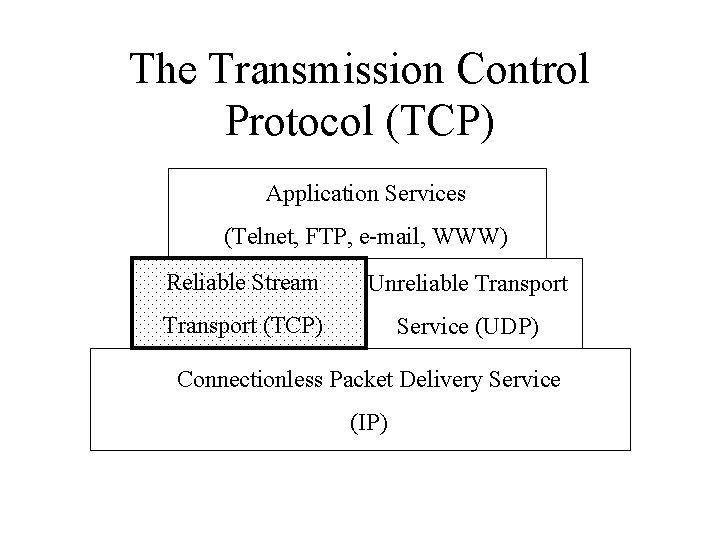
The Transmission Control Protocol TCP Application Services Telnet







- Slides: 30

The Transmission Control Protocol (TCP) Application Services (Telnet, FTP, e-mail, WWW) Reliable Stream Unreliable Transport (TCP) Service (UDP) Connectionless Packet Delivery Service (IP)

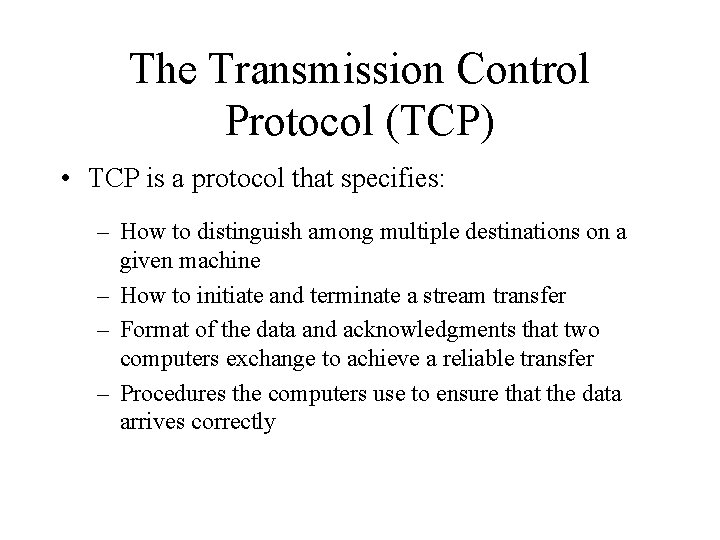
The Transmission Control Protocol (TCP) • TCP is a protocol that specifies: – How to distinguish among multiple destinations on a given machine – How to initiate and terminate a stream transfer – Format of the data and acknowledgments that two computers exchange to achieve a reliable transfer – Procedures the computers use to ensure that the data arrives correctly

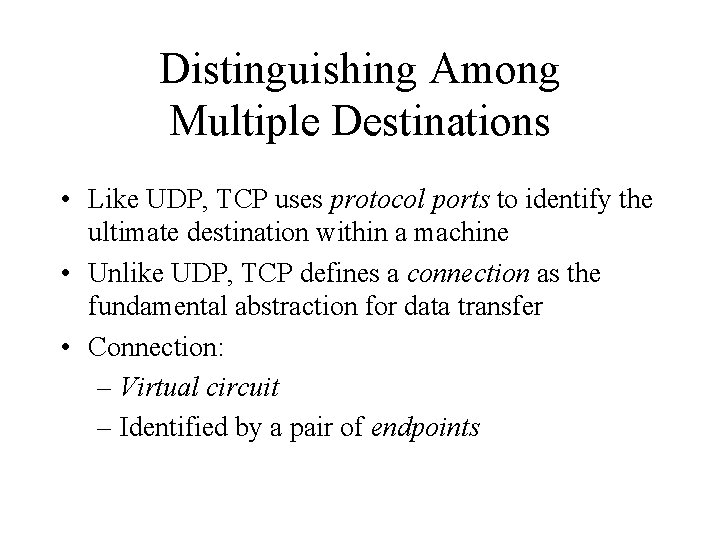
Distinguishing Among Multiple Destinations • Like UDP, TCP uses protocol ports to identify the ultimate destination within a machine • Unlike UDP, TCP defines a connection as the fundamental abstraction for data transfer • Connection: – Virtual circuit – Identified by a pair of endpoints

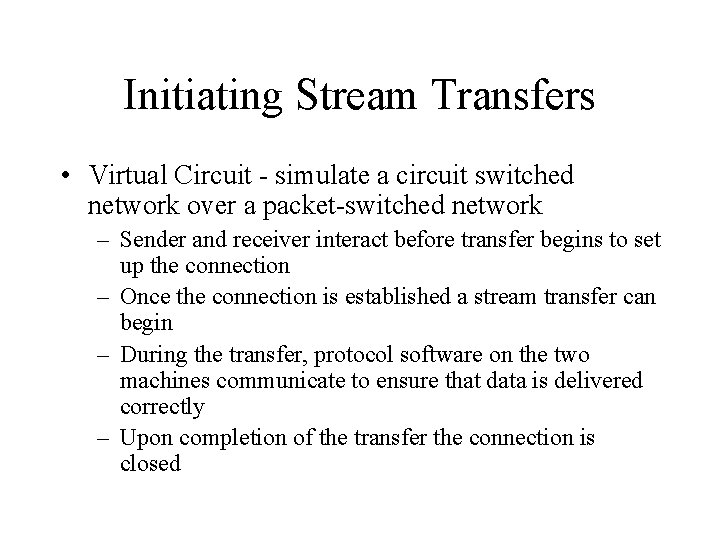
Initiating Stream Transfers • Virtual Circuit - simulate a circuit switched network over a packet-switched network – Sender and receiver interact before transfer begins to set up the connection – Once the connection is established a stream transfer can begin – During the transfer, protocol software on the two machines communicate to ensure that data is delivered correctly – Upon completion of the transfer the connection is closed

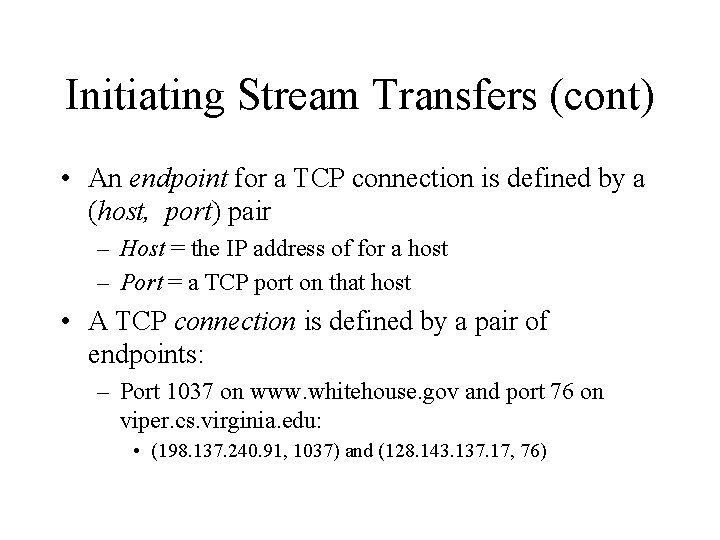
Initiating Stream Transfers (cont) • An endpoint for a TCP connection is defined by a (host, port) pair – Host = the IP address of for a host – Port = a TCP port on that host • A TCP connection is defined by a pair of endpoints: – Port 1037 on www. whitehouse. gov and port 76 on viper. cs. virginia. edu: • (198. 137. 240. 91, 1037) and (128. 143. 137. 17, 76)

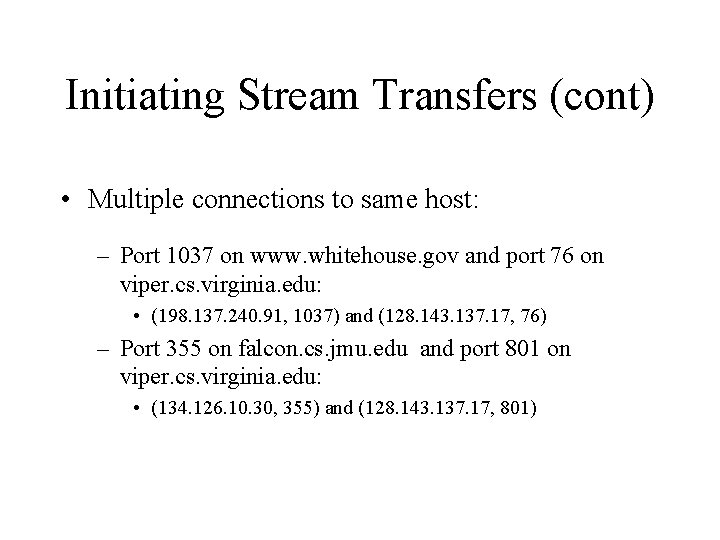
Initiating Stream Transfers (cont) • Multiple connections to same host: – Port 1037 on www. whitehouse. gov and port 76 on viper. cs. virginia. edu: • (198. 137. 240. 91, 1037) and (128. 143. 137. 17, 76) – Port 355 on falcon. cs. jmu. edu and port 801 on viper. cs. virginia. edu: • (134. 126. 10. 30, 355) and (128. 143. 137. 17, 801)

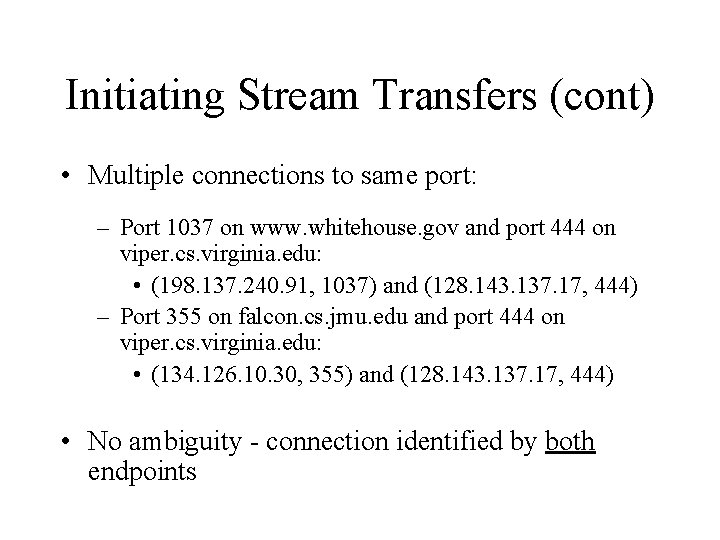
Initiating Stream Transfers (cont) • Multiple connections to same port: – Port 1037 on www. whitehouse. gov and port 444 on viper. cs. virginia. edu: • (198. 137. 240. 91, 1037) and (128. 143. 137. 17, 444) – Port 355 on falcon. cs. jmu. edu and port 444 on viper. cs. virginia. edu: • (134. 126. 10. 30, 355) and (128. 143. 137. 17, 444) • No ambiguity - connection identified by both endpoints

Initiating Stream Transfers (cont) • Both endpoints must agree to participate: – Passive open - one application program contacts its O. S. and indicates that it will accept an incoming connection – Active open - application program at other end contacts its O. S. and requests a connection • Both TCP software modules cooperate to establish a connection • Application programs can transmit data (TCP provides reliability)

TCP Data Stream Format • Data from application programs is a sequence of octets (with no type associated) • TCP divides data into segments for transmission • Usually, each segment travels across the internet in a single IP datagram

Review: Unreliable Packet Delivery Service • Benefits: – Fast – Cost-effective • Drawbacks: – Packet loss, corruption, delay, duplication, out-of-order delivery – Sender might transmit faster than receiver can receive – Dictates a set packet size

The Need for a Reliable Stream Delivery Service • Application-level programmers don’t want: – To have to provide reliability in each application – To be constrained by fixed-size packets • Application-level programmers do want: – – Reliability Unstructured, stream-oriented service Full duplex virtual circuit connection Buffered transfer

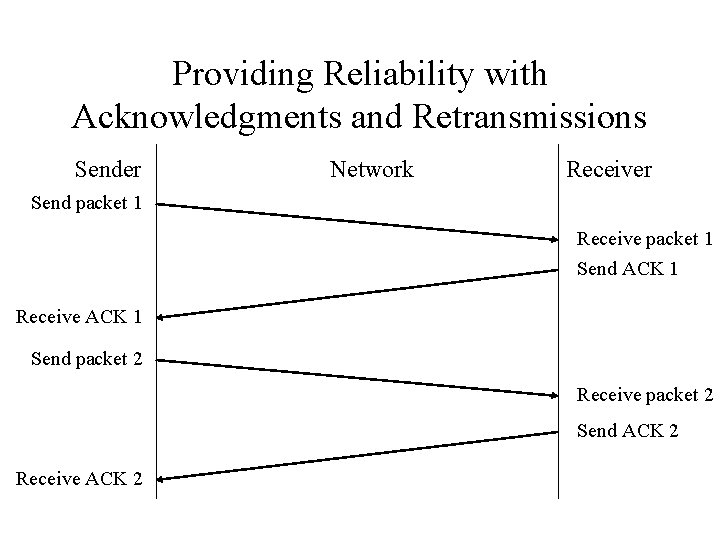
Providing Reliability with Acknowledgments and Retransmissions Sender Network Receiver Send packet 1 Receive packet 1 Send ACK 1 Receive ACK 1 Send packet 2 Receive packet 2 Send ACK 2 Receive ACK 2

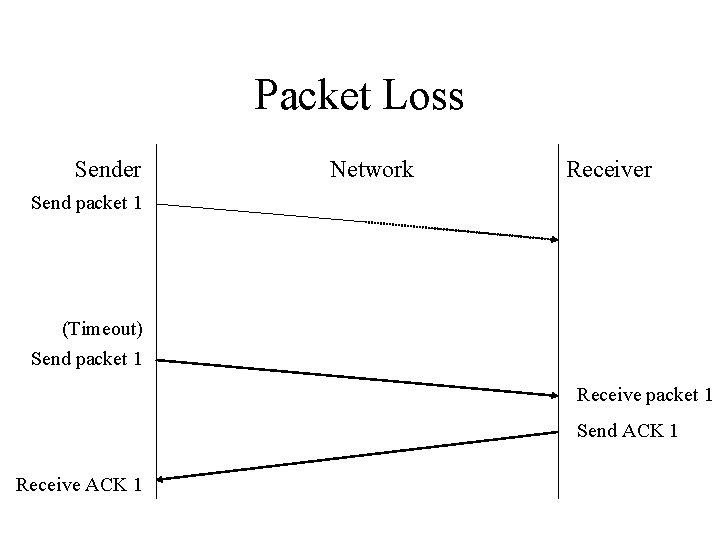
Packet Loss Sender Network Receiver Send packet 1 (Timeout) Send packet 1 Receive packet 1 Send ACK 1 Receive ACK 1

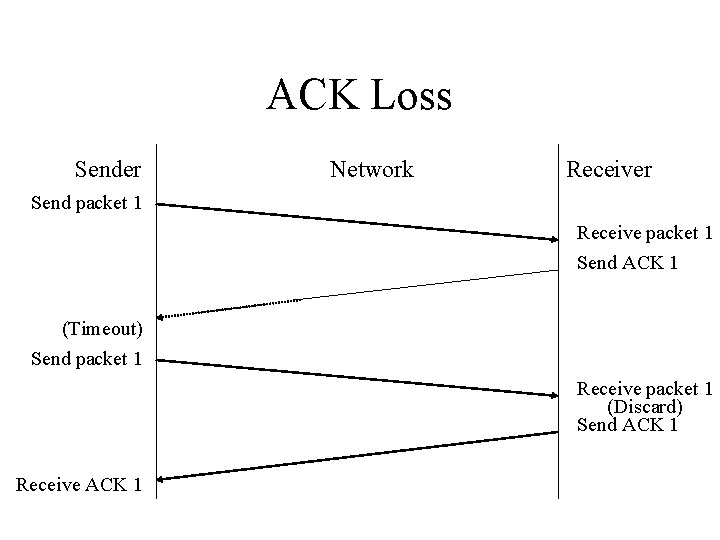
ACK Loss Sender Network Receiver Send packet 1 Receive packet 1 Send ACK 1 (Timeout) Send packet 1 Receive packet 1 (Discard) Send ACK 1 Receive ACK 1

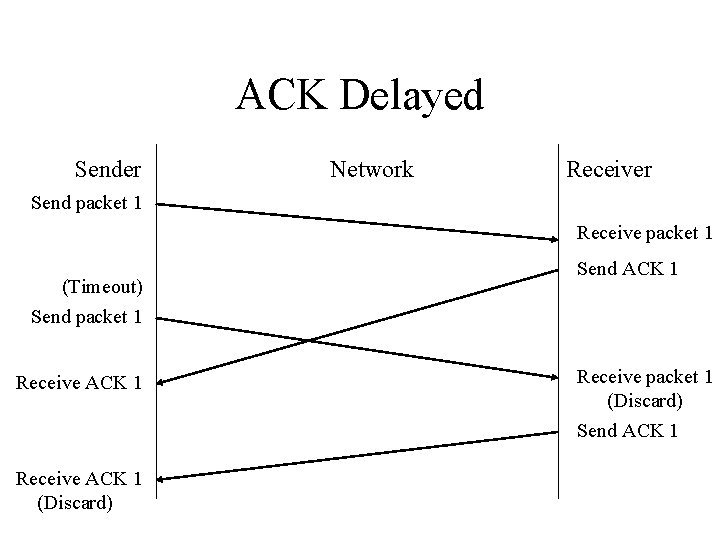
ACK Delayed Sender Network Receiver Send packet 1 Receive packet 1 (Timeout) Send packet 1 Receive ACK 1 (Discard) Send ACK 1 Receive packet 1 (Discard) Send ACK 1

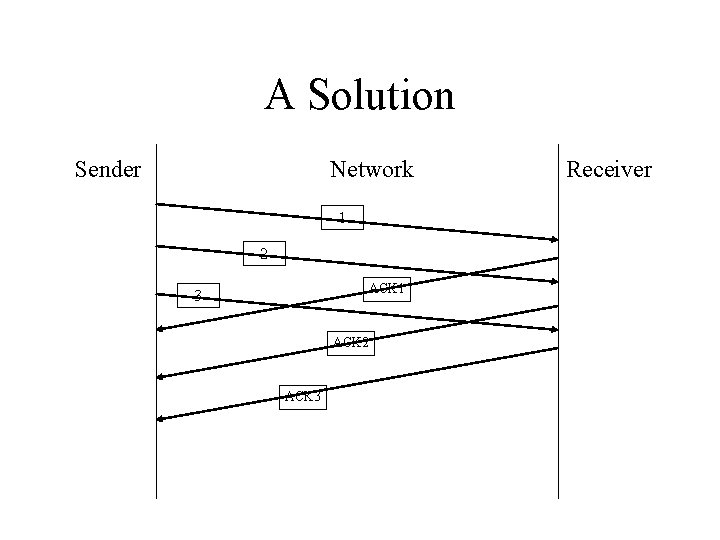
A Problem A simple positive acknowledgment protocol wastes a substantial amount of network bandwidth because it must delay sending a new packet until it receives an acknowledgment for the previous packet.

A Solution Sender Network 1 2 ACK 1 3 ACK 2 ACK 3 Receiver

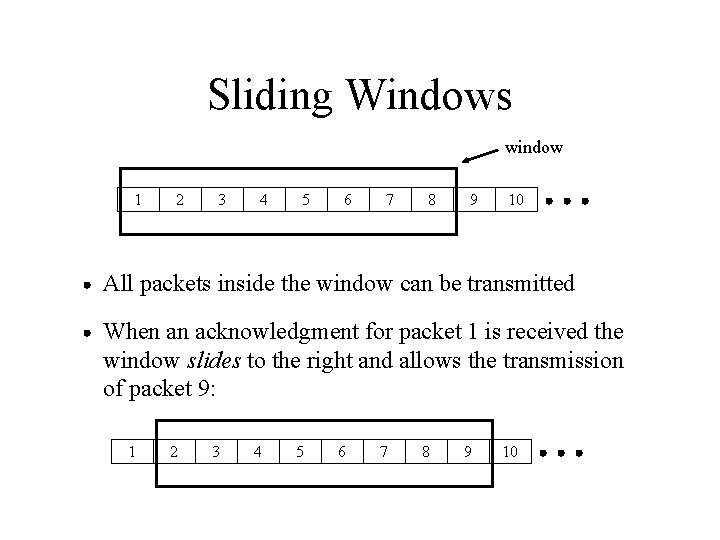
Sliding Windows window 1 2 3 4 5 6 7 8 9 10 All packets inside the window can be transmitted When an acknowledgment for packet 1 is received the window slides to the right and allows the transmission of packet 9: 1 2 3 4 5 6 7 8 9 10

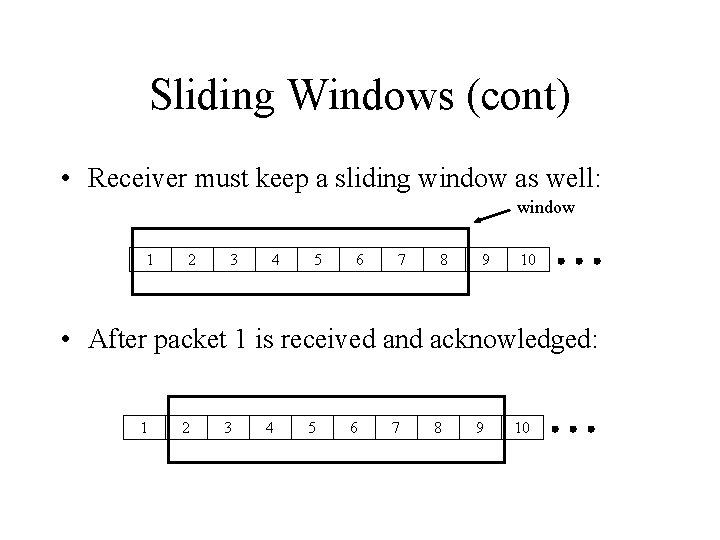
Sliding Windows (cont) • Receiver must keep a sliding window as well: window 1 2 3 4 5 6 7 8 9 10 • After packet 1 is received and acknowledged: 1 2 3 4 5 6 7 8 9 10

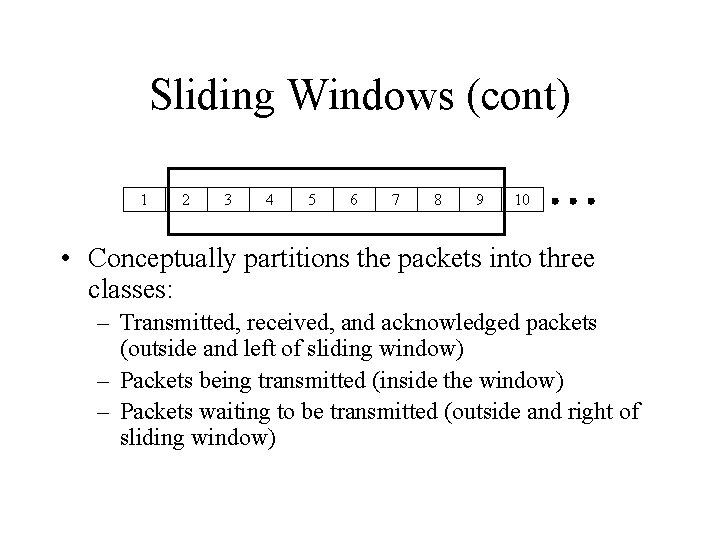
Sliding Windows (cont) 1 2 3 4 5 6 7 8 9 10 • Conceptually partitions the packets into three classes: – Transmitted, received, and acknowledged packets (outside and left of sliding window) – Packets being transmitted (inside the window) – Packets waiting to be transmitted (outside and right of sliding window)

Sliding Windows (cont) • Only unacknowledged packets are retransmitted – Keep separate timer for each packet • Performance: – Depends on the window size and the speed of the underlying network – Note: sliding window protocol with window size = 1 is the same as the simple positive acknowledgment protocol we saw earlier

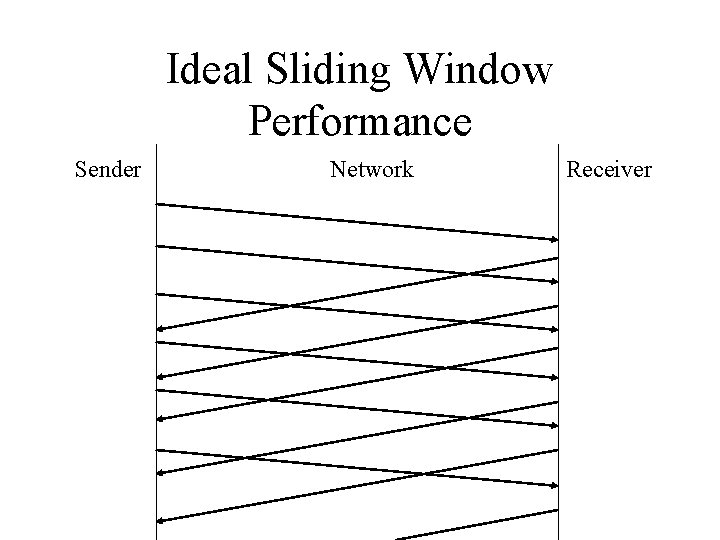
Sliding Windows: Performance • Tuning the sliding window protocol – Increase window size so that sender is transmitting packets as fast as the network can carry them – Eliminates network idle time – Increases throughput (as compared to the simple positive acknowledgment protocol)

Ideal Sliding Window Performance Sender Network Receiver

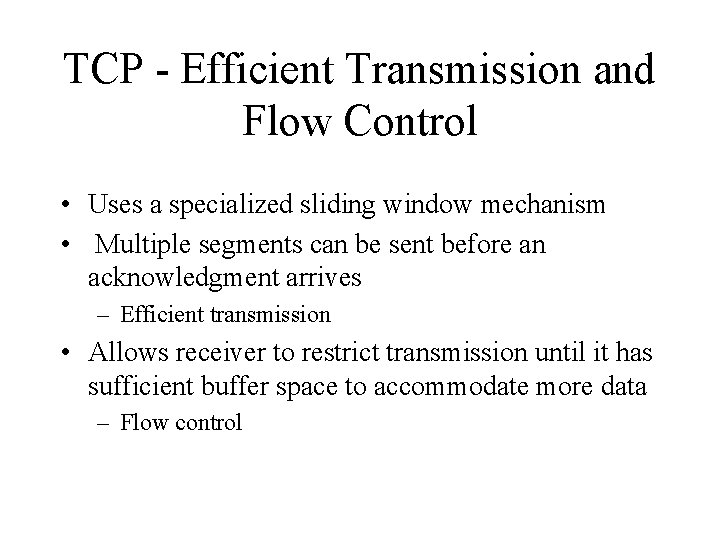
TCP - Efficient Transmission and Flow Control • Uses a specialized sliding window mechanism • Multiple segments can be sent before an acknowledgment arrives – Efficient transmission • Allows receiver to restrict transmission until it has sufficient buffer space to accommodate more data – Flow control

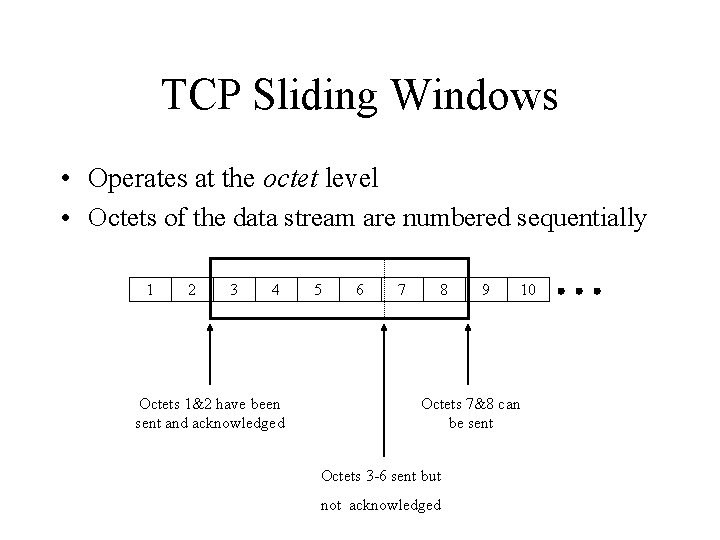
TCP Sliding Windows • Operates at the octet level • Octets of the data stream are numbered sequentially 1 2 3 4 Octets 1&2 have been sent and acknowledged 5 6 7 8 9 10 Octets 7&8 can be sent Octets 3 -6 sent but not acknowledged

TCP Sliding Windows • Four per (full duplex) connection: – A sends to B – A receives from B – B sends to A – B receives from A

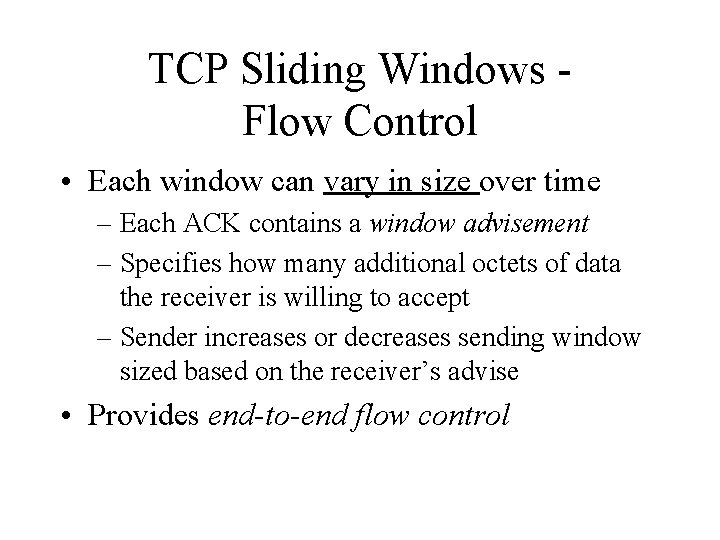
TCP Sliding Windows Flow Control • Each window can vary in size over time – Each ACK contains a window advisement – Specifies how many additional octets of data the receiver is willing to accept – Sender increases or decreases sending window sized based on the receiver’s advise • Provides end-to-end flow control

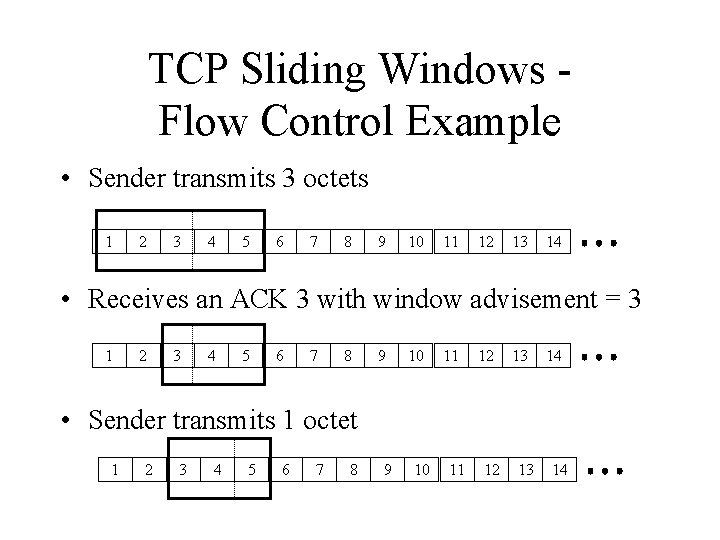
TCP Sliding Windows Flow Control Example • Sender transmits 3 octets 1 2 3 4 5 6 7 8 9 10 11 12 13 14 • Receives an ACK 3 with window advisement = 3 1 2 3 4 5 6 7 8 9 10 11 12 13 14 • Sender transmits 1 octet 1 2 3 4 5 6 7 8 9 10 11 12 13 14

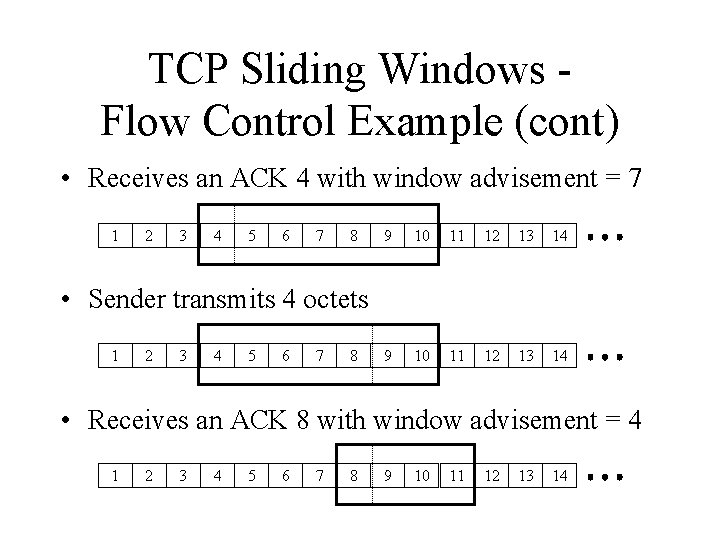
TCP Sliding Windows Flow Control Example (cont) • Receives an ACK 4 with window advisement = 7 1 2 3 4 5 6 7 8 9 10 11 12 13 14 • Sender transmits 4 octets 1 2 3 4 5 6 7 8 • Receives an ACK 8 with window advisement = 4 1 2 3 4 5 6 7 8 9 10 11 12 13 14

Summary • TCP is a transport protocol that specifies: – How to distinguish among multiple destinations on a given machine – How to initiate and terminate a stream transfer – Format of the data and acknowledgments that two computers exchange to achieve a reliable transfer – Procedures the computers use to ensure that the data arrives correctly