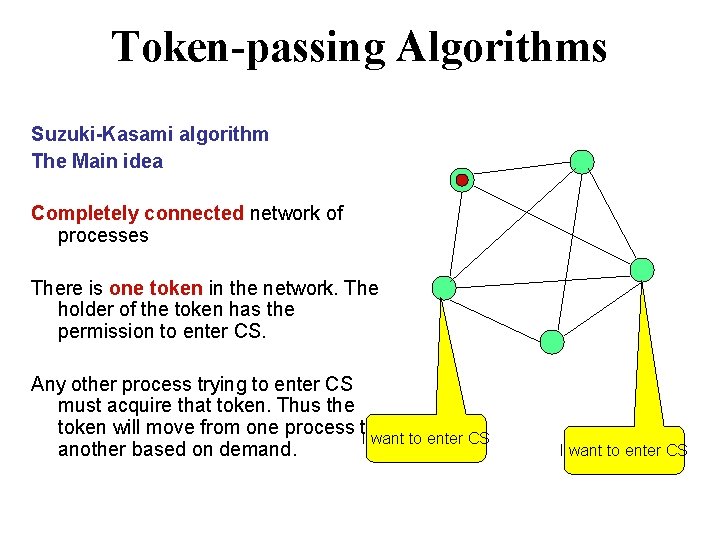
Tokenpassing Algorithms SuzukiKasami algorithm The Main idea Completely
![Suzuki-Kasami’s algorithm {Program of process j} Initially, i: req[i] = last[i] = 0 * Suzuki-Kasami’s algorithm {Program of process j} Initially, i: req[i] = last[i] = 0 *](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-4.jpg)
![Example req=[1, 0, 0, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 0, Example req=[1, 0, 0, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 0,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-5.jpg)
![Example req=[1, 1, 1, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 1, Example req=[1, 1, 1, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-6.jpg)
![Example req=[1, 1, 1, 0, 0] last=[1, 0, 0] Q=(1, 2) 1 0 2 Example req=[1, 1, 1, 0, 0] last=[1, 0, 0] Q=(1, 2) 1 0 2](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-7.jpg)
![Example req=[1, 1, 1, 0, 0] 1 0 req=[1, 1, 1, 0, 0] last=[1, Example req=[1, 1, 1, 0, 0] 1 0 req=[1, 1, 1, 0, 0] last=[1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-8.jpg)
![Example req=[2, 1, 1, 1, 0] 1 0 req=[2, 1, 1, 1, 0] last=[1, Example req=[2, 1, 1, 1, 0] 1 0 req=[2, 1, 1, 1, 0] last=[1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-9.jpg)
![Example req=[2, 1, 1, 1, 0] 1 0 2 4 req=[2, 1, 1, 1, Example req=[2, 1, 1, 1, 0] 1 0 2 4 req=[2, 1, 1, 1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-10.jpg)






- Slides: 19

Token-passing Algorithms Suzuki-Kasami algorithm The Main idea Completely connected network of processes There is one token in the network. The holder of the token has the permission to enter CS. Any other process trying to enter CS must acquire that token. Thus the token will move from one process to I want to enter CS another based on demand. I want to enter CS

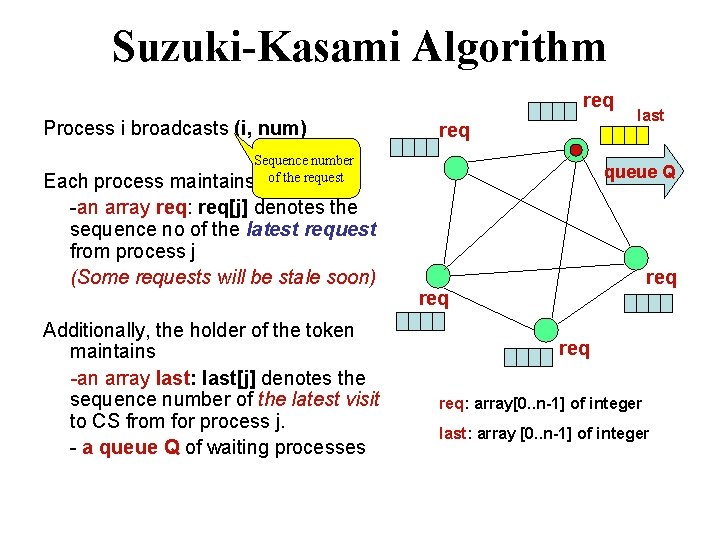
Suzuki-Kasami Algorithm req Process i broadcasts (i, num) req Sequence number maintains of the request Each process -an array req: req[j] denotes the sequence no of the latest request from process j (Some requests will be stale soon) Additionally, the holder of the token maintains -an array last: last[j] denotes the sequence number of the latest visit to CS from for process j. - a queue Q of waiting processes last queue Q req req: array[0. . n-1] of integer last: array [0. . n-1] of integer

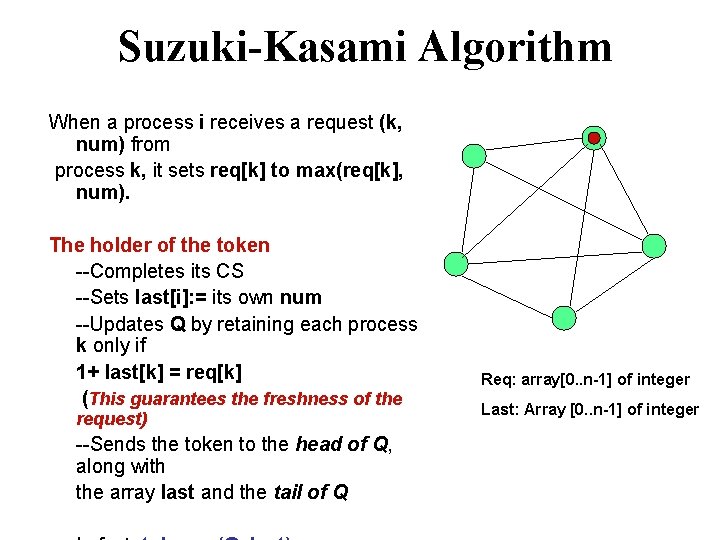
Suzuki-Kasami Algorithm When a process i receives a request (k, num) from process k, it sets req[k] to max(req[k], num). The holder of the token --Completes its CS --Sets last[i]: = its own num --Updates Q by retaining each process k only if 1+ last[k] = req[k] (This guarantees the freshness of the request) --Sends the token to the head of Q, along with the array last and the tail of Q Req: array[0. . n-1] of integer Last: Array [0. . n-1] of integer
![SuzukiKasamis algorithm Program of process j Initially i reqi lasti 0 Suzuki-Kasami’s algorithm {Program of process j} Initially, i: req[i] = last[i] = 0 *](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-4.jpg)
Suzuki-Kasami’s algorithm {Program of process j} Initially, i: req[i] = last[i] = 0 * Entry protocol * req[j] : = req[j] + 1 Send (j, req[j]) to all Wait until token (Q, last) arrives Critical Section * Exit protocol * last[j] : = req[j] k ≠ j: k Q req[k] = last[k] + 1 append k to Q; if Q is not empty send (tail-of-Q, last) to head-of-Q fi * Upon receiving a request (k, num) * req[k] : = max(req[k], num)
![Example req1 0 0 0 0 last0 0 0 1 0 2 req1 0 Example req=[1, 0, 0, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 0,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-5.jpg)
Example req=[1, 0, 0, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 0, 0] 4 req=[1, 0, 0] 3 req=[1, 0, 0] initial state
![Example req1 1 1 0 0 last0 0 0 1 0 2 req1 1 Example req=[1, 1, 1, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-6.jpg)
Example req=[1, 1, 1, 0, 0] last=[0, 0, 0] 1 0 2 req=[1, 1, 1, 0, 0] 4 req=[1, 1, 1, 0, 0] 3 req=[1, 1, 1, 0, 0] 1 & 2 send requests
![Example req1 1 1 0 0 last1 0 0 Q1 2 1 0 2 Example req=[1, 1, 1, 0, 0] last=[1, 0, 0] Q=(1, 2) 1 0 2](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-7.jpg)
Example req=[1, 1, 1, 0, 0] last=[1, 0, 0] Q=(1, 2) 1 0 2 req=[1, 1, 1, 0, 0] 4 req=[1, 1, 1, 0, 0] 3 req=[1, 1, 1, 0, 0] 0 prepares to exit CS
![Example req1 1 1 0 0 1 0 req1 1 1 0 0 last1 Example req=[1, 1, 1, 0, 0] 1 0 req=[1, 1, 1, 0, 0] last=[1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-8.jpg)
Example req=[1, 1, 1, 0, 0] 1 0 req=[1, 1, 1, 0, 0] last=[1, 0, 0] Q=(2) 2 req=[1, 1, 1, 0, 0] 4 req=[1, 1, 1, 0, 0] 3 req=[1, 1, 1, 0, 0] 0 passes token (Q and last) to 1
![Example req2 1 1 1 0 1 0 req2 1 1 1 0 last1 Example req=[2, 1, 1, 1, 0] 1 0 req=[2, 1, 1, 1, 0] last=[1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-9.jpg)
Example req=[2, 1, 1, 1, 0] 1 0 req=[2, 1, 1, 1, 0] last=[1, 0, 0] Q=(2, 0, 3) 2 req=[2, 1, 1, 1, 0] 4 req=[2, 1, 1, 1, 0] 3 req=[2, 1, 1, 1, 0] 0 and 3 send requests
![Example req2 1 1 1 0 1 0 2 4 req2 1 1 1 Example req=[2, 1, 1, 1, 0] 1 0 2 4 req=[2, 1, 1, 1,](https://slidetodoc.com/presentation_image_h2/00d9f085f9ebb191306bdb89c481e87d/image-10.jpg)
Example req=[2, 1, 1, 1, 0] 1 0 2 4 req=[2, 1, 1, 1, 0] 3 req=[2, 1, 1, 1, 0] last=[1, 1, 0, 0, 0] Q=(0, 3) req=[2, 1, 1, 1, 0] 1 sends token to 2

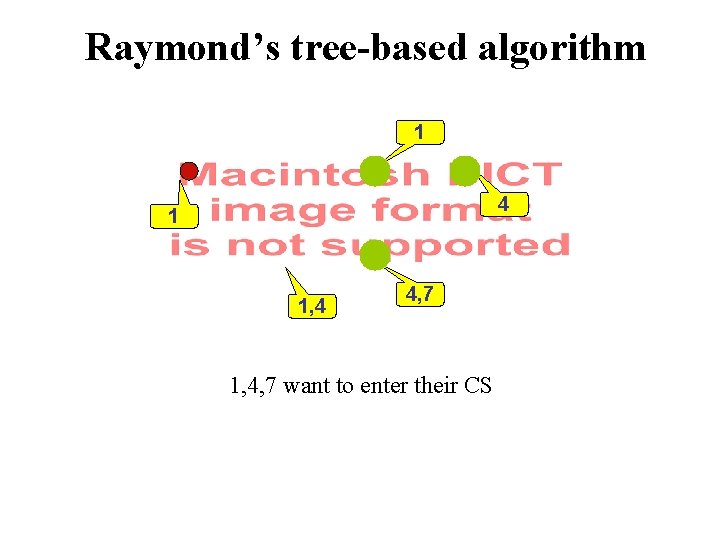
Raymond’s tree-based algorithm 1 4 1 1, 4 4, 7 1, 4, 7 want to enter their CS

Raymond’s Algorithm 1 4 1, 4 4, 7 2 sends the token to 6

Raymond’s Algorithm 4 4, 7 6 forwards the token to 1 The message complexity is O(diameter) of the tree. Extensive empirical measurements show that the average diameter of randomly chosen trees of size n is O(log n). Therefore, the authors claim that the average message complexity is O(log n)

Distributed snapshot -- How many messages are in transit on the internet? -- What is the global state of a distributed system of N processes? How do we compute these?

One-dollar bank Let a $1 coin circulate in a network of a million banks. How can someone count the total $ in circulation? If not counted “properly, ” then one may think the total $ in circulation to be one million.

Importance of snapshots Major uses in - deadlock detection - termination detection - rollback recovery - global predicate computation

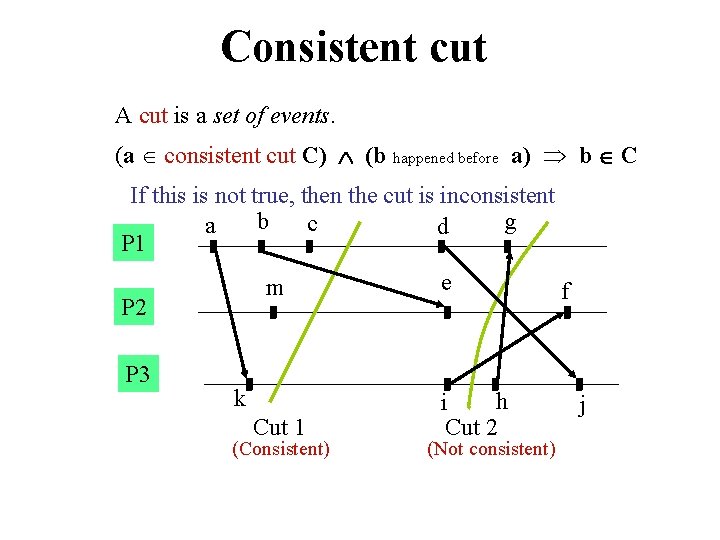
Consistent cut A cut is a set of events. (a consistent cut C) (b happened before a) b C If this is not true, then the cut is inconsistent b g c a d P 1 m P 2 P 3 k Cut 1 (Consistent) e h i Cut 2 (Not consistent) f j

Consistent snapshot The set of states immediately following a consistent cut forms a consistent snapshot of a distributed system. • A snapshot that is of practical interest is the most recent one. Let C 1 and C 2 be two consistent cuts and C 1 C 2. Then C 2 is more recent than C 1. • Analyze why certain cuts in the one-dollar bank are inconsistent.

Consistent snapshot How to record a consistent snapshot? Note that 1. The recording must be non-invasive 2. Recording must be done on-the-fly. You cannot stop the system.