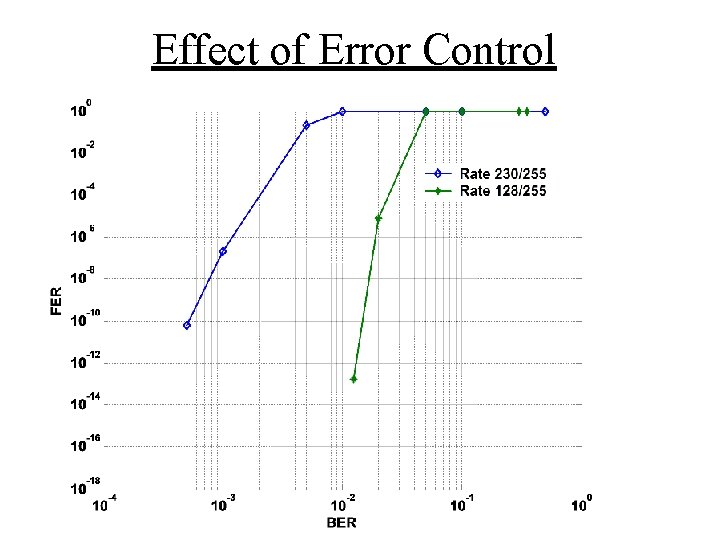
Synchronous vs. Asynchronous • Our original vision was for with synchronous operation (and a universally known key) as a requirement. • However, our system concept can trade spectral efficiency to operate asynchronously. • Example: Sixty wavelengths but still using only sixteen of the two hundred forty available slots, each transmitter can have it’s own key. • Collisions lead to a bit error rate of. 1%. • Reed Solomon error correction brings FER to well below 10 -10.

Effect of Error Control