Topics Network topology Virtual LAN Port scanners and







- Slides: 15

Topics • • • Network topology Virtual LAN Port scanners and utilities Packet sniffers Weak protocols Practical exercise

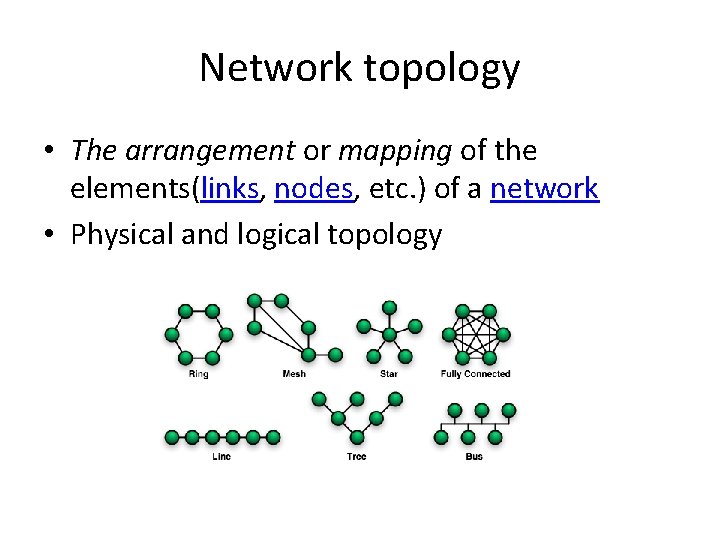
Network topology • The arrangement or mapping of the elements(links, nodes, etc. ) of a network • Physical and logical topology

Layer 3 details • IP addresses • Subnetting – Subnet mask • Gateways and route information • Getting adjacency info • Relaxed security enforcement between machines on the same subnet

Virtual LAN • “…. a group of hosts with a common set of requirements that communicate as if they were attached to the Broadcast domain, regardless of their physical location. ” • Software for network reconfiguration • Traffic segmentation and easy relocations

Layer 4 - Transport • Ports and Services • Common services listen to well-known ports – IANA – Easy to organize using well-known ports • Target for attackers • Vulnerable services • Port scanning

nmap utility • Free, open source utility for network exploration • Uses IP packets to determine what hosts are available and up on a network – Port information; Services offered – Versioning information – Used by sysadmins for

Packet Analyzers • Network protocol analyzer • Interactively browse packet data from a live network • tcpdump, netstat • GUIs exist

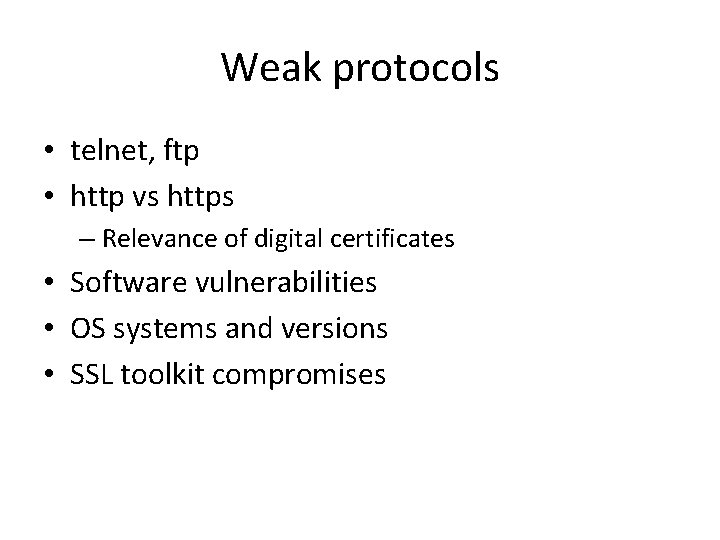
Weak protocols • telnet, ftp • http vs https – Relevance of digital certificates • Software vulnerabilities • OS systems and versions • SSL toolkit compromises

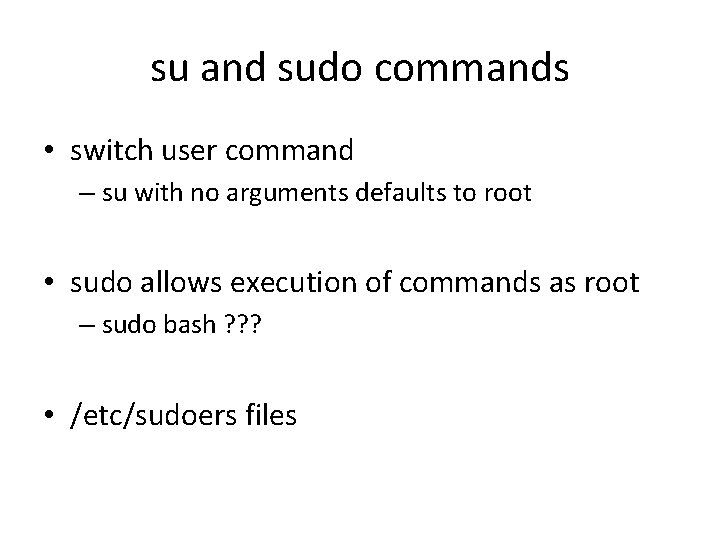
su and sudo commands • switch user command – su with no arguments defaults to root • sudo allows execution of commands as root – sudo bash ? ? ? • /etc/sudoers files

Firewalls • iptables program – Packet filtering • Control traffic flow from and to the system – Rule chains – Targets – Session states • /etc/sysconfig/iptables – sudo iptables -L

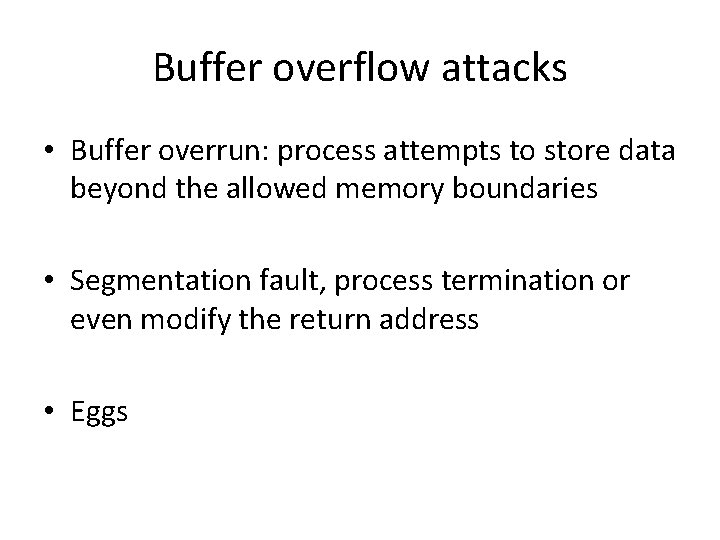
Buffer overflow attacks • Buffer overrun: process attempts to store data beyond the allowed memory boundaries • Segmentation fault, process termination or even modify the return address • Eggs

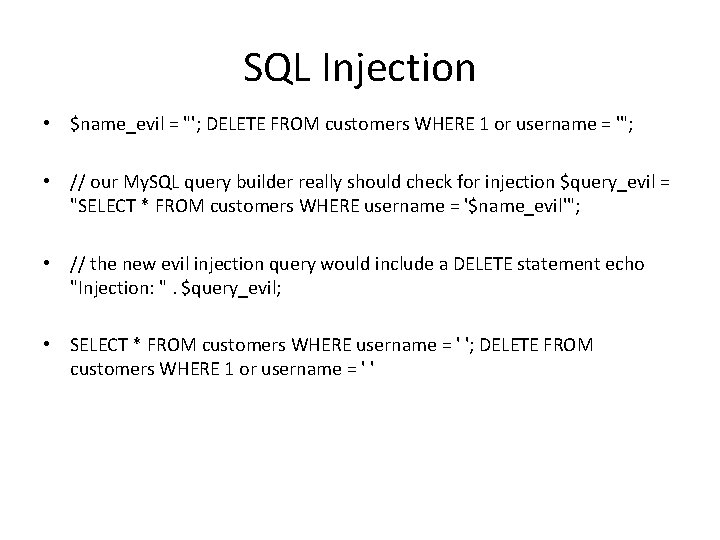
SQL Injection • $name_evil = "'; DELETE FROM customers WHERE 1 or username = '"; • // our My. SQL query builder really should check for injection $query_evil = "SELECT * FROM customers WHERE username = '$name_evil'"; • // the new evil injection query would include a DELETE statement echo "Injection: ". $query_evil; • SELECT * FROM customers WHERE username = ' '; DELETE FROM customers WHERE 1 or username = ' '

Homework Exercises 1 – Due March 6, 2009 • Get an account on the CS Linux servers and run nmap to gain an understanding on the network, the services available for access, their versioning information. • Explain how you can write to /etc/passwd file using passwd command though you do not have rights (as the regular user) to modify the contents of the file.

Homework Exercise 2 – Due March 13, 2006, 5 pm • Create a firewall rule (iptables) to allow Remote desktop connections to the server optimus. cs. uh. edu only if the connection is from on-campus. • Explain if the http support in gmail still maintains the privacy of email communication between the browser and gmail server.

Homework Exercise 3 – Due March 23, 2009 at 1 pm • Even if two users have identical passwords, the hashes of their passwords in the /etc/passwd file or /etc/shadow file are different. How is this done and why is it done? Explain in not more than a page.
 What is topology in computer
What is topology in computer Scanners produce text and graphics on a physical medium
Scanners produce text and graphics on a physical medium Definetion of computer
Definetion of computer Lan topology types
Lan topology types Lan topology
Lan topology Aufbau eines scanners
Aufbau eines scanners Scanners input devices
Scanners input devices Scanners multi-coupes
Scanners multi-coupes Difference between virtual circuit and datagram subnet
Difference between virtual circuit and datagram subnet Camera with lan port
Camera with lan port 8255 ppi architecture
8255 ppi architecture The bsr and the io modes of 8255 is selected by the
The bsr and the io modes of 8255 is selected by the Hfss tutorial
Hfss tutorial Star mesh
Star mesh Network topology advantages and disadvantages
Network topology advantages and disadvantages Virtual topology ansys workbench
Virtual topology ansys workbench