Threats Flaws Attack Techniques Understanding Threats Defacement Infiltration




























- Slides: 43

Threats, Flaws & Attack Techniques

Understanding Threats • • Defacement Infiltration Phishing Pharming Insider Threats Click Fraud Denial of Service Data Theft/Loss

Defacement • Online destruction, attackers replace legitimate pages with illegitimate ones • Targeted towards political web sites • Ex: White House website defaced by anti-NATO activists, Chinese hackers

Infiltration • Unauthorized parties gain access to resources of computer system (e. g. CPUs, disk, network bandwidth) • Could gain read/write access to back-end DB • Ensure that attacker’s writes can be detected • Different goals for different organizations – Political site only needs integrity of data – Financial site needs integrity & confidentiality

Phishing • Attacker sets up spoofed site that looks real – attracts, users to enter login credentials and stores them – Usually sent through an e-mail with link to spoofed site asking users to “verify” their account info – The links might be disguised through the click texts – Watchful users can see actual URL if they hover link

Pharming • Like phishing, attacker’s goal is to get user to enter sensitive data into spoofed website. • Attacker can redirect the user to fake website, even if he entered the correct web site address by the DNS spoofing. • Attacker makes DNS translate legitimate URL to their IP address instead, and the result gets cached, poisoning future replies as well

Insider Threats • Attacks carried out with cooperation of insiders – Insiders could have access to data and leak it – Ex: DB and Sys Admins usually get complete access • Separation of Privilege / Least Privilege Principle – Provide individuals with only enough privileges needed to complete their tasks – Don’t give unrestricted access to all data and resources

Click Fraud • Targeted against pay-per-click ads • Attacker could click on competitor’s ads – reduces other’s ad budgets, gains exclusive attention of legitimate users • Site publishers could click on ads to get revenue

Denial of Service (Do. S) • Attacker floods server with packets causing it to drop legitimate packets – Makes service unavailable, downtime = lost revenue • Particularly a threat for financial and ecommerce vendors

Data Theft and Data Loss • Several Examples: Bof. A, Choice. Point, Veteran’s Admn. – Bof. A: backup data tapes lost in transit – Choice. Point: fraudsters queried DB for sensitive info – VA: employee took computer to home & his home was robbed • California state laws, require companies to disclose theft/loss • Even for encrypted data, should store key in separate media

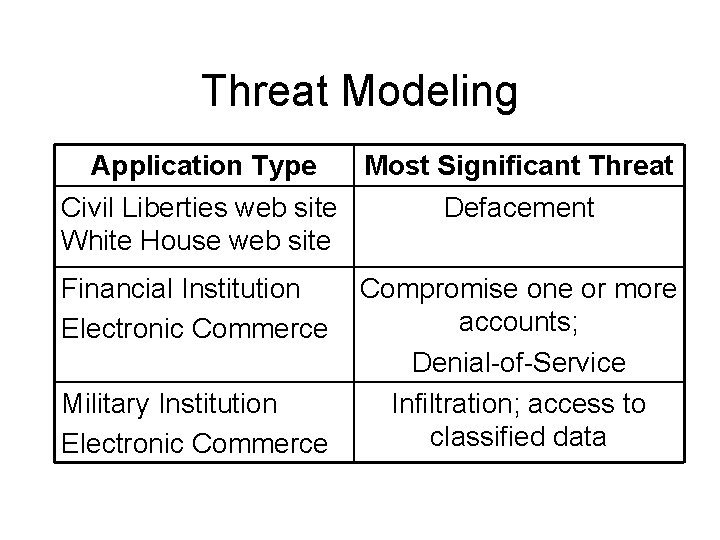
Threat Modeling Application Type Most Significant Threat Civil Liberties web site Defacement White House web site Financial Institution Electronic Commerce Military Institution Electronic Commerce Compromise one or more accounts; Denial-of-Service Infiltration; access to classified data

Designing-In Security • Design features with security in mind – Not as an afterthought – Hard to “add-on” security later • Bad Examples: Windows 98, Internet

Windows 98 • Diagnostic Mode: – Accessed through 'F 8' key when booting – Can bypassword protections, giving attacker complete access to hard disks & data • Username/Password Security was added as an afterthought • Should have been included at the start, then required it for entering diagnostic mode

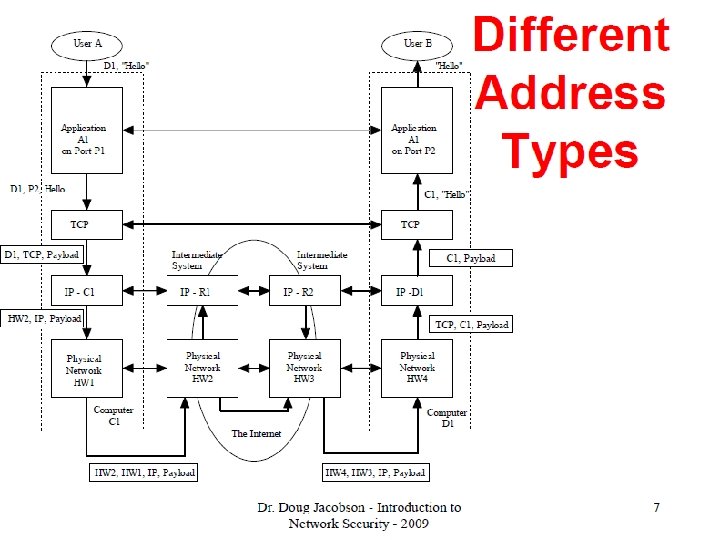
The Internet • All nodes originally university or military (i. e. trusted) since it grew out of DARPA • With commercialization, lots of new hosts, allowed to connect to existing hosts regardless of whether they were trusted • Deployed Firewalls: allows host to only let in trusted traffic • Loopholes: lying about IPs, using cleared ports


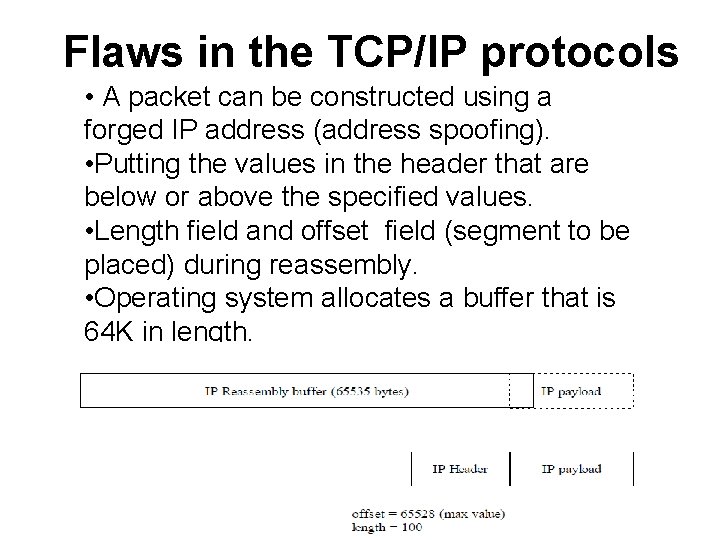
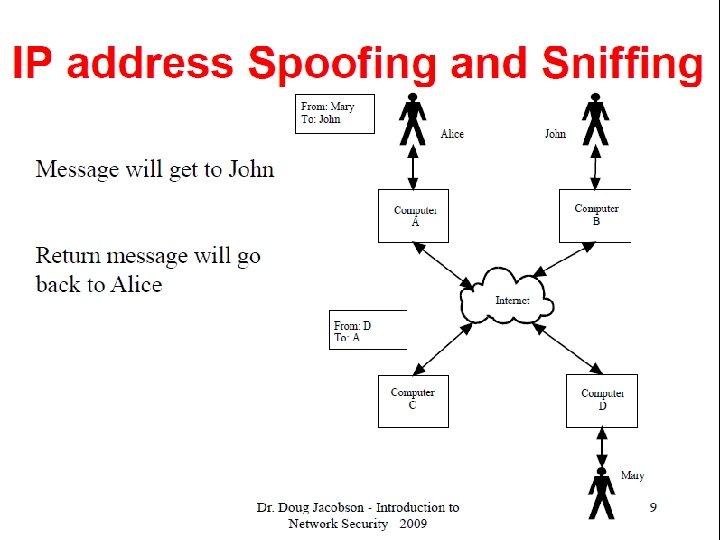
Flaws in the TCP/IP protocols • A packet can be constructed using a forged IP address (address spoofing). • Putting the values in the header that are below or above the specified values. • Length field and offset field (segment to be placed) during reassembly. • Operating system allocates a buffer that is 64 K in length.


Packet Sniffing • A packet sniffer reads all the packets passing it. • This works well in shared environment, but is of limited value on a switched network, where packets are only sent between communicating pairs of machines


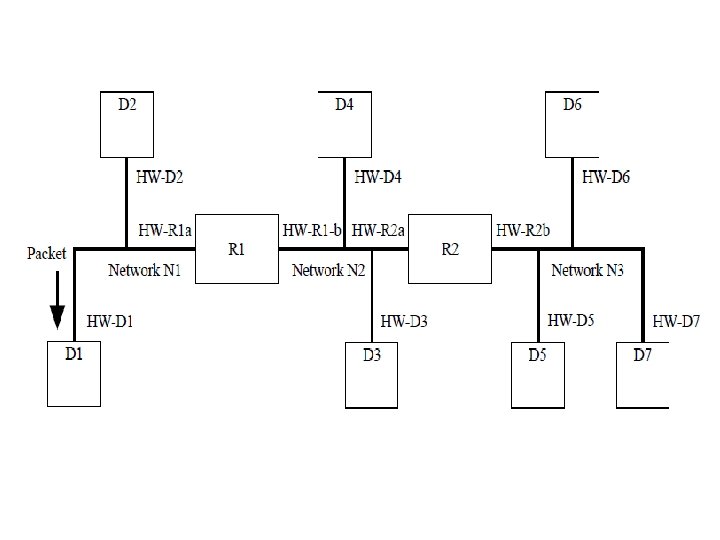
Hardware Addressing • A LAN provides connectivity for all computers but most communications are one-to-one – to avoid unnecessary interruptions, each NIC is assigned a unique numerical address (48 bits) called its hardware address, physical address or MAC address • Each frame transmitted across the network includes a destination and a source MAC address field – the destination MAC address is decoded to determine whether to accept it – the source address field is used when a reply is needed

Other Addressing Modes • Broadcasting – some applications require that a sender transmits a frame to all stations on the network – use a special reserved broadcast address as destination – all NICs are configured to accept frames with their own address and the broadcast address • Promiscuous Mode – NICs can often be configured to accept all packets – useful for network analysers (sniffers). – has security suggestions

TCP If an attacker can predict the starting point, then the recipient can be tricked into believing he is talking to a trusted machine. UDP Much easier to spoof UDP packets, since there is no handshake or sequence numbers. ARP Determines mappings. ARP spoofing, sniffer responds to the ARP message first, then all traffic will be sent to the sniffer. ARP messages can be emitted and all traffic could be diverted to itself (if hacker has the write access).

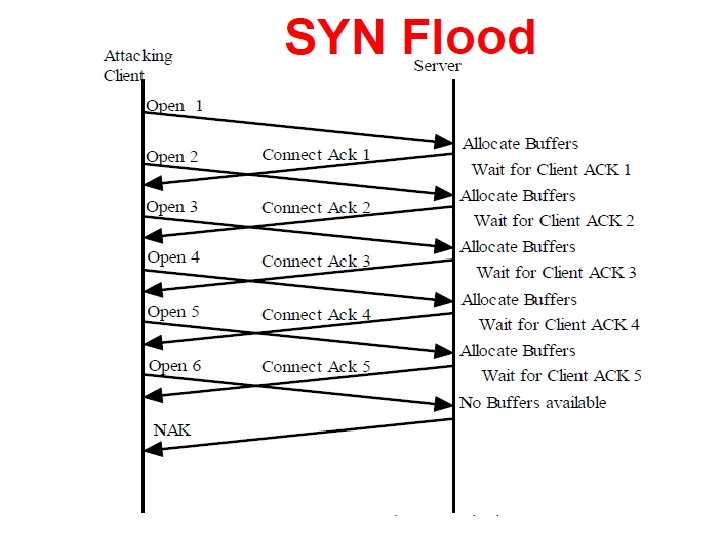
SYN Flood • Source system sends a large number of TCP synchronise sequence numbers" (SYN) packets to the target system. • Spoofed IP address • Target’s buffer will be become full. TCP 3 -way handshake


Defences • Reduce the timer wait • Increase the size of the buffer • Install network devices are capable of identifying SYN flood attacks • Firewalls are capable of reducing the effects of SYN floods • Intrusion detection system that can identify SYN flood attacks

ICMP • Internet control message protocol used to inform hosts of a better route, or to report trouble with a route or to terminate a connection due to network problems. • ICMP messages on a given host are specific to a particular connection • Redirect message or Destination Unreachable message should be connection specific but older version of ICMP implementation do not follow this convention. • possible to abuse ICMP to create new paths to a destination.

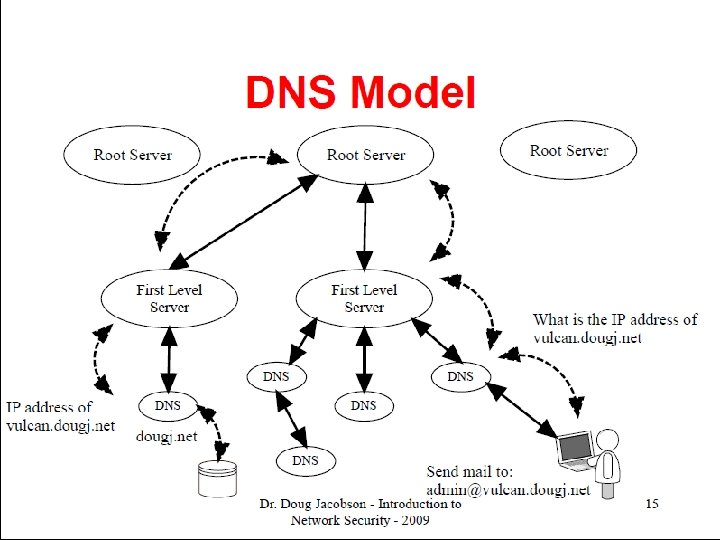
DNS • Domain Name Service. Distributed database system used to map host names to IP addresses, and vice versa. • DNS system is laid out in a tree structure with a set of root DNS servers that have knowledge about the location of the first level domain servers. • A first level domain server has information about the IP addresses of every host within its domain or knows which DNS server within its domain to ask.


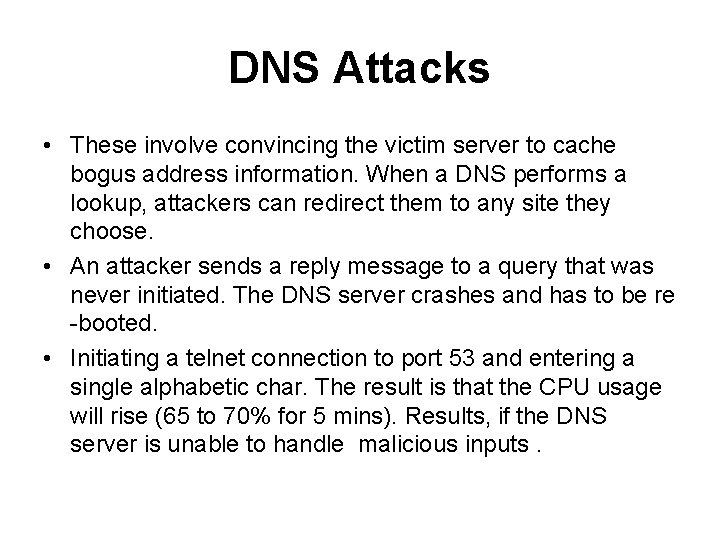
DNS Attacks • These involve convincing the victim server to cache bogus address information. When a DNS performs a lookup, attackers can redirect them to any site they choose. • An attacker sends a reply message to a query that was never initiated. The DNS server crashes and has to be re -booted. • Initiating a telnet connection to port 53 and entering a single alphabetic char. The result is that the CPU usage will rise (65 to 70% for 5 mins). Results, if the DNS server is unable to handle malicious inputs.

Defences • Zone transfers should be restricted to authorised servers only. • On the network side, configure the firewall to deny all unauthorised in-bound connections to TCP port 53

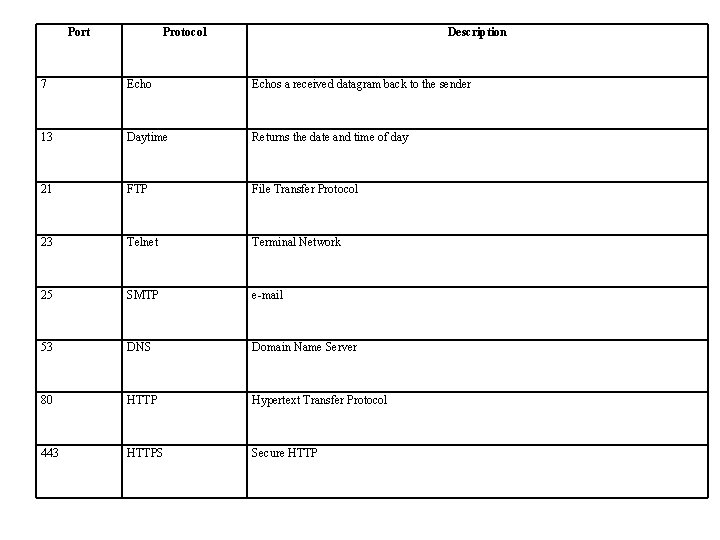
Port Protocol Description 7 Echos a received datagram back to the sender 13 Daytime Returns the date and time of day 21 FTP File Transfer Protocol 23 Telnet Terminal Network 25 SMTP e-mail 53 DNS Domain Name Server 80 HTTP Hypertext Transfer Protocol 443 HTTPS Secure HTTP

Routers • Easiest is to employ the IP loose source route option. • Inject bogus RIP packets into a network. • RIP suffers from the same problems as insecure DNS in that RIP depends only on the source IP address. Hosts and routers will generally believe them.

Telnet • Caller supplies an account name and usually a password to login. • Common hacking trick to use the local telnet program to record the user name and password. • Any hacker can steal the password and can enter into the system.

SMTP • Codes are well known and it is relatively easy for hackers to use them. • Using the codes, mail can be sent directly to port 25 on a particular server • You can not be sure who sent you email based on SMTP (The original SMTP specification did not include a facility for authentication of senders) • telnet mailservername. mywork. com 25 • mail from: hacker 1@bahria. edu. pk • rcpt to: victim@bahria. edu. pk • data quit

Denial of Service Attacks • Smurf, Fraggle and teardrop – are all techniques used by attackers to cause disorder over the Internet. • Do. S attack disturbs or completely denies service to legitimate users, networks or systems. • Attacker spoofs their source address to mask their identify. • Attacker is frustrated by the security of a particular site, then the final resort may be to launch a Do. S attack.

Do. S attacks techniques • Overloading the target system by consuming all the resources • Using the normal behaviour of the system to lock out legal users (Entering wrong passwords)

Ping of Death • All the attacker needed is the victim’s IP address. • IP packets have a maximum size of 65, 535 bytes • Maximum transmission unit (MTU) for an Ethernet LAN is 1500 bytes. • An oversized packet is constructed and sent to the target system causing the victim to crash.

Distributed Do. S • DDo. S attacks are usually controlled from a single master system and attack a single site. • Smurf - The attacker sends a ping packet to the broadcast address of a large network. The broadcast message is delivered to all stations on a network. The source IP address is spoofed and is the IP address of the system, which is to be attacked and all other sends reply to the victim.

War Dialling • The objective is to reveal easily penetrated modems. • As Internet connections become increasingly secure, attackers are looking for alternative back-door routes into the internal network. Unauthorized or poorly configured dial-up modems could give an intruder direct access to your internal servers.

Defences • Merge all dial-up connectivity to a central modem bank and make this an untrusted connection off the internal network (in the DMZ). • Use intrusion detection and firewalls to limit and monitor connection to trusted hosts. • Dial-back authentication – the remote system hangs up and immediately dials back.

War Driving • War driving is exactly, driving round with a laptop equipped with a wireless network interface card an antenna looking for sites with wireless networks. • Low security on wireless connection • Easy penetration

