The Ultimate Web Service Client Code Security Client

The Ultimate Web Service Client Code Security & Client Deployment Slides for this event will be posted at: http: //www. microsoft. com/uk/msdn/postevents Stephen Turner Software Design Engineer Microsoft UK sturner@microsoft. com

Agenda Code access security Enabling mobile code scenarios Running under Full. Trust, Local. Intranet and Internet permission sets Managing security policy Client deployment Deployment background XCopy deployment Windows Installer deployment No-Touch deployment

Why do We Need Code Security? The enemy is among us – no perimeters Innocent but trusted code often plays host to malicious mobile code Malicious code can do anything that the user has permissions to do The user will always make the wrong security decision
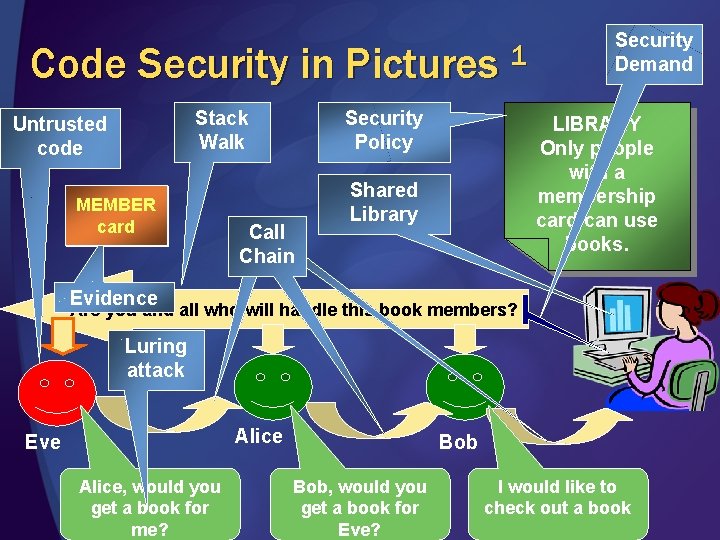
Code Security in Pictures 1 Stack Walk Untrusted code MEMBER card Security Policy Call Chain Security Demand LIBRARY Only people with a membership card can use books. Shared Library Evidence Are you and all who will handle this book members? Luring attack Alice Eve Alice, would you get a book for me? Bob, would you get a book for Eve? I would like to check out a book
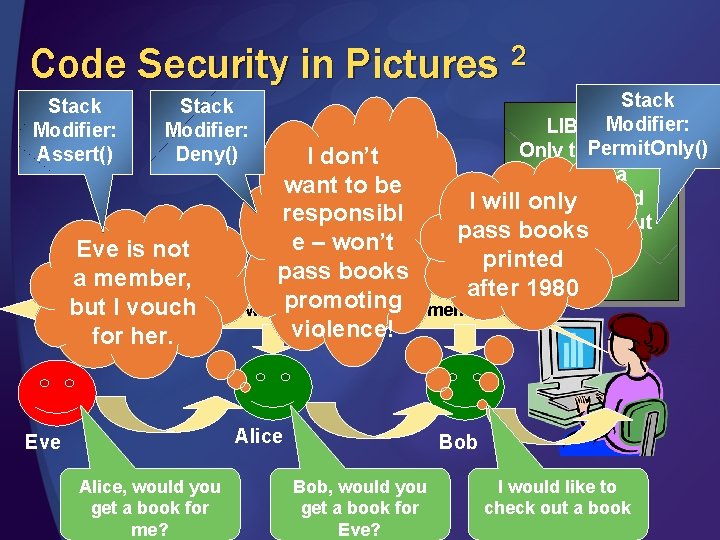
Code Security in Pictures 2 Stack Modifier: Assert() Stack Modifier: LIBRARY Permit. Only() Only those who have a I willmember only card can check out pass books a book. Stack Modifier: Deny() I don’t want to be responsibl e – won’t Eve is not printed pass books a member, after 1980 promoting but I vouch Are you and all who will handle this book members? violence! for her. Alice Eve Alice, would you get a book for me? Bob, would you get a book for Eve? I would like to check out a book

Code Access Security Client Apps Run Safely from the Internet Evidence of code origin and credentials Origin: IE zone, web site & URL Credentials: strong name signature, Authenticode Security Permissions Authorization to execute a protected operation Restricted access to a machine resource Security Policy Determines permissions based on evidence Easily maintained by administrator & policy No security decision is ever made by the user!

Code Access Security Granular Permissions Protect Resources File. IO File. Dialog Isolated. Storage Environment Registry UI Printing Reflection Security Socket Web Ole. Db SQLClient Message. Queue Event. Log Directory. Services … extensible Execution, Assertion, Skip verification, Unmanaged code, Control evidence, Control policy, Control principal, Control threads
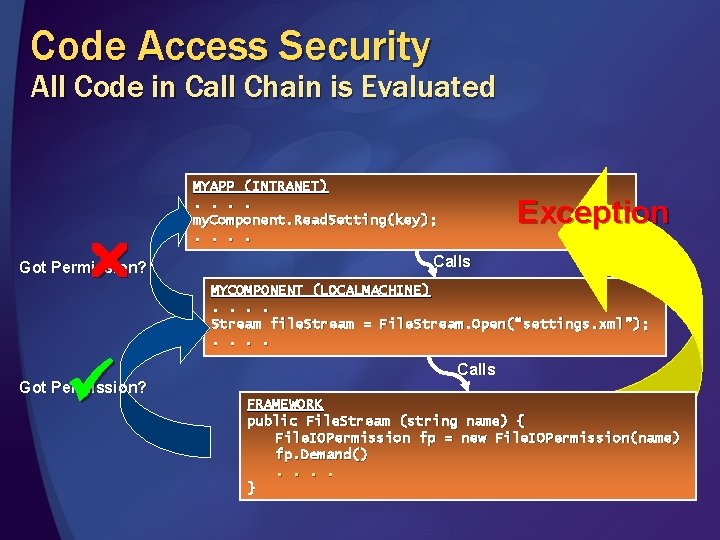
Code Access Security All Code in Call Chain is Evaluated Got Permission? MYAPP (INTRANET). . my. Component. Read. Setting(key); . . Exception Calls MYCOMPONENT (LOCALMACHINE). . Stream file. Stream = File. Stream. Open(“settings. xml”); . . Calls FRAMEWORK public File. Stream (string name) { File. IOPermission fp = new File. IOPermission(name) fp. Demand(). . }
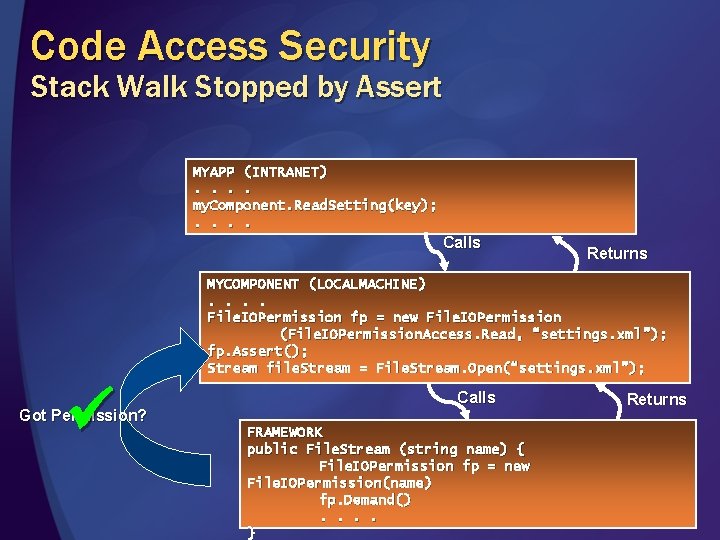
Code Access Security Stack Walk Stopped by Assert MYAPP (INTRANET). . my. Component. Read. Setting(key); . . Calls Returns MYCOMPONENT (LOCALMACHINE). . File. IOPermission fp = new File. IOPermission (File. IOPermission. Access. Read, “settings. xml”); fp. Assert(); Stream file. Stream = File. Stream. Open(“settings. xml”); Got Permission? Calls FRAMEWORK public File. Stream (string name) { File. IOPermission fp = new File. IOPermission(name) fp. Demand(). . } Returns

Code Access Security Running under Full. Trust, Local. Intranet and Internet security permission sets Windows Forms control within a browser page Managing security policy

Agenda Code access security Enabling mobile code scenarios Running under Full. Trust, Local. Intranet and Internet permission sets Managing security policy Client deployment Deployment background XCopy deployment Windows Installer deployment No-Touch deployment

Deployment Problems Installing client apps is fragile Will the install of app 1 break app 2? Traditional DLL hell problem Installing client apps is hard & expensive Must touch every client Both for 1 st time install & subsequent updates

V 1 of the. NET Framework Addressed #1 app safety issue, DLL Hell Application isolation Controlled versioning of shared components Did not address application install safety Began to address ease of deployment Run from URL / UNC exes Managed browser controls

XCopy Deployment Simple file-copy deployment XCOPY or otherwise Run off a share, CD, disk-on-key, etc. No setup required Good candidates XML Web services ASP. NET Web applications Small desktop applications Limitations Can’t create shortcuts links, Start menu icon, etc. Can’t configure users, groups, other security issues Can’t verify dependencies or run installation logic

Windows Installer Deployment Proven technology Best option for traditional deployment Extended to support needs of. NET Visual Studio. NET tools: Uses Windows Installer 2. 0 Setup and Deployment project templates

No-Touch Deployment Why not avoid installations altogether? Deploy. NET Windows apps over the Web Rich-client UI married to thin-client deployment Two options: Internet Explorer 5. 01+ Application loader Easily manage security Auto-update capability Byproduct of no-touch Updater mechanism for installed apps

No-Touch Deployment Using Internet Explorer User navigates to URL: <a href=“http: //myserver/myapp. exe”>Run my app!</a> IE 5. 01+ listens for requested assemblies Downloads to assembly download cache C: windowsassemblydownload Assigned IEExec process to launch app with restricted security settings Not required to run IE first If not already open, browser only appears momentarily

No-Touch Deployment Using Assembly. Load. From(url) Two scenarios Small desktop app on client URL-launched EXE needs greater access Dim app As [Assembly] = _ [Assembly]. Load. From("http: //CORPSVR/Foo/Bar. dll") Compile to DLL, not EXE Trickle-feed “On demand” or JIT-loaded assemblies Break up large application Must factor correctly
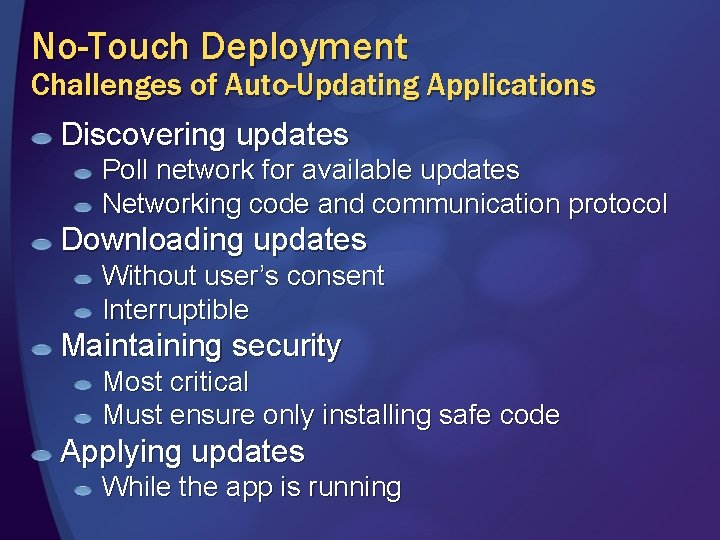
No-Touch Deployment Challenges of Auto-Updating Applications Discovering updates Poll network for available updates Networking code and communication protocol Downloading updates Without user’s consent Interruptible Maintaining security Most critical Must ensure only installing safe code Applying updates While the app is running

Updater Application Block (UAB) “Plug-and-play” components One of the Microsoft “Patterns and Practices” Or, build your own: Custom controllers Custom downloaders Custom validators Custom post-processors Fully documented and extensible http: //msdn. microsoft. com/library/default. asp? url=/library/en-us/dnbda/html/updater. asp
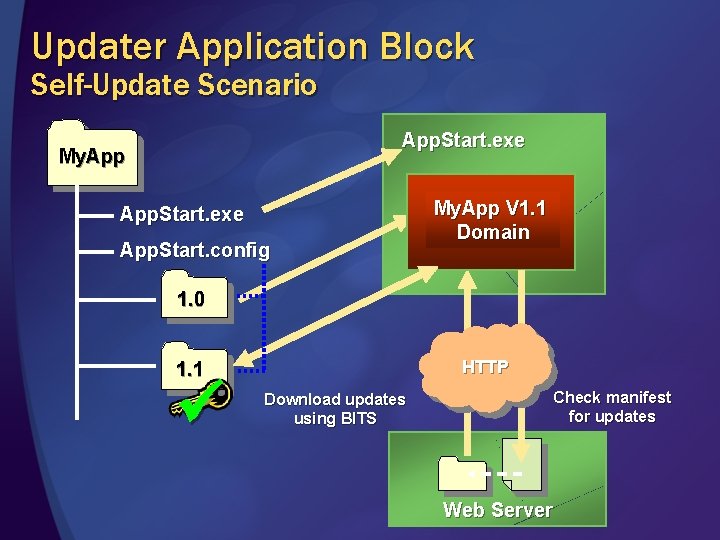
Updater Application Block Self-Update Scenario App. Start. exe My. App. Start. exe App. Start. config My. App. V 1. 1 V 1 Domain 1. 0 HTTP 1. 1 Download updates using BITS Check manifest for updates Web Server

Client Deployment Updater Application Block
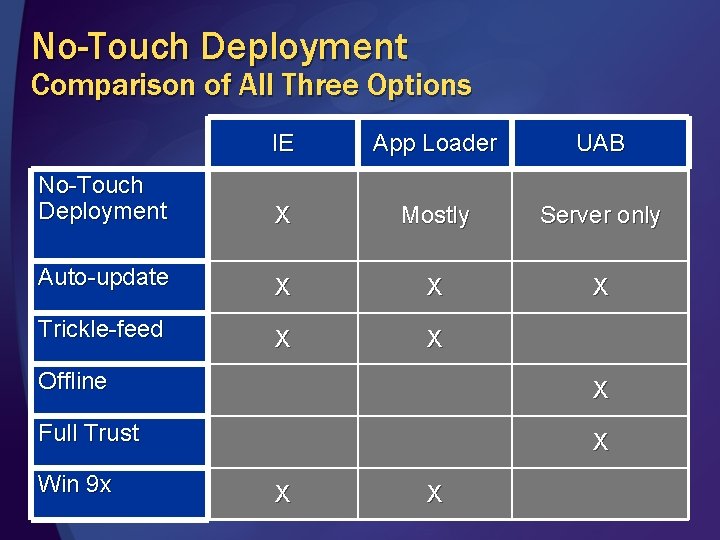
No-Touch Deployment Comparison of All Three Options IE App Loader UAB No-Touch Deployment X Mostly Server only Auto-update X X X Trickle-feed X X Offline X Full Trust X Win 9 x X X

Click. Once New with the. NET Framework 2. 0 Bring the ease & reliability of web application deployment to client applications.

Click. Once Development Experience Integrated VS Support Integrated to core project system Setup is not a post-development operation Publish Wizard Copies application to web server FTP, UNC, Front. Page Server Extensions

Client Deployment Building, deploying & updating a client application with Click. Once
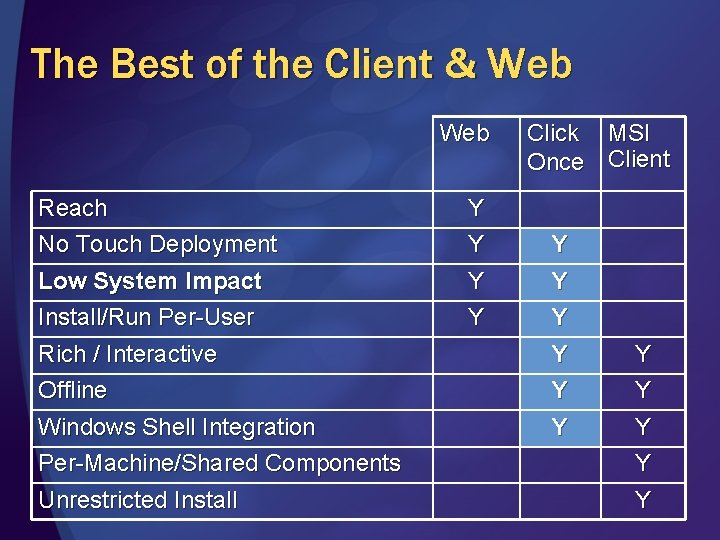
The Best of the Client & Web Reach No Touch Deployment Y Y Low System Impact Install/Run Per-User Y Y Rich / Interactive Offline Windows Shell Integration Per-Machine/Shared Components Unrestricted Install Click MSI Once Client Y Y Y
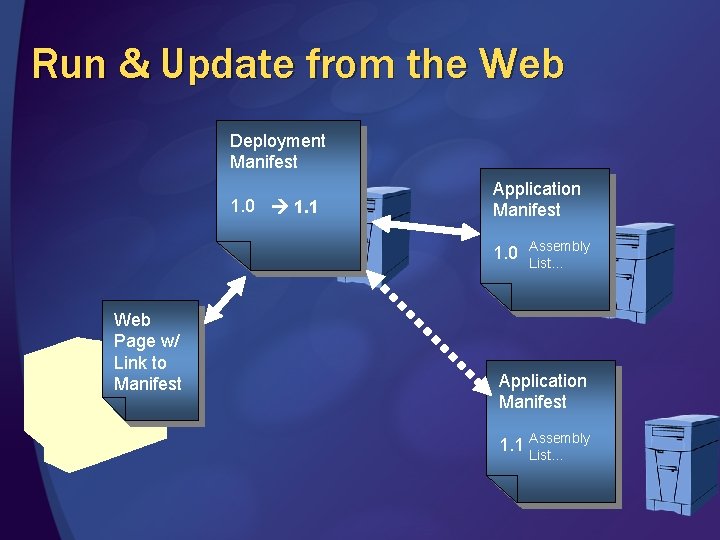
Run & Update from the Web Deployment Manifest 1. 0 1. 1 Application Manifest 1. 0 Web Page w/ Link to Manifest Assembly List… Application Manifest 1. 1 Assembly List…
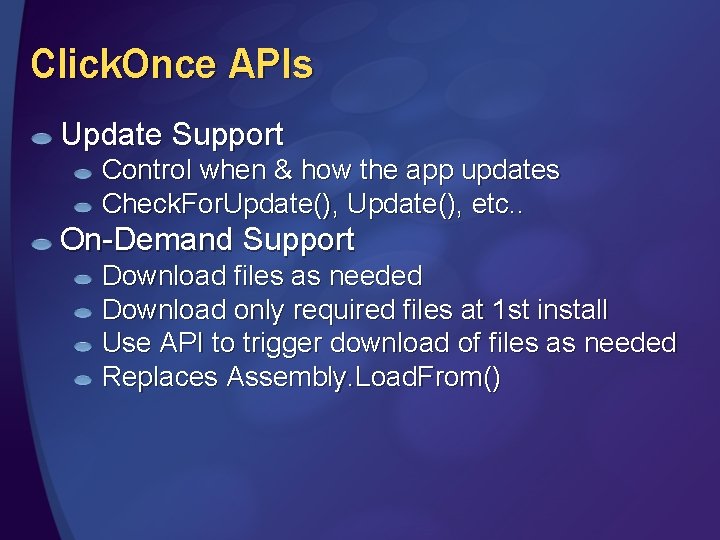
Click. Once APIs Update Support Control when & how the app updates Check. For. Update(), etc. . On-Demand Support Download files as needed Download only required files at 1 st install Use API to trigger download of files as needed Replaces Assembly. Load. From()

Call to action Code access security Client deployment Use Updater Application Block today Use Click. Once tomorrow

MSDN Connection Get personalised info & a customised RSS feed The programming language(s) you’re interested in The technology area(s) you’re interested in The information you want View news, technical resources, events, webcasts and community information Sign up for MSDN Connection at: http: //www. microsoft. com/uk/msdn

Additional Information Post Events Site All information on past events, slide decks etc http: //www. microsoft. com/uk/msdn/postevents The UK MSDN Site & Flash Local news, events, webcasts http: //www. microsoft. com/uk/msdn Register to received the bi-weekly MSDN Flash by email http: //www. microsoft. com/uk/msdn/flash. aspx Try Visual Studio http: //www. microsoft. com/vstudio/tryit Take a look at the Express products http: //msdn. microsoft. com/express Got. Dot. Net and ASP. NET – lots of excellent resources http: //www. gotdotnet. com

Useful Resources on the Internet Web sites http: //msdn. microsoft. com/security http: //msdn. microsoft. com/smartclient http: //windowsforms. net Newsgroups http: //msdn. microsoft. com/newsgroups news: //microsoft. public. dotnet. framework. windowsforms

Books on. NET Security. NET Framework Security La. Macchia et al. , Addison-Wesley ISBN 0 -672 -32184 -X Bible for both administrators and developers Visual Basic Code Security Handbook Eric Lippert, Wrox Press ISBN 1 -86100 -747 -7 Practical guide for developers with lots of code examples Chapters on best practice and worst practice

© 2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.

- Slides: 36