Timing Analysis of Keystrokes And Timing Attacks on









- Slides: 31

Timing Analysis of Keystrokes And Timing Attacks on SSH AUTHERS: DAWN XIAODONG SONG, DAVID WAGNER XUQING TIAN PUBLICATION: USENIX SECURITY SIMPOSIUM 2001 PRESENTER: HIRAL CHHAYA FOR CAP 6133

OUTLINE…… Secure Shell (SSH) weaknesses Analysis Attack of user keystroke patterns using inter-keystroke timing Performance evaluation Countermeasures Comments and conclusion

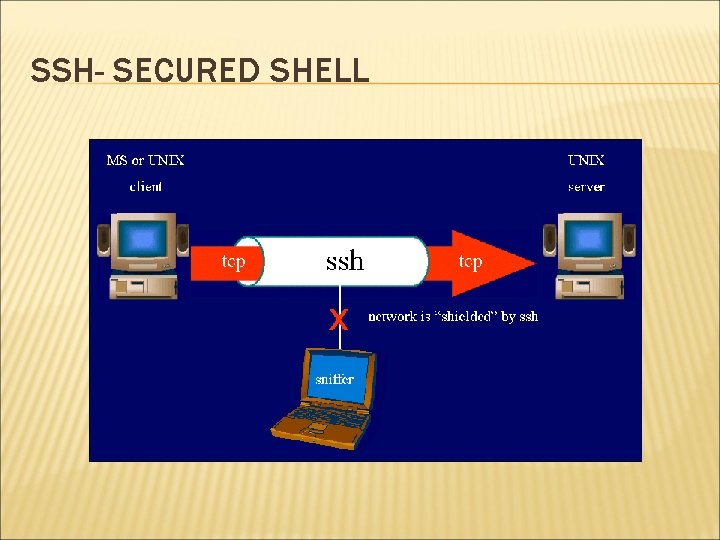
SSH- SECURED SHELL Offers an encrypted channel and strong authentication. Replaces telnet, rlogin. protects a network from attacks such as IP spoofing, IP source routing, and DNS spoofing. If attacker tries to takeover the network SSh diconnects.

SSH- SECURED SHELL

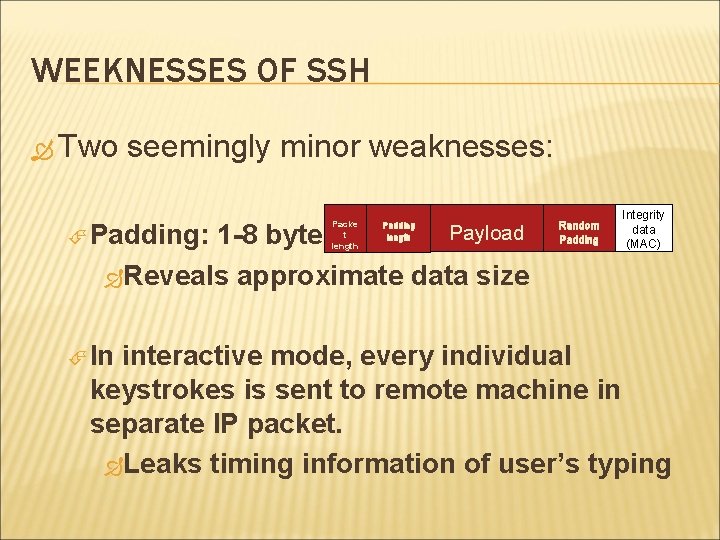
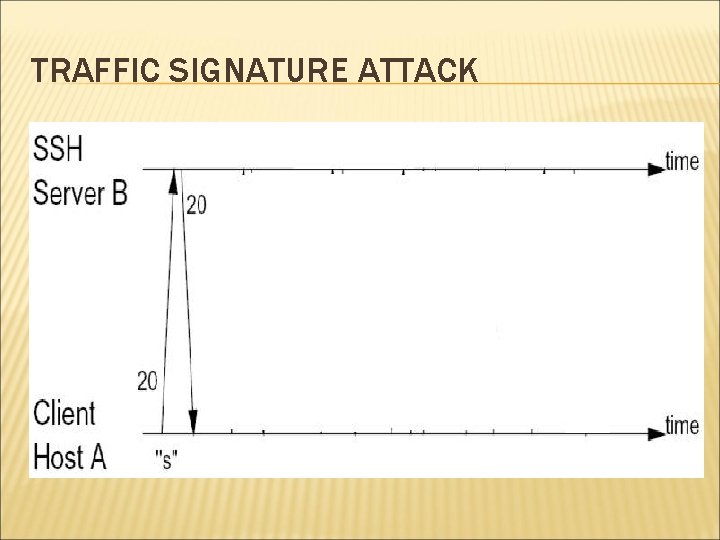
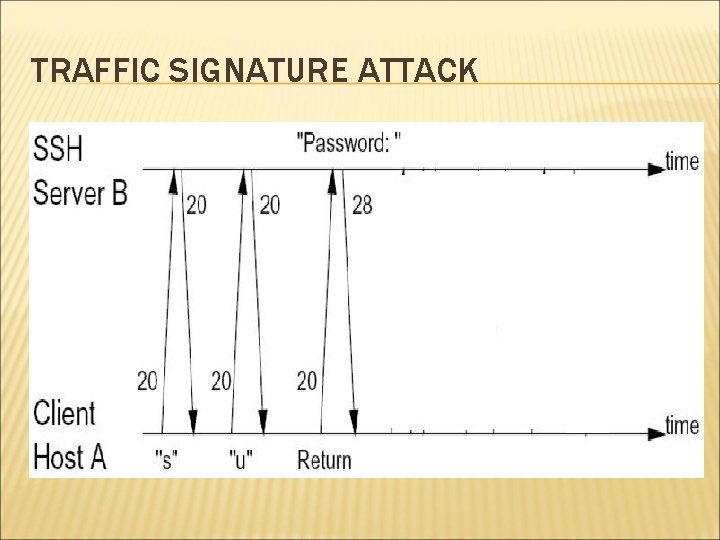
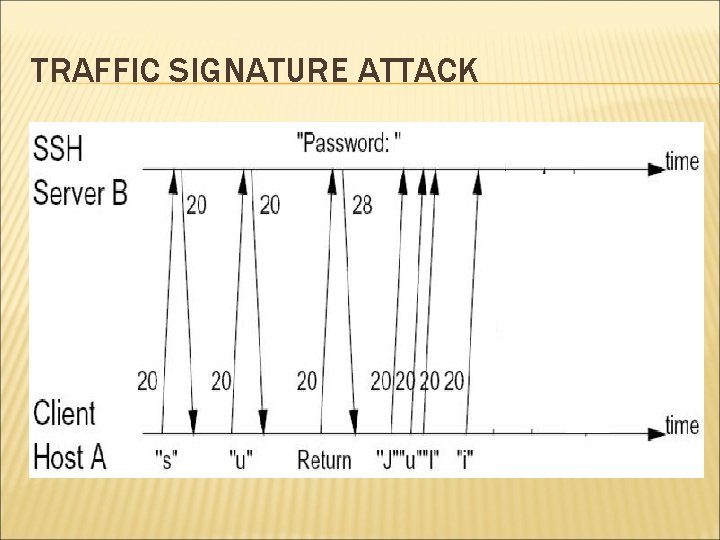
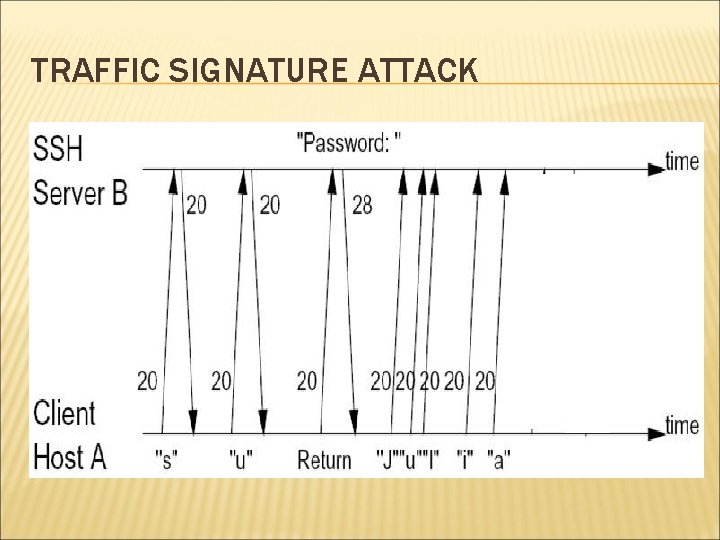
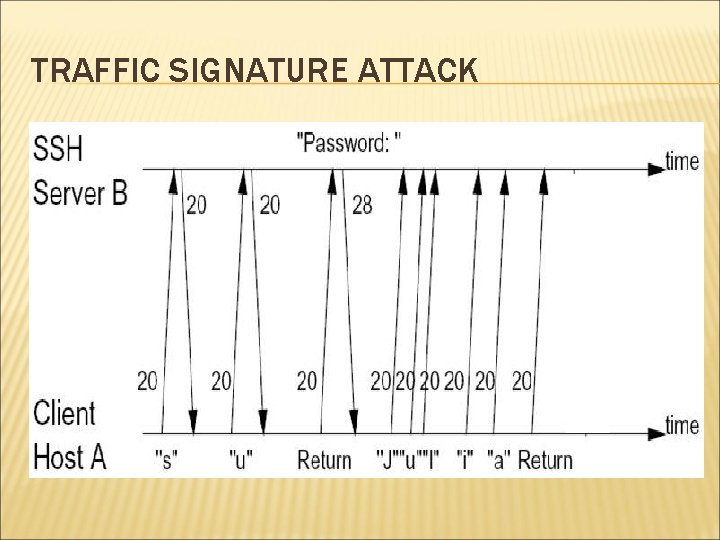
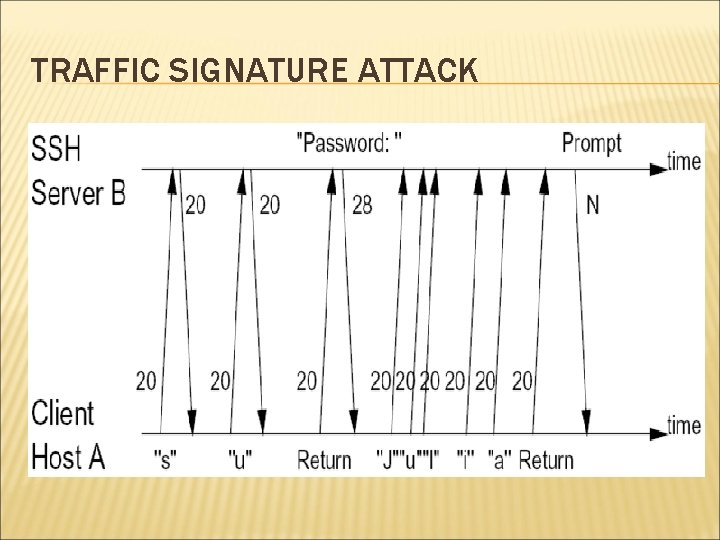
WEEKNESSES OF SSH Two seemingly minor weaknesses: Padding: Payload 1 -8 bytes Reveals approximate data size In Packe t length Padding length Random Padding Integrity data (MAC) interactive mode, every individual keystrokes is sent to remote machine in separate IP packet. Leaks timing information of user’s typing

TRAFFIC SIGNATURE ATTACK

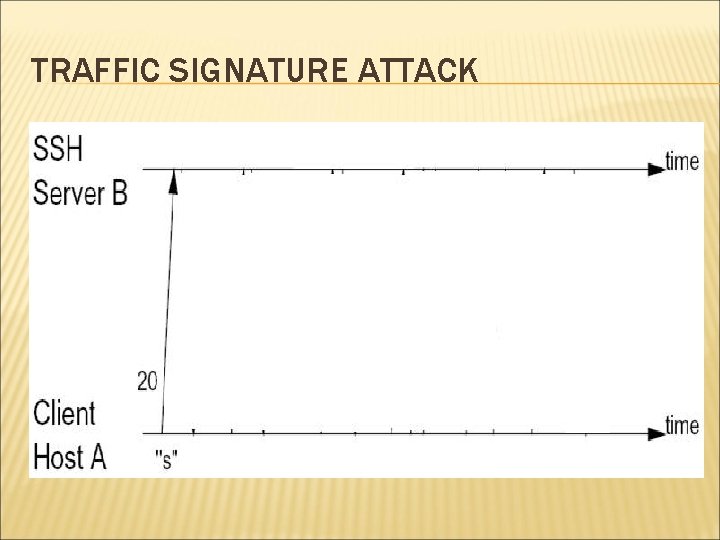
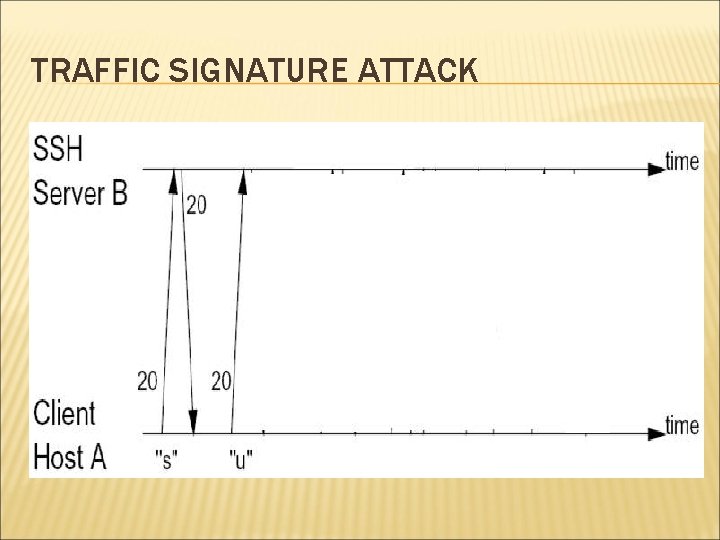
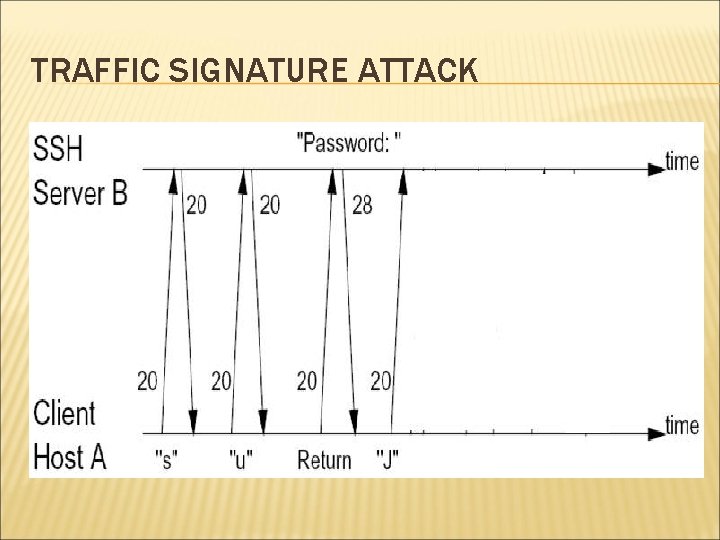
TRAFFIC SIGNATURE ATTACK

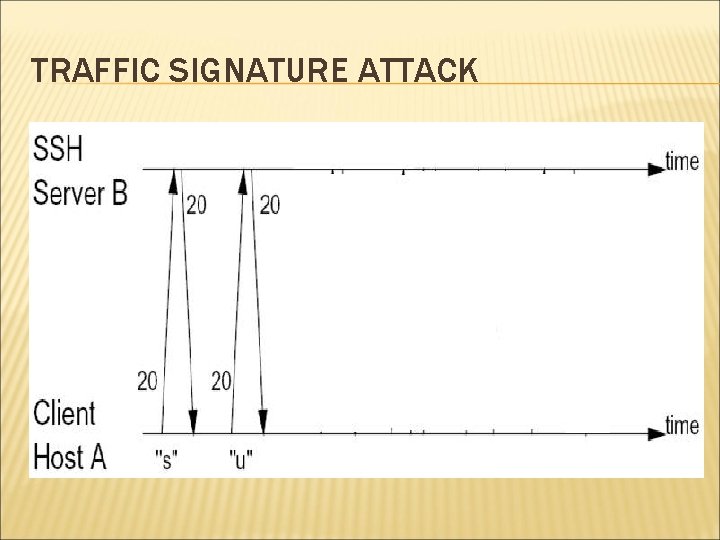
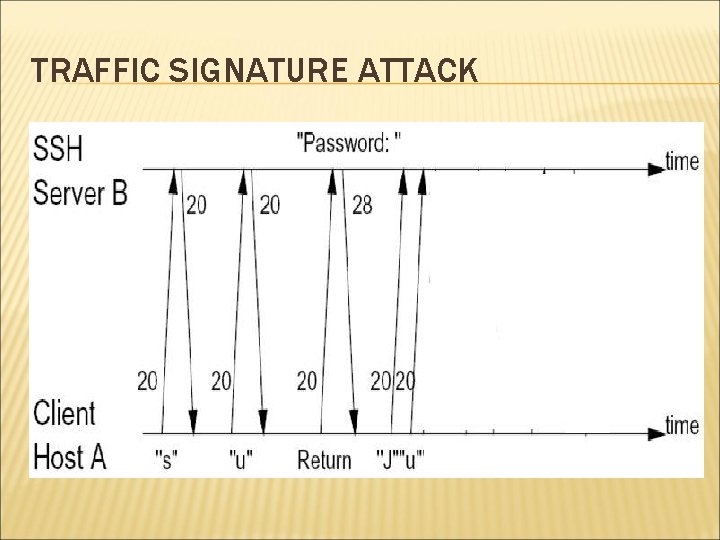
TRAFFIC SIGNATURE ATTACK

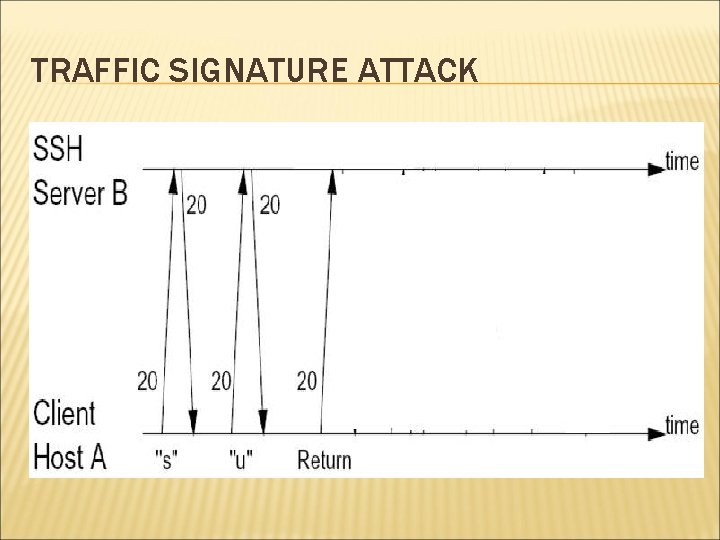
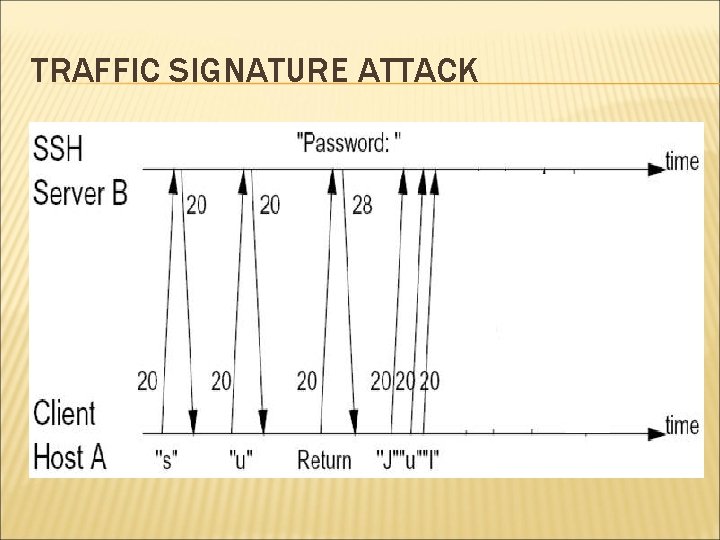
TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

TRAFFIC SIGNATURE ATTACK

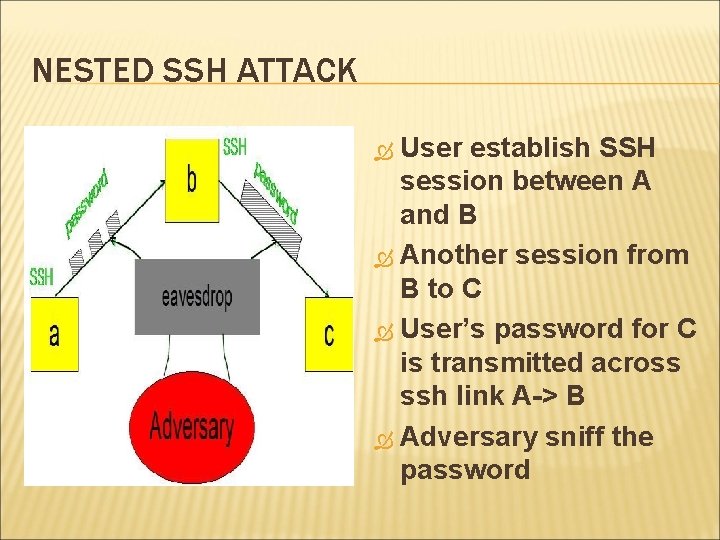
NESTED SSH ATTACK User establish SSH session between A and B Another session from B to C User’s password for C is transmitted across ssh link A-> B Adversary sniff the password

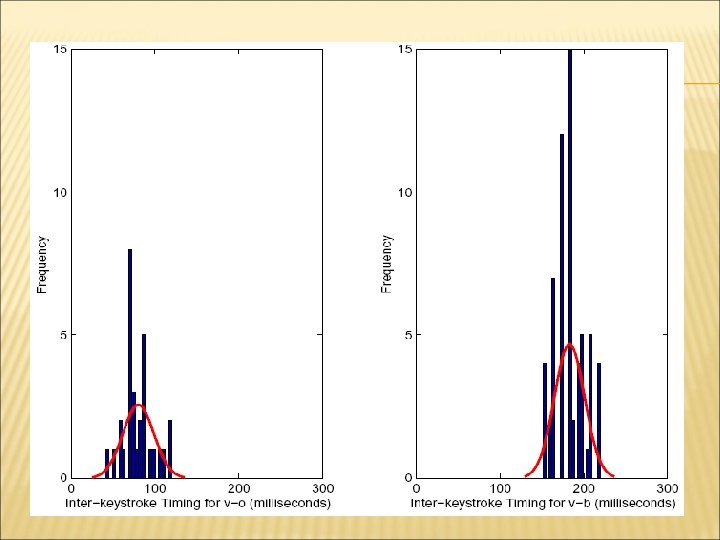
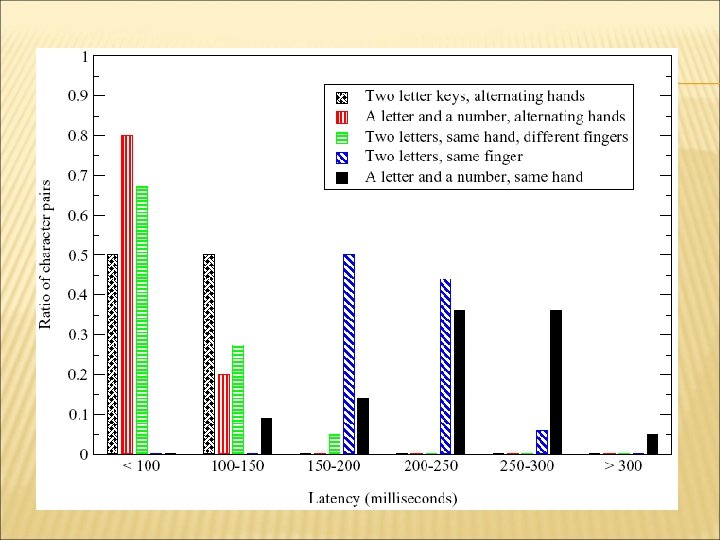
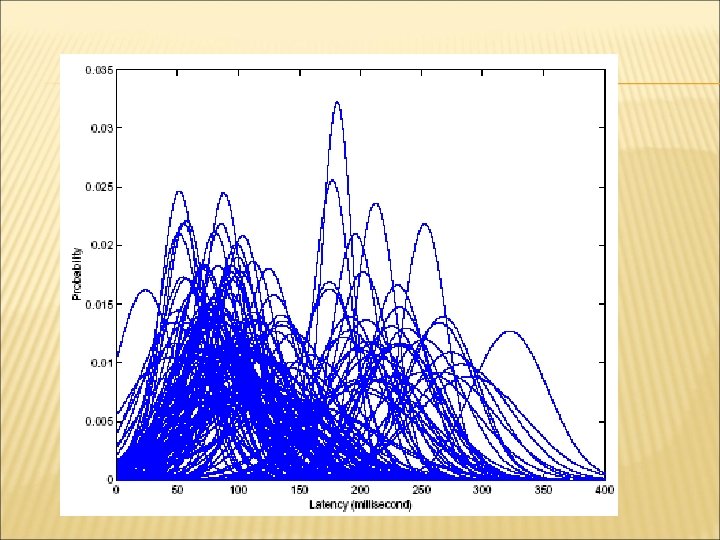
STATISTICAL ANALYSIS OF INTER-KEYSTROKE TIMINGS Pick a pair of characters, e. g. (“v”, “o”) Ask users to type the pair for 30 -40 times Collect latency information Repeat for every different pair of characters




HIDDEN MARKOV MODEL (HMM) HMM - A Markov model when the current state can not be observed. Outputs of the process are observed. Probability of output depends only on the state. Information on the prior path of the process can be inferred from it’s output.

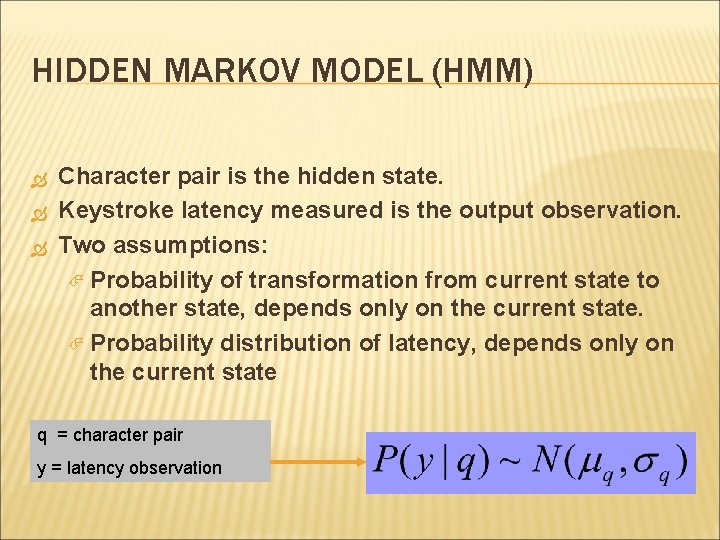
HIDDEN MARKOV MODEL (HMM) Character pair is the hidden state. Keystroke latency measured is the output observation. Two assumptions: Probability of transformation from current state to another state, depends only on the current state. Probability distribution of latency, depends only on the current state q = character pair y = latency observation

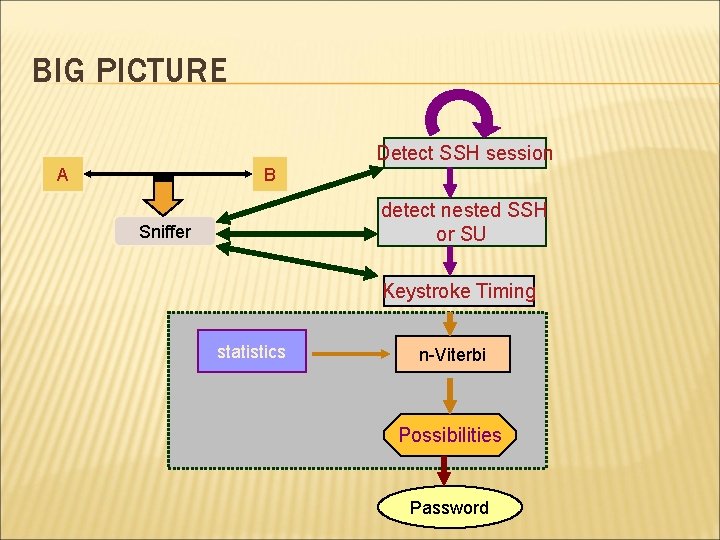
BIG PICTURE A B Detect SSH session detect nested SSH or SU Sniffer Keystroke Timing statistics n-Viterbi Possibilities Password

COUNTERMEASURES Let the server return dummy packets when it receives keystroke packets from the client. Let the client randomly delay sending keystroke packets. Let the client send keystroke packets at a constant rate.

STRENGTHS Novel Nice idea technique Good performance Interesting findings Countermeasures given

WEEKNESSES No mention of how to deal with backspace No discussion of how different keyboard layouts affect the results Laptop vs desktop Different regions keyboard layouts in different

THANK YOU