Todays Session Introduction Overview of Biometrics Dr Charles
Today’s Session Introduction Overview of Biometrics Dr. Charles C. Tappert Seidenberg School of CSIS, Pace University http: //csis. pace. edu/~ctappert/ SUBTITLE
Today’s Focus - Biometrics The Biometrics Component of Cybersecurity You will learn: Basics of biometrics Many exercises and projects for your students See agenda at http: //www. csis. pace. edu/~ctappert/2016 Cybersecurity. Workshop/
What is Biometrics? The science of identifying, or verifying the identity of, a person based on physiological or behavioral traits Physical traits Four Most Common: Fingerprint, Face, Hand Geometry, Iris Behavioral traits Two Most Common: Signature, Voice Pace University research primarily concerns computer-user input: keystroke and mouse input, writing linguistic style, semantic content Biometrics websites and videos http: //www. biometrics. gov/ Biometric Security (hand geometry)
Ways of Using Biometrics Security Applications Authentication (Verification) User claims an identity – system authenticates or rejects person Binary decision – yes, you are the person you claim to be or no you are not Identification System identifies a person 1 -of-n decision (more difficult problem than authentication) Less Common Applications Estimate a person’s age, gender, mood, handedness (left/right) E. g. , In the 1970 s, gov’t wanted to measure pilot anxiety from voice
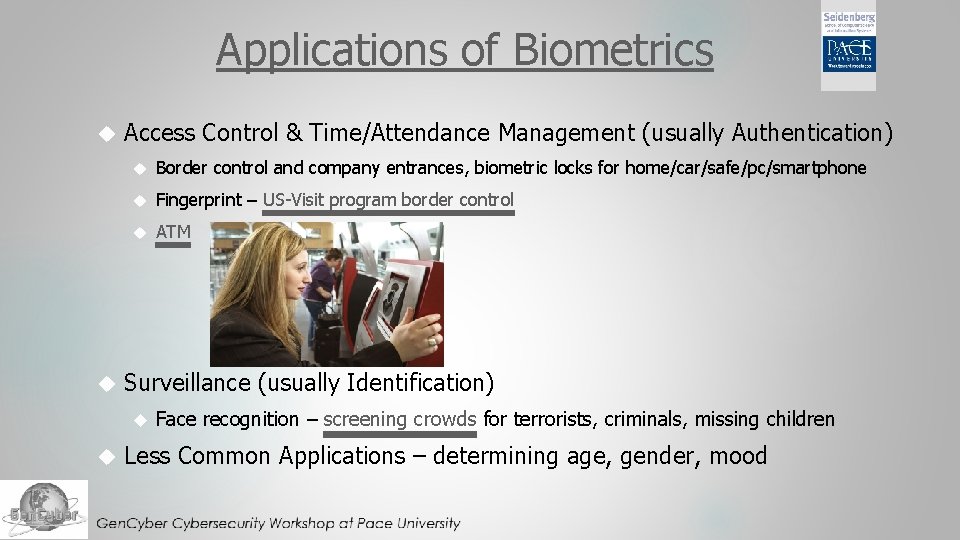
Applications of Biometrics Access Control & Time/Attendance Management (usually Authentication) Border control and company entrances, biometric locks for home/car/safe/pc/smartphone Fingerprint – US-Visit program border control ATM Surveillance (usually Identification) Face recognition – screening crowds for terrorists, criminals, missing children Less Common Applications – determining age, gender, mood
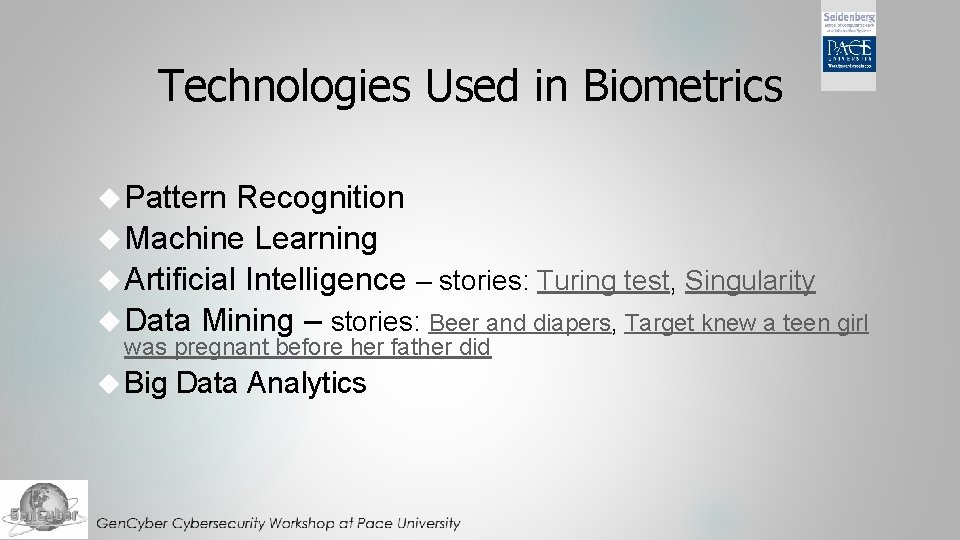
Technologies Used in Biometrics Pattern Recognition Machine Learning Artificial Intelligence – stories: Turing test, Singularity Data Mining – stories: Beer and diapers, Target knew a teen girl was pregnant before her father did Big Data Analytics

Traditional Modes of Person Authentication Possessions – what you have Keys, passports, smartcards, etc. Knowledge – what you know Secret information: passwords, etc. Biometrics – what you are or what you do Characteristics of the human body and human actions that differentiate people from each other
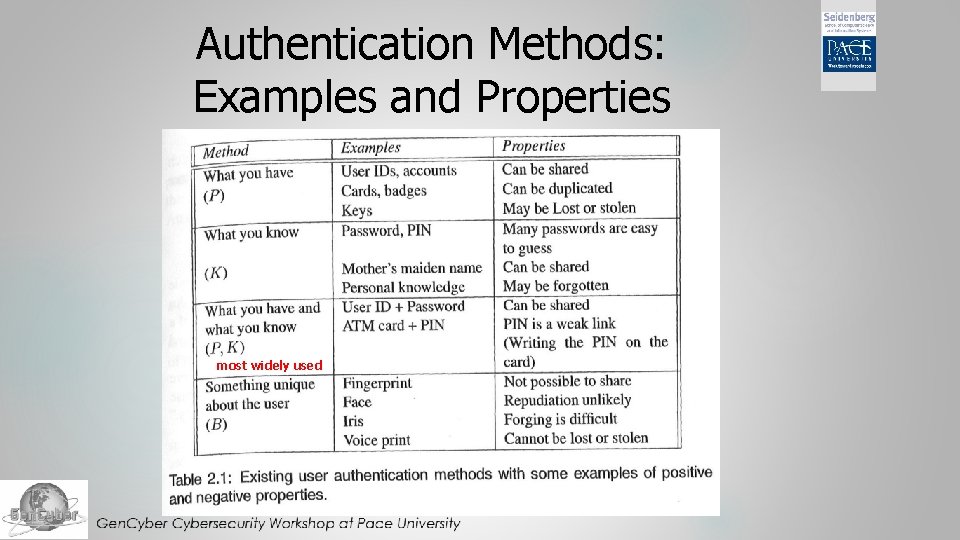
Authentication Methods: Examples and Properties most widely used
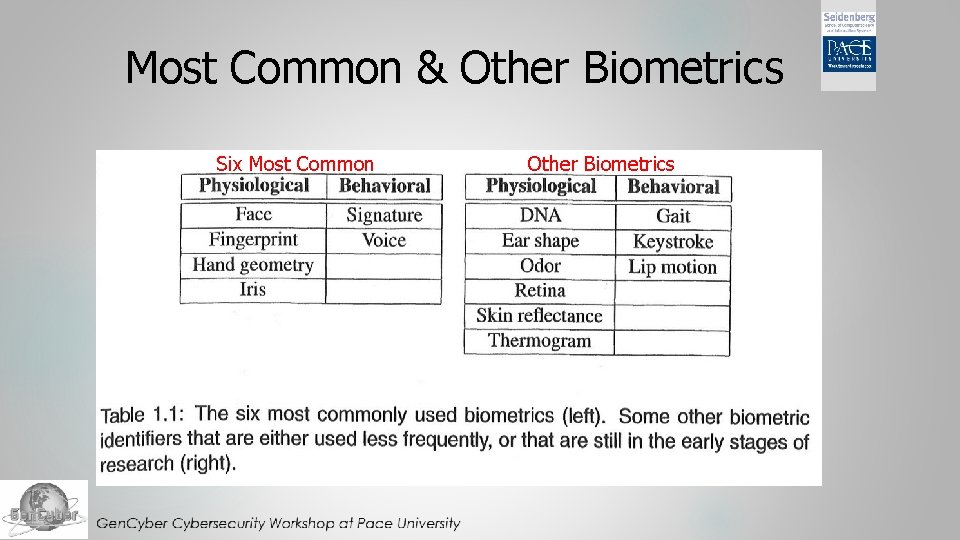
Most Common & Other Biometrics Six Most Common Other Biometrics
Attributes Necessary to Make a Biometric Practical Universality Uniqueness biometric characteristic invariant over time Collectability no two persons have the same biometric characteristic Permanence every person has the biometric characteristic measurable with a sensing device Acceptability user population and public in general should have no strong objections to measuring/collecting the biometric Retina not very acceptable – requires close proximity to camera
System Performance and Design Issues System performance (accuracy) Computational speed (DNA slow) Exception handling (difficult to predict) System cost (high for DNA) Security (can system be compromised? ) Privacy (data confidentiality)

Face Biometric Acquisition Single 2 D image Video sequence 3 D image via stereo imaging, etc. Michigan State University – Anil Jain http: //biometrics. cse. msu. edu/Presentations/Anil. Jain_ Face. Recognition_KU 10. pdf

Face Recognition Each person has a unique face?
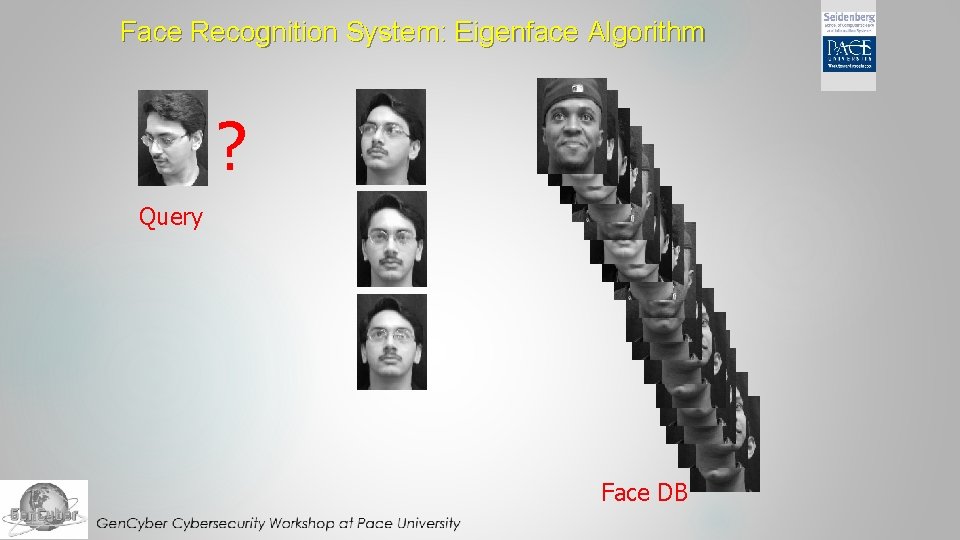
Face Recognition System: Eigenface Algorithm ? Query Face DB

Inspirational Portrait of Individuality
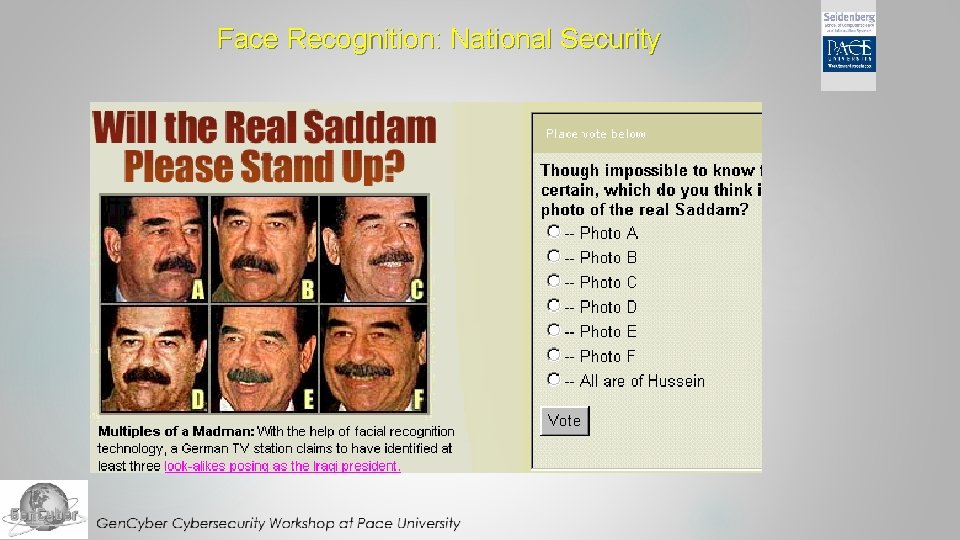
Face Recognition: National Security
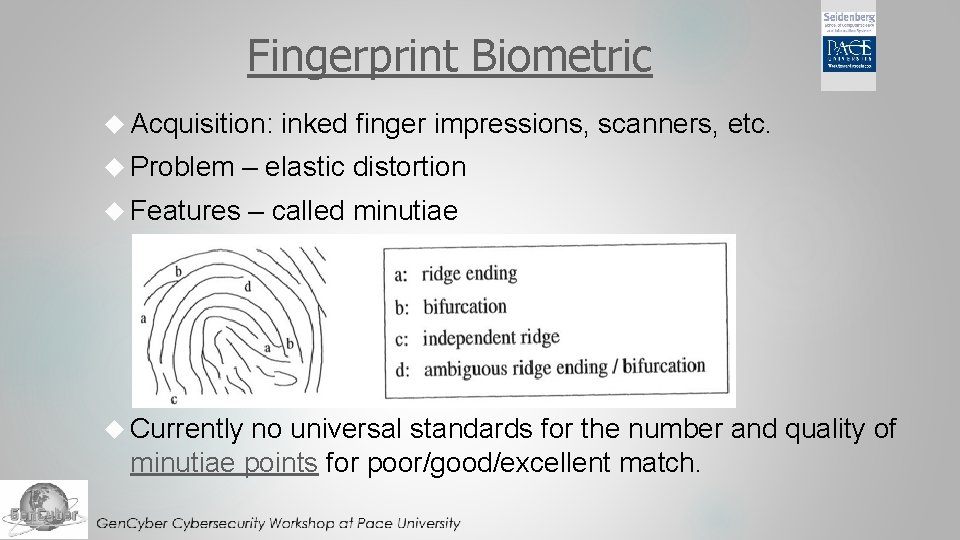
Fingerprint Biometric Acquisition: inked finger impressions, scanners, etc. Problem – elastic distortion Features – called minutiae Currently no universal standards for the number and quality of minutiae points for poor/good/excellent match.

Fingerprint Verification
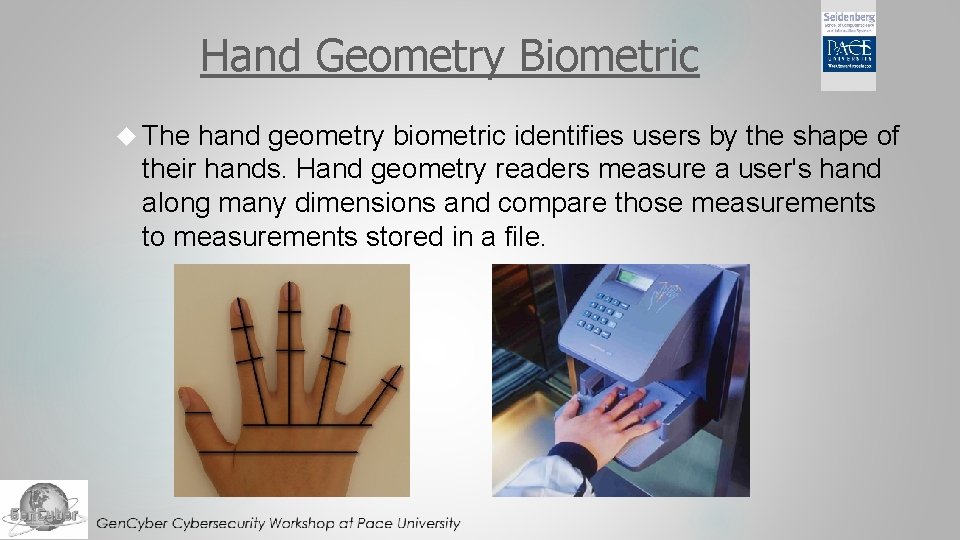
Hand Geometry Biometric The hand geometry biometric identifies users by the shape of their hands. Hand geometry readers measure a user's hand along many dimensions and compare those measurements to measurements stored in a file.
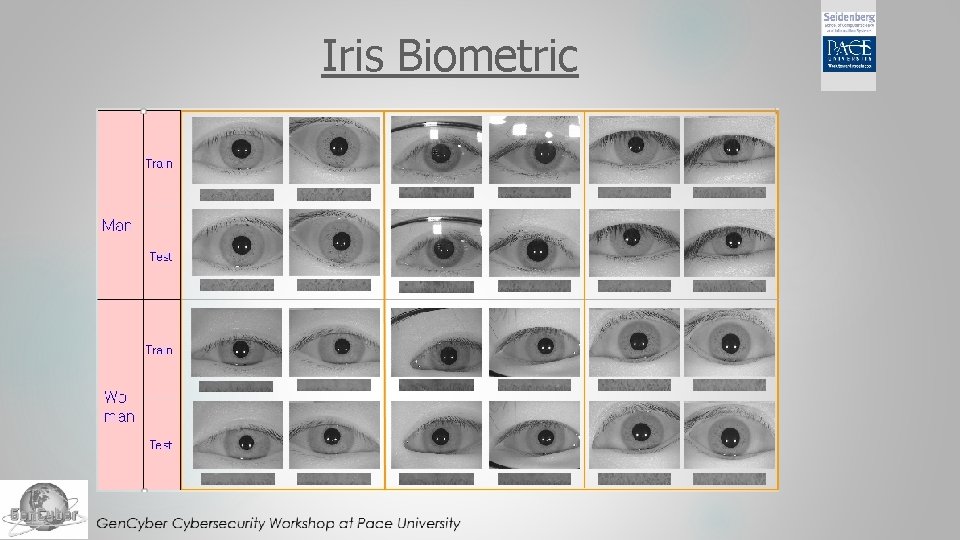
Iris Biometric

Iris Authentication: Image Processing

Biometric Authentication A robot identifies a suspect, from the movie “Minority Report. ”
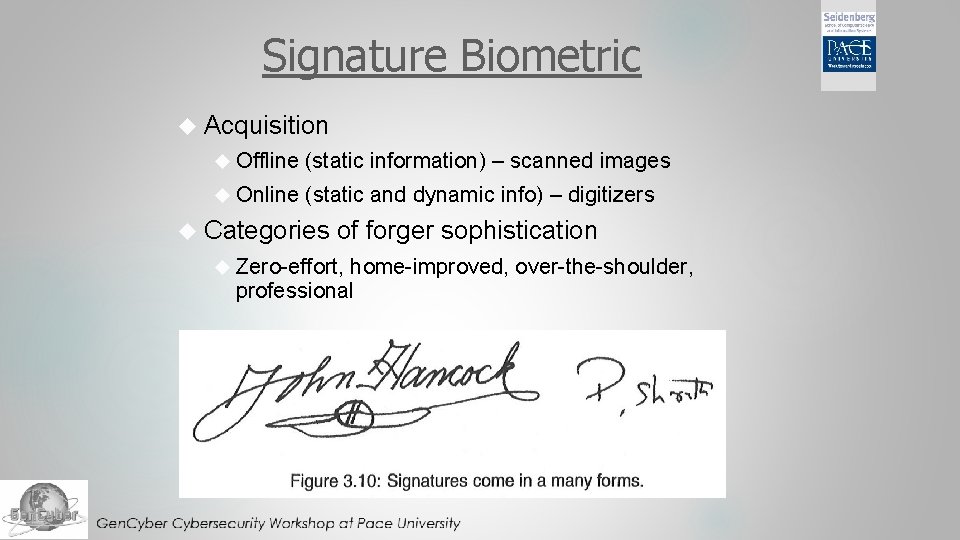
Signature Biometric Acquisition Offline (static information) – scanned images Online (static and dynamic info) – digitizers Categories of forger sophistication Zero-effort, home-improved, over-the-shoulder, professional
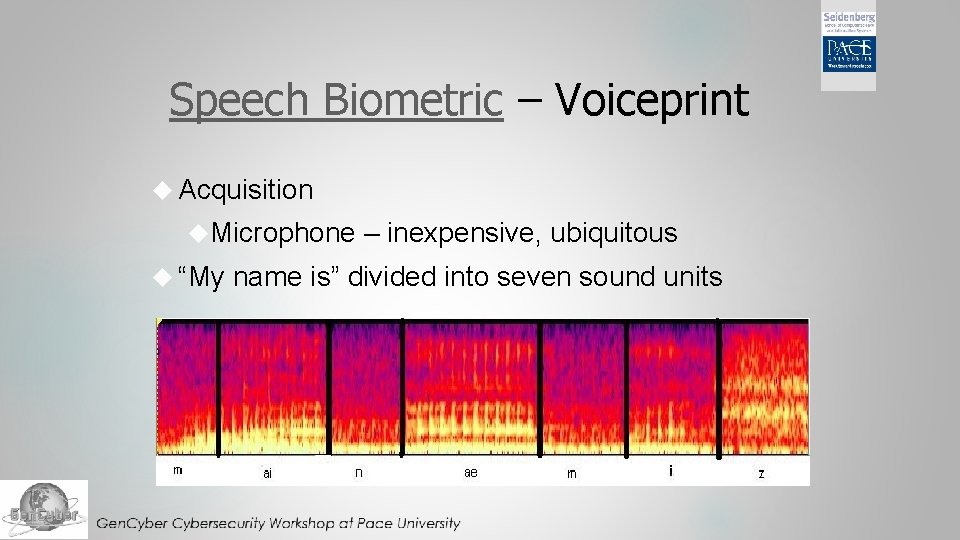
Speech Biometric – Voiceprint Acquisition Microphone – inexpensive, ubiquitous “My name is” divided into seven sound units
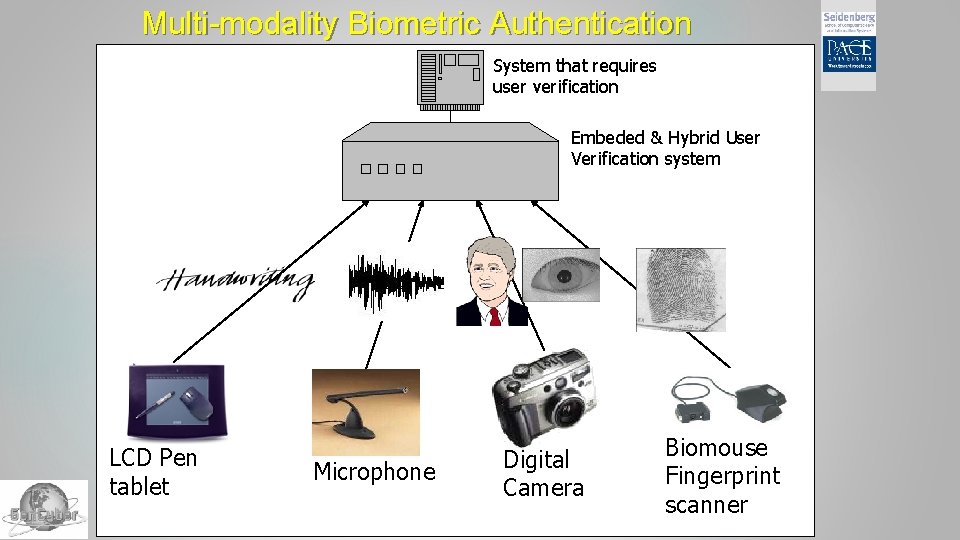
Multi-modality Biometric Authentication System that requires user verification Embeded & Hybrid User Verification system LCD Pen tablet Microphone Digital Camera Biomouse Fingerprint scanner
Biometric System Evaluation Types Technical Evaluation (T) Simulation tests – usual for academic studies Scenario Evaluation (S) Testing facility that simulates the actual installation Operational Evaluation Actual installation testing – most realistic
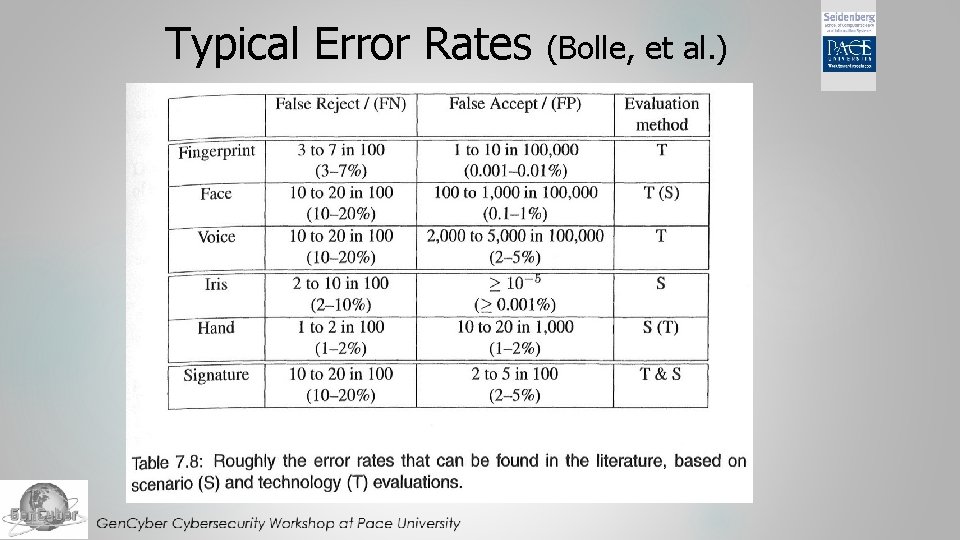
Typical Error Rates (Bolle, et al. )
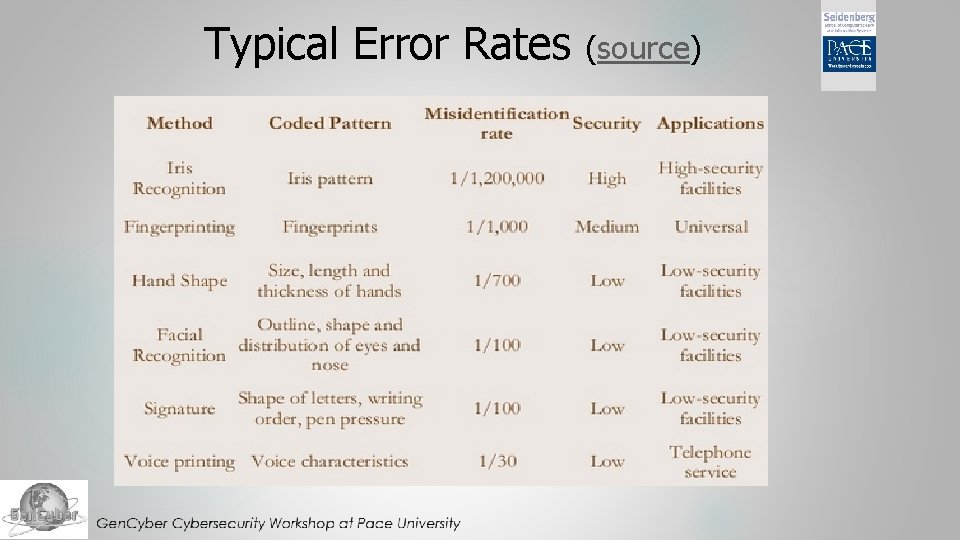
Typical Error Rates (source)

Iris Biometric: National Geographic Case Sharbat Gula Photos 1985 & 2002 A Life Revealed 1 2 Is Sharbat Gula without question the famous “Afghan girl”? Though she remembers being photographed in the school tent of her refugee camp, and her resemblance to the girl in Mc. Curry's photo is apparent, the Geographic sought expert opinion. In Pakistan, ophthalmologist Mustafa Iqbal examined Sharbat, with her husband at her side. Iqbal felt “ 100 percent certain” that her iris patterns and eye freckles matched those in Mc. Curry's photo. A scar on the right side of her nose was another distinguishing mark.
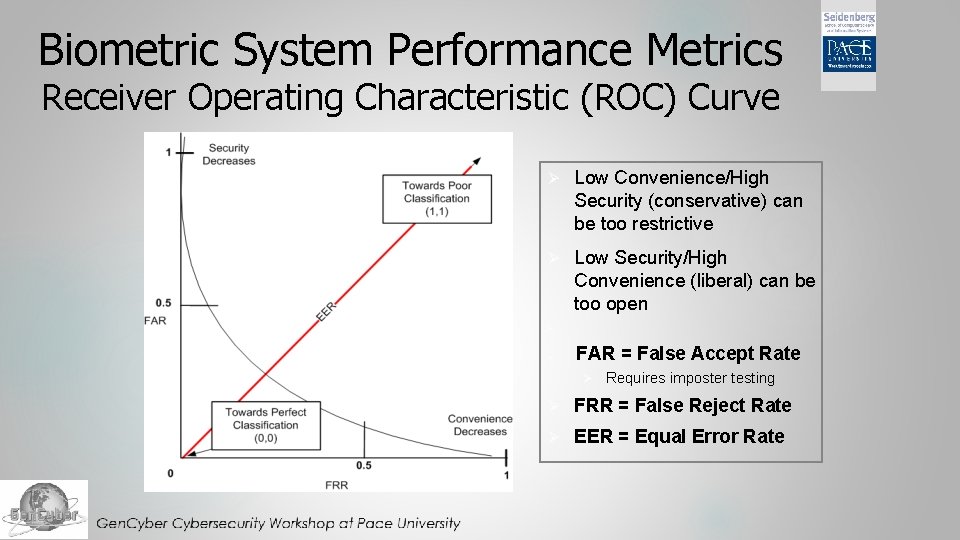
Biometric System Performance Metrics Receiver Operating Characteristic (ROC) Curve Ø Low Convenience/High Security (conservative) can be too restrictive Ø Low Security/High Convenience (liberal) can be too open Ø Ø FAR = False Accept Rate Ø Requires imposter testing Ø FRR = False Reject Rate Ø EER = Equal Error Rate

Biometric Zoo Sheep Dominant group, systems perform well for them Goats Weak distinctive traits, produce many False Rejects Lambs Easy to imitate, cause “passive” False Accepts Wolves Good at imitating, cause “active” False Accepts Chameleons Easy to imitate and good at imitating others
Many Biometric Systems and Interesting Articles on the Internet Microsoft's Age Estimator Key. Trac keystroke demo Secret Lock Michigan State University DNA Generated Face – NYT science section article Building a Face, and Case, on DNA – March 2015

Project Ideas List and describe various biometrics, can you think of new ones? List and describe interesting movies involving biometrics. What is the government doing in biometrics? Define and describe the various technologies used in biometrics. Find interesting Web and news items related to biometrics – e. g. , mood estimation from face or voice. List and describe the ways people use the usual authentication method of combining what you have and what you know. Investigate the biometric zoo. Investigate what biometrics are easy to spoof and how it is done.
References Guide to Biometrics, Bolle, et al. , Springer 2004 Pace University conference, journal, and book publications, see http: //www. csis. pace. edu/~ctappert/pubs. htm Wikipedia and other Internet sources

Copyright for Material Reuse This materials are developed with support from the Gen. Cyber program of the National Security Agency and the Cyber. Corps program of the National Science Foundation. Copyright © 2016 Charles Tappert (ctappert@pace. edu), Pace University. Please properly acknowledge the source for any reuse of the materials as below. Charles Tappert, 2016 Gen. Cybersecurity Workshop, Pace University Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1. 3 or any later version published by the Free Software Foundation. A copy of the license is available at http: //www. gnu. org/copyleft/fdl. html.

Acknowledgment The authors would like to acknowledge the support from the Gen. Cyber program of the National Security Agency and the Cyber. Corps program of the National Science Foundation. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation, the National Security Agency or the US government.
- Slides: 36