Thesis Direction Introduction Henrry C Y Chiang Thesis






- Slides: 16

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) Thesis Direction Introduction Presented by: Henrry, C. Y. Chiang (江政祐) 10/7/202020071016 OPLAB, Dep. of Information Management, NTU 1 / 16

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) Today’s Agenda 1. Background 2. Motivation 3. Problem Description 4. Problem Formulation - Assumptions Given Parameters Objective function and Constraints Decision Variables 10/7/202020071016 OPLAB, Dep. of Information Management, NTU 2 / 16

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) Today’s Agenda 1. Background 2. Motivation 3. Problem Description 4. Problem Formulation - Assumptions Given Parameters Objective function and Constraints Decision Variables 10/7/202020071016 OPLAB, Dep. of Information Management, NTU 3 / 16

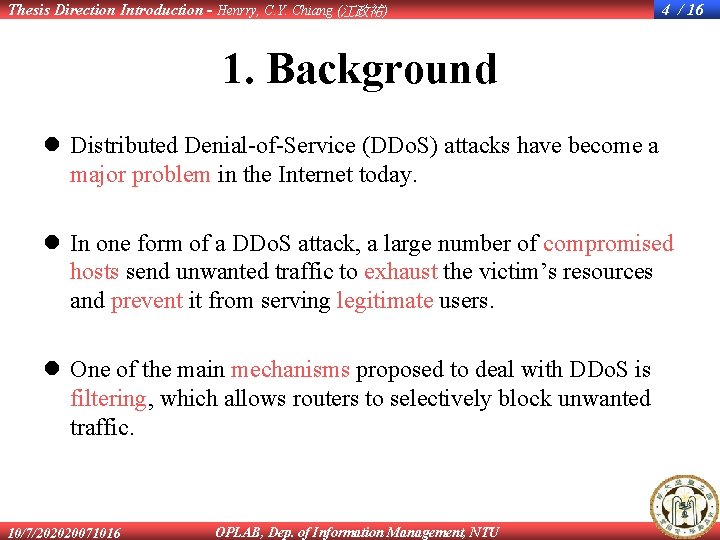
Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 4 / 16 1. Background l Distributed Denial-of-Service (DDo. S) attacks have become a major problem in the Internet today. l In one form of a DDo. S attack, a large number of compromised hosts send unwanted traffic to exhaust the victim’s resources and prevent it from serving legitimate users. l One of the main mechanisms proposed to deal with DDo. S is filtering, which allows routers to selectively block unwanted traffic. 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) Today’s Agenda 1. Background 2. Motivation 3. Problem Description 4. Problem Formulation - Assumptions Given Parameters Objective function and Constraints Decision Variables 10/7/202020071016 OPLAB, Dep. of Information Management, NTU 5 / 16

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 6 / 16 2. Motivation The proposed filtering mechanism to defend against distributed denial-of-service (DDo. S) attacks: l seldom considers the capability of the filter, the capability of the router and multiple (backup) servers under DDo. S attacks. l can not guarantee 100% legitimate traffic will not be mistakenly discarded. l has to consider the percentage of the total attack traffic filtered after filters have been allocated. 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) Today’s Agenda 1. Background 2. Motivation 3. Problem Description 4. Problem Formulation - Assumptions Given Parameters Objective function and Constraints Decision Variables 10/7/202020071016 OPLAB, Dep. of Information Management, NTU 7 / 16

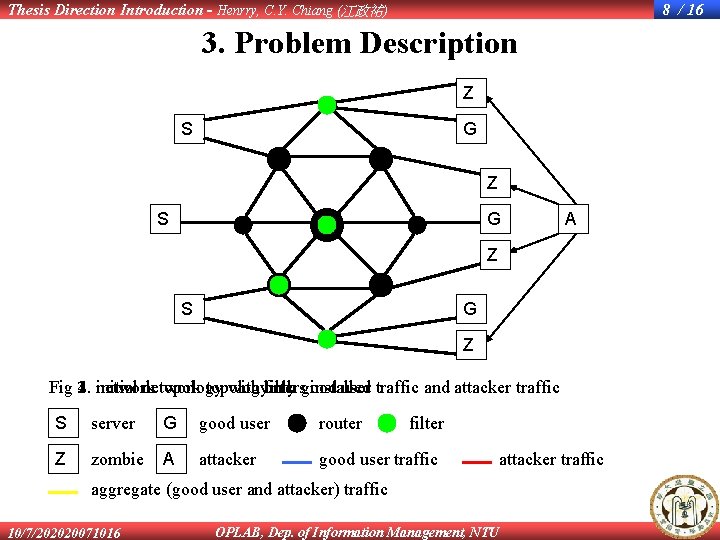
Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 8 / 16 3. Problem Description Z S G A Z S G Z Fig 2. 1. 3. network 4. initial network topology with only both good filters installed user traffic and attacker traffic S server G good user router Z zombie A attacker good user traffic filter attacker traffic aggregate (good user and attacker) traffic 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) Today’s Agenda 1. Background 2. Motivation 3. Problem Description 4. Problem Formulation - Assumptions Given Parameters Objective function and Constraints Decision Variables 10/7/202020071016 OPLAB, Dep. of Information Management, NTU 9 / 16

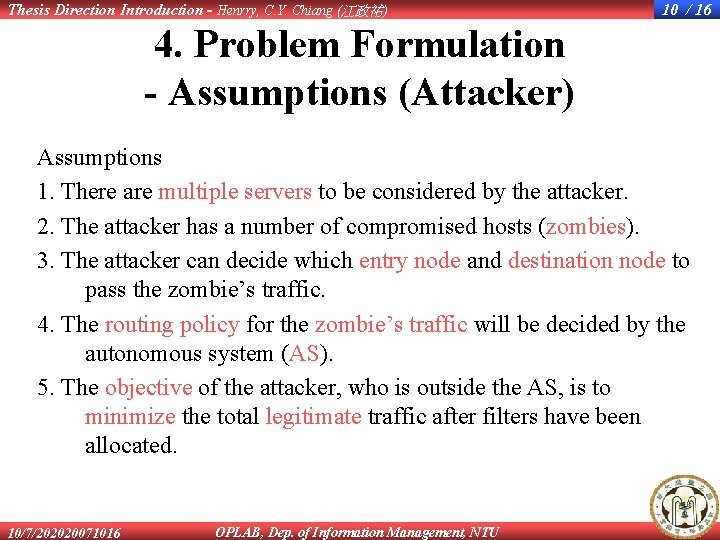
Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 10 / 16 4. Problem Formulation - Assumptions (Attacker) Assumptions 1. There are multiple servers to be considered by the attacker. 2. The attacker has a number of compromised hosts (zombies). 3. The attacker can decide which entry node and destination node to pass the zombie’s traffic. 4. The routing policy for the zombie’s traffic will be decided by the autonomous system (AS). 5. The objective of the attacker, who is outside the AS, is to minimize the total legitimate traffic after filters have been allocated. 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

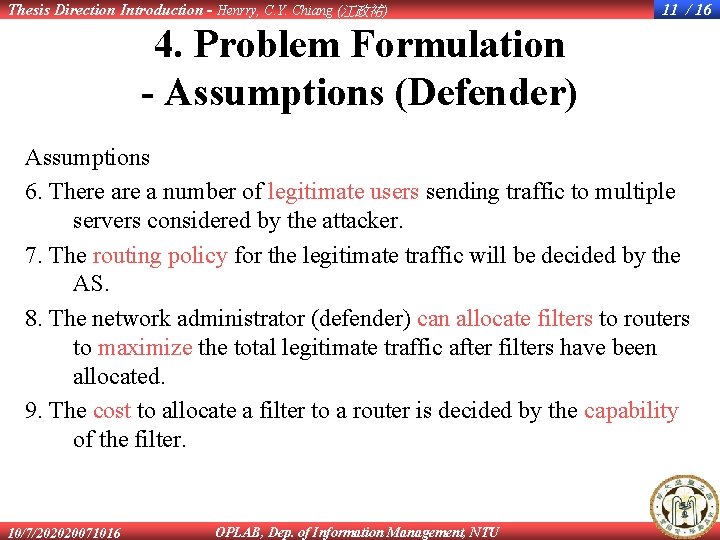
Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 11 / 16 4. Problem Formulation - Assumptions (Defender) Assumptions 6. There a number of legitimate users sending traffic to multiple servers considered by the attacker. 7. The routing policy for the legitimate traffic will be decided by the AS. 8. The network administrator (defender) can allocate filters to routers to maximize the total legitimate traffic after filters have been allocated. 9. The cost to allocate a filter to a router is decided by the capability of the filter. 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

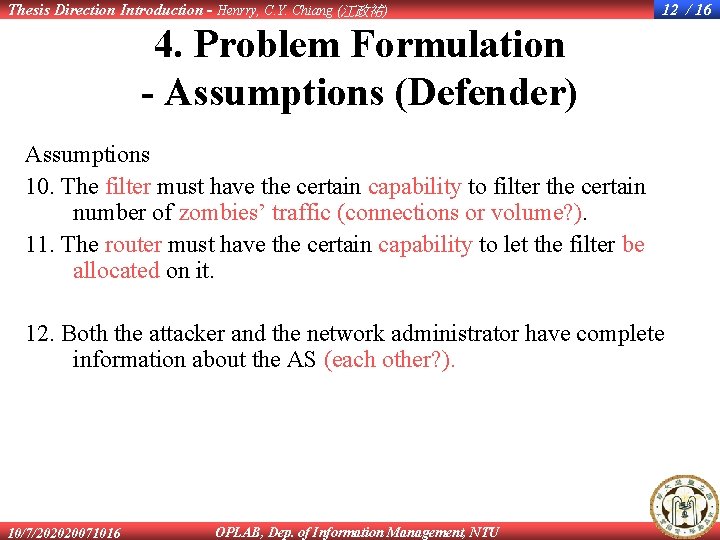
Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 12 / 16 4. Problem Formulation - Assumptions (Defender) Assumptions 10. The filter must have the certain capability to filter the certain number of zombies’ traffic (connections or volume? ). 11. The router must have the certain capability to let the filter be allocated on it. 12. Both the attacker and the network administrator have complete information about the AS (each other? ). 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

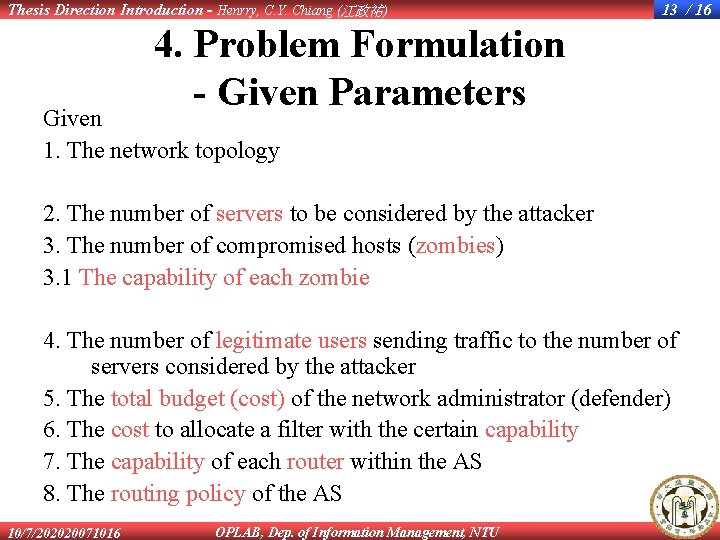
Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 13 / 16 4. Problem Formulation - Given Parameters Given 1. The network topology 2. The number of servers to be considered by the attacker 3. The number of compromised hosts (zombies) 3. 1 The capability of each zombie 4. The number of legitimate users sending traffic to the number of servers considered by the attacker 5. The total budget (cost) of the network administrator (defender) 6. The cost to allocate a filter with the certain capability 7. The capability of each router within the AS 8. The routing policy of the AS 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

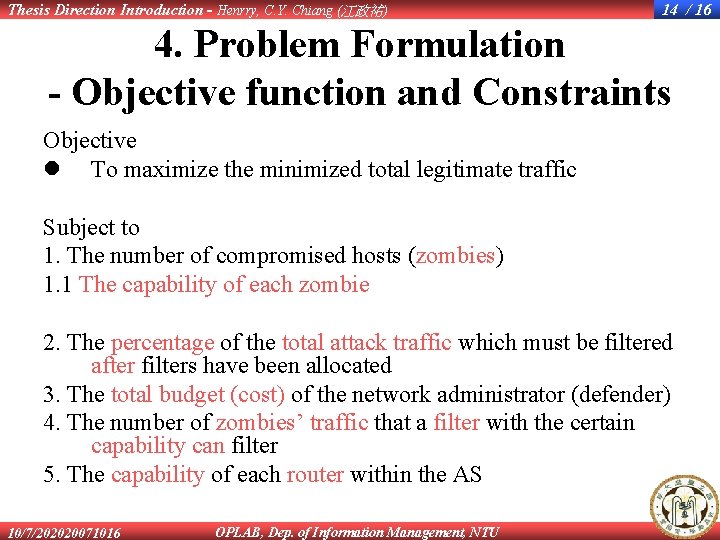
Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 14 / 16 4. Problem Formulation - Objective function and Constraints Objective l To maximize the minimized total legitimate traffic Subject to 1. The number of compromised hosts (zombies) 1. 1 The capability of each zombie 2. The percentage of the total attack traffic which must be filtered after filters have been allocated 3. The total budget (cost) of the network administrator (defender) 4. The number of zombies’ traffic that a filter with the certain capability can filter 5. The capability of each router within the AS 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 15 / 16 4. Problem Formulation - Decision Variables To determine l Defender: 1. The budget (filters) allocation strategy l Attacker: 1. The volume of the traffic that each compromised host (zombie) sends 2. The destination node that each compromised host (zombie) sends traffic to 3. The entry node that each compromised host (zombie) sends traffic to pass 10/7/202020071016 OPLAB, Dep. of Information Management, NTU

Thesis Direction Introduction - Henrry, C. Y. Chiang (江政祐) 16 / 16 The End - It’s my greatest honor to have your attention. 10/7/202020071016 OPLAB, Dep. of Information Management, NTU