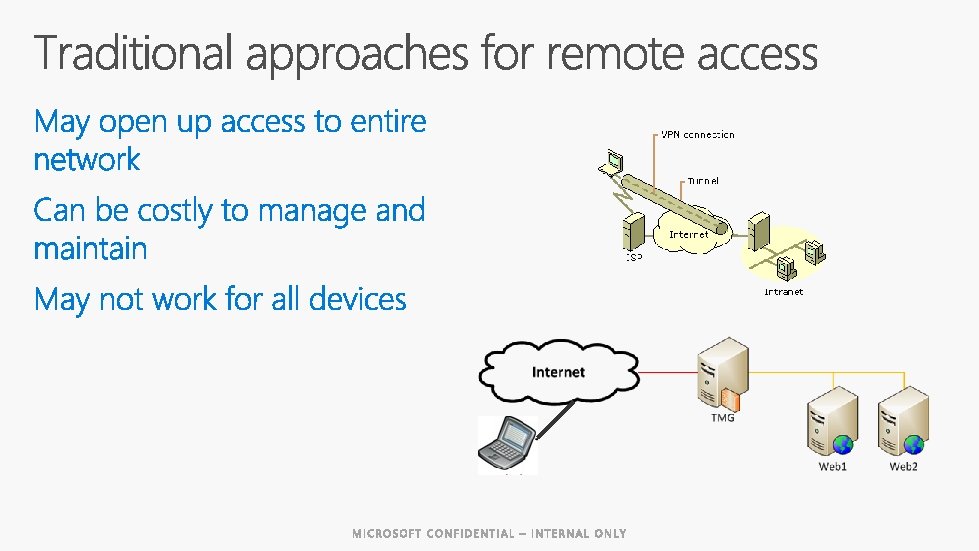
THR 3062 Any Device Any Place Any time




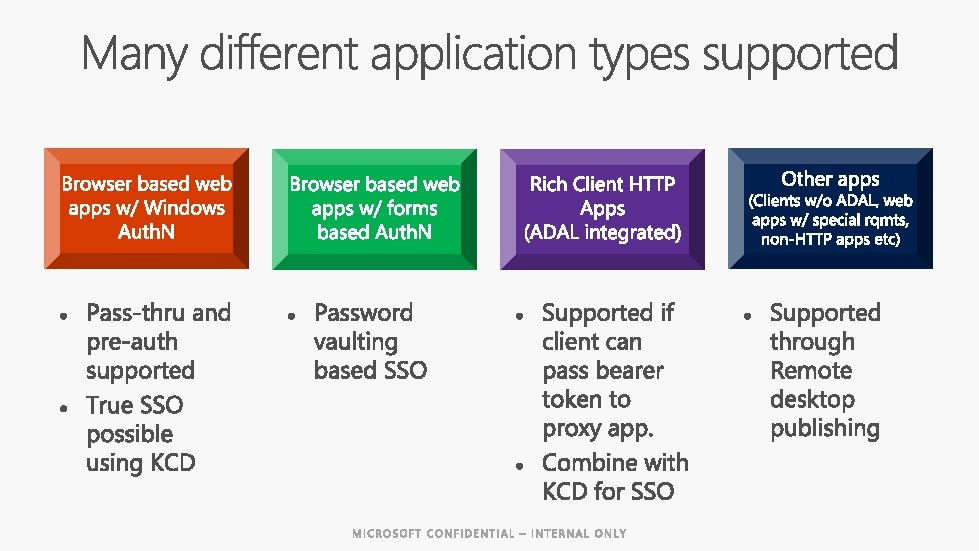



- Slides: 15

THR 3062

Any Device Any Place Any time Using their corporate identity To all their apps (including on-prem)


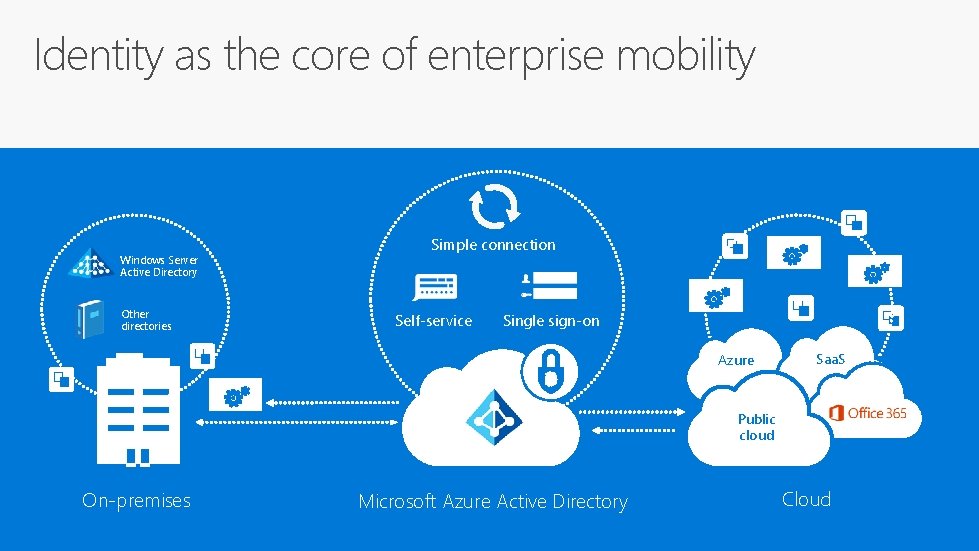
Identity as the core of enterprise mobility Windows Server Active Directory Other directories Simple connection Self-service Single sign-on Azure Saa. S Public cloud On-premises Microsoft Azure Active Directory Cloud

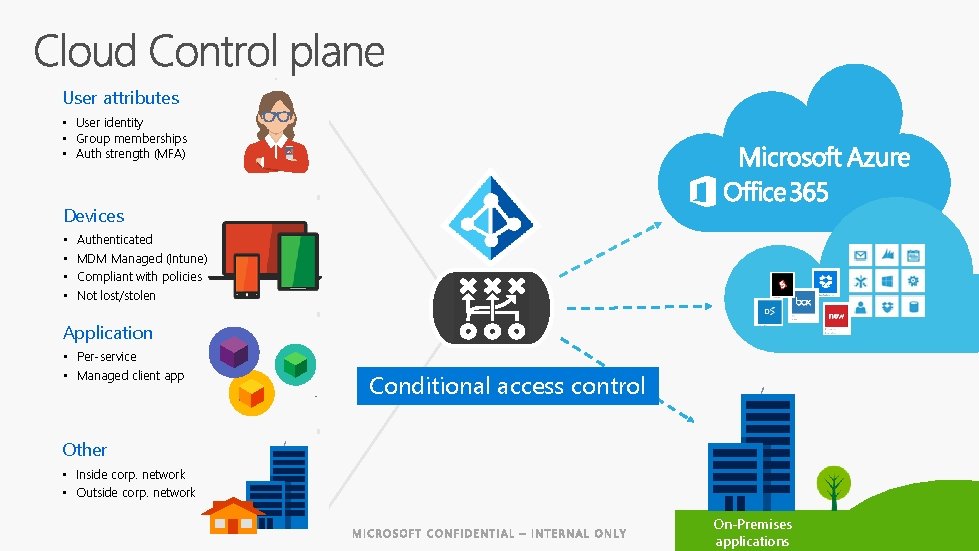
User attributes • User identity • Group memberships • Auth strength (MFA) Devices • • Authenticated MDM Managed (Intune) Compliant with policies Not lost/stolen Application • Per-service • Managed client app Conditional access control Other • Inside corp. network • Outside corp. network On-Premises applications

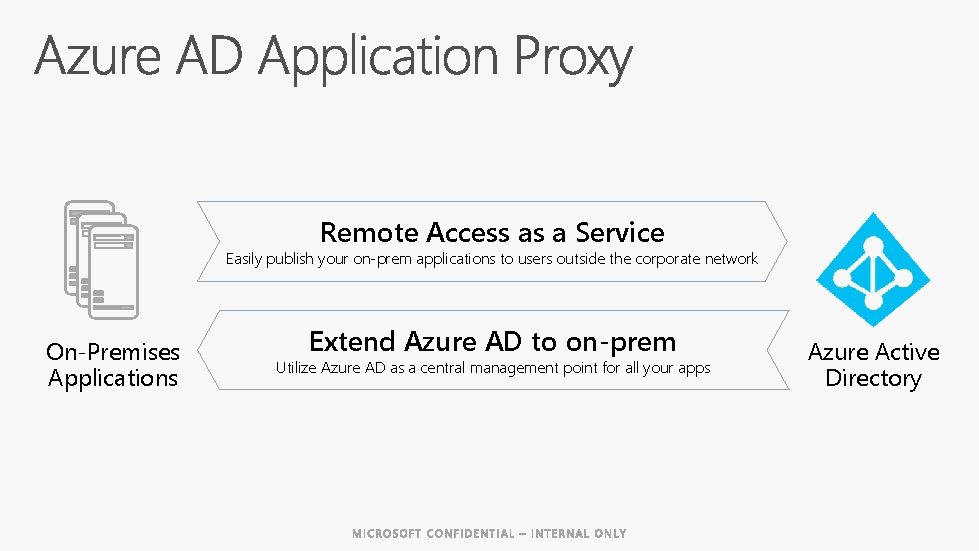
Remote Access as a Service Easily publish your on-prem applications to users outside the corporate network On-Premises Applications Extend Azure AD to on-prem Utilize Azure AD as a central management point for all your apps Azure Active Directory


“We’re also publishing more than 200 on prem web applications to the cloud with Azure Active Directory App Proxy which makes our employees lives easier since they can securely access these apps without VPN. ” Stephen Booth, IT Solution Manager, Unilever

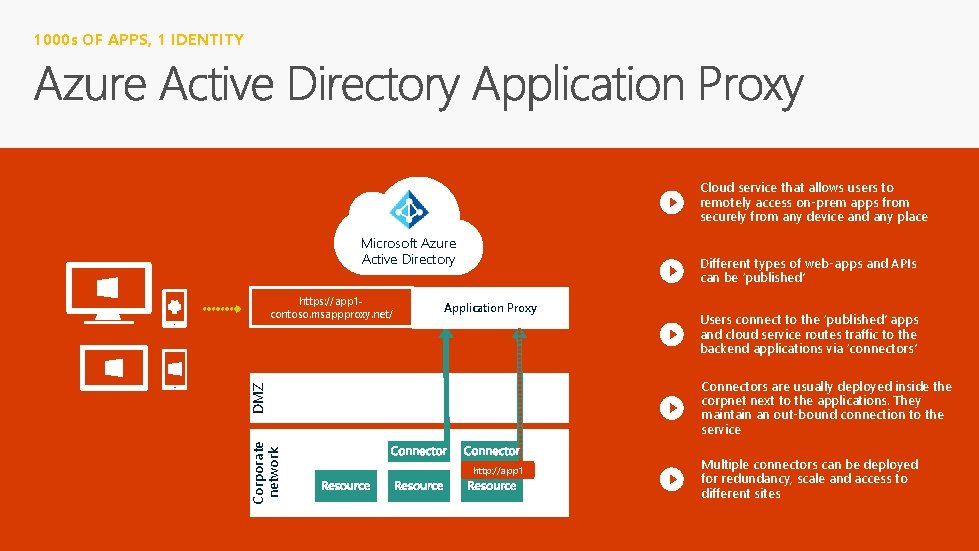
1000 s OF APPS, 1 IDENTITY Cloud service that allows users to remotely access on-prem apps from securely from any device and any place Microsoft Azure Active Directory Application Proxy Corporate network Users connect to the ‘published’ apps and cloud service routes traffic to the backend applications via ‘connectors’ Connectors are usually deployed inside the corpnet next to the applications. They maintain an out-bound connection to the service DMZ https: //app 1 contoso. msappproxy. net/ Different types of web-apps and APIs can be ‘published’ http: //app 1 Multiple connectors can be deployed for redundancy, scale and access to different sites


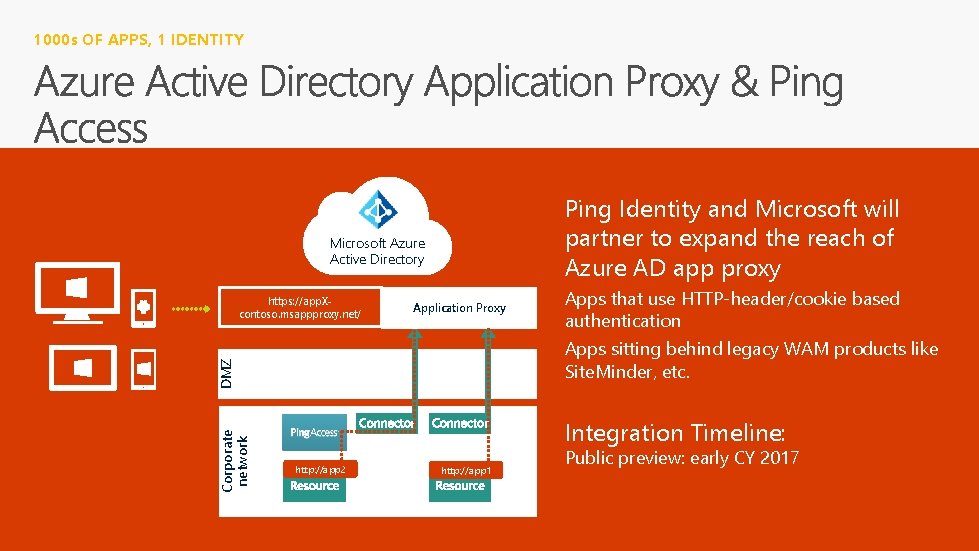
1000 s OF APPS, 1 IDENTITY Ping Identity and Microsoft will partner to expand the reach of Azure AD app proxy Microsoft Azure Active Directory https: //app. Xcontoso. msappproxy. net/ Application Proxy Apps sitting behind legacy WAM products like Site. Minder, etc. DMZ Corporate network Apps that use HTTP-header/cookie based authentication Integration Timeline: http: //app 2 http: //app 1 Public preview: early CY 2017


www. microsoft. com/itprocareercenter www. microsoft. com/itprocloudessentials www. microsoft. com/mechanics https: //techcommunity. microsoft. com

http: //myignite. microsoft. com https: //aka. ms/ignite. mobileapp
