There is nothing more important than our customers



- Slides: 18

“There is nothing more important than our customers” Jak zabezpečit sítě proti útokům zevnitř a přitom maximálně využít stávající infrastrukturu Michal Zlesák Area Sales Manager - Eastern EMEA michal. zlesak@enterasys. com

Securing the Network starts with the Questions to Ask… • Do you have a corporate IT security policy? • How do you enforce your security policy? • Can you identify a security breach occurring within the corporate infrastructure? • How long does it take to identify an internal security breach? • How long does it take to patch your entire environment on the discovery of a security breach? • Do you have mobile users that connect to the corporate infrastructure, but also connect to the Internet through non trusted and possibly non secure locations (home, coffee shop, etc. )? • Can your IT organization remove or quarantine anything on the network in a moment’s notice? • What would a complete system meltdown cost your organization? © 2006 Enterasys Networks, Inc. All rights reserved.

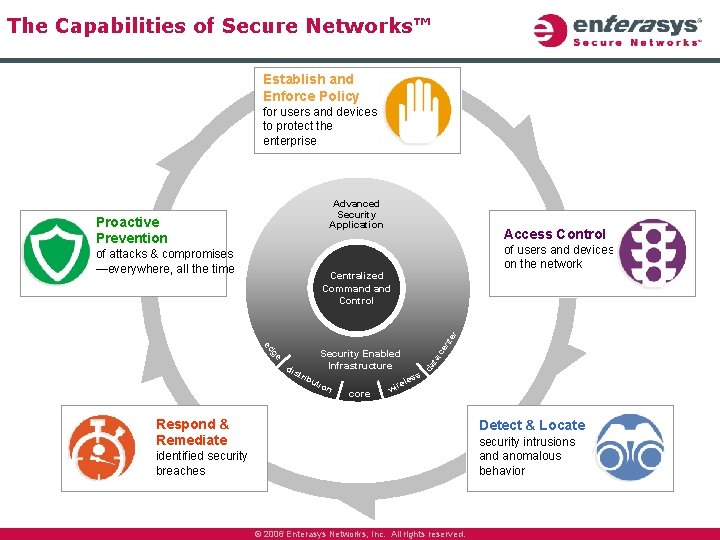
The Capabilities of Secure Networks™ Establish and Enforce Policy for users and devices to protect the enterprise Advanced Security Application Proactive Prevention of attacks & compromises —everywhere, all the time Access Control of users and devices on the network trib uti on ce ta Security Enabled Infrastructure ge dis s da ed nt er Centralized Command Control les core e wir Respond & Remediate Detect & Locate security intrusions and anomalous behavior identified security breaches © 2006 Enterasys Networks, Inc. All rights reserved.

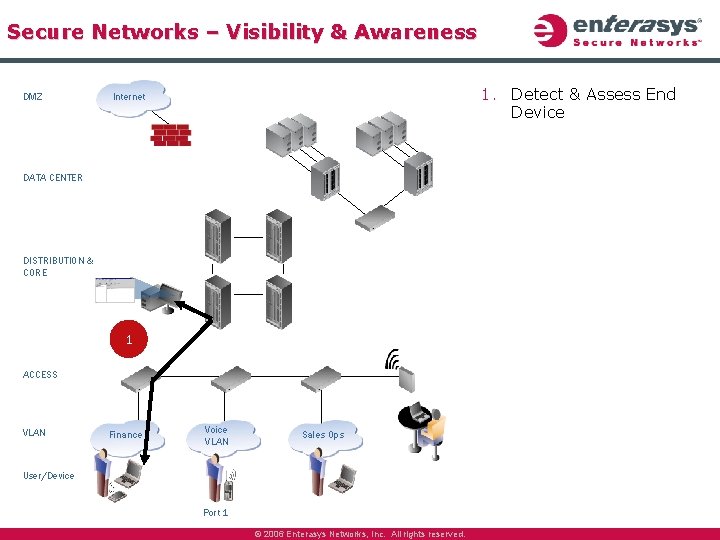
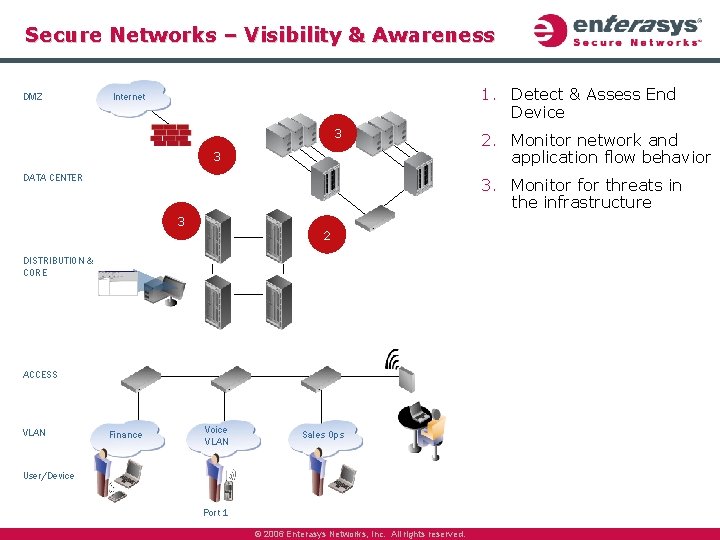
Secure Networks – Visibility & Awareness DMZ 1. Detect & Assess End Device Internet DATA CENTER DISTRIBUTION & CORE 1 ACCESS VLAN Finance Voice VLAN Sales Ops User/Device Port 1 © 2006 Enterasys Networks, Inc. All rights reserved.

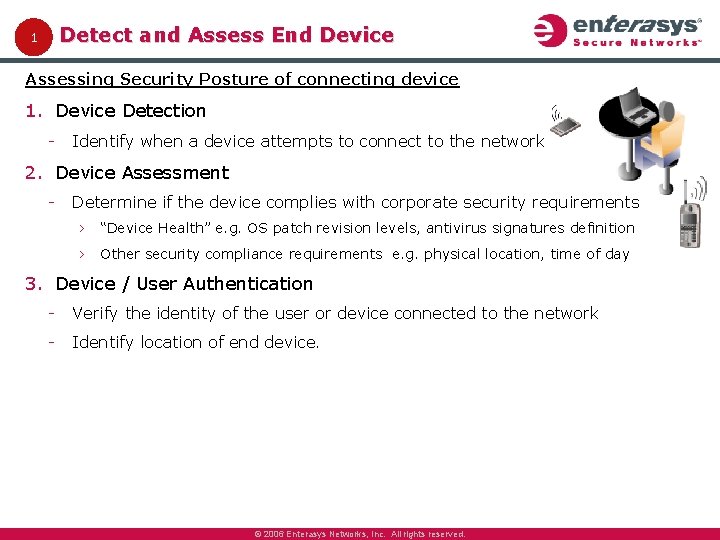
Detect and Assess End Device 1 Assessing Security Posture of connecting device 1. Device Detection Identify when a device attempts to connect to the network 2. Device Assessment Determine if the device complies with corporate security requirements › “Device Health” e. g. OS patch revision levels, antivirus signatures definition › Other security compliance requirements e. g. physical location, time of day 3. Device / User Authentication Verify the identity of the user or device connected to the network Identify location of end device. © 2006 Enterasys Networks, Inc. All rights reserved.

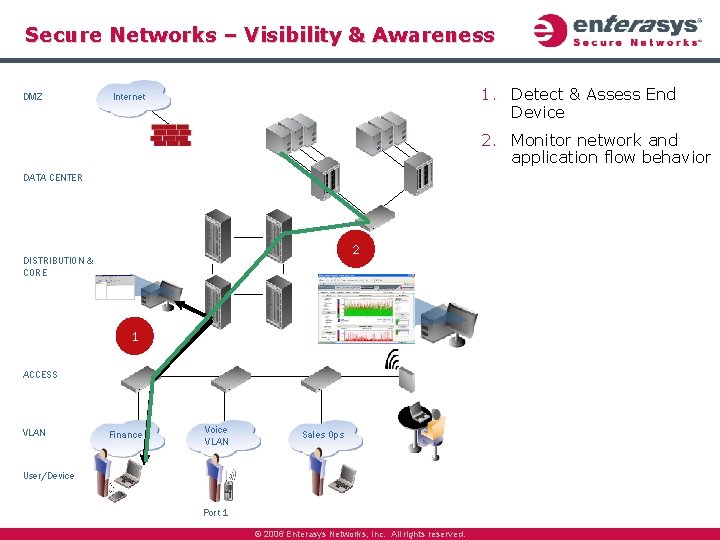
Secure Networks – Visibility & Awareness DMZ 1. Detect & Assess End Device Internet 2. Monitor network and application flow behavior DATA CENTER 2 DISTRIBUTION & CORE 1 ACCESS VLAN Finance Voice VLAN Sales Ops User/Device Port 1 © 2006 Enterasys Networks, Inc. All rights reserved.

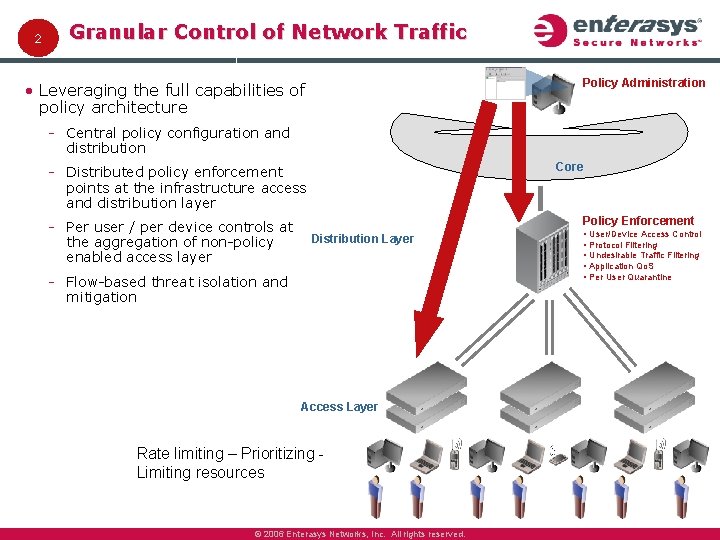
2 Granular Control of Network Traffic Policy Administration • Leveraging the full capabilities of policy architecture Central policy configuration and distribution Core Distributed policy enforcement points at the infrastructure access and distribution layer Per user / per device controls at the aggregation of non policy enabled access layer Policy Enforcement Distribution Layer Flow based threat isolation and mitigation Access Layer Rate limiting – Prioritizing Limiting resources © 2006 Enterasys Networks, Inc. All rights reserved. • User/Device Access Control • Protocol Filtering • Undesirable Traffic Filtering • Application Qo. S • Per User Quarantine

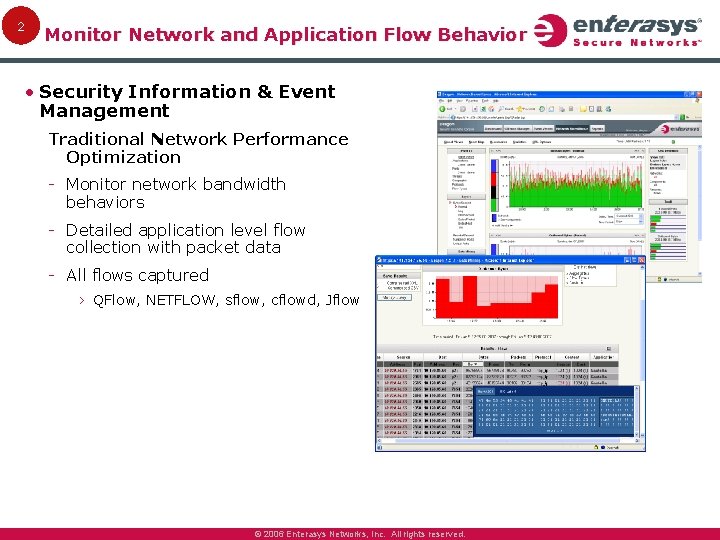
2 Monitor Network and Application Flow Behavior • Security Information & Event Management Traditional Network Performance Optimization Monitor network bandwidth behaviors Detailed application level flow collection with packet data All flows captured › QFlow, NETFLOW, sflow, cflowd, Jflow © 2006 Enterasys Networks, Inc. All rights reserved.

Secure Networks – Visibility & Awareness DMZ 1. Detect & Assess End Device Internet 3 3 DATA CENTER 3. Monitor for threats in the infrastructure 3 2 DISTRIBUTION & CORE ACCESS VLAN 2. Monitor network and application flow behavior Finance Voice VLAN Sales Ops User/Device Port 1 © 2006 Enterasys Networks, Inc. All rights reserved.

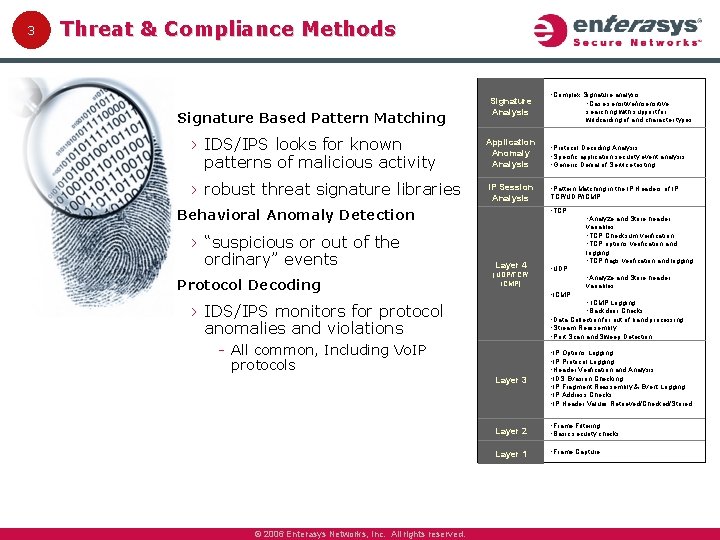
3 Threat & Compliance Methods Signature Based Pattern Matching Signature Analysis › IDS/IPS looks for known patterns of malicious activity Application Anomaly Analysis › robust threat signature libraries IP Session Analysis Behavioral Anomaly Detection › “suspicious or out of the ordinary” events Protocol Decoding searching with support for wildcarding of and character types • Protocol Decoding Analysis • Specific application security event analysis • Generic Denial of Service testing • Pattern Matching in the IP Headers of IP TCP/UDP/ICMP • TCP • Analyze and Store header Layer 4 (UDP/TCP/ ICMP) variables • TCP Checksum verification • TCP options verification and logging • TCP flags verification and logging • UDP • Analyze and Store header variables • ICMP Logging • Backdoor Checks › IDS/IPS monitors for protocol anomalies and violations • Data Collection for out of band processing • Stream Reassembly • Port Scan and Sweep Detection All common, Including Vo. IP protocols © 2006 Enterasys Networks, Inc. All rights reserved. • Complex Signature analysis • Case sensitive/insensitive Layer 3 • IP Options Logging • IP Protocol Logging • Header Verification and Analysis • IDS Evasion Checking • IP Fragment Reassembly & Event Logging • IP Address Checks • IP Header Values Retrieved/Checked/Stored Layer 2 • Frame Filtering • Basic security checks Layer 1 • Frame Capture

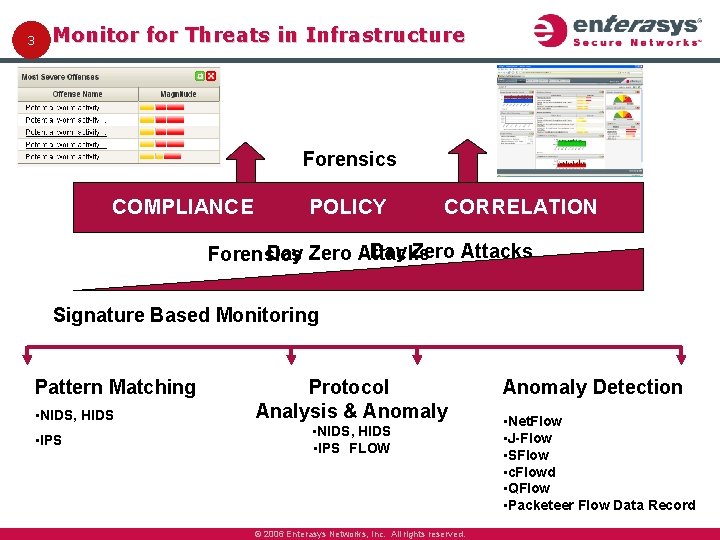
3 Monitor for Threats in Infrastructure Forensics COMPLIANCE POLICY CORRELATION Day Zero Attacks Forensics Signature Based Monitoring Pattern Matching • NIDS, HIDS • IPS Behavior Based Monitoring Protocol Analysis & Anomaly • NIDS, HIDS • IPS , FLOW © 2006 Enterasys Networks, Inc. All rights reserved. Anomaly Detection • Net. Flow • J-Flow • SFlow • c. Flowd • QFlow • Packeteer Flow Data Record

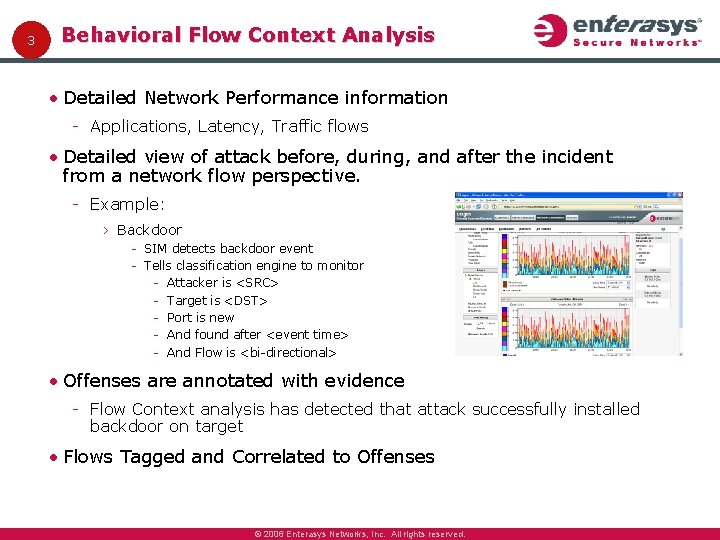
3 Behavioral Flow Context Analysis • Detailed Network Performance information Applications, Latency, Traffic flows • Detailed view of attack before, during, and after the incident from a network flow perspective. Example: › Backdoor SIM detects backdoor event Tells classification engine to monitor Attacker is <SRC> Target is <DST> Port is new And found after <event time> And Flow is <bi directional> • Offenses are annotated with evidence Flow Context analysis has detected that attack successfully installed backdoor on target • Flows Tagged and Correlated to Offenses © 2006 Enterasys Networks, Inc. All rights reserved.

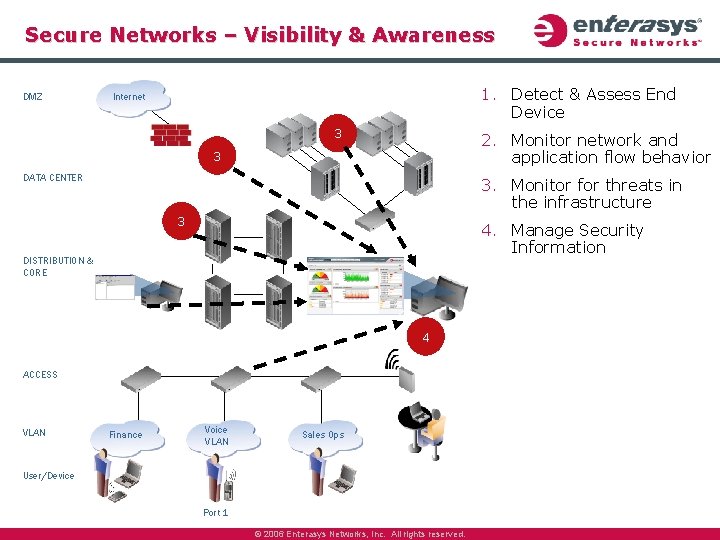
Secure Networks – Visibility & Awareness DMZ 1. Detect & Assess End Device Internet 3 2. Monitor network and application flow behavior 3 DATA CENTER 3. Monitor for threats in the infrastructure 3 4. Manage Security Information DISTRIBUTION & CORE 4 ACCESS VLAN Finance Voice VLAN Sales Ops User/Device Port 1 © 2006 Enterasys Networks, Inc. All rights reserved.

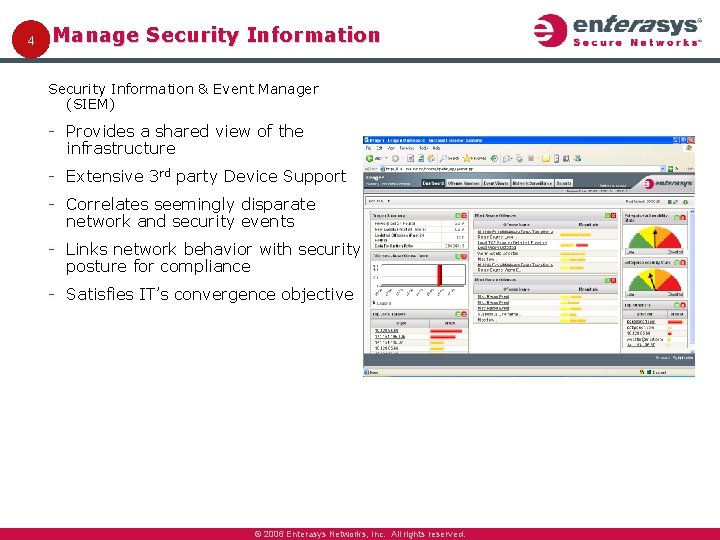
4 Manage Security Information & Event Manager (SIEM) Provides a shared view of the infrastructure Extensive 3 rd party Device Support Correlates seemingly disparate network and security events Links network behavior with security posture for compliance Satisfies IT’s convergence objective © 2006 Enterasys Networks, Inc. All rights reserved.

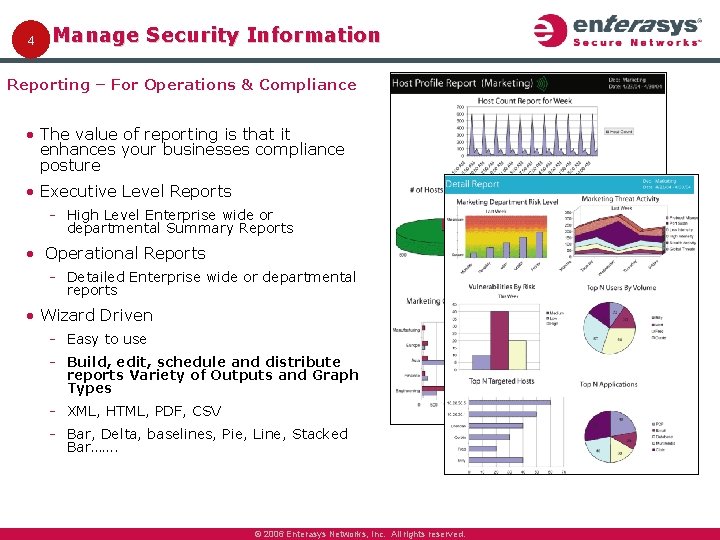
4 Manage Security Information Reporting – For Operations & Compliance • The value of reporting is that it enhances your businesses compliance posture • Executive Level Reports High Level Enterprise wide or departmental Summary Reports • Operational Reports Detailed Enterprise wide or departmental reports • Wizard Driven Easy to use Build, edit, schedule and distribute reports Variety of Outputs and Graph Types XML, HTML, PDF, CSV Bar, Delta, baselines, Pie, Line, Stacked Bar……. © 2006 Enterasys Networks, Inc. All rights reserved.

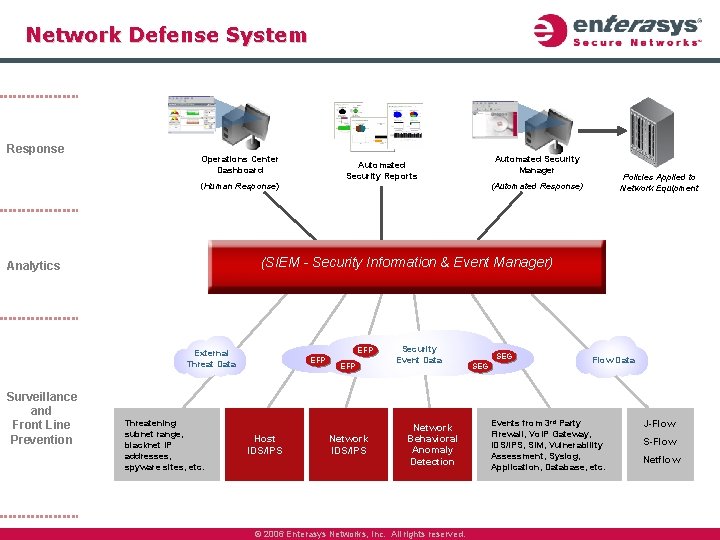
Network Defense System Response Operations Center Dashboard Automated Security Manager Automated Security Reports (Human Response) (SIEM - Security Information & Event Manager) Analytics EFP External Threat Data Surveillance and Front Line Prevention Policies Applied to Network Equipment (Automated Response) Threatening subnet range, blacknet IP addresses, spyware sites, etc. EFP Host IDS/IPS EFP Network IDS/IPS Security Event Data Network Behavioral Anomaly Detection © 2006 Enterasys Networks, Inc. All rights reserved. SEG Flow Data Events from 3 rd Party Firewall, Vo. IP Gateway, IDS/IPS, SIM, Vulnerability Assessment, Syslog, Application, Database, etc. J-Flow S-Flow Netflow

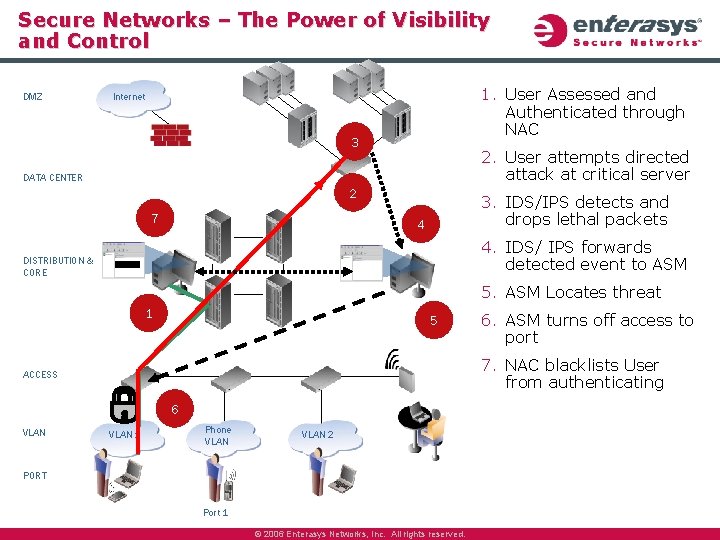
Secure Networks – The Power of Visibility and Control DMZ 1. User Assessed and Authenticated through NAC Internet 3 2. User attempts directed attack at critical server DATA CENTER 2 7 3. IDS/IPS detects and drops lethal packets 4 4. IDS/ IPS forwards detected event to ASM DISTRIBUTION & CORE 5. ASM Locates threat 1 5 7. NAC blacklists User from authenticating ACCESS 6 VLAN 6. ASM turns off access to port VLAN 1 Phone VLAN 2 PORT Port 1 © 2006 Enterasys Networks, Inc. All rights reserved.

“There is nothing more important than our customers” Thank You