Transitions in Programming Models Luca Cardelli Microsoft Research


![A Personal Agenda ● Flows [exploit join calculus] – Synchronization chords – (f. k. A Personal Agenda ● Flows [exploit join calculus] – Synchronization chords – (f. k.](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-8.jpg)







![Example: Typing Cambridge[ Eagle[ chair[0] | chair[0] ] ] Description Cambridge[ Eagle[ chair[0] | Example: Typing Cambridge[ Eagle[ chair[0] | chair[0] ] ] Description Cambridge[ Eagle[ chair[0] |](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-28.jpg)
![Example: Policies “Vertical” implications about nesting Borders[ Starbucks[…] | Books[…] ] Borders[T] Borders[Starbucks[T] | Example: Policies “Vertical” implications about nesting Borders[ Starbucks[…] | Books[…] ] Borders[T] Borders[Starbucks[T] |](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-30.jpg)
![Future Trends ● Freely mixing logical descriptions and data: spatial logics a[b[A B]] a[C] Future Trends ● Freely mixing logical descriptions and data: spatial logics a[b[A B]] a[C]](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-32.jpg)
![Data arrays T : : = | | | N T[] T(…, T, …) Data arrays T : : = | | | N T[] T(…, T, …)](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-33.jpg)


![Type Systems for Hidden Names ● my. Account : Hy. … id[y] … checkbook[y] Type Systems for Hidden Names ● my. Account : Hy. … id[y] … checkbook[y]](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-40.jpg)











- Slides: 58

Transitions in Programming Models Luca Cardelli Microsoft Research Cambridge UK ICSE St. Louis, 2005 -05 -18

Significant Transitions ● Programming languages (PLs) – They evolve slowly and occasionally, e. g. : ●C to C++ : More robust data structures (objects) ●C++ to Java : More robust control flows (strong typing) – But new programming models are invented routinely ●As domain-specific libraries or API’s ●As program analysis tools ●As language extensions ● Transitions – Significant transitions in programming models eventually “precipitate” into new programming languages (unpredictably) – We can watch out for significant transitions in programming models 10/7/2020 2

Transitions in 3 (related) areas ● We are in the middle of a radical transition in programming models (and eventually PLs) ● A new emphasis on computation on WANs – Wide area flows ●Messages nor RPC, schedules not threads. Messaging API’s. ●Need to integrate these new flows into PL control constructs. – Wide area data ●XML is “net data”. XML API’s. ●Need to integrate this new data into PL data structures. – Wide area protection ●Access control, data protection. Security and privacy API’s. ●Need to integrate security properties into PL assertions. ● Disruptive transitions – Forget RPC (and threads): the world is asynchronous. – Forget type systems as we know them. – Forget trusting anything non-local. 10/7/2020 3

Flow Integration ● Wish: Wouldn’t it be nice to hide concurrency from programmers? – – SQL does it well UI packages do it fine (mostly single-threaded!) RPC does it ok But we are moving towards more asynchrony, I. e. towards more visible concurrency (e-commerce scripts and languages, web services, etc. ) You can hide all concurrency some of the time, and you can hide some concurrency all the time, but you can’t hide all concurrency all the time. – Asynchronous message-based concurrency does not fit easily with more traditional shared-memory synchronous concurrency control ● Goal: make concurrent flows available and checkable at the language level. 10/7/2020 4

Data Integration ● Wish: Wouldn't it be nice to "program directly against the schema" in a well-typed way? – PL data has traditionally been "triangular" (trees), while persistent data has traditionally been "square" (tables) – This has caused integration problems: the “impedance mismatch” in data base programming languages – Now, persistent data (XML) is triangular too! – However, the type systems for PL data (based on tree matching) and XML (based on tree automata) are still deeply incompatible ● Goal: make semistructured data easily available and checkable at the language level. 10/7/2020 5

Protection Integration ● Wish: Wouldn’t it be nice to have automatic security? – It’s an applet. Sits is a sandbox. End of story. (? ) – Ok, what about semi-automatic security? Explicitly grant/require permissions. (Stack walking etc. ) – Leads to “sophisticated” access models that programmers do not understand reliably. ● Security today: obscure mechanisms to prevent something from happening. – It is usually not clear what security mechanisms are meant to achieve. – Need to move towards declarative security and privacy interfaces and policies. ● Goal: make protection policies available and checkable at the language level. 10/7/2020 6

Language Reliability ● Whether or not we merge new programming models into PLs, we need analysis tools for these new situations – Flow: e. g. : behavioral type/analysis system ●“Does the program respect the protocol? ” – Data: e. g. : semistructured type/analysis systems ●“Does the program output match the schema? ” – Protection: e. g. : information-flow type/analysis system ●“Does the program defy policy or leak secrets” ● Analysis tools are critical for software reliability – Getting it right without assistance is just too hard. – These technologies need to be developed in any case, and is better if they can be incorporated in programming languages. 10/7/2020 7
![A Personal Agenda Flows exploit join calculus Synchronization chords f k A Personal Agenda ● Flows [exploit join calculus] – Synchronization chords – (f. k.](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-8.jpg)
A Personal Agenda ● Flows [exploit join calculus] – Synchronization chords – (f. k. a. Polyphonic C#) ● Data [exploit spatial logics as types] – Description logics – (f. k. a. Xen/X#) ● Protection [exploit p-calculus-style restriction] – Flows: Secrecy and Group Creation – Data: Trees with hidden labels 10/7/2020 8

Flows 10/7/2020 9

Language Support for (WAN) Distribution ● Distribution concurrency + latency asynchrony more concurrency – Approaches: Message-passing, event-based programming, dataflow models, etc. – Languages: coordination (orchestration) languages, workflow languages, etc. ● Good language support for asynchrony – Make invariants and intentions more apparent (part of the interface), because: ● It’s good software engineering ● Allows the compiler much more freedom to choose different ● implementations Also helps other tools 10/7/2020 10

Flows ● An extension of the C# language with new concurrency constructs ● Based on the join calculus – A foundational process calculus like the p-calculus but better suited to asynchronous, distributed systems. – First applied to functional languages (Jo. Caml). – It adapts remarkably well to o-o classes and methods. ● A single model that works for – Local concurrency (multiple threads on a single machine). – Distributed concurrency (asynchronous messaging over LAN or WAN). – With no distributed consensus. ● It an unusual model. But it’s also a simple extension of familiar o-o notions. – No threads, no locks, no fork, only join. 10/7/2020 11

In one slide: ● Client Side (method invocation) – Objects have both synchronous and asynchronous methods. – If the method is synchronous, the caller blocks until the method returns some result (as usual). – If the method is async, the call completes at once and returns void (as in message passing). ● Server Side (class definition) – A class defines a collection of chords (method synchronization patterns), which define what happens once a particular set of methods have been invoked. One method may appear in several chords. – When enough pending method calls match a chord pattern, the chord body runs. If there are several matches, an unspecified chord is selected. – Each chord can have at most one synchronous method (providing the result). A chord containing only asynchronous methods effectively forks a new thread. 10/7/2020 12

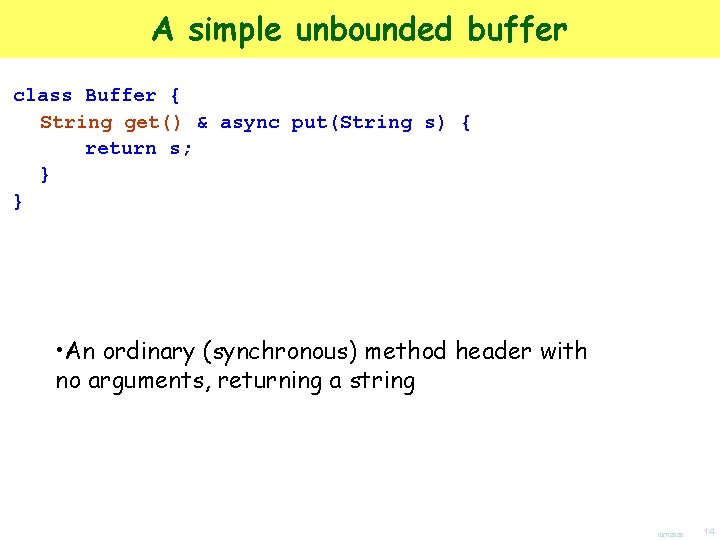
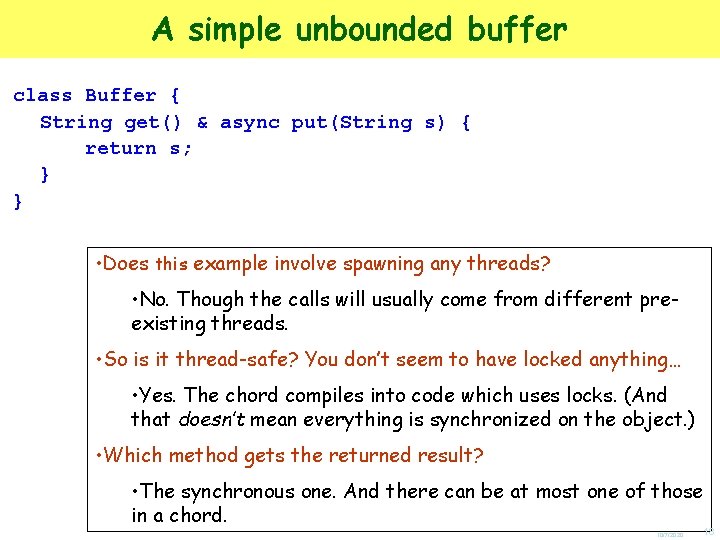
A simple unbounded buffer class Buffer { String get() & async put(String s) { return s; } } 10/7/2020 13

A simple unbounded buffer class Buffer { String get() & async put(String s) { return s; } } • An ordinary (synchronous) method header with no arguments, returning a string 10/7/2020 14

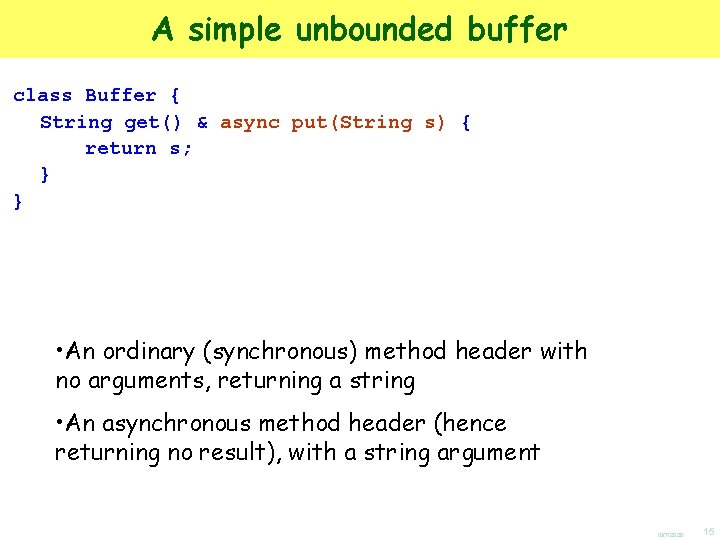
A simple unbounded buffer class Buffer { String get() & async put(String s) { return s; } } • An ordinary (synchronous) method header with no arguments, returning a string • An asynchronous method header (hence returning no result), with a string argument 10/7/2020 15

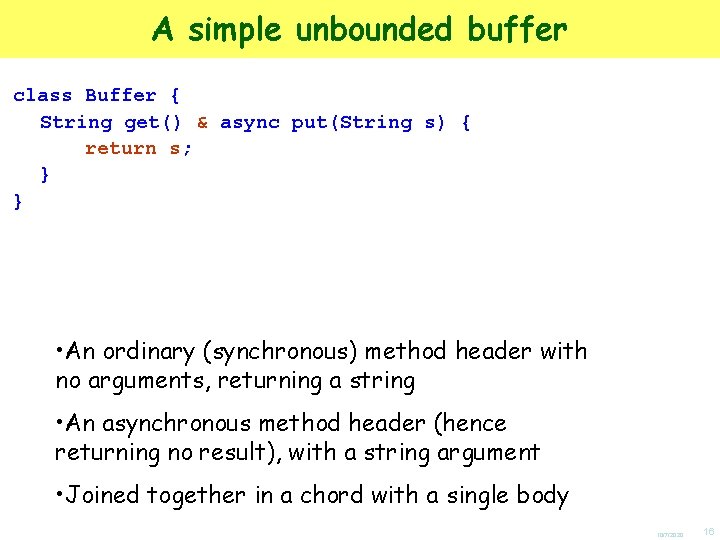
A simple unbounded buffer class Buffer { String get() & async put(String s) { return s; } } • An ordinary (synchronous) method header with no arguments, returning a string • An asynchronous method header (hence returning no result), with a string argument • Joined together in a chord with a single body 10/7/2020 16

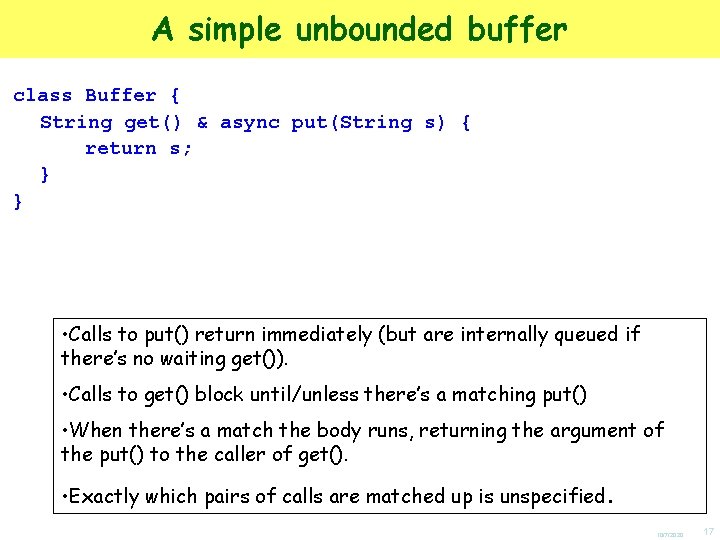
A simple unbounded buffer class Buffer { String get() & async put(String s) { return s; } } • Calls to put() return immediately (but are internally queued if there’s no waiting get()). • Calls to get() block until/unless there’s a matching put() • When there’s a match the body runs, returning the argument of the put() to the caller of get(). • Exactly which pairs of calls are matched up is unspecified. 10/7/2020 17

A simple unbounded buffer class Buffer { String get() & async put(String s) { return s; } } • Does this example involve spawning any threads? • No. Though the calls will usually come from different preexisting threads. • So is it thread-safe? You don’t seem to have locked anything… • Yes. The chord compiles into code which uses locks. (And that doesn’t mean everything is synchronized on the object. ) • Which method gets the returned result? • The synchronous one. And there can be at most one of those in a chord. 10/7/2020 18

Reader/Writer …using threads and mutexes in Modula 3 An introduction to programming with threads. Andrew D. Birrell, January 1989. An integer i represents the lock state: -1 0 1 2 (exclusive) (available) (shared) 3… 10/7/2020 19

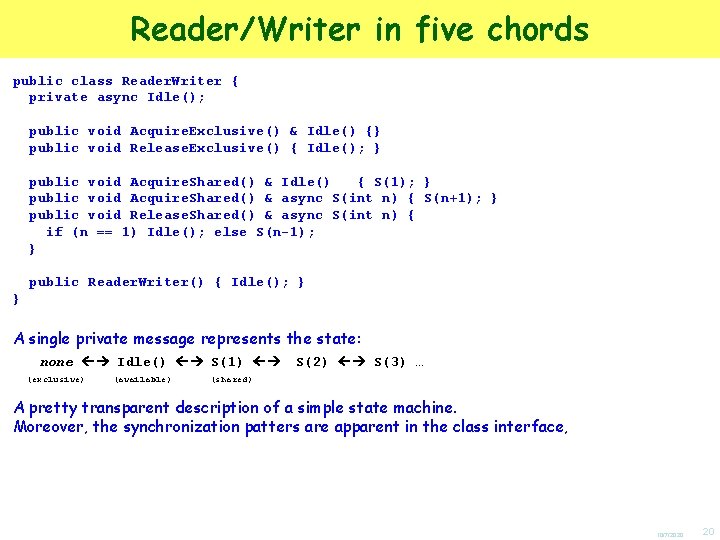
Reader/Writer in five chords public class Reader. Writer { private async Idle(); public void Acquire. Exclusive() & Idle() {} public void Release. Exclusive() { Idle(); } public void Acquire. Shared() & Idle() { S(1); } public void Acquire. Shared() & async S(int n) { S(n+1); } public void Release. Shared() & async S(int n) { if (n == 1) Idle(); else S(n-1); } public Reader. Writer() { Idle(); } } A single private message represents the state: none Idle() S(1) (exclusive) (available) S(2) S(3) … (shared) A pretty transparent description of a simple state machine. Moreover, the synchronization patters are apparent in the class interface, 10/7/2020 20

Features ● A clean, simple, new model for asynchronous concurrency – Minimalist design – to build whatever complex synchronization behaviors you need – Easier to express and enforce concurrency invariants; not “buried in the code” any more – Much better than programming reactive state machines by hand (the complier does it for you). – Efficiently compiled to queues, automata, match bit-vectors, and thread pools. – Compatible with existing constructs, though they constrain our design somewhat ● More transparently exposes the control flows – Solid foundations, on which to build analysis tools. – And checkable notions of contracts. 10/7/2020 21

Future Trends ● Protocol contracts – Typechecking-style support for checking the interaction of concurrent protocols. – A. k. a behavioral type system, session types, etc. – Required for software reliability – Facilitated by explicit concurrency interfaces. 10/7/2020 22

Data 10/7/2020 23

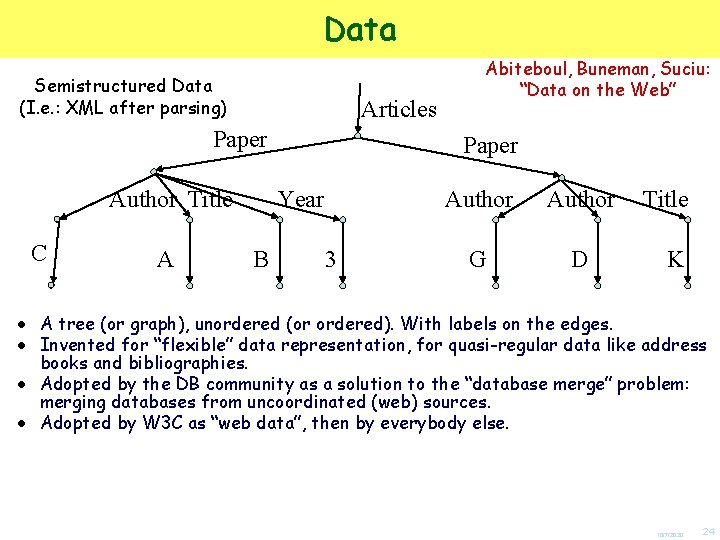
Data Semistructured Data (I. e. : XML after parsing) Articles Paper Author Title C ● ● A Paper Year B Abiteboul, Buneman, Suciu: “Data on the Web” 3 Author G D Title K A tree (or graph), unordered (or ordered). With labels on the edges. Invented for “flexible” data representation, for quasi-regular data like address books and bibliographies. Adopted by the DB community as a solution to the “database merge” problem: merging databases from uncoordinated (web) sources. Adopted by W 3 C as “web data”, then by everybody else. 10/7/2020 24

It’s Unusual Data ● Not really arrays/lists: – Many children with the same label, instead of indexed children. – Mixture of repeated and non repeated labels under a node. ● Not really records: – Many children with the same label. – Missing/additional fields with no tagging information. ● Not really variants (tagged unions): – Labeled but untagged unions. ● Unusual data. – Yet, it aims to be the new universal standard for interoperability of programming languages, databases, e-commerce. . . 10/7/2020 25

Needs Unusual Languages ● New flexible types and schemas are required. – Based on “regular expressions over trees” reviving techniques from tree-automata theory. ● New processing languages required. – Xduce [Pierce, Hosoya], Cduce, … – Various web scripting abominations. ● New access methods/query languages required. – E. g. Existence of paths through the tree. 10/7/2020 26

Data Descriptions ● We want to talk about data – I. e. , specify/query/constrain/typecheck the possible structure of data, for many possible reasons: ●Typing (and typechecking): for language and database use. ●Constraining (and checking): for policy or integrity use. ●Querying (and searching): for semistructured database use. ●Specifying (and verifying): for architecture or design documents. ● A description (spatial formula) is a formal way of talking about the possible structure of data. – We go after a general framework: a very expressive language of descriptions. – Combining logical and structural connectives. – Special classes of descriptions can be used as types, schemas, constraints, queries, and specifications. 10/7/2020 27
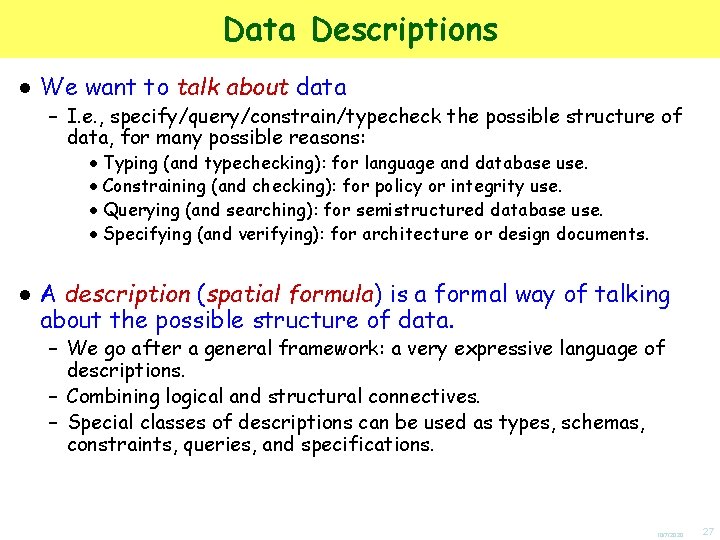
![Example Typing Cambridge Eagle chair0 chair0 Description Cambridge Eagle chair0 Example: Typing Cambridge[ Eagle[ chair[0] | chair[0] ] ] Description Cambridge[ Eagle[ chair[0] |](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-28.jpg)
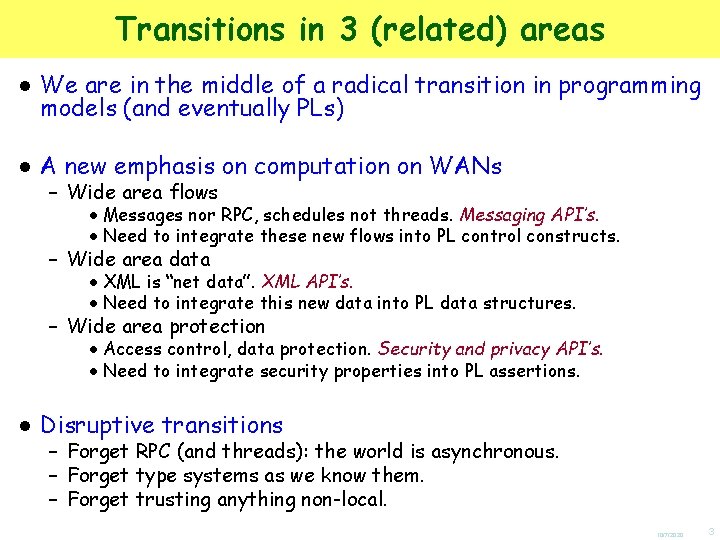
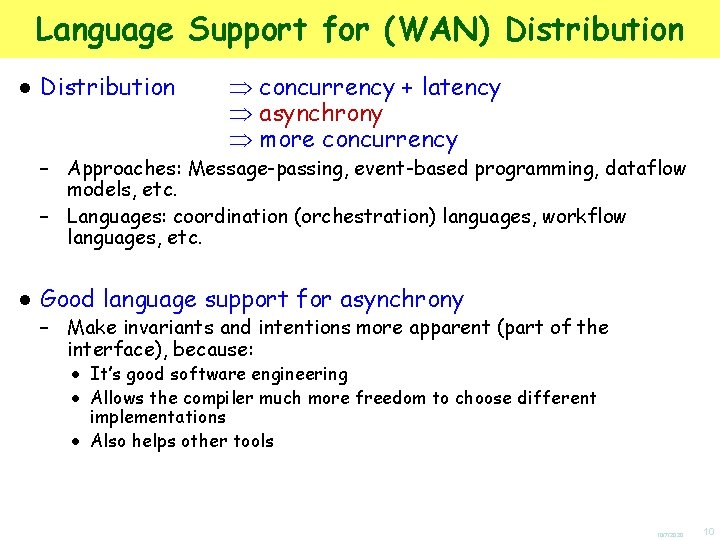
Example: Typing Cambridge[ Eagle[ chair[0] | chair[0] ] ] Description Cambridge[ Eagle[ chair[0] | T ]|T ] In Cambridge there is (nothing but) a pub called the Eagle that contains (nothing but) two empty chairs. data matches description Data In Cambridge there is (at least) a pub called the Eagle that contains (at least) one empty chair. 10/7/2020 28

Example: Queries With match variables X: Who is really sitting at the Eagle? Eagle[ chair[ 0 X] | T ] Cambridge[ Eagle[ chair[John[0]] | chair[Mary[0]] | chair[0] ] ] Yes: X = John[0] Yes: X = Mary[0] With select-from: from Eagle[. . . ] match Eagle[chair[ 0 X] | T] select person[X] Single result: person[John[0]] | person[Mary[0]] 10/7/2020 29
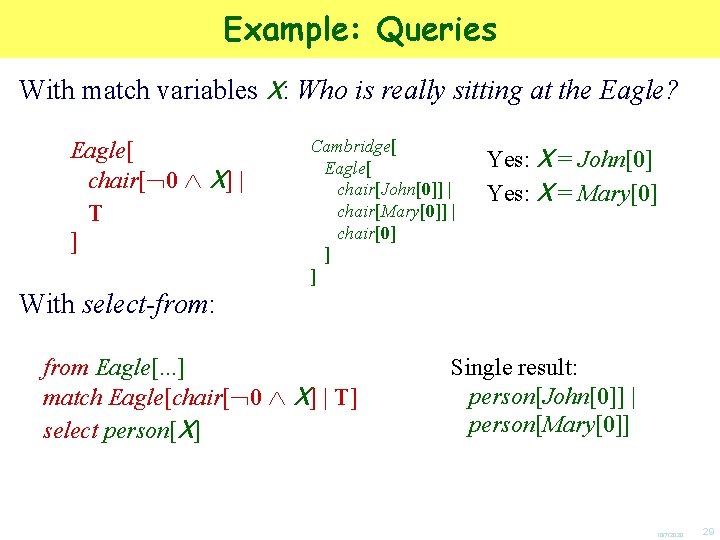
![Example Policies Vertical implications about nesting Borders Starbucks Books BordersT BordersStarbucksT Example: Policies “Vertical” implications about nesting Borders[ Starbucks[…] | Books[…] ] Borders[T] Borders[Starbucks[T] |](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-30.jpg)
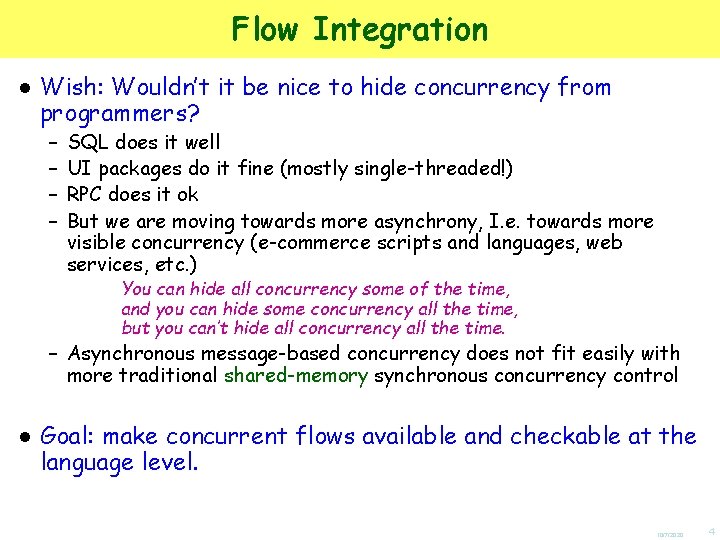
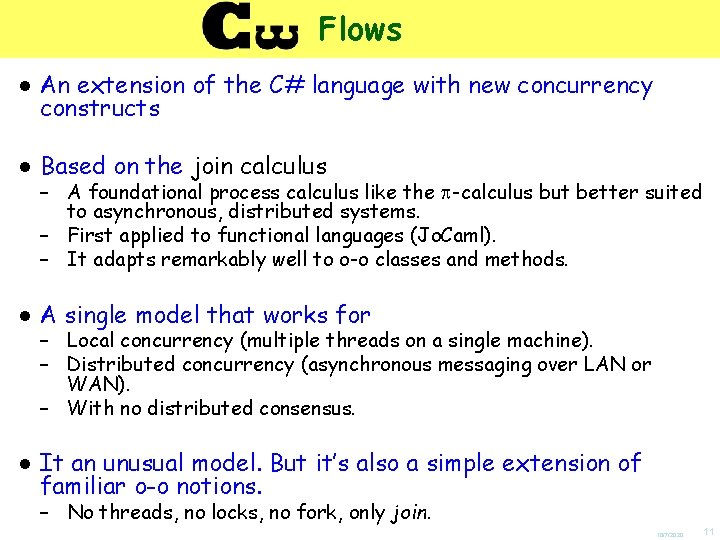
Example: Policies “Vertical” implications about nesting Borders[ Starbucks[…] | Books[…] ] Borders[T] Borders[Starbucks[T] | T] “Business Policy” If it’s a Borders, then it must contain a Starbucks “Horizontal” implications about proximity Smoker[…] | Non. Smoker[…] | Smoker[…] “Social Policy” (Non. Smoker[T] | T) (Smoker[T] | T) If there is a Non. Smoker, then there must be a Smoker nearby 10/7/2020 30

Example: Schemas ● Spatial formulas are a “very rich type system”. We can comfortably represent various kinds of schemas. ● Ex. : Xduce-like (DTD-like) schemas: 0 A|B A B n[A] A* A+ A? the empty tree an A next to a B either an A or a B an edge n leading to an A @ m. X. 0 (A | X) the merge of zero or more As @ A | A* the merge of one or more As @ 0 A zero or one A 10/7/2020 31
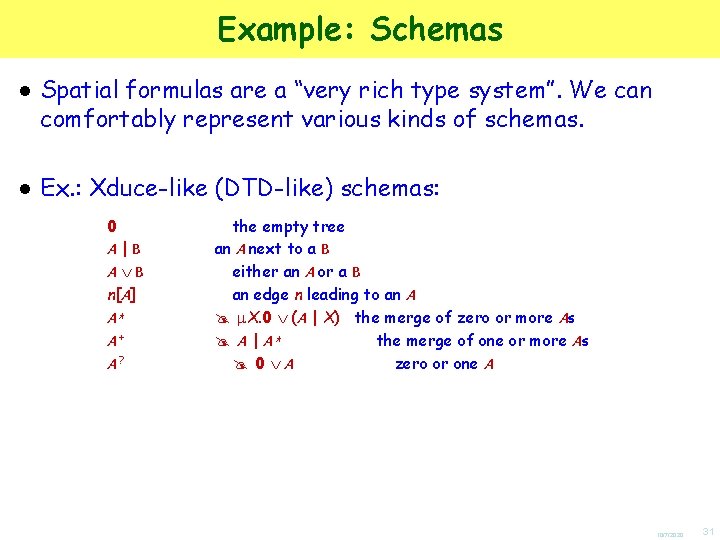
![Future Trends Freely mixing logical descriptions and data spatial logics abA B aC Future Trends ● Freely mixing logical descriptions and data: spatial logics a[b[A B]] a[C]](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-32.jpg)
Future Trends ● Freely mixing logical descriptions and data: spatial logics a[b[A B]] a[C] – Fusion of type systems, query languages, policy specifications, etc. – Lots of open theoretical problems in this area (typing and subtyping algorithms, decidable sublogics, etc. ) 10/7/2020 32
![Data arrays T N T T T Data arrays T : : = | | | N T[] T(…, T, …)](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-33.jpg)
Data arrays T : : = | | | N T[] T(…, T, …) T|T T? T* […, T m, …] closures unions nullables streams tuples (rows) Generalized member access (powerful “. ”) 10/7/2020 33

Protection 10/7/2020 34

Hiding ● Any kind of security/privacy issue has to do with hiding something – Hiding procedures by access control – Hiding data by encryption ● In programming languages: – How can we protect/hide flows? (Security) – How can we protect/hide data? (Privacy) – Exploit the mother of all hiding operators: p-calculus restriction (already widely used in crypto protocol analysis). 10/7/2020 35

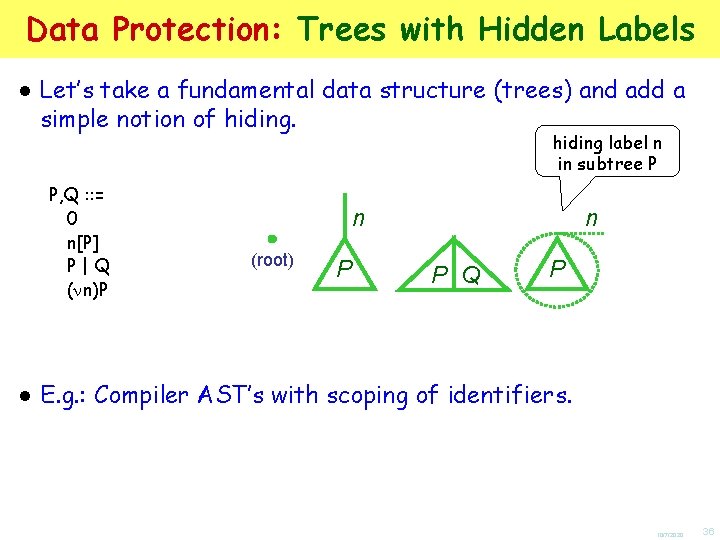
Data Protection: Trees with Hidden Labels ● Let’s take a fundamental data structure (trees) and add a simple notion of hiding. P, Q : : = 0 n[P] P|Q ( n)P hiding label n in subtree P n (root) P n P Q P ● E. g. : Compiler AST’s with scoping of identifiers. 10/7/2020 36

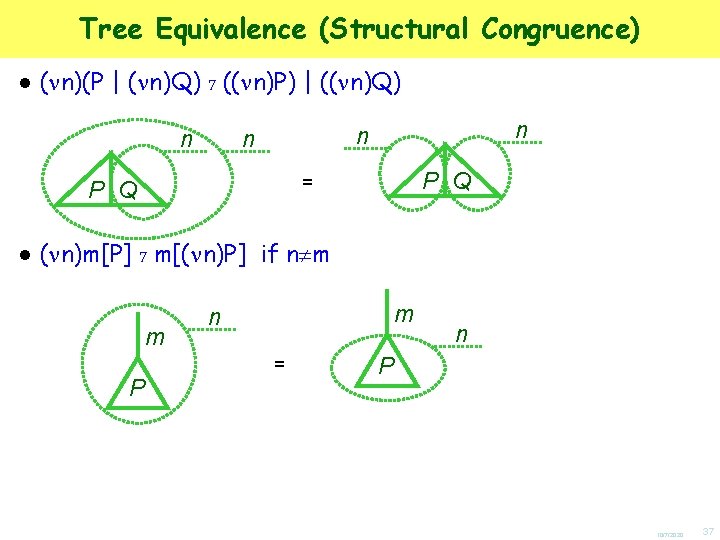
Tree Equivalence (Structural Congruence) ● ( n)(P | ( n)Q) 7 (( n)P) | (( n)Q) n n P Q = P Q ● ( n)m[P] 7 m[( n)P] m if n m m n = P n P 10/7/2020 37

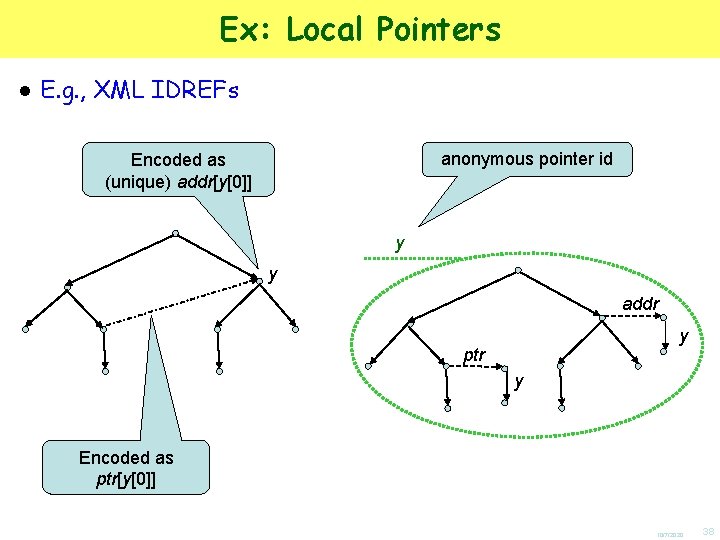
Ex: Local Pointers ● E. g. , XML IDREFs anonymous pointer id Encoded as (unique) addr[y[0]] y y addr y ptr y Encoded as ptr[y[0]] 10/7/2020 38

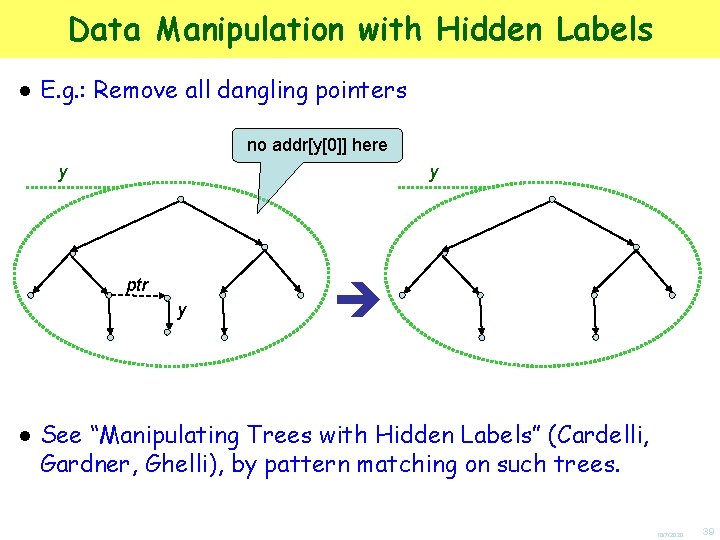
Data Manipulation with Hidden Labels ● E. g. : Remove all dangling pointers no addr[y[0]] here y y ptr y è ● See “Manipulating Trees with Hidden Labels” (Cardelli, Gardner, Ghelli), by pattern matching on such trees. 10/7/2020 39
![Type Systems for Hidden Names my Account Hy idy checkbooky Type Systems for Hidden Names ● my. Account : Hy. … id[y] … checkbook[y]](https://slidetodoc.com/presentation_image/ffdafeb38f98ed568a0c3bf0aea4df7b/image-40.jpg)
Type Systems for Hidden Names ● my. Account : Hy. … id[y] … checkbook[y] … Hiding quantifier ● These are name-dependent types – Dependent types: traditionally very hard to handle because of computational effects. – But dependent only on “pure names”: no computational effects. – Name-dependent types are emerging as a general techniques for handling freshness, hiding, protocols (e. g. Vault), and perhaps security/privacy aspects in type systems. ● As a basis for transformation languages – Well-typed tree transformations that use and generate hidden labels without violating their “anonymity”. 10/7/2020 40

Future Trends ● Hiding as a data structure constructor and as a data type quantifier. 10/7/2020 41

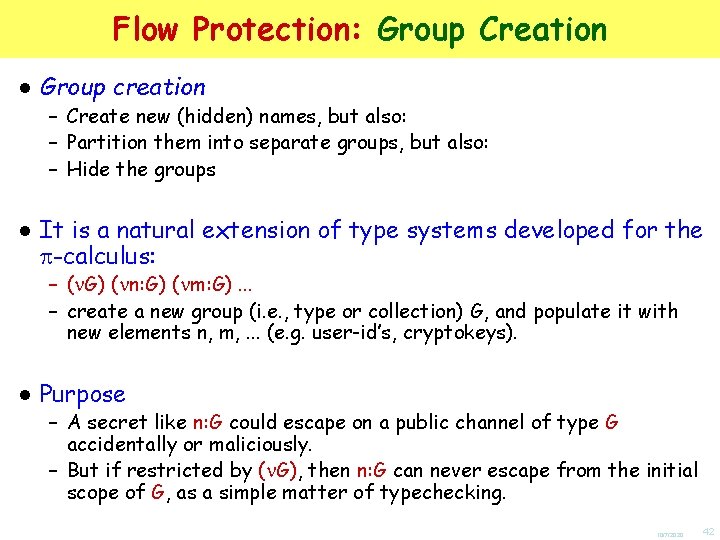
Flow Protection: Group Creation ● Group creation – Create new (hidden) names, but also: – Partition them into separate groups, but also: – Hide the groups ● It is a natural extension of type systems developed for the p-calculus: – ( G) ( n: G) ( m: G). . . – create a new group (i. e. , type or collection) G, and populate it with new elements n, m, . . . (e. g. user-id’s, cryptokeys). ● Purpose – A secret like n: G could escape on a public channel of type G accidentally or maliciously. – But if restricted by ( G), then n: G can never escape from the initial scope of G, as a simple matter of typechecking. 10/7/2020 42

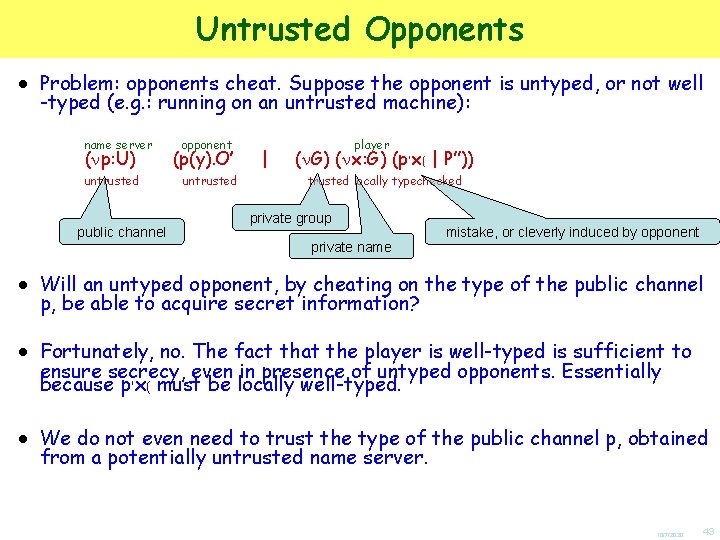
Untrusted Opponents ● Problem: opponents cheat. Suppose the opponent is untyped, or not well -typed (e. g. : running on an untrusted machine): name server ( p: U) untrusted public channel opponent player (p(y). O’ | ( G) ( x: G) (p'x( | P”)) untrusted locally typechecked private group private name mistake, or cleverly induced by opponent ● Will an untyped opponent, by cheating on the type of the public channel p, be able to acquire secret information? ● Fortunately, no. The fact that the player is well-typed is sufficient to ensure secrecy, even in presence of untyped opponents. Essentially because p'x( must be locally well-typed. ● We do not even need to trust the type of the public channel p, obtained from a potentially untrusted name server. 10/7/2020 43

Secrecy Guarantee ● Programmer’s reference manual: Names of group G remain secret, forever, outside the initial scope of ( G). ● Secrecy Theorem (paraphrased) If ( G)( x: …G…)P is well-typed, then P will not leak x even to an untyped (untrusted) opponent. 10/7/2020 44

Future Trends ● Programming constructs that help enforce security properties by typechecking or analysis. 10/7/2020 45

Conclusions 10/7/2020 46

WAN Flows, Data, Protection ● New languages – Language evolution is driven by wishes. – Language adoption is driven by needs. ● We now badly need evolution in areas related to WAN- programming for non-experts (i. e. with language support). – Concurrent flows. ●Applications of Join Calculus. – Semistructured data. ●Applications of Spatial Logics. – Flow and data protection. ●Applications of p-calculus restriction. ● Why all these calculi/logics/blah things? – Formal methods are no longer a complete luxury, in a new world where we increasingly need to guarantee good behavior. 10/7/2020 47

References ● Flows – – Join Calculus: Fournet et al. Polyphonic. C#/ Benton, Cardelli, Fournet. Behave!: Larus et al. Vault: De. Line et al. + Kobayashi, Honda, Yoshida, Vasconcelos, … ● Data – Xen/ : Meijer, Bierman et al. , http: //www. research. microsoft. com/Comega/ – TQL: Cardelli, Ghelli et al. ● Protection – – Fresh-ML: Pitts et al. Secrecy and Groups: Cardelli, Ghelli, Gordon. Trees with Hidden Labels: Cardelli, Gardner, Ghelli. + Type systems for security (many). www. research. microsoft. com/Comega/ 10/7/2020 48

10/7/2020 49

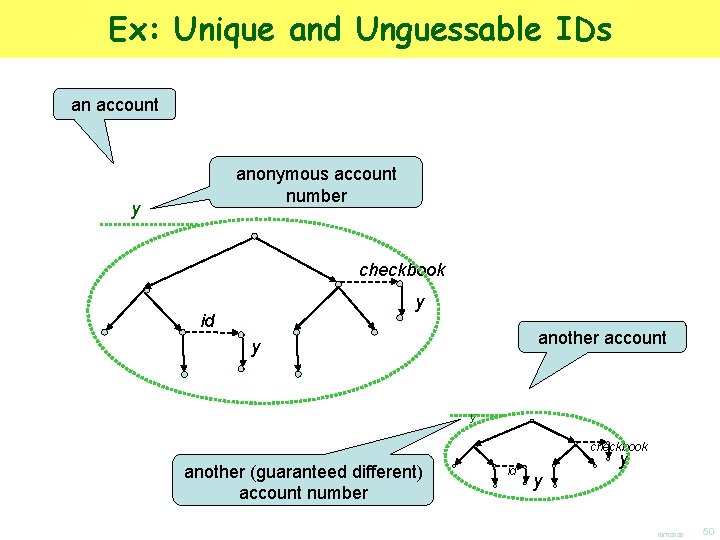
Ex: Unique and Unguessable IDs an account anonymous account number y checkbook y id another account y y checkbook another (guaranteed different) account number id y y 10/7/2020 50

Asynch requests/responses ● Service exposes an async method which takes parameters and somewhere to put the result: – a buffer, or a channel, or – here, an asynchronous delegate, used as a callback. public delegate async Int. CB(int v); // the callback public class Service { public async request(String arg, Int. CB callback){ … // compute result callback(result); // respond! } } 10/7/2020 51

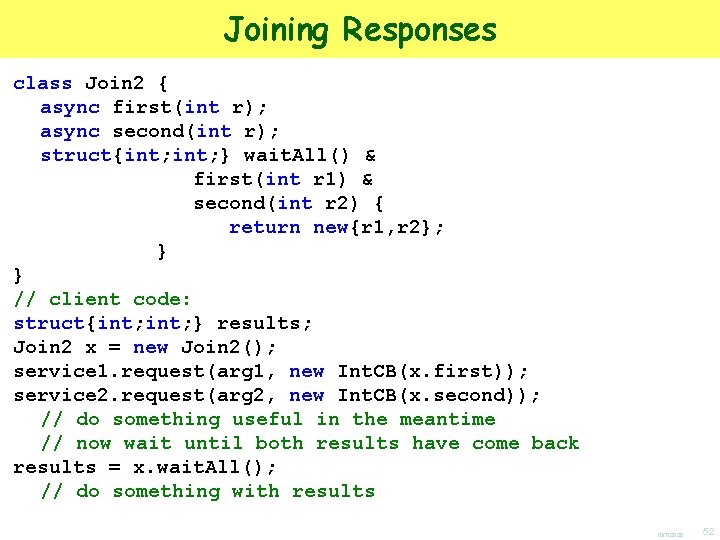
Joining Responses class Join 2 { async first(int r); async second(int r); struct{int; } wait. All() & first(int r 1) & second(int r 2) { return new{r 1, r 2}; } } // client code: struct{int; } results; Join 2 x = new Join 2(); service 1. request(arg 1, new Int. CB(x. first)); service 2. request(arg 2, new Int. CB(x. second)); // do something useful in the meantime // now wait until both results have come back results = x. wait. All(); // do something with results 10/7/2020 52

New Programming Models ● We are in the middle of a transition in programming models (and eventually PLs) – More radical than C to C++ ● Brought more robust data structures (objects) – More radical than C++ to Java ● Brought more robust control flows (strong typing) ● We now have a Cambrian explosion of programming models. – Lots of badly misshaped things are going to evolve before architectures settle down. – What’s on the other side of the transition? 10/7/2020 53

How to Integrate Transitions ● New programming models often require new kinds of analysis. – Domain Specific Languages: PLs equipped with specialized analysis for specific programming models – E. g. SQL (both data and concurrency optimization), security policy languages ● But some transitions go beyond DSL’s – C++ was not just a DSL for objects, and Java was not just a DSL for type safety – Some transitions really require new “general-purpose” languages – We need more than a messaging DSL, an XML DSL, a protection DSL. 10/7/2020 54

State of the Craft ● Java-style monitors ● OS shared memory primitives ● Delegate-based asynchronous callback model ● Hard to understand, use and get right – Concurrency behavior (send/receive) buried inside the program. – Different models at different scales – Support for asynchrony all on the caller side – little help building code to handle messages (must be thread-safe, reactive, and deadlock-free) 10/7/2020 55

Implementation ● ● Translation into thread librarires. Introduce queues for pending calls (holding blocked threads for sync methods, arguments for asyncs). Efficient – bitmasks to look for matches, thread pools. Insulates from nasty underlaying semantic details. 10/7/2020 56

What can we do about this? ● Assumptions – The existing situation is extremely messy ● How many web services have you deployed lately? – Those 3 WAN-related transitions in programming models have a high probability of precipitating into new languages for WAN programming ● Research plan – In view of that, try to make some progress in one or more of those areas 10/7/2020 57

-- Assorted Language-Related Advanced Activities (Microsoft-centric) ● Semistructured Data ● TQL, Spatial Data Types … ● MS: Xen (Erik Meijer, Wolfram Shulte, Herman Venter, …) – Extends C# with XML-like data types and XML query expressions, integrated with real SQL queries. ● Concurrent Flows ● BPEL, Polyphonic C#, Sharpie, Behavioral Types … ● MS: Highwire (Greg Meredith, …) – Distributed scheduling language based on p-calculus and linear logic types. ● Security/Privacy/Protocols ● Samoa, Vault … ● MS: Binder (John De. Treville) – A Logic-Based security language 10/7/2020 58