THE US NATIONAL VIRTUAL OBSERVATORY Alternate security mechanisms

THE US NATIONAL VIRTUAL OBSERVATORY Alternate security mechanisms Matthew J. Graham (Caltech, NVO) IVOA Trieste: Grid & Web Services 22 May 2008 1

Security review • Users don’t care about protocols and standards – they care about better experience with enhanced privacy and security • User experience: – why is security necessary? – Certificates? . globus directories? WTF? • Developer experience: – Buzkashi • Community interests: – Decentralization IVOA Trieste: Grid & Web Services 22 May 2008 2
Open. ID • Single digital identity for use with any web site or service requiring authentication • Open, free and decentralized standard • Well supported • 120 million Open. IDs (July 2007) • Microsoft, Google, Yahoo (Jan 2008) IVOA Trieste: Grid & Web Services 22 May 2008 3

Open. ID: how it works • User registers an Open. ID identity (URI or XRI) with an Open. ID identity provider • Relying party (service provider) displays single input box for Open. ID identifier • Relying party converts Open. ID identifier to a canonical URL form and obtains identity service provider URL from there • Relying party and identity provider establish shared secret and then user is redirected to identity provider for authentication • User is redirected back to relying party along with credentials. Relying party validates that credentials originated from relying party using shared secret. IVOA Trieste: Grid & Web Services 22 May 2008 4

Open. ID: issues • NVO setting up prototype Open. ID identity provider service alongside current SSO setup: – use attribute to strengthen • Open. ID has little provision for web services (SOAP or RESTful): – requires communication between user and relying party and user and identity provider – checkid_immediate? – check_authentication? IVOA Trieste: Grid & Web Services 22 May 2008 5

OAuth • An API access delegation protocol • Well supported • User grants access to their protected resources to a consumer using tokens generated by a service provider instead of their credentials • Defines three endpoints: – Request token – User authentication - Access token IVOA Trieste: Grid & Web Services 22 May 2008 6
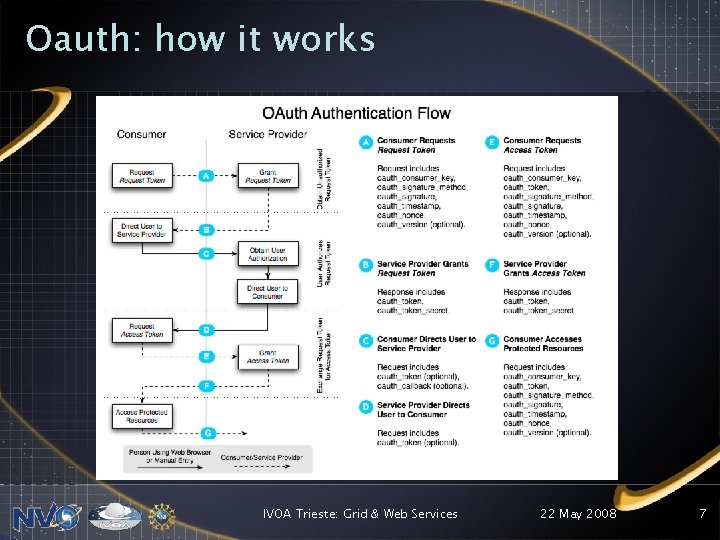
Oauth: how it works IVOA Trieste: Grid & Web Services 22 May 2008 7
OAuth • All done with HTTP GET/POST and headers • As with Open. ID, requires some level of user interaction: capture credentials or request approval IVOA Trieste: Grid & Web Services 22 May 2008 8

Summary • Industry embracing decentralised security mechanisms: – “web of trust” vs hierarchical model • Currently well-suited to web apps involving a browser but not to web services (no user) • What is the Grid community doing? – Shibboleth/Grid. Shib? IVOA Trieste: Grid & Web Services 22 May 2008 9
- Slides: 9