Toward SecurityManaged Virtual Science Networks Jeff Chase Duke















![Secure Routing Owner roa( IP, AS 0) AS 0 advertise (IP, [AS 0], AS Secure Routing Owner roa( IP, AS 0) AS 0 advertise (IP, [AS 0], AS](https://slidetodoc.com/presentation_image/1ae13ae825b40b352797999da8b8fe6a/image-37.jpg)


- Slides: 46

Toward Security-Managed Virtual Science Networks Jeff Chase Duke University Paul Ruth RENCI - UNC Chapel Hill Collaborators: Nick Buraglio (ESnet); Mert Cevik, Cong Wang (RENCI); Yuanjun Yao, Qiang Cao, Rubens Farias (Duke); Victor Orlikowski, Charley Kneifel (Duke OIT).

This material is based upon work supported by the US National Science Foundation under Grants No. (ACI-1642140, ACI 1642142, CNS-1330659, CNS-1243315) and through the Global Environment for Network Innovations (GENI) program. Any opinions, findings, and conclusions or recommendations do not necessarily reflect the views of NSF. 2

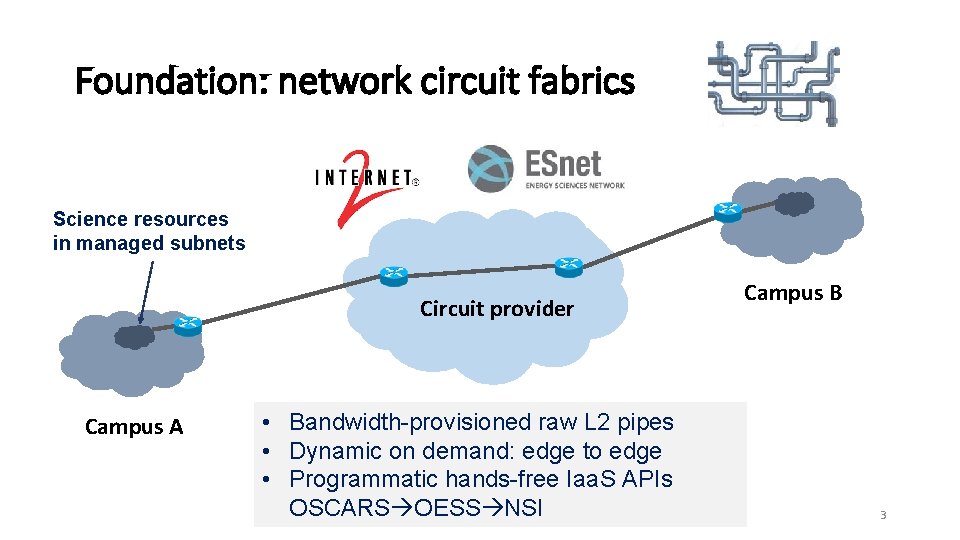
Foundation: network circuit fabrics Science resources in managed subnets Circuit provider Campus A • Bandwidth-provisioned raw L 2 pipes • Dynamic on demand: edge to edge • Programmatic hands-free Iaa. S APIs OSCARS OESS NSI Campus B 3

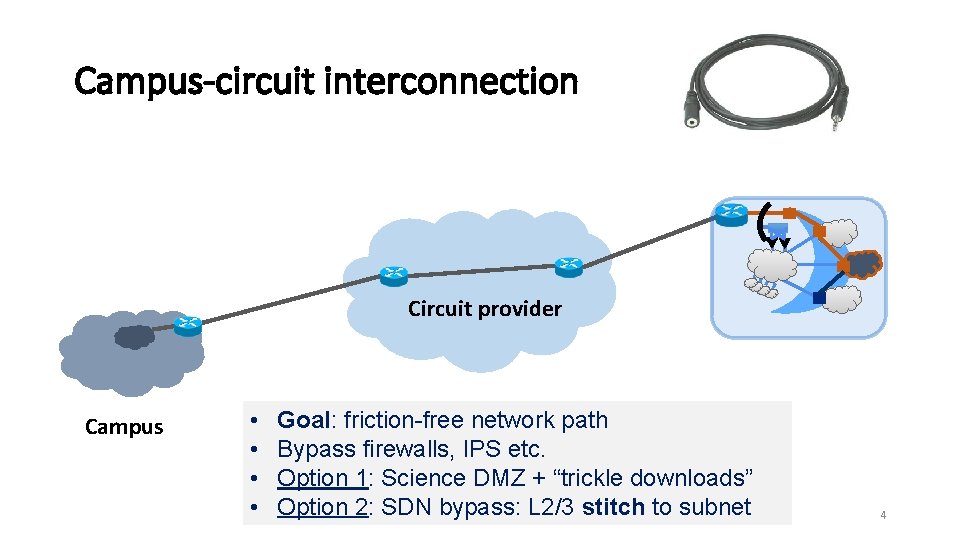
Campus-circuit interconnection Circuit provider Campus • • Goal: friction-free network path Bypass firewalls, IPS etc. Option 1: Science DMZ + “trickle downloads” Option 2: SDN bypass: L 2/3 stitch to subnet 4

5

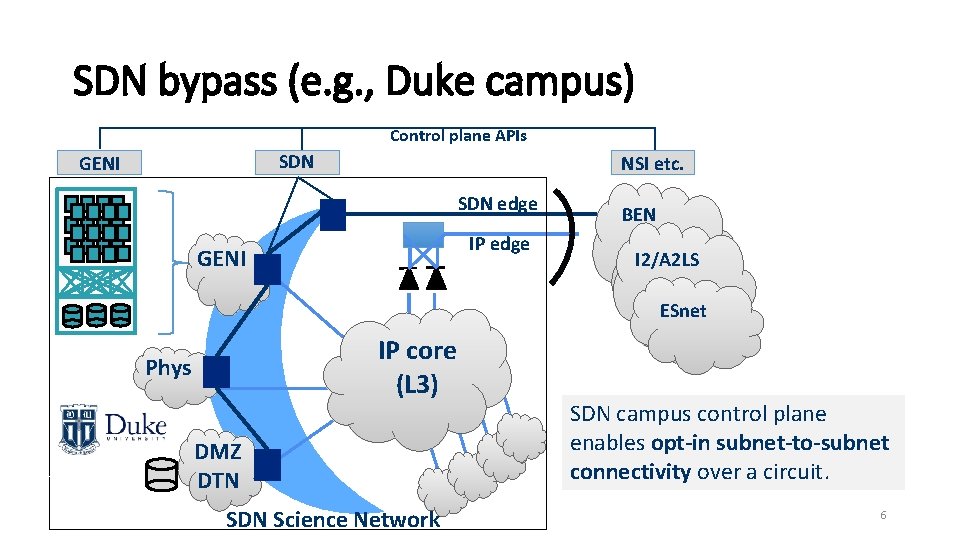
SDN bypass (e. g. , Duke campus) Control plane APIs SDN GENI NSI etc. SDN edge IP edge GENI BEN I 2/A 2 LS ESnet IP core (L 3) Phys DMZ DTN SDN Science Network SDN campus control plane enables opt-in subnet-to-subnet connectivity over a circuit. 6

Virtual Science Networks: the vision Idea: Use circuits to create a private network provisioned to link multiple resources/subnets. Super-facility Testbed slice Campus • • • Cross-campus collaborations Facility access Examples: cluster, LCF, testbed Resource sharing Virtual data enclaves Live network services LCF site Deep network programmability • Routing control • Security monitoring / NFV • Dynamic peering • Topology adaptation • Elastic edge clouds 7

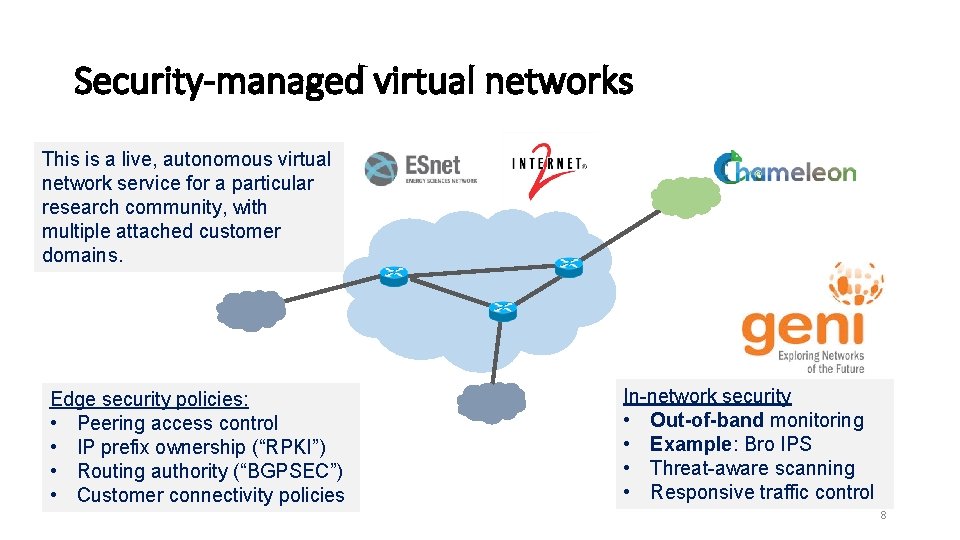
Security-managed virtual networks This is a live, autonomous virtual network service for a particular research community, with multiple attached customer domains. Edge security policies: • Peering access control • IP prefix ownership (“RPKI”) • Routing authority (“BGPSEC”) • Customer connectivity policies In-network security • Out-of-band monitoring • Example: Bro IPS • Threat-aware scanning • Responsive traffic control 8

Cabo economic refactoring: “Decouple infrastructure providers from service providers, who offer end-to-end services. ” Nick Feamster

End-to-End Services • Multi-provider VPNs • Paths with end-to-end performance guarantees Today Competing ISPs with different goals must coordinate Cabo Single service provider controls end -to-end path 10

Overview: vision and approach Build an architecture and platform for: • Built-to-order virtual science networks • An application of virtual Network Service Providers (v. NSPs) • Subnet-to-subnet fast-path connectivity across campus boundaries • Security management with declarative policy, e. g. , for virtual data enclaves Elements of approach: • SAFE logical trust system: logic certificates and policy rules • Leverage national research fabrics and NSF-funded CI. • Use GENI resources (for now) for v. NSP routing and security. • Specifically: built-to-order virtual network slices on Exo. GENI

https: //arxiv. org/pdf/1803. 09886. pdf 12

Exo. GENI § 23 Open. Stack cloud sites § GENI API 13

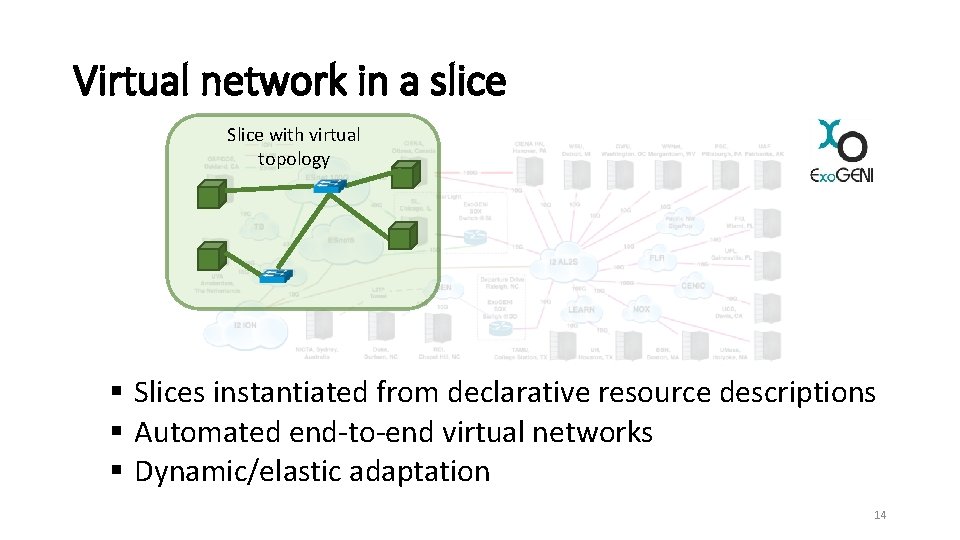
Virtual network in a slice Slice with virtual topology § Slices instantiated from declarative resource descriptions § Automated end-to-end virtual networks § Dynamic/elastic adaptation 14

Elastic slice controllers: Ahab Slice with virtual topology § Ahab controller architecture § Provision VMs and pipes § Instantiate slice and adapt the slice over time 15

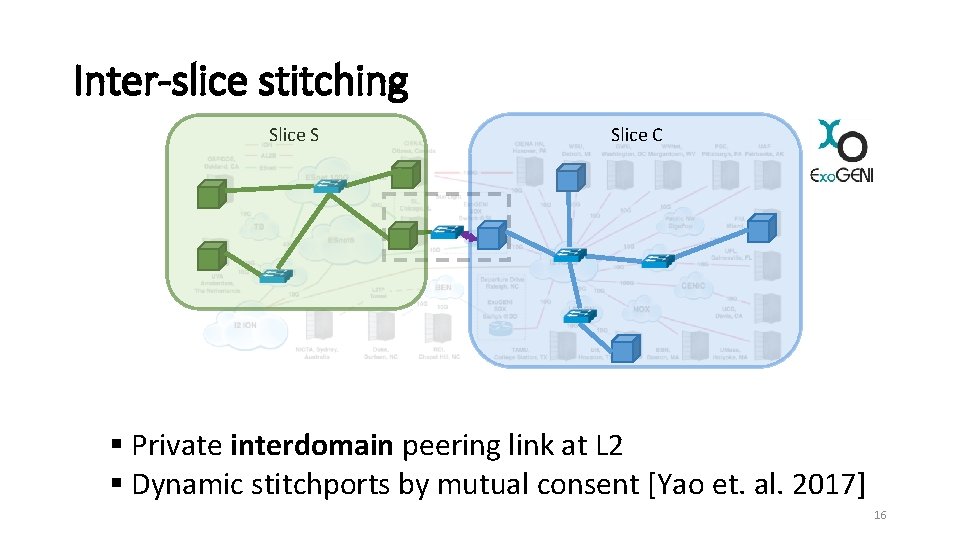
Inter-slice stitching Slice S Slice C § Private interdomain peering link at L 2 § Dynamic stitchports by mutual consent [Yao et. al. 2017] 16

Stitching to external resources v. NSP (slice) Client subnet (campus) Client subnet (slice) 17

Ahab slice controllers Slice s = Slice. create(slice. Proxy, slice. Context, “My. Slice”); Compute. Node node 0 = s. add. Compute. Node(“node 0”); node 0. set. Image(image. URL, image. Hash, image. Name); node 0. set. Domain(domain. Name); node 0. set. Node. Type(“XO Medium”); My. Slice net 0 node 0 stitch. Port 0 Client subnet (campus) Stitch. Port sp = s. add. Stitch. Port(”stitch. Port 0"); sp. set. Label(” 690"); sp. set. Port("http: //geni-orca. renci. org/owl/ion. rdf#AL 2 S/Duke/Cisco/6509/Ten. Gigabit. Ethernet/1/1/ethernet"); Network net 0 = s. add. Broadcast. Link("net 0"); net 0. stitch(node 0); net 0. stitch(sp); s. commit(); 18

Virtual Network Service Provider (v. NSP) 19

Exo. Plex platform 20

Customer peering: stitching 21

Connectivity: dynamic network resources 22

Secure routing and IP prefix ownership 23

Embedded NFV service chain 24

Example v. NSP: v. SDX Ø Virtual SDX § Distributed: many points of presence to attach customers § Elastic backplane: allocate/release network resources dynamically 25

Example v. NSP: v. SDX § Clients: 2 Chameleon slices, 2 Exo. GENI Slices 26

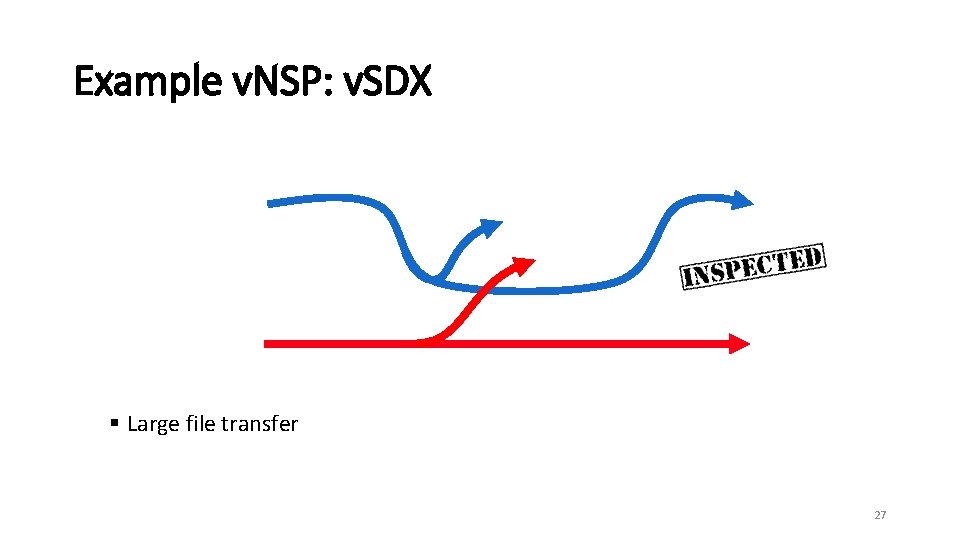
Example v. NSP: v. SDX § Large file transfer 27

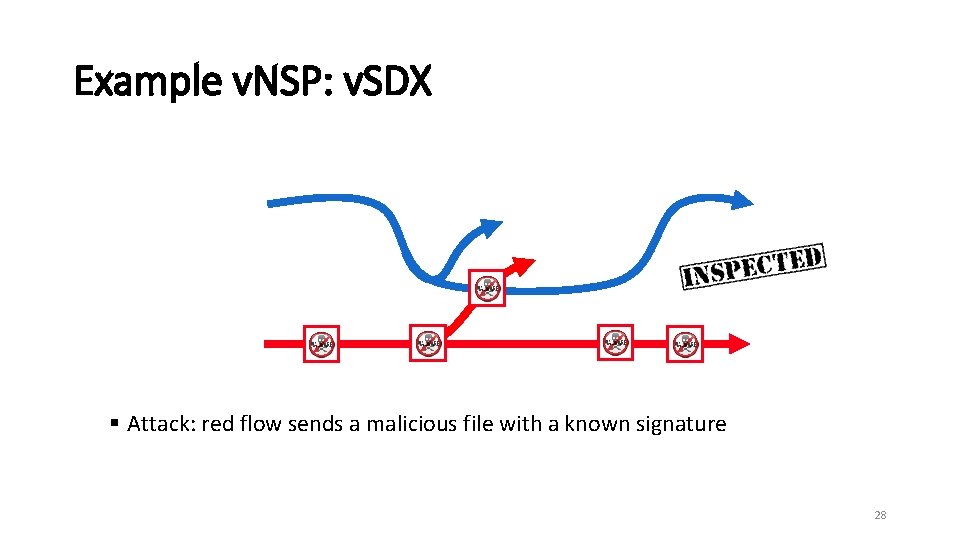
Example v. NSP: v. SDX § Attack: red flow sends a malicious file with a known signature 28

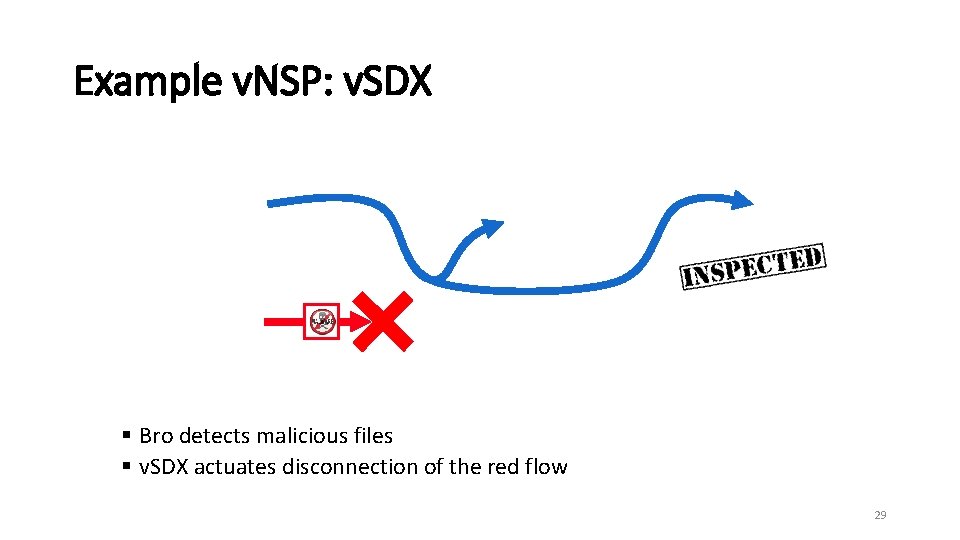
Example v. NSP: v. SDX § Bro detects malicious files § v. SDX actuates disconnection of the red flow 29

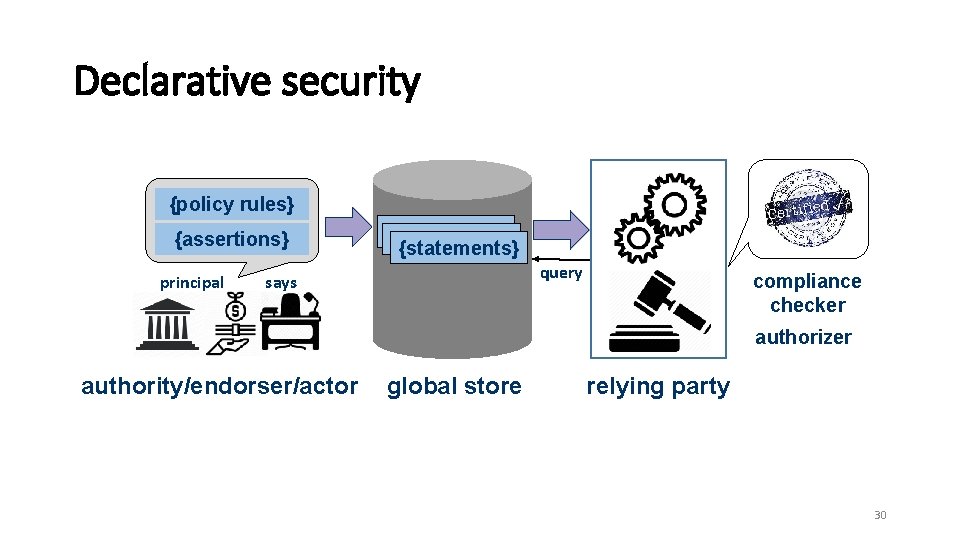
Declarative security {policy rules} {assertions} principal {statements} query says compliance checker authorizer authority/endorser/actor global store relying party 30

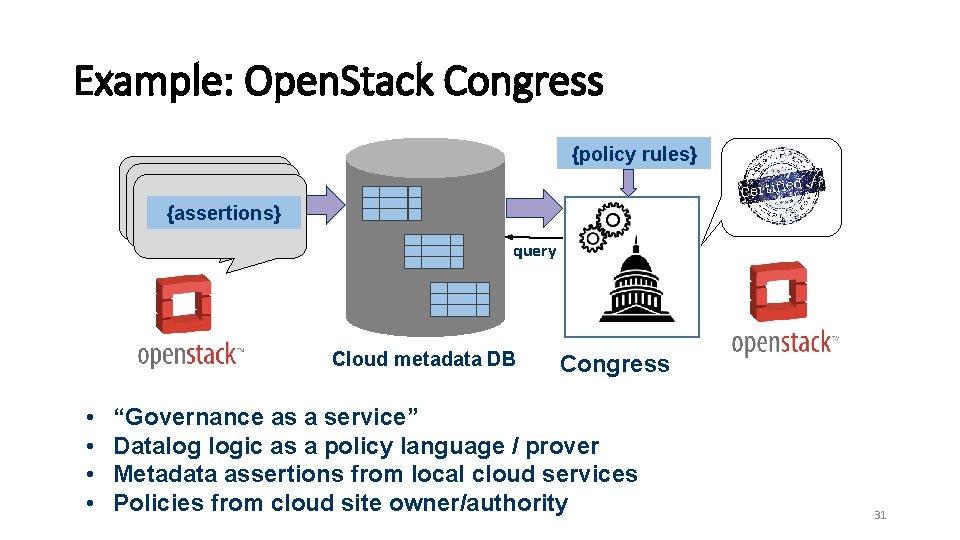
Example: Open. Stack Congress {policy rules} {assertions} query Cloud metadata DB • • Congress “Governance as a service” Datalog logic as a policy language / prover Metadata assertions from local cloud services Policies from cloud site owner/authority 31

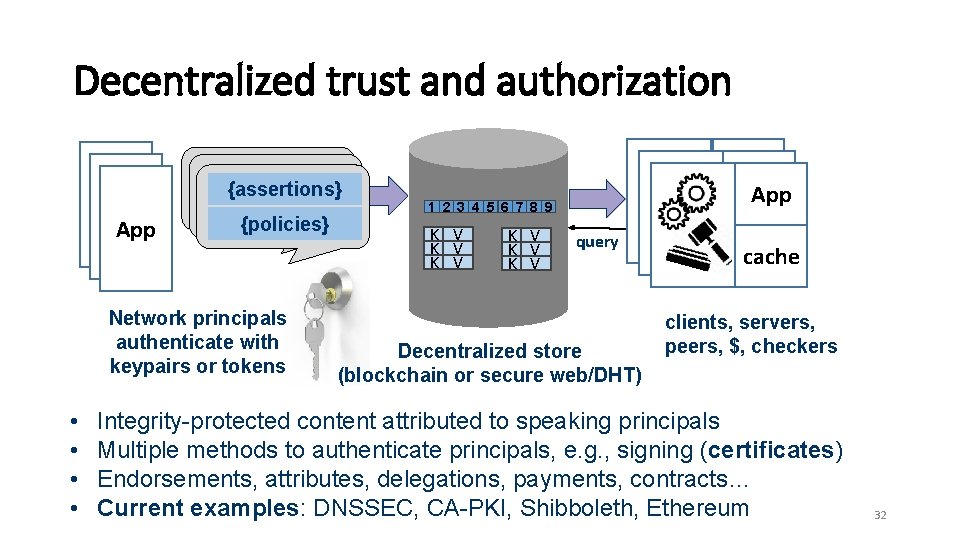
Decentralized trust and authorization {assertions} App {policies} Network principals authenticate with keypairs or tokens • • App 1 2 3 4 5 6 7 8 9 K V K V K V query Decentralized store (blockchain or secure web/DHT) cache clients, servers, peers, $, checkers Integrity-protected content attributed to speaking principals Multiple methods to authenticate principals, e. g. , signing (certificates) Endorsements, attributes, delegations, payments, contracts… Current examples: DNSSEC, CA-PKI, Shibboleth, Ethereum 32

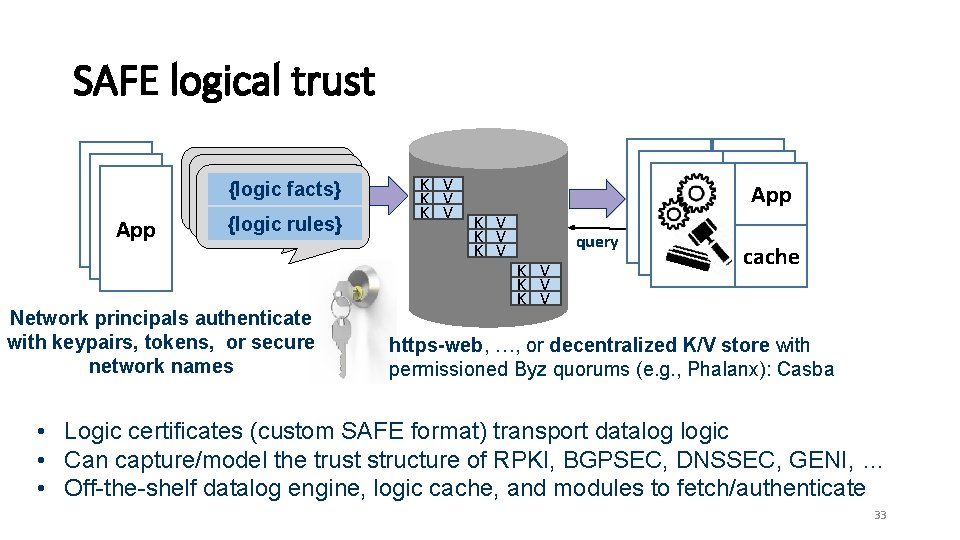
SAFE logical trust {logic facts} App {logic rules} Network principals authenticate with keypairs, tokens, or secure network names K V K V App K V K V query K V K V cache https-web, …, or decentralized K/V store with permissioned Byz quorums (e. g. , Phalanx): Casba • Logic certificates (custom SAFE format) transport datalog logic • Can capture/model the trust structure of RPKI, BGPSEC, DNSSEC, GENI, … • Off-the-shelf datalog engine, logic cache, and modules to fetch/authenticate 33

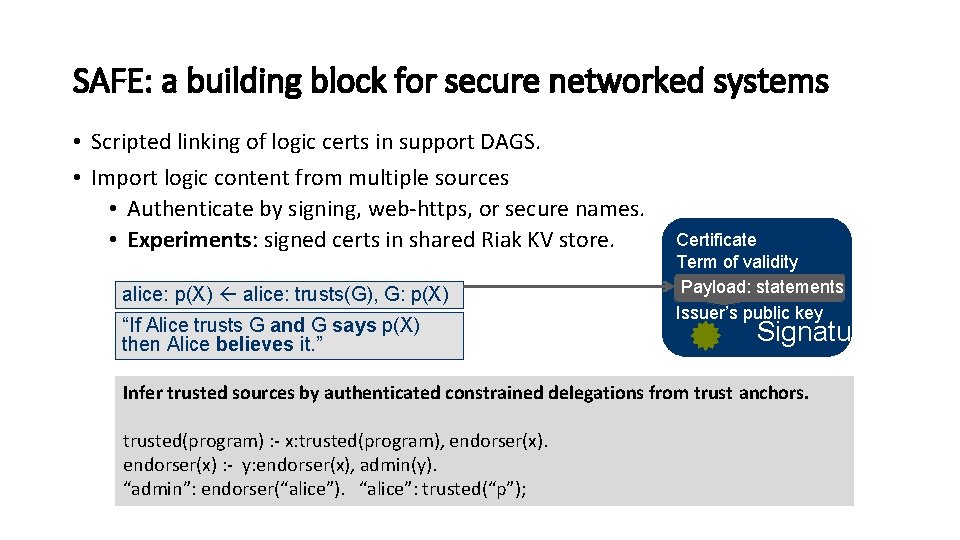
SAFE: a building block for secure networked systems • Scripted linking of logic certs in support DAGS. • Import logic content from multiple sources • Authenticate by signing, web-https, or secure names. • Experiments: signed certs in shared Riak KV store. alice: p(X) alice: trusts(G), G: p(X) “If Alice trusts G and G says p(X) then Alice believes it. ” Certificate Term of validity Payload: statements Issuer’s public key Signature Infer trusted sources by authenticated constrained delegations from trust anchors. trusted(program) : - x: trusted(program), endorser(x) : - y: endorser(x), admin(y). “admin”: endorser(“alice”). “alice”: trusted(“p”);

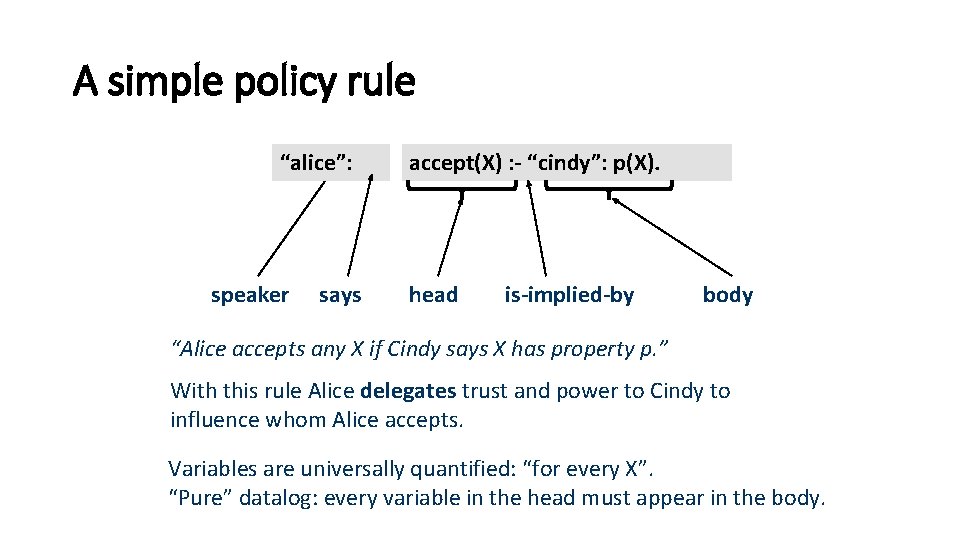
A simple policy rule “alice”: speaker says accept(X) : - “cindy”: p(X). head is-implied-by body “Alice accepts any X if Cindy says X has property p. ” With this rule Alice delegates trust and power to Cindy to influence whom Alice accepts. Variables are universally quantified: “for every X”. “Pure” datalog: every variable in the head must appear in the body.

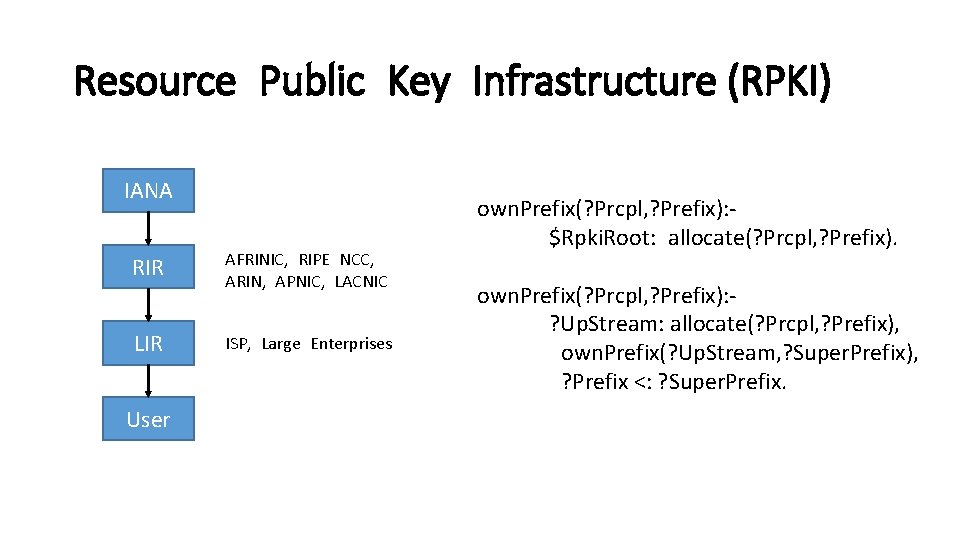
Resource Public Key Infrastructure (RPKI) IANA RIR AFRINIC, RIPE NCC, ARIN, APNIC, LACNIC LIR ISP, Large Enterprises User own. Prefix(? Prcpl, ? Prefix): $Rpki. Root: allocate(? Prcpl, ? Prefix). own. Prefix(? Prcpl, ? Prefix): ? Up. Stream: allocate(? Prcpl, ? Prefix), own. Prefix(? Up. Stream, ? Super. Prefix), ? Prefix <: ? Super. Prefix.
![Secure Routing Owner roa IP AS 0 AS 0 advertise IP AS 0 AS Secure Routing Owner roa( IP, AS 0) AS 0 advertise (IP, [AS 0], AS](https://slidetodoc.com/presentation_image/1ae13ae825b40b352797999da8b8fe6a/image-37.jpg)
Secure Routing Owner roa( IP, AS 0) AS 0 advertise (IP, [AS 0], AS 1) authorized. Advertise(? Dst. IP, ? Path, ? Dst. AS): eq([? Advertiser|? Tail], ? Path), ? Tail ==[], ? Advertiser: advertise(? Dst. IP, ? Path, ? AS), ? Owner: roa(? Dst. IP, ? Advertiser), own. Prefix(? Owner, ? Dst. IP). AS 1 advertise (IP, [AS 1, AS 0], AS 2) AS 2 authorized. Advertise(? Dst. IP, ? Path, ? Dst. AS): eq([? Advertiser|? Tail], ? Path), ? Tail ==[], ? Advertiser: advertise(? Dst. IP, ? Path, ? AS), authorized. Advertise(? Dst. IP, ? Tail, ? Advertiser).

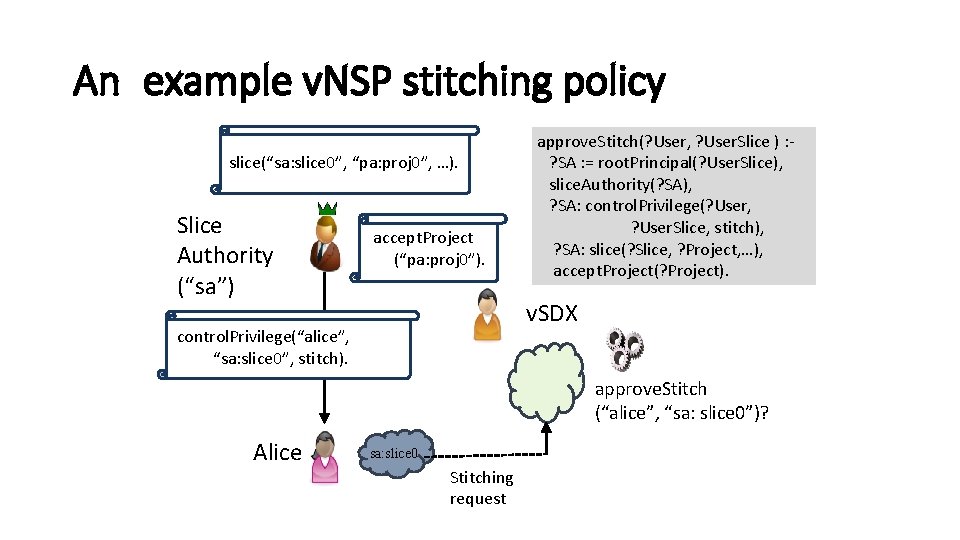
An example v. NSP stitching policy slice(“sa: slice 0”, “pa: proj 0”, …). Slice Authority (“sa”) accept. Project (“pa: proj 0”). approve. Stitch(? User, ? User. Slice ) : ? SA : = root. Principal(? User. Slice), slice. Authority(? SA), ? SA: control. Privilege(? User, ? User. Slice, stitch), ? SA: slice(? Slice, ? Project, …), accept. Project(? Project). v. SDX control. Privilege(“alice”, “sa: slice 0”, stitch). approve. Stitch (“alice”, “sa: slice 0”)? Alice sa: slice 0 Stitching request

SAFE authorization: connectivity § Connectivity authorization § User-based § Project-based 39

Conclusion Ø Exo. Plex for deploying network service providers on testbeds Ø A configurable, security-managed virtual SDX on Exo. GENI Ø Experiments with slices on Exo. GENI and Chameleon 40

This work is partially supported by NSF awards OAC-1642140 and OAC-1642142. https: //github. com/RENCI-NRIG/SAFE. git under branch cnert-2018 41

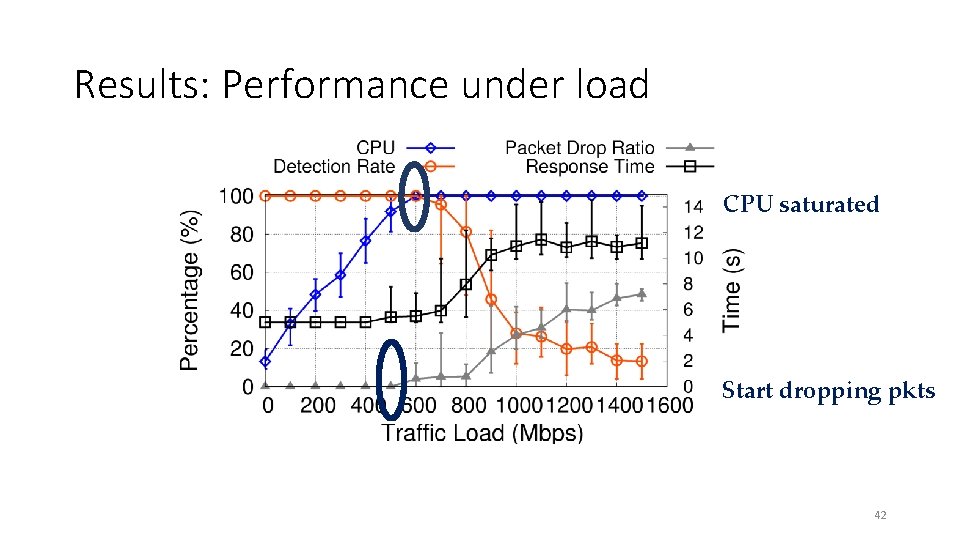
Results: Performance under load CPU saturated Start dropping pkts 42

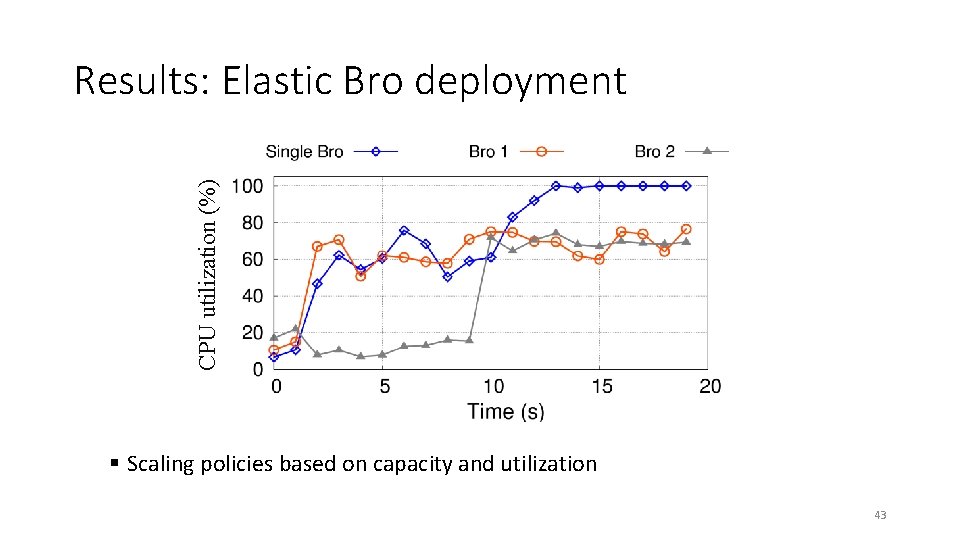
CPU utilization (%) Results: Elastic Bro deployment § Scaling policies based on capacity and utilization 43

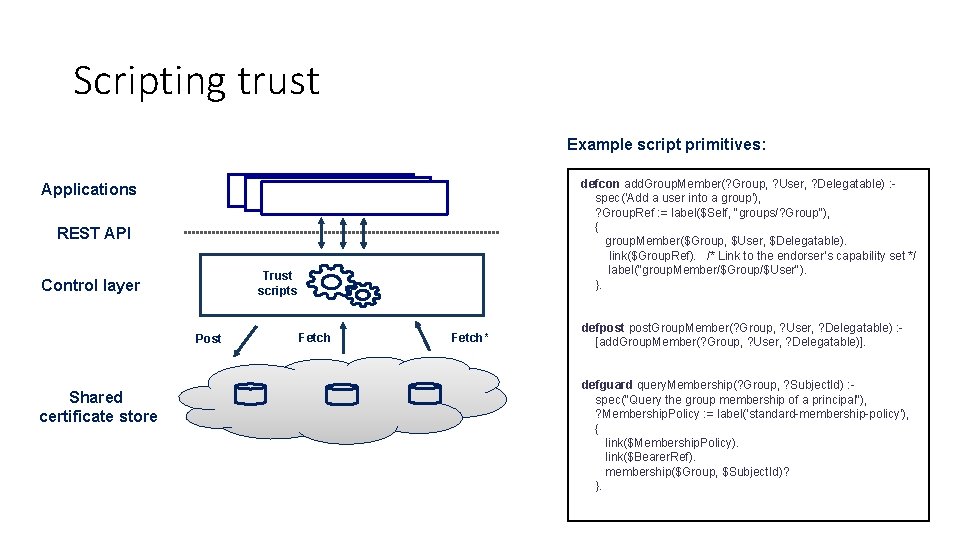
Scripting trust Example script primitives: defcon add. Group. Member(? Group, ? User, ? Delegatable) : spec('Add a user into a group'), ? Group. Ref : = label($Self, "groups/? Group"), { group. Member($Group, $User, $Delegatable). link($Group. Ref). /* Link to the endorser’s capability set */ label("group. Member/$Group/$User"). }. Applications REST API Trust scripts Control layer Post Shared certificate store Fetch* defpost. Group. Member(? Group, ? User, ? Delegatable) : [add. Group. Member(? Group, ? User, ? Delegatable)]. defguard query. Membership(? Group, ? Subject. Id) : spec("Query the group membership of a principal"), ? Membership. Policy : = label('standard-membership-policy'), { link($Membership. Policy). link($Bearer. Ref). membership($Group, $Subject. Id)? }.

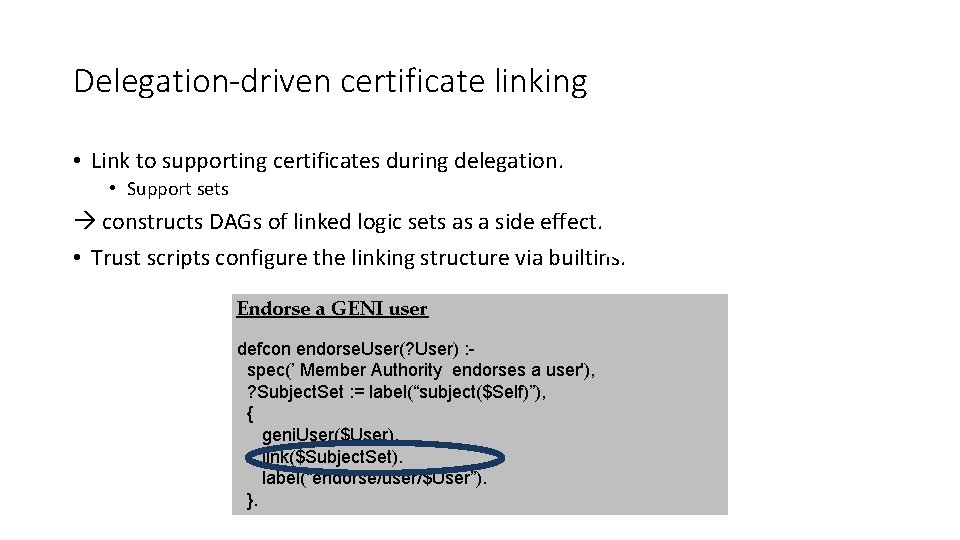
Delegation-driven certificate linking • Link to supporting certificates during delegation. • Support sets constructs DAGs of linked logic sets as a side effect. • Trust scripts configure the linking structure via builtins. Endorse a GENI user defcon endorse. User(? User) : spec(’ Member Authority endorses a user'), ? Subject. Set : = label(“subject($Self)”), { geni. User($User). link($Subject. Set). label(“endorse/user/$User”). }.

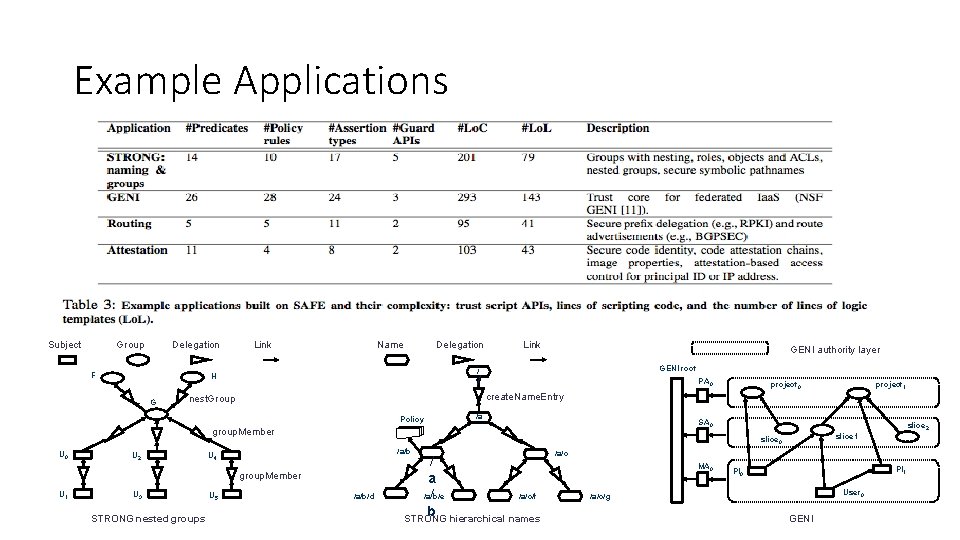
Example Applications Subject Group Delegation F Link Name Delegation GENI authority layer GENI root / H G Link / PA 0 /a SA 0 group. Member U 2 U 3 /a/b U 4 STRONG nested groups U 5 slice 2 slice 1 slice 0 group. Member U 1 project 1 create. Name. Entry nest. Group Policy U 0 project 0 /a/b/d / a /a/b/e /a/c/f / b STRONG hierarchical names /a/c MA 0 PI 1 PI 0 User 0 /a/c/g GENI