Topic 2 d HighLevel languages and System Software















- Slides: 48

Topic 2 d High-Level languages and System Software (Toolchain) Introduction to Computer Systems Engineering (CPEG 323) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 1

Reading List • Slides: Topic 2 d • Operating System and Compiler Books 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 2

Tool Chain toolchain n A collection of system softwares used to develop for a particular hardware target If you designed a new processor, what is the basic system software tool set you need? 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 3

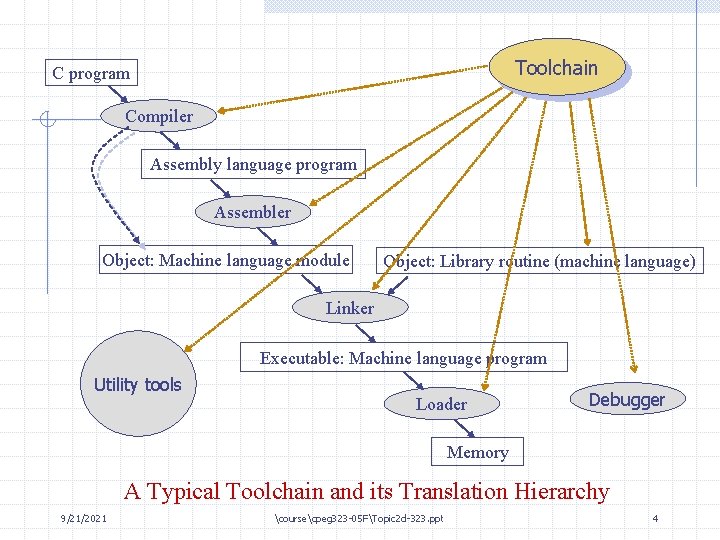
Toolchain C program Compiler Assembly language program Assembler Object: Machine language module Object: Library routine (machine language) Linker Executable: Machine language program Utility tools Loader Debugger Memory A Typical Toolchain and its Translation Hierarchy 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 4

Tool Chain Two good examples n Simple. Scalar www. simplescalar. com n GNUPro www. intel. com (Search GNUPro) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 5

Tool Chain Basic Set: • • • 9/21/2021 Compilers: C, C++, Fortran, and etc. Binary utilities: assembler, linker, objdump, ar, nm Debugger Simulator (functional / cycle-accurate) Others: performance monitor (VTune of Intel) coursecpeg 323 -05 FTopic 2 d-323. ppt 6

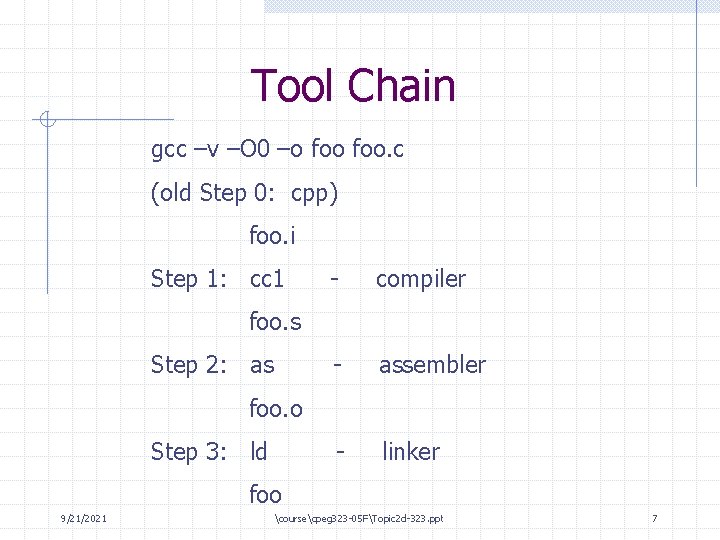
Tool Chain gcc –v –O 0 –o foo. c (old Step 0: cpp) foo. i Step 1: cc 1 - compiler - assembler - linker foo. s Step 2: as foo. o Step 3: ld foo 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 7

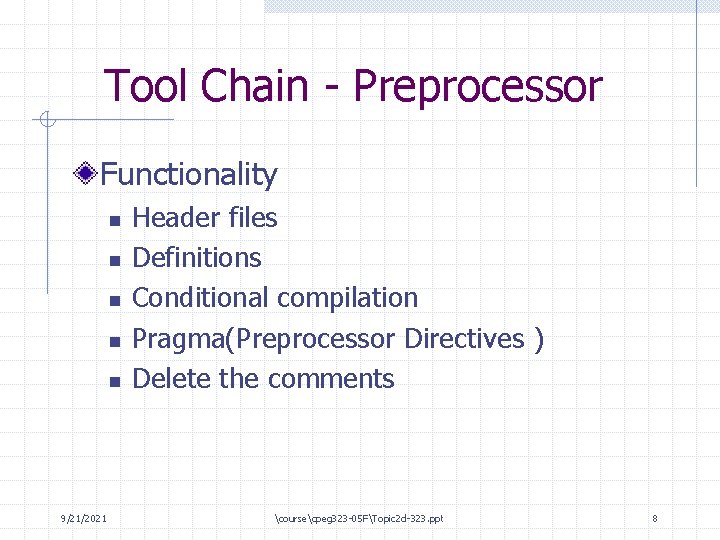
Tool Chain - Preprocessor Functionality n n n 9/21/2021 Header files Definitions Conditional compilation Pragma(Preprocessor Directives ) Delete the comments coursecpeg 323 -05 FTopic 2 d-323. ppt 8

Tool Chain - Compiler Transform a program from high level language to assembly language (or machine language) Optimizations 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 9

Parameter Passing • Caller save. The calling procedure (caller) is responsible for saving and restoring any registers that must be preserved across the call. The called procedure (callee) can then modify any register without constraint. • Callee save. The callee is responsible for saving and restoring any registers that it might use. The caller uses registers without worrying about restoring them after a call. 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 10

Saving Registers • If you call a function, whatever you have in $s 0 to $s 7 is guaranteed to be there when the function gets back to you • But registers $t 0 - $t 9 are fair game to be reused by the function • What are the alternatives? - Save nothing? - Save everything? • Why caller/callee save ? 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 11

Why caller save / callee save? If all caller save ? n Even callee doesn’t kill any of the saved registers – waste of cycles and memory resource If all callee save ? n 9/21/2021 Callee has to save all the register (which will be used by callee), even caller doesn’t use them coursecpeg 323 -05 FTopic 2 d-323. ppt 12

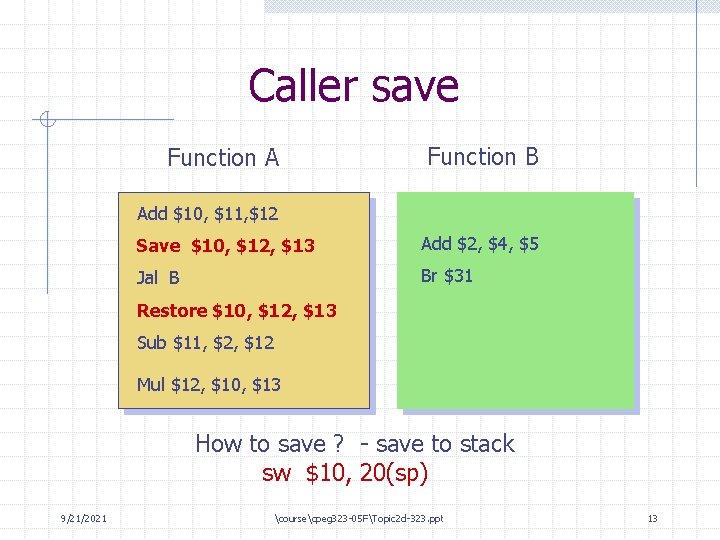
Caller save Function A Function B Add $10, $11, $12 Save $10, $12, $13 Add $2, $4, $5 Jal B Br $31 Restore $10, $12, $13 Sub $11, $2, $12 Mul $12, $10, $13 How to save ? - save to stack sw $10, 20(sp) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 13

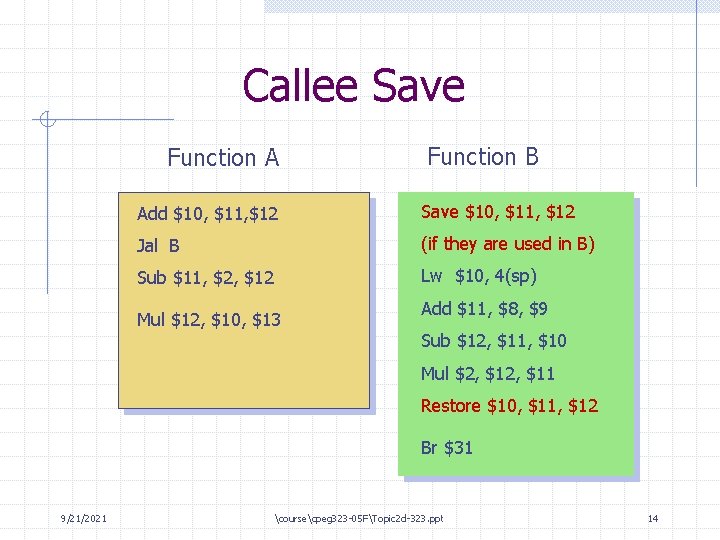
Callee Save Function A Function B Add $10, $11, $12 Save $10, $11, $12 Jal B (if they are used in B) Sub $11, $2, $12 Lw $10, 4(sp) Mul $12, $10, $13 Add $11, $8, $9 Sub $12, $11, $10 Mul $2, $11 Restore $10, $11, $12 Br $31 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 14

Caller Save / Callee Save When to use caller save register ? n n TEMPORARY VARIABLE Also called Scratch Register When to use callee save register ? n 9/21/2021 GLOBAL VARIABLE coursecpeg 323 -05 FTopic 2 d-323. ppt 15

Tool Chain - Assembler Transform assembly code into binary (machine code) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 16

Tool Chain - Linker Linking – resolve symbols Relocation – assign memory address 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 17

Tool Chain - loader Cannot see by user Done by Shell and OS kernel 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 18

Tool Chain – Library Libc/Libm 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 19

Tool Chain Objdump n n 9/21/2021 See the memory layout and sections Symbol table Disassembly code Relocation information coursecpeg 323 -05 FTopic 2 d-323. ppt 20

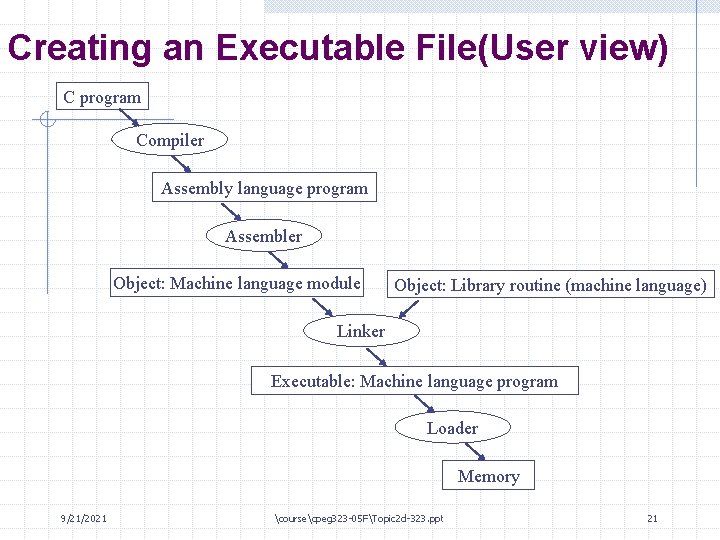
Creating an Executable File(User view) C program Compiler Assembly language program Assembler Object: Machine language module Object: Library routine (machine language) Linker Executable: Machine language program Loader Memory 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 21

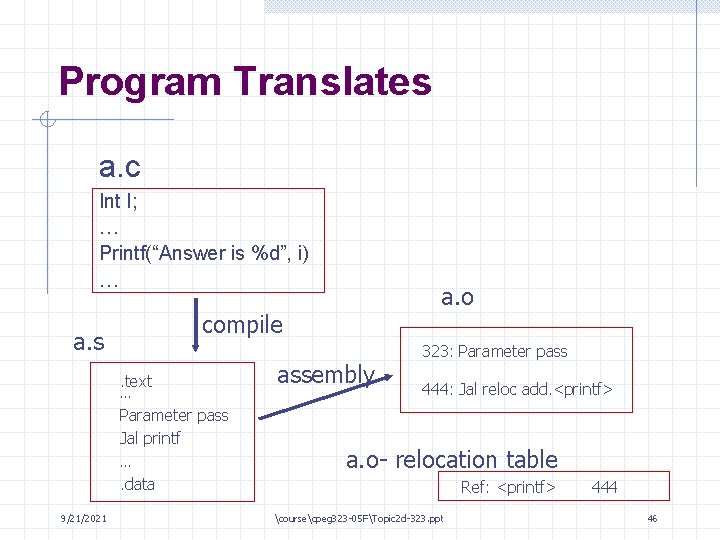
Compiling/Assembling a Program • Code converted from high-level to machine language (binary) • Each source file converted to a separate “object file” - - in Unix, object files have extension. o This is not executable (yet)! Intended to be combined with other modules, not standalone May not have everything we need (e. g. , a main () function) • Functions not assigned specific locations in memory • Each function given a “relocation table” - This table tells exactly which addresses need to be resolved 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 22

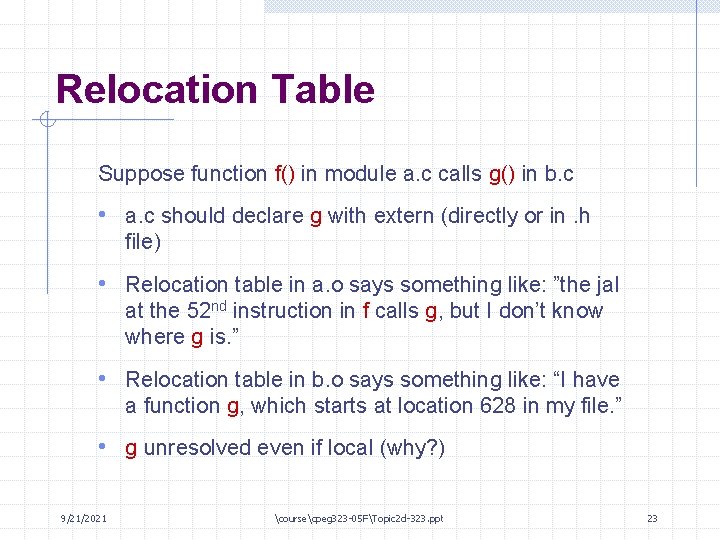
Relocation Table Suppose function f() in module a. c calls g() in b. c • a. c should declare g with extern (directly or in. h file) • Relocation table in a. o says something like: ”the jal at the 52 nd instruction in f calls g, but I don’t know where g is. ” • Relocation table in b. o says something like: “I have a function g, which starts at location 628 in my file. ” • g unresolved even if local (why? ) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 23

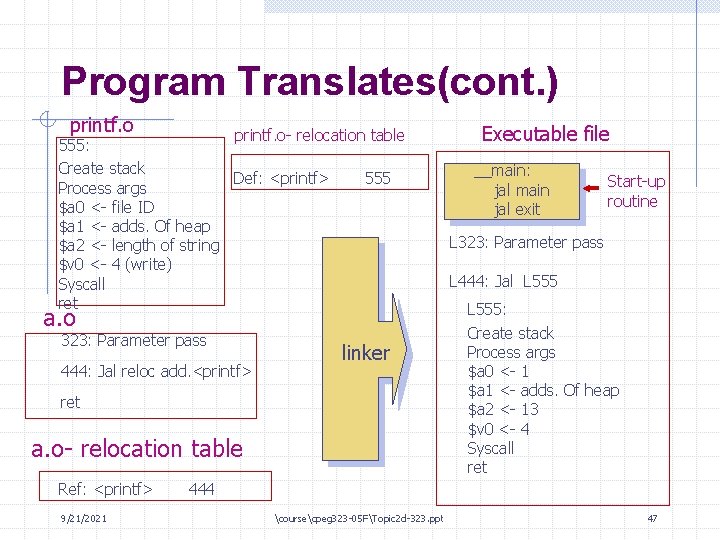
Linking a program • Linker combines one or more object files into a proper executable • Linker determines which functions needed, discards the rest • All needed functions put one after the other in text segment • Linker resolves all labels; for instance - Function f() in a. o calls g() in b. o - Linker knows where it put g(), so it fixes the jal in f() • Linker includes extra code: - Initialization code before call to main() - “Cleanup” code after main() returns 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 24

Loading A program that links without an error can be run. Before being run, the program resides in a file on secondary storage, such as a disk. On Unix system, the operating system kernel brings a program into memory and starts running. 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 25

Libraries • Libraries contain functions intended to be shared & reused, e. g. , - C library: printf(), malloc(), strcmp(), sin(), cos() - STL (Standard Template Library) in C++ - Big software projects may make their own libraries • Static libraries (*. a in Unix) made part of the executable by linker • Dynamic libraries (*. so in Unix, *. dll in Windows) combined at runtime - Executable still has relocation table of unresolved function calls - Loader does the final resolution when you execute the program 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 26

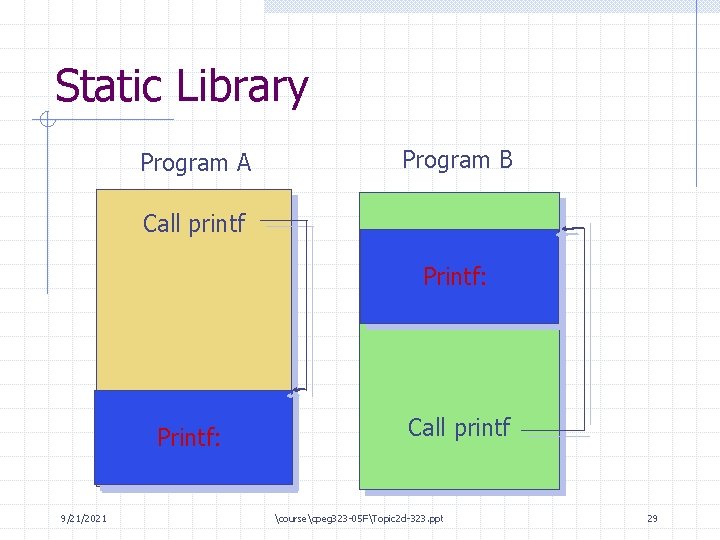
Dynamic vs. Static Library Dynamic library: processes share one copy of the code Static library: each process has its own copy of the code Why? 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 27

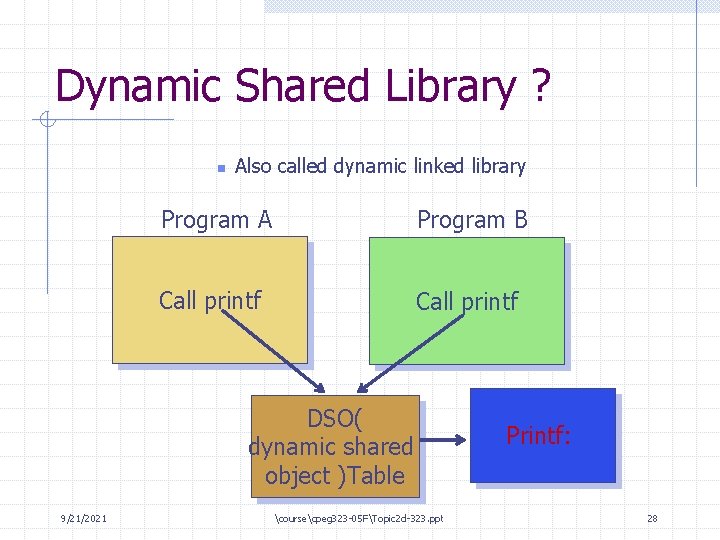
Dynamic Shared Library ? n Also called dynamic linked library Program A Program B Call printf DSO( dynamic shared object )Table 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt Printf: 28

Static Library Program A Program B Call printf Printf: 9/21/2021 Call printf coursecpeg 323 -05 FTopic 2 d-323. ppt 29

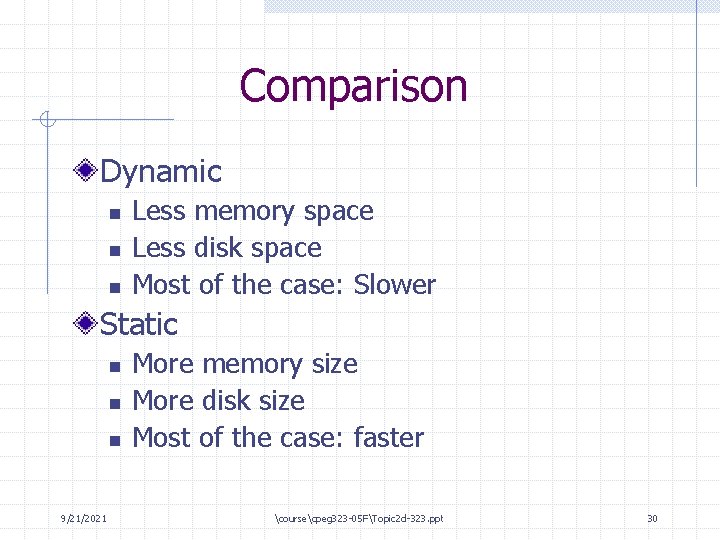
Comparison Dynamic n n n Less memory space Less disk space Most of the case: Slower Static n n n 9/21/2021 More memory size More disk size Most of the case: faster coursecpeg 323 -05 FTopic 2 d-323. ppt 30

Debugger Instruction level debugger Source level debugger Major techniques n n Ptrace (POSIX API. on Linux/Unix system) Embedded or raw machine w Software trap w Single step mode 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 31

Debugger • “Source-level” debugger lets you step through your source code • Requires extra information attached to executable - Location and type of every function and variable First instruction address corresponding to each line of source • Usually requires extra switches to compiler and linker, e. g. , -g • Two popular graphical debuggers are ddd and xxgdb (on ECE/CIS machines) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 32

Run a Executable File (OS View) The operating system performs the following steps: 1. Reads the executable file’s header to determine the size of the text and data segments. 2. “Establish” a new address space (e. g. via the creation of a new page table) for the program. This address space is large enough to hold the text and data segments, along with a stack segment 3. Copies instructions and data from the executable file into the new address space 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 33

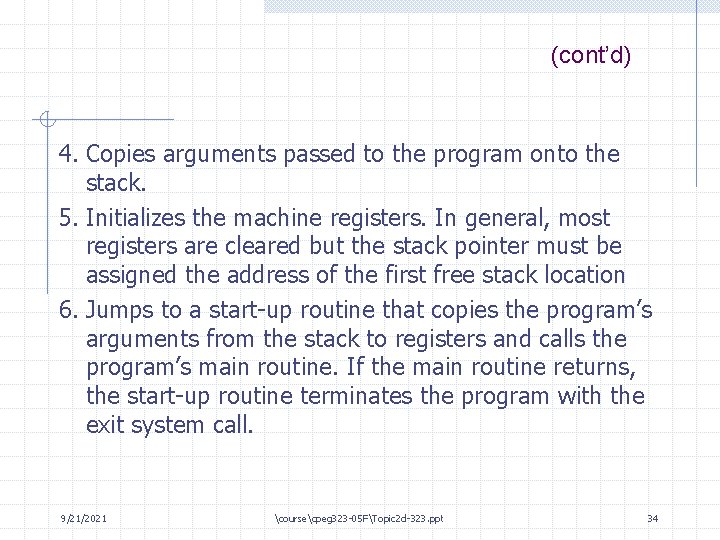
(cont’d) 4. Copies arguments passed to the program onto the stack. 5. Initializes the machine registers. In general, most registers are cleared but the stack pointer must be assigned the address of the first free stack location 6. Jumps to a start-up routine that copies the program’s arguments from the stack to registers and calls the program’s main routine. If the main routine returns, the start-up routine terminates the program with the exit system call. 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 34

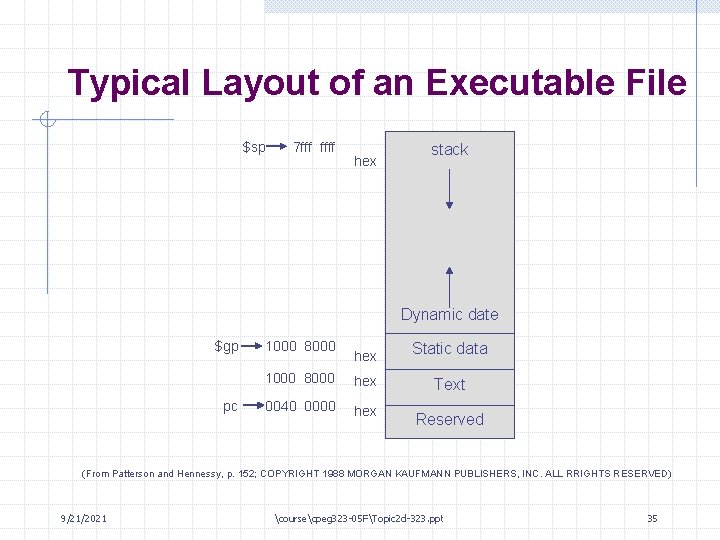
Typical Layout of an Executable File $sp 7 fff ffff hex stack Dynamic date $gp pc 1000 8000 hex Static data 1000 8000 hex Text 0040 0000 hex Reserved (From Patterson and Hennessy, p. 152; COPYRIGHT 1988 MORGAN KAUFMANN PUBLISHERS, INC. ALL RRIGHTS RESERVED) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 35

The Role of the OS Kernel The OS “kernel” performs the following essential functions: • Manages resources (memory, disks, I/O) – mostly via “drivers” • Switches between users (in a multi-user system such as copland) • Provides convenient functions for applications to access resources • Protects users from one another • Provides essential “glue”, e. g. , support for loaders • For this to work efficiently, the CPU must have some support for the kernel. 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 36

Processor Support for the OS kernel • Most processors have at least 2 distinct levels or “modes”: - “Supervisor” (or “privileged” or “kernel”) mode - “User” level (including “root” or “administrator”) • Lower levels can’t do some things, e. g. , access the disk drive • CPU boots in kernel mode; drops to user mode to run user code • Early micros (such as 8086) lacked such modes 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 37

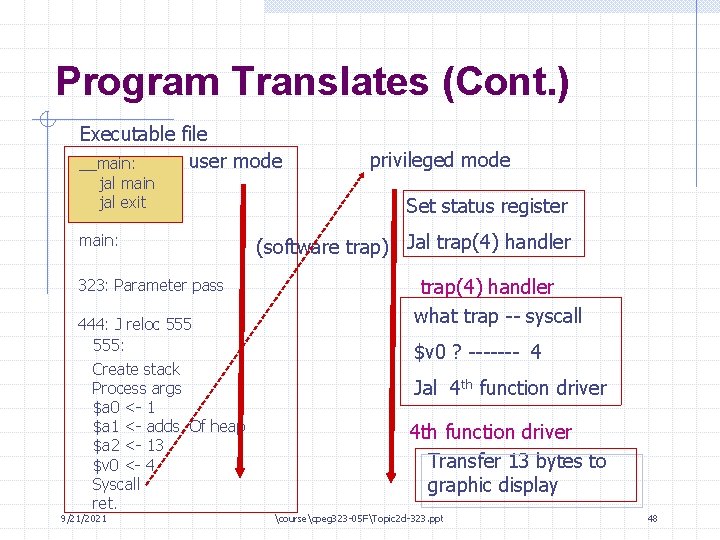
Traps So once we’re in user mode, how do we get back to the privileged mode? Through “traps” – exceptional or unusual conditions requiring intervention by the kernel: • Hardware error (divide by 0 or access to illegal memory address) • Hardware “interrupt” (Ethernet card got data; mouse clicked) • Clock signal telling multi-user OS to switch to another user • “Software trap” when user code requests something from kernel • PC reaches value stored in special “breakpoint” register 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 38

Trap Handlers When a trap occurs, the CPU: • Sets bits in special “status” reg. , indicating the cause of the trap • Switches to privileged mode • Jumps to a “trap handler” (installed at boot time) at fixed location - Handler reads status bits and takes appropriate action - Return address saved, like jal instruction * When kernel is done, a special instruction return to the user code, dropping into user mode automatically 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 39

Software Traps To do just about anything on the system involving shared resources (such as write to a file), the user code must ask the kernel to do it! • • • User code gets access to the kernel through “trap” instructions “System calls” provided for operations such as writing files A function call to a system call converted to a software trap Args passed in the usual way (e. g. , $a 0 -$a 3 in MIPS) In MIPS, use the “syscall” instruction - No operands in assemble-language instruction - Specify which system call you want by putting a value in $v 0 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 40

System Calls • POSIX standard defines system calls and their numbers • For instance, call no. 4 is the write() function: #include <unistd. h> ssize_t write(int fildes, cost void *buf, size_t nbyte); Every open file is identified by a unique “file descriptor” (int) • This function writes nbytes, starting at address buf, to the file 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 41

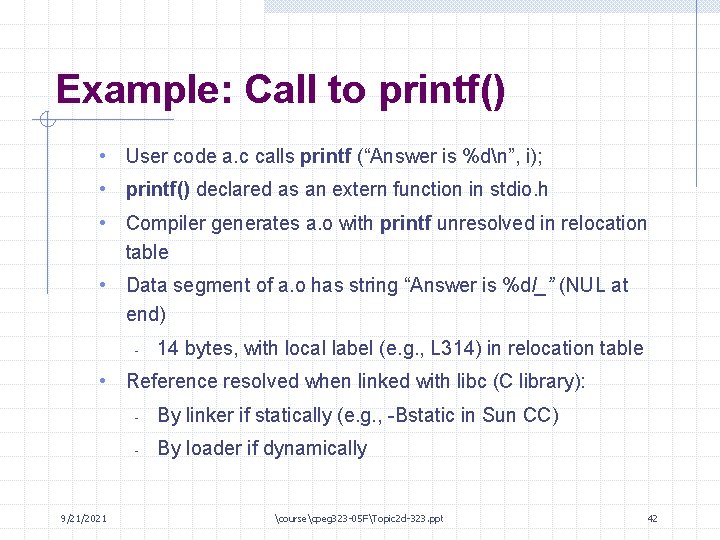
Example: Call to printf() • User code a. c calls printf (“Answer is %dn”, i); • printf() declared as an extern function in stdio. h • Compiler generates a. o with printf unresolved in relocation table • Data segment of a. o has string “Answer is %dl_” (NUL at end) - 14 bytes, with local label (e. g. , L 314) in relocation table • Reference resolved when linked with libc (C library): 9/21/2021 - By linker if statically (e. g. , -Bstatic in Sun CC) - By loader if dynamically coursecpeg 323 -05 FTopic 2 d-323. ppt 42

Calling printf() • Program sets args to printf (L 314 and i)’ does jal printf • printf (still in user mode) does the following: - Creates new stack frame (as any non-leaf function should) - Processes args; makes new string “Answer is 42 l” in heap - Creates args to write() function: • Constant 1 in $a 0 (file descriptor 1 is stdout) • Address of heap string in $a 1 • Constant 13 in $a 2 - Puts constant 4 in $v 0 and does a syscall instruction 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 43

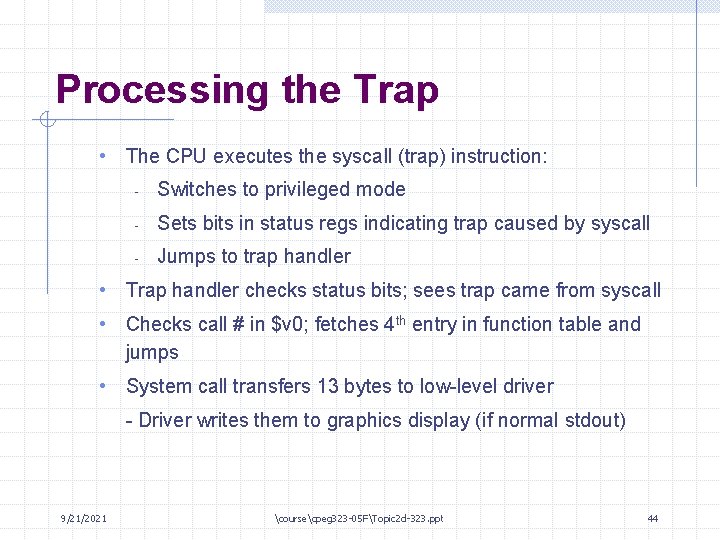
Processing the Trap • The CPU executes the syscall (trap) instruction: - Switches to privileged mode - Sets bits in status regs indicating trap caused by syscall - Jumps to trap handler • Trap handler checks status bits; sees trap came from syscall • Checks call # in $v 0; fetches 4 th entry in function table and jumps • System call transfers 13 bytes to low-level driver - Driver writes them to graphics display (if normal stdout) 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 44

Toolchain Review Caller save /Callee save register Caller save register. The registers that the calling procedure (caller) is responsible for saving and restoring across the call. The called procedure (callee) can then modify the registers without constraint. Callee save register. The registers that the callee is responsible for saving and restoring if it might use. The caller uses the registers without worrying about restoring them after a call. 9/21/2021 coursecpeg 323 -05 FTopic 2 d-323. ppt 45

Program Translates a. c Int I; … Printf(“Answer is %d”, i) … a. s compile. text … Parameter pass Jal printf …. data 9/21/2021 a. o assembly 323: Parameter pass 444: Jal reloc add. <printf> a. o- relocation table Ref: <printf> coursecpeg 323 -05 FTopic 2 d-323. ppt 444 46

Program Translates(cont. ) printf. o- relocation table 555: Create stack Def: <printf> 555 Process args $a 0 <- file ID $a 1 <- adds. Of heap $a 2 <- length of string $v 0 <- 4 (write) Syscall ret a. o 323: Parameter pass 444: Jal reloc add. <printf> linker ret a. o- relocation table Ref: <printf> 9/21/2021 Executable file __main: jal main jal exit Start-up routine L 323: Parameter pass L 444: Jal L 555: Create stack Process args $a 0 <- 1 $a 1 <- adds. Of heap $a 2 <- 13 $v 0 <- 4 Syscall ret 444 coursecpeg 323 -05 FTopic 2 d-323. ppt 47

Program Translates (Cont. ) Executable file user mode __main: jal main jal exit main: 323: Parameter pass 444: J reloc 555: Create stack Process args $a 0 <- 1 $a 1 <- adds. Of heap $a 2 <- 13 $v 0 <- 4 Syscall ret. 9/21/2021 privileged mode Set status register (software trap) Jal trap(4) handler what trap -- syscall $v 0 ? ------- 4 Jal 4 th function driver Transfer 13 bytes to graphic display coursecpeg 323 -05 FTopic 2 d-323. ppt 48