To what extent does technological advances impact the













- Slides: 17

To what extent does technological advances impact the global society? -The Political Perspective Group Members: John Oldano- Economic Perspective Amir Ashry- Social/Cultural Perspective Alyssa Gershon- Environmental Perspective Joshua Guzman Candidate Number: 0121 Centre Number: US 799

What is Technology? ● Technology refers to methods, systems, and devices which are the result of scientific knowledge being used for practical purposes (Collins Dictionary). ● Throughout history, new innovations have produced more food, created better tools, made life easier, but allowed war to be more devastating. Today technology influences and impacts almost every aspect of our life. Overall, it has both positive and negative effects.

Why are technological advances an issue? ● Technological advances are an issue we should care about due to innovations being created more effectively and devastatingly as weapons of war has become more destructive with the potential to eliminate humanity. ● In addition, the unlimited potential of technology to warfare is dangerous as it can also lead to cyber warfare.

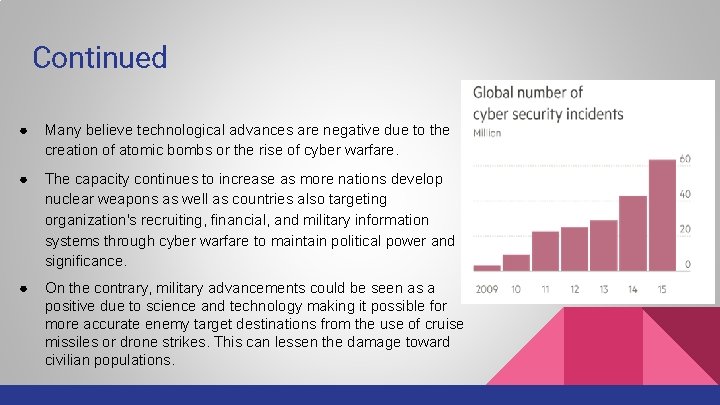
Continued ● Many believe technological advances are negative due to the creation of atomic bombs or the rise of cyber warfare. ● The capacity continues to increase as more nations develop nuclear weapons as well as countries also targeting organization's recruiting, financial, and military information systems through cyber warfare to maintain political power and significance. ● On the contrary, military advancements could be seen as a positive due to science and technology making it possible for more accurate enemy target destinations from the use of cruise missiles or drone strikes. This can lessen the damage toward civilian populations.

The United Nations and the Geneva Convention ● ○ What are the Geneva Conventions? In short, during war, countries must obey rules such as: not torturing prisoners of war, not attacking civilians, you must limit as much impact of warfare on women and children, as well as other civilians. You also must treat detainees humanely (International Committee of the Red Cross, 2016). ● How does IHL respond to the use of autonomous weapons? The IHL limits the rights of parties to develop and use new means or methods of warfare like robots or drones. In addition, whether or not a particular autonomous weapon is lawful depends on how it works and whether it can be used in a way that complies with international law (ICRC, 2016). ○ ○

Drone Strikes in Syria and Iraq (Global) ● Since 2014, the U. S. and its allies have launched over 50, 000 missiles or bombs on Syria and Iraq amounting to an explosion about every 20 minutes for two years. ● The civilian death toll of air launched explosives doubled from 2016 to 2017 as civilians of Syria and Iraq accounted for about 11, 000 to 18, 000 deaths according to a survey by Air Wars in 2017. ● Air Wars director Chris Woods stated, “ For years and years now we’ve been fed this line by the military that they don’t kill civilians, that our weapons are so smart we only kill the bad guys… That’s just not true. It’s not born out by data. ”

Politics and Drone Strikes in Syria and Iraq (Global) ● The reported document in 2013, is a considerable assertion that minimizing civilian casualties is both a moral and strategic imperative. ● A centerpiece of President Obama’s PPG, released in May 2013, was the provision that lethal force could be used only when commanders could know with “near certainty” that civilians would not be harmed in the operation. ● However, the Trump Administration removed the extensive interagency review process described in the PPG and replaced it with boundaries of U. S. operations against designated terrorist groups(s) in a given nation-that are reviewed and re-approved once a year due to the overwhelming civilian casualties during Obama’s Presidency.

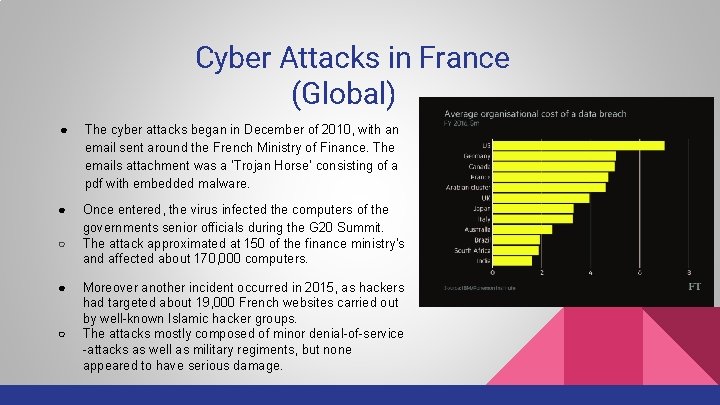
Cyber Attacks in France (Global) ● The cyber attacks began in December of 2010, with an email sent around the French Ministry of Finance. The emails attachment was a ‘Trojan Horse’ consisting of a pdf with embedded malware. ● Once entered, the virus infected the computers of the governments senior officials during the G 20 Summit. The attack approximated at 150 of the finance ministry’s and affected about 170, 000 computers. ○ ● ○ Moreover another incident occurred in 2015, as hackers had targeted about 19, 000 French websites carried out by well-known Islamic hacker groups. The attacks mostly composed of minor denial-of-service -attacks as well as military regiments, but none appeared to have serious damage.

France and Cyber Security (Global) ● With the development of cyberspace, it opened up criminal use of the internet, including for terrorist purposes; large-scale propagation of false information; espionage for politics; and attacks on transport, energy, or communication for sabotaging purposes. ● The French national security policy is based on two essential texts, The 2013 White Paper on national security and defence and the 2015 National Strategy for Digital Security. ● These texts challenged digital technology and the associated threats and helped with five objectives such as: guaranteeing national sovereignty, providing a firm response to acts of cybercrime, informing the public at large, making digital security a competitive advantage for French businesses, and enhancing France’s voice on the international stage.

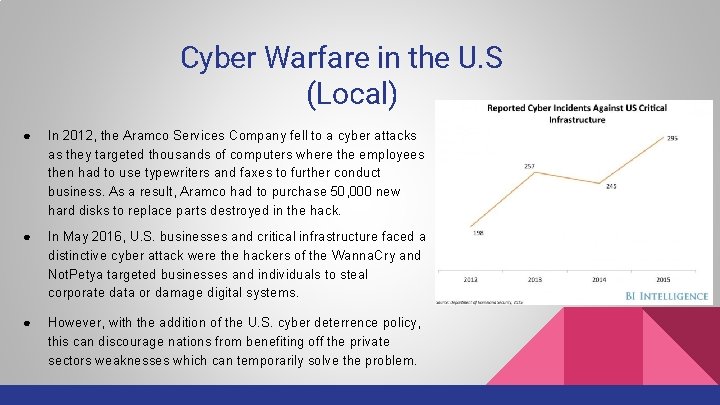
Cyber Warfare in the U. S (Local) ● In 2012, the Aramco Services Company fell to a cyber attacks as they targeted thousands of computers where the employees then had to use typewriters and faxes to further conduct business. As a result, Aramco had to purchase 50, 000 new hard disks to replace parts destroyed in the hack. ● In May 2016, U. S. businesses and critical infrastructure faced a distinctive cyber attack were the hackers of the Wanna. Cry and Not. Petya targeted businesses and individuals to steal corporate data or damage digital systems. ● However, with the addition of the U. S. cyber deterrence policy, this can discourage nations from benefiting off the private sectors weaknesses which can temporarily solve the problem.

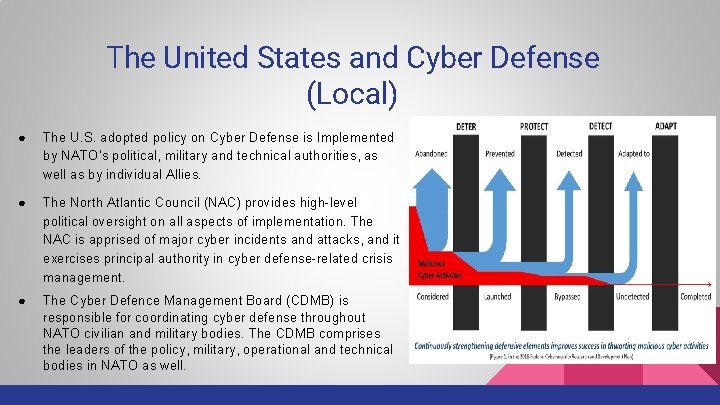
The United States and Cyber Defense (Local) ● The U. S. adopted policy on Cyber Defense is Implemented by NATO’s political, military and technical authorities, as well as by individual Allies. ● The North Atlantic Council (NAC) provides high-level political oversight on all aspects of implementation. The NAC is apprised of major cyber incidents and attacks, and it exercises principal authority in cyber defense-related crisis management. ● The Cyber Defence Management Board (CDMB) is responsible for coordinating cyber defense throughout NATO civilian and military bodies. The CDMB comprises the leaders of the policy, military, operational and technical bodies in NATO as well.

Solution ● In order to successfully limit the technological advancement and distribution of technology which can be harmful to the global society, a worldwide organization must be created. ● All first world countries will join together to create The World Technological Control Organization (WTCO) which will monitor and restrict technological advances on autonomous weapons or cyber hacking which can potentially have a negative impact on the global society.

Conclusion ● Overall, The World Technological Control Organization is created to prevent and ban new technological innovations that can negatively impact the global society through the political, economic, cultural, and environmental perspective. Whether it’s dealing with restrictions on military technology, robotic employment, disruption of culture and landmarks, or leading to the deforestation and destruction of nature.

Bibliography ➢ “Technology Definition and Meaning | Collins English Dictionary. ” Take Heed/Pay Heed Definition and Meaning | Collins English Dictionary, n. d. , 2018. Accessed: 10/3/2018, https: //www. collinsdictionary. com/us/dictionary/english/technology ➢ Knuth, Don, The Dangers of Technological Development Don Knuth's Home Page, 2018. Accessed: 10/3/2018, https: //cs. stanford. edu/people/eroberts/cs 181/projects/technology-dangers/issues. html ➢ Loendorf, William, The social, economic, and political impact of technology: an historical perspective, American Society for Engineering and Education, 2010. Accessed: 10/4/18 ➢ United Nations, Federal Public Service Foreign Affairs, March 14, 2010, Accessed: 10/5/18, https: //diplomatie. belgium. be/en/policy_areas/peace_and_security/in_international_organisations/united_nation s ➢ “Frequently Asked Questions on the Rules of War. ” Comité Internacional De La Cruz Roja, November 3, 2017, Accessed: 10/7/18, https: //www. icrc. org/en/document/ihl-rules-of-war-FAQ-Geneva-Conventions

Bibliography ➢ General Mac. Arthur's Thayer Award Speech -- Duty, Honor, Country (1962). , Accessed: 10/9/18, http: //www. au. af. mil/au/awcgate/gabrmetz/gabr 0022. htm. ➢ Asher-Schapiro, Avi. “U. S. Drone Strikes in Iraq and Syria | Washington Spectator. ” Washington Spectator. December 29, 2018. Accessed: 10/13/15, https: //washingtonspectator. org/drones-syria-obama/ ➢ “Airwars Home – New. ” Airwars, n. d. Accessed: 10/15/18, https: //airwars. org/. ➢ Computer Crime Statutes, National Conferences of State Legislatures, 2018. Accessed: 10/20/18, http: //www. ncsl. org/research/telecommunications-and-information-technology/computer-hacking-and-unauthorizedaccess-laws. aspx ➢ Breene, Keith. “Who Are the Cyberwar Superpowers? ” World Economic Forum, n. d. Accessed: 10/20/18, https: //www. weforum. org/agenda/2016/05/who-are-the-cyberwar-superpowers/ ➢ NATO. “Cyber Defence. ” NATO, n. d. Accessed: 10/20/18, https: //www. nato. int/cps/en/natohq/topics_78170. htm.

Bibliography ➢ Ministère de l'Europe et des Affaires étrangères. “Cyber Security. ” France Diplomatie : : Ministry for Europe and Foreign Affairs. Accessed: 10/21/18, www. diplomatie. gouv. fr/en/french-foreign-policy/defence-security/cyber-security/. ➢ “Cyberattack during the Paris G 20 Summit. ” Wikipedia, Wikimedia Foundation, August 15, 2017. Accessed: 11/21/18 https: //en. wikipedia. org/wiki/Cyberattack_during_the_Paris_G 20_Summit#Attacks_in_December_2010 -January_2011 ➢ Ap. “France Hit by Unprecedented Wave of Cyber Attacks. ” CBS News, CBS Interactive, January 15, 2015. Accessed: 10/21/18, www. cbsnews. com/news/france-hit-by-19000 -cyber-attacks-after-charlie-hebdo-terror-attacks/. ➢ “Cyber Warfare in the United States. ” Wikipedia. Wikimedia Foundation, October 13, 2018. Accessed: 10/22/18, https: //en. wikipedia. org/wiki/Cyberwarfare_in_the_United_States#Cyberattack_as_an_act_of_war. ➢ “Trump's New Drone Strike Policy: What's Any Different? Why It Matters. ” Just Security, August 6, 2018. Accessed: 10/22/18, https: //www. justsecurity. org/45227/trumps-drone-strike-policy-different-matters/. ➢ Mc. Veigh, Karen. “'Crazy Numbers': Civilian Deaths from Airstrikes Almost Double in a Year. ” The Guardian News and Media, January 8, 2018. Accessed: 11/22/18, https: //www. theguardian. com/global-development/2018/jan/08/civilian-deaths -from-airstrikes-almost-double-year. ➢ “Raising the Consequences of Hacking American Companies. ” Nuclear Stability in a Post-Arms Control World | Center for Strategic and International Studies, Accessed: 11/23/18, www. csis. org/analysis/raising-consequences-hacking-americancompanies.

Picture Sources ● https: //www. planetdeadly. com/wp-content/uploads/teapot-nuclear-blast. jpg ● https: //assets. weforum. org/editor/6 CL 6 u. AHD 0 Ti. T 5 q 9 NW 9 Bz. MAq. WKBC 5 v. W-Sqr. V 5 KCEvm-E. png ● https: //ichef. bbci. co. uk/news/660/cpsprodpb/1 D 5 D/production/_87071570_treaty. jpg ● https: //i. guim. co. uk/img/media/84 e 4 e 4 f 6 f 04880 f 4 bb 4 adb 10 c 8 ebb 42 ef 62 f 1665/0_0_2906_1743/master/290 6. jpg? width=620&quality=85&auto=format&fit=max&s=bfe 0262704 dd 6 ede 0 ab 703 f 51 dc 48948 ● https: //assets 2. thebureauinvestigates. com/uploads/_header. Medium/7046443151_301 c 8 e 8 c 02_b. jpg? mtim e=20170206160946 ● https: //ig. ft. com/sites/special-reports/cyber-attacks/media/gr 236 x_chart_4_data_breach-mr_eefnzsk. jpg ● https: //foreignpolicymag. files. wordpress. com/2017/01/french-crop. jpg? w=960 ● http: //static 5. uk. businessinsider. com/image/57474460 dd 089598668 b 4584 -700 -517/cyber%20 attacks. jpg ● https: //obamawhitehouse. archives. gov/sites/whitehouse. gov/files/images/Blog/Cybersecurity%20 R%26 D% 20 Strategy%20 graphic. jpg