Towards a Development of a Learners Ratified Acceptance










- Slides: 24

Towards a Development of a Learners’ Ratified Acceptance of Multi-biometrics Intentions Model (RAMIM): Initial Empirical Results By: Yair Levy Nova Southeastern University and Michelle M. Ramim Nova Southeastern University 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 1

Outline • • • Introduction Statement of the problem Objective Theoretical background Proposed initial model and propositions Methodology and sample Data analysis and results Implications Proposed revised model 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 2

Introduction • • • Growing use of organizational electronic records Growing use e-learning Valid authentication of users is a perpetual challenge amongst organizations Authentication should expand beyond the limited username/password verification Reduce misuse and unethical conduct * Source: United States Department of Education, National Center of Educational Statistics (NCES) (2005) 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 3

Introduction (Cont. ) • The use of information security related devices in highly secured environments: – Financial institutions – Government agencies – Military facilities • Expanded utility for management – Employee attendance – Track employee daily activities 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 4

Statement of the problem • A growing concern – Invasiveness of biometric devices – Effective safeguarding of biometric information – Potential misuse of information captured by biometric devices – Increase of identity fraud crimes – Compromising of existing identification methodologies 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 5

Statement of the problem (Cont. ) • • • Context of e-learning systems Issues with academic misconduct A new trend • • • Integrate more than a single biometric method of authentication Increase accuracy Transparency Reliability beyond the initial point of entry Monitoring real-time users’ activity in a non-intrusive manner 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 6

Objectives • • Multi-biometric authentication method Initial empirical results Develop and validate a learners’ Ratified Acceptance of Multi-biometrics Intentions Model (RAMIM). The multi-biometric authentication – Two devices: fingerprint scanner and Web-cam head geometry scanner 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 7

Theoretical Background • Authentication Theory – Authentication is the process whereby the system verifies the user’s identity as declared (Liebl, 1993). – Two principal authentication elements: • • Identification - the user declares their identity Verification - the identity is validated – There are several established authentication protocols (password authentication protocol (PAP), encryption, etc. ) 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 8

Theoretical Background (Cont. ) • User authentication: (Furnell et al. , 2000) – – – • • • Something the user knows (e. g. password or personal identification number (PIN)) Something the user has (e. g. a card, token, etc) Something the user is (e. g. a biometric characteristic) Passwords are the most common authentication method (Oorschot & Thorpe, 2008; Rodwell, Furnell, & Reynolds, 2007) Passwords tend to be undermined by users Promote additional authentication methods – – Physiological and behavioral biometrics Multiple means of authentications 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 9

Theoretical Background (Cont. ) • Biometrics - a process that examines unique biological characteristics of humans (James et al. , 2006) – – – • DNA, voice, retinal and iris, fingerprints, facial images, hand prints, or other unique biological characteristics Biometric technologies operate by scanning a biological characteristic and matching it with the stored data Behavioral characteristics - keystrokes dynamics, and mouse clicks (Sasamoto et al. , 2008; Pusara & Brodley, 2004) Further work is needed to commercialize such methods to large scale systems. 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 10

Multi-Biometrics • A multilateral model scheme that utilizes a mixture of two or more biological and/or physiological characteristics that the end-user has in a secured environment • Multi-biometrics can enable ongoing nonintrusive verification not only at the point of entry but also throughout the logged-in session. • Use in various corporate and e-learning situations. • The context outlined here is during e-exams. 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 11

Users’ Acceptance of Technology • Challenges in experiments with biometrics • Before moving to experiments with actual systems, seek better understanding of the acceptance of such systems by the users (Venkatesh et al. , 2003) • Users’ perceived usefulness and ease-of-use are strong predictors of technology acceptance (Davis, 1989; Simon & Paper, 2007; Venkatesh et al. , 2003; Viswanath & Hillol, 2008). – Theory of Reasoned Action (TRA) (Ajzen & Fishbein, 1980). • Intention to use a technology is a significant predictor of actual use (Bagozzi, 2007; Gefen et al. , 2003) 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 12

Ethical Decision Making • Users’ ethical decisions making • Ethical issues with the use of e-learning systems have been a growing concern • Users who are more ethically driven will be open to accept multi-biometrics • Learners who are more ethically driven will be more inclined to use multi-biometrics during eexams. 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 13

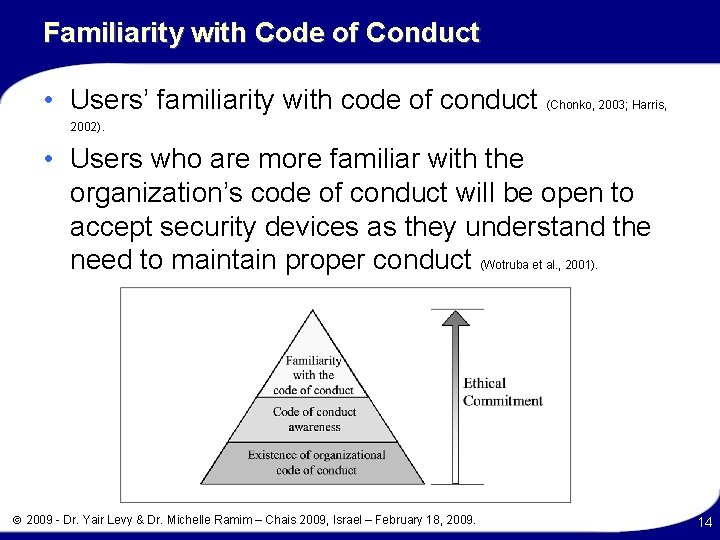
Familiarity with Code of Conduct • Users’ familiarity with code of conduct (Chonko, 2003; Harris, 2002). • Users who are more familiar with the organization’s code of conduct will be open to accept security devices as they understand the need to maintain proper conduct (Wotruba et al. , 2001). 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 14

Proposed Initial Model 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 15

Propositions P 1: Learners’ familiarity with university’s code of conduct will have a significant positive contribution to their intention to use multi-biometrics for authentication during e-learning exams. P 2: Learners’ perceived ease-of-use will have a significant positive contribution to their intention to use multibiometrics for authentication during e-learning exams. P 3: Learners’ perceived usefulness will have a significant positive contribution to their intention to use multibiometrics for authentication during e-learning exams. P 4: Learners’ ethical decision making will have a significant positive contribution to their intention to use multibiometrics for authentication during e-learning exams. 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 16

Methodology • Use of validated measures from prior literature – Perceived ease-of-use, perceived usefulness, and intention to use were adopted (Gefen et al. , 2003; James et al. , 2006). – Familiarity with the code of conduct and ethical decision making (Ramim, 2007). • All items used 5 -point Likert-type scale. • Survey items were specifically in the context of intention to use multi-biometrics for authentication during e-learning exams. • Used Ordinal Logistic Regression (OLR) for initial data. Plan to use Structural Equations Modeling (SEM) in the future. 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 17

Sample • The sample: 97 entry level managers from service oriented organization and government agencies in USA who attended e-learning Masters of Business Administration (MBA) and Masters of Public Administration (MPA) courses. • Gender distribution: 61% males and 39% females • About 60% between the ages of 19 -34. • Majority (above 81%) had previously taken two or more e-learning courses 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 18

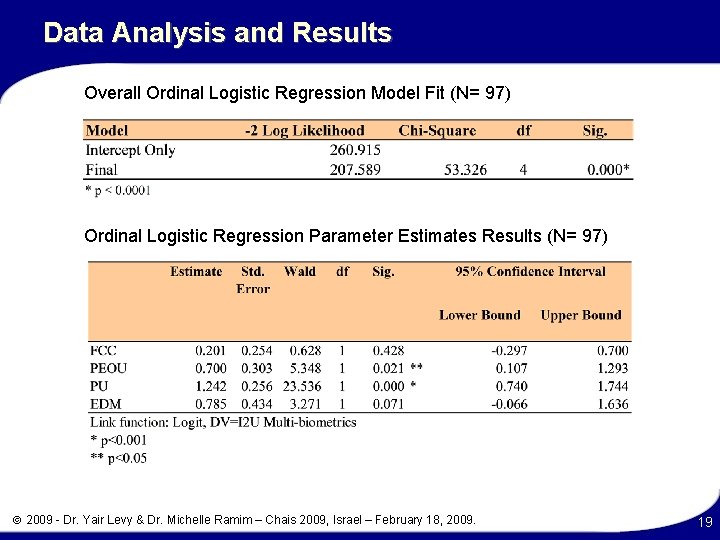
Data Analysis and Results Overall Ordinal Logistic Regression Model Fit (N= 97) Ordinal Logistic Regression Parameter Estimates Results (N= 97) 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 19

Data Analysis and Results (Cont. ) 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 20

Proposed Revised Model 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 21

Thank you! • Questions? 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 22

Contact Information - Michelle M. Ramim, Ph. D. Part-time Professor Nova Southeastern University H. Wayne Huizenga School of Business and Entrepreneurship The De. Santis Building 3301 College Avenue Ft. Lauderdale, FL 33314 E-mail: ramim@nova. edu Site: http: //www. nova. edu/~ramim/ 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 23

Contact Information - Yair Levy, Ph. D. Associate Professor Nova Southeastern University Graduate School of Computer and Information Sciences The De. Santis Building - Room 4058 3301 College Avenue Fort Lauderdale, FL 33314 Tel. : 954 -262 -2006 Fax: 954 -262 -3915 E-mail: levyy@nova. edu Site: http: //scis. nova. edu/~levyy/ 2009 - Dr. Yair Levy & Dr. Michelle Ramim – Chais 2009, Israel – February 18, 2009. 24