Timing and Performance Ethernet Communication Ethernet allows for
- Slides: 1

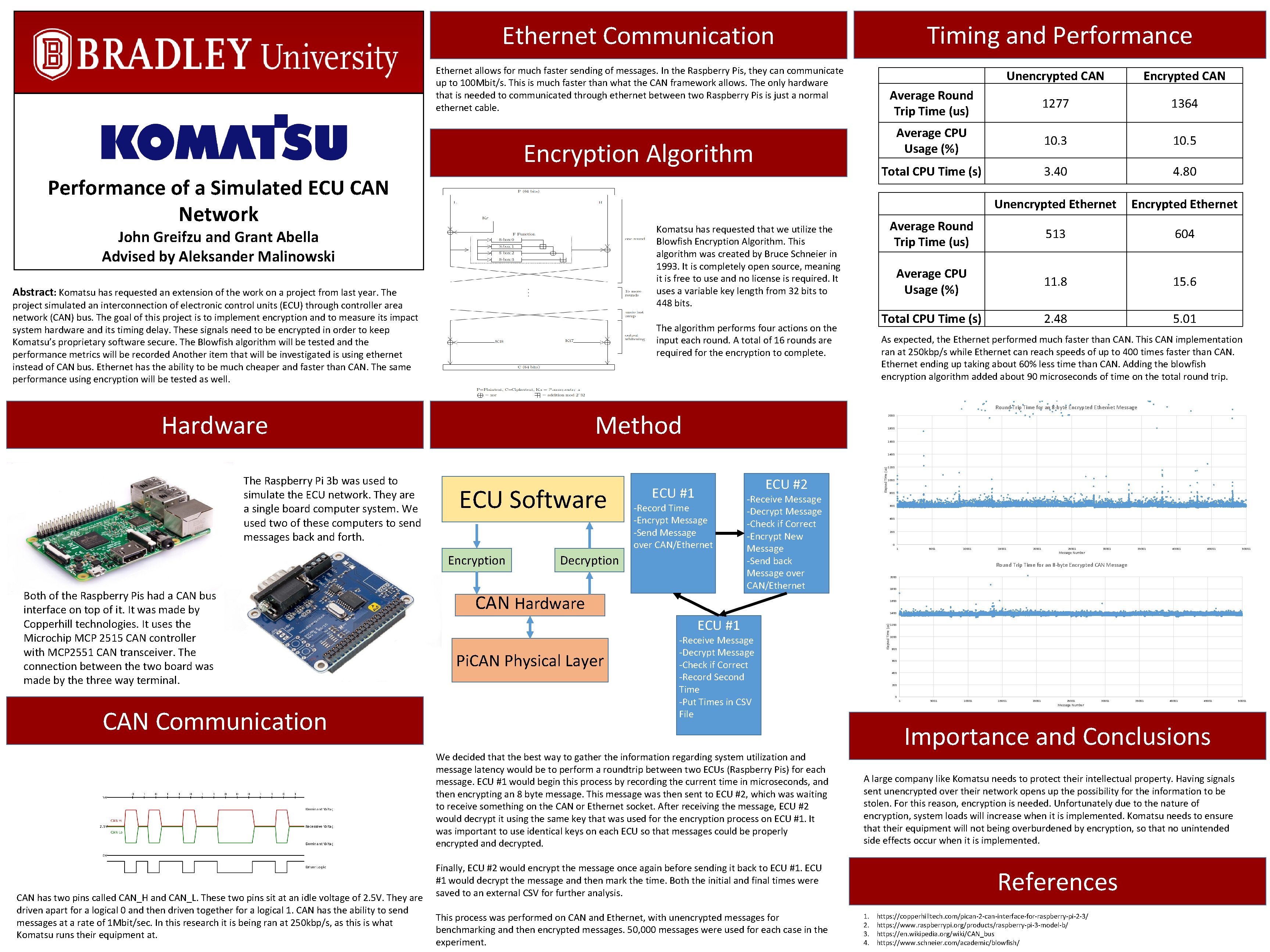
Timing and Performance Ethernet Communication Ethernet allows for much faster sending of messages. In the Raspberry Pis, they can communicate up to 100 Mbit/s. This is much faster than what the CAN framework allows. The only hardware that is needed to communicated through ethernet between two Raspberry Pis is just a normal ethernet cable. Encryption Algorithm Performance of a Simulated ECU CAN Network Unencrypted CAN Encrypted CAN Average Round Trip Time (us) 1277 1364 Average CPU Usage (%) 10. 3 10. 5 Total CPU Time (s) 3. 40 4. 80 Unencrypted Ethernet Encrypted Ethernet Average Round Trip Time (us) 513 604 Average CPU Usage (%) 11. 8 15. 6 Total CPU Time (s) 2. 48 5. 01 Komatsu has requested that we utilize the Blowfish Encryption Algorithm. This algorithm was created by Bruce Schneier in 1993. It is completely open source, meaning it is free to use and no license is required. It uses a variable key length from 32 bits to 448 bits. John Greifzu and Grant Abella Advised by Aleksander Malinowski Abstract: Komatsu has requested an extension of the work on a project from last year. The project simulated an interconnection of electronic control units (ECU) through controller area network (CAN) bus. The goal of this project is to implement encryption and to measure its impact system hardware and its timing delay. These signals need to be encrypted in order to keep Komatsu’s proprietary software secure. The Blowfish algorithm will be tested and the performance metrics will be recorded Another item that will be investigated is using ethernet instead of CAN bus. Ethernet has the ability to be much cheaper and faster than CAN. The same performance using encryption will be tested as well. The algorithm performs four actions on the input each round. A total of 16 rounds are required for the encryption to complete. As expected, the Ethernet performed much faster than CAN. This CAN implementation ran at 250 kbp/s while Ethernet can reach speeds of up to 400 times faster than CAN. Ethernet ending up taking about 60% less time than CAN. Adding the blowfish encryption algorithm added about 90 microseconds of time on the total round trip. Round Trip Time for an 8 -byte Encrypted Ethernet Message Method Hardware 2000 1800 1600 1400 ECU Software Encryption Both of the Raspberry Pis had a CAN bus interface on top of it. It was made by Copperhill technologies. It uses the Microchip MCP 2515 CAN controller with MCP 2551 CAN transceiver. The connection between the two board was made by the three way terminal. CAN Communication ECU #2 ECU #1 -Record Time -Encrypt Message -Send Message over CAN/Ethernet Decryption CAN Hardware -Receive Message -Decrypt Message -Check if Correct -Encrypt New Message -Send back Message over CAN/Ethernet 600 400 200 0 1 5001 10001 15001 20001 25001 Message Number 30001 35001 40001 45001 50001 Round Trip Time for an 8 -byte Encrypted CAN Message 2000 1800 1400 ECU #1 Pi. CAN Physical Layer 800 1600 1200 -Receive Message -Decrypt Message -Check if Correct -Record Second Time -Put Times in CSV File We decided that the best way to gather the information regarding system utilization and message latency would be to perform a roundtrip between two ECUs (Raspberry Pis) for each message. ECU #1 would begin this process by recording the current time in microseconds, and then encrypting an 8 byte message. This message was then sent to ECU #2, which was waiting to receive something on the CAN or Ethernet socket. After receiving the message, ECU #2 would decrypt it using the same key that was used for the encryption process on ECU #1. It was important to use identical keys on each ECU so that messages could be properly encrypted and decrypted. CAN has two pins called CAN_H and CAN_L. These two pins sit at an idle voltage of 2. 5 V. They are driven apart for a logical 0 and then driven together for a logical 1. CAN has the ability to send messages at a rate of 1 Mbit/sec. In this research it is being ran at 250 kbp/s, as this is what Komatsu runs their equipment at. 1000 Elapsed Time (us) The Raspberry Pi 3 b was used to simulate the ECU network. They are a single board computer system. We used two of these computers to send messages back and forth. Elapsed Time (us) 1200 1000 600 400 200 0 1 5001 10001 15001 20001 25001 Message Number 30001 35001 40001 45001 Importance and Conclusions A large company like Komatsu needs to protect their intellectual property. Having signals sent unencrypted over their network opens up the possibility for the information to be stolen. For this reason, encryption is needed. Unfortunately due to the nature of encryption, system loads will increase when it is implemented. Komatsu needs to ensure that their equipment will not being overburdened by encryption, so that no unintended side effects occur when it is implemented. Finally, ECU #2 would encrypt the message once again before sending it back to ECU #1 would decrypt the message and then mark the time. Both the initial and final times were saved to an external CSV for further analysis. This process was performed on CAN and Ethernet, with unencrypted messages for benchmarking and then encrypted messages. 50, 000 messages were used for each case in the experiment. 800 References 1. 2. 3. 4. https: //copperhilltech. com/pican-2 -can-interface-for-raspberry-pi-2 -3/ https: //www. raspberrypi. org/products/raspberry-pi-3 -model-b/ https: //en. wikipedia. org/wiki/CAN_bus https: //www. schneier. com/academic/blowfish/ 50001