The Social Context of Computing The Social Context






















































- Slides: 59

The Social Context of Computing

The Social Context of Computing What is it? • Appropriate vs. Inappropriate – Proper Credit vs. Plagiarism • Codes of ethics for computer users and professionals, ex. ACM Code of Ethics • Protection of Privacy and Civil Liberties

Group 1 – Topics • Introduction to the Social Implications of • • • Computing Social Implications of Networked Communication Growth of, Control of and Access to the Internet Gender related Issues of Computing International Issues Computer Crime Prevention

Introduction to the Social Implications of Computing By Ryan Andrew

Historical Perspective • ACM Code of Ethics and Professional Conduct – Adopted in 1973 from work dating to the 1940’s • General Moral Imperatives, Professional Responsibilities, Organizational Leadership Imperatives, Compliance with the Code • “As an ACM member I will contribute to society and human well-being” - First Code

• IFIP’s Technical Committee 9 (TC 9) – Established in 1976 – Relationships between Computers and Society • Not technical issues – 8 Working Groups added since then • Computers and Work (est. 1977) • Social Accountability (est. 1977) • Home-Oriented Informatics and Telematics (est. 1988) • Social Implications of Computers in Developing Countries (est. • • 1989) Applications and Social Implications of Virtual Worlds (est. 1989) Information Technology Mis-Use and the Law (est. 1990) History of Computing (est. 1992) Women and Information Technology (est. 2001)

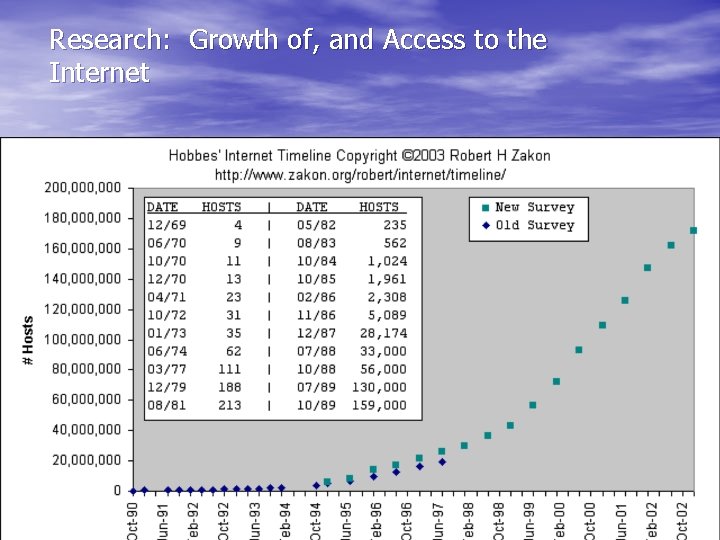
Research: Growth of, and Access to the Internet

Research: Growth of, and Access to the Internet • Issues with Internet Access – Low-Bandwidth and Low-Connectivity – Stats • In 1998, the country of Ethiopia had a 256 Kbps connection to the rest of the Internet. • In 2000, India had a total international bandwidth of 350 Mbps for 1 billion people. • Eight Arab countries (Egypt, Saudi Arabia, Lebanon, Jordan, Morocco, Oman, Syria, and the UAE) have, combined, the same bandwidth as 518 cable modem subscribers in the U. S.

Research: Growth of, and Access to the Internet • Issues with Internet Access – ISP Charges • For example, “one ISP in Ghana is faced with the fact that Internet bandwidth that would cost less than $1, 000 in the US must be beamed to Ghana through a satellite link to Canada, at about $40, 000 a month. ” • Often economically unfeasible

Research: Growth of, and Access to the Internet • Issues with Internet Access - Solutions – TEK Search Engine – Characteristics - can be generally applied • Low-connectivity, in that it does not rely on end-to-end connection at any point in time. • Low-bandwidth, in that it maximizes ‘information density’ and only sends attachments that can be downloaded over slow connections. • User friendly, in that it does not overwhelm users from information-poor environments with more results than they can manage. • Similar to standard search engine tools, so that the skills the user acquires can be transferred to other Web tools in the future.

Research: Computer Crime and Prevention • Many crimes through Internet – Plagiarism, peer-to-peer sharing, etc. – Focus on child exploitation…pedophiles • “Most pedophiles are attracted to the fact that there are many dark corners of the Internet that are not being regulated. ” • Easy for a pedophile to exploit an innocent child without even having to leave his or her home. • Free programs exist that allow potential pedophiles to surf the Internet or use e-mail anonymously. – Prevention - Protection of Children From Sexual Predators Act of 1998, U. S.

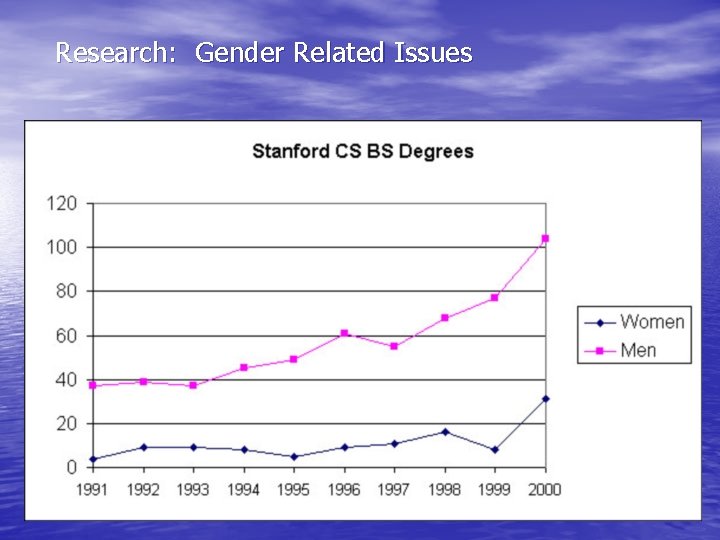
Research: Gender Related Issues • Growing concern of a gender divide – The following based on British population • It is recognized that males dominate the use of technologies in all areas of society. • Fewer girls are taking up Computing at an advanced level, and universities are experiencing a continued lack of interest in applications by women to computing degrees. • In 1996, 19% of computer science students we were reported to be female. • Today, only 21% of computing graduates in the UK are women. – Barely an increase

Research: Gender Related Issues

Conclusion – Implications of computing clear to see • Both the good and bad • These instances give a broader view of the need to recognize these negative implications – During development before they occur – Currently existing as well to derive possible solutions • ACM and IFIP – Aid in both prevention and solution to reduce the negative implications of computing • Realize there will always be negatives to a positive thing

Social Implications of Networked Communications By Matthew Chedister

Impacts of the Internet • Networked Communications, more specifically the Internet, has effected society in many ways – Methods of Communication – Amassment of media – The emergence of virtual communities – Leads to new social responsibilities

How the Internet Affects Methods of Communications • Applications that increase communications and decrease the impact of geographic barriers – Bulletin Board programs such as USENET – Instant Messaging Programs such as MSN Instant Messenger and IRC – Most common, e-mail

How the Internet Affects Methods of Communications • Many of these applications are replacing their non-computer related counterparts – E-mail is faster than the Postal Service – IRC doesn’t require the telephone – USENET doesn’t require a physical bulletin board, or thumbtacks.

Impact of Increased Communications • People within a society and between societies can now communicate in ways that were impossible before • Has made communication easier • Varied and easier forms of communication can have massive affects on society

How the Internet has Affected Amassment of Media • Many encyclopedias, dictionaries, and similar resources available online • Movie clips and song clips have become commonplace on the Internet • Significant impact on the 1996 Presidential Election

1996 US Presidential Election • Privately run Web. Pages and media-based Web. Pages collected documents from journalists, pollsters, politicians – Politics. Now • Networked Communications allowed the • candidates better and more immediate access to their campaign teams First time ever candidacy was declared online before publicly

Advent of Virtual Communities • Two definitions – Physically based virtual communities • Actual community augmented by electric resources such as online libraries, town meetings, etc. – Shared interest virtual communities • Community members have similar interests, can span continents, gender, creed

Impact of Virtual Communities • Physically based virtual communities can help bring local people together – Strengthen existing social relations • Shared interest virtual communities have the potential to form new social relations between people, but also can hinder existing relations within a community

Example of Sacrificing Real Community Relations for Virtual Ones • http: //www. head 2 headgames. com/pics/cscpl 18. jpg

New Social Responsibilities • Issues of privacy – Windows 98 personal identifier • Issues of freedom of speech – 1996 Communication Decency Act • Advent of computer crime – Identity theft has become a large concern in recent years

Need for Regulation • Regulation policies are being created both on national and international levels – Aforementioned 1996 Act – In 2000, the European Commission began to work on a set of international regulations • The social implications of such regulations could range anywhere from censorship of obscene material to specialized online transactions to guarantee privacy

Conclusions • Networked Communications, most importantly the Internet, have various impacts on society – Establishes new methods of communication between persons around the world – Provides a means by which to amass large amounts of media that is easily accessible – Has laid the groundwork for the development of virtual communities, new social trends in their own right – Results in a new set of social responsibilities and regulations

Growth of, Control of and Access to the Internet By Roy Chung

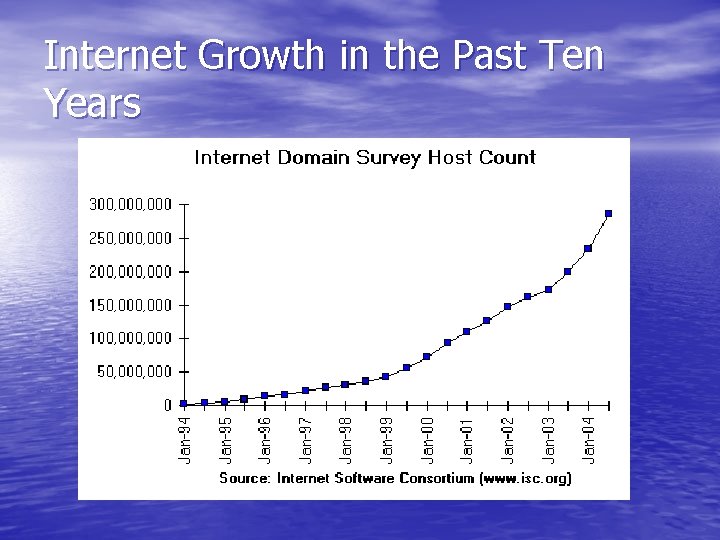
A Brief History of the Internet • First recorded description of social interactions • • • through networking done by J. C. R. Licklider of MIT in 1962. On September 1969, BBN delivered the first network computer and created the first long distance computer network, named ARPANET. During the 1970’s, ARPANET evolved in size and stability. Email was the most noteworthy development.

A Brief History of the Internet • In the 1980’s, a set of new communication • • • protocols, TCP/IP, was introduced. In 1983, there was the transition of the ARPANET host protocol from NCP to TCP/IP. In 1989 ARPANET was decommissioned, leaving a number of private companies to provide the backbone of the Internet. The World-Wide Web was conceived by Tim Berners-Lee and Robert Cailliau at CERN and made public in 1991.

Internet Growth in the Past Ten Years

Control of the Internet • Originally developed for military and then • • academic use. It was a closed network, so an ethical debate was not present. With the sudden growth of the Internet, ethical issues are becoming prevalent. Who should be held responsible? Governments, ISP’s, operators of services, along with end-users. However, much work still needs to be done.

Ethical Debates Regarding Control • Protection of minors. • Protection/privacy of the individual. • Respect for cultural differences. • Finding a balance between freedom of expression versus censorship. • Value and accuracy of the information provided.

Access to the Internet • Internet originally developed for the intellectual. • Access to the Internet should be universal, • • • regardless of income or disability. As the Internet continues to expand, more ethical debates will arise. Acceptable Use Policies are put in place in many institutions. Access to the Internet is a privilege that carries many responsibilities.


Gender related Issues of Computing By Gene Cumm

International Issues By Daniel Dauchy

Globalization due to IT • Definition – the unification of the nations on earth • Increase in globalization brought about by the new ways of communicating: – Email – Video conferencing – And other cheap and nearly instantaneous ways to communicate

1. ) The Open-Source Software Movement • Open Source Software – • free distribution of source code Started off as a social community – Hackers Richard Stallman

Closed-Source V. S. Open-Source Mike Wendy • Caused by the attempted passing of legislation that • supports open-source software Lobbying: – Closed-Source: Initiative for Software Choice (ISC) – Open-Source: Sincere Choice Bruce Perens

2. ) Offshoring Jobs Lost to Date Projected Job Loss Jobs at Risk 300, 000 -995, 000 3. 3 million-6 million 14. 1 million 300, 000 -500, 000 (Goldman Sachs) 3. 3 million over 15 years (Forrester Research) 400, 000 -500, 000 (Business Week) 6 million over 10 years (Goldman Sachs) 14. 1 million (UC Berkeley) 995, 000 (economy. com) • Offshoring – The sending of jobs overseas – For example American companies moving parts of their operations to India • Causes social issues in both countries *Statistics taken on March 16, 2004

In the United States • Social movements • against outsourcing have mobilized Movements include: – The American Champions – Techs Unite – The E-Activist Network – Communications Workers of America

In India • Increase in the number of middle class Indian people – Statistics: • The new 487 million middle-class Indians are expected to spend $420 billion in the next four years – Draws the attention of many companies

Related to Globalization? • The Open-Source Movement – Allows modification and improvement of source code on a global level • Offshoring – By directly influencing the culture of the affected areas

Computer Crime By Martin Goldman

What Is Computer Crime? • Criminal activity that is committed using computers, or that targets computers, or both – Many different types of offenses – Different types of perpetrators, different motivations – One of the biggest criminal threats facing society today

What Are the Crimes? • Breaches of Physical Security – Disruption of service – Interception of communication

What Are the Crimes? • Breaches of Personnel Security – Masquerading – Social engineering

What Are the Crimes? • Breaches of Communications/Data Security – Data attacks (e. g. data theft) – Software attacks (e. g. malware)

Who Are the Perpetrators? • Crackers • “Professional” Criminals • Vandals

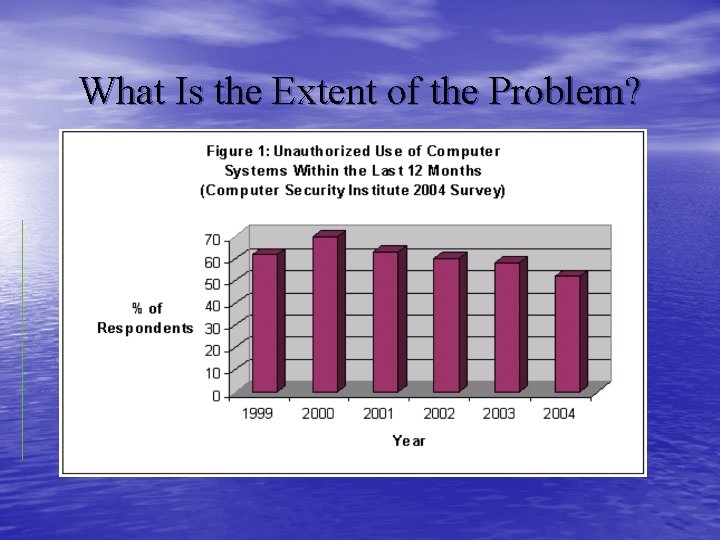
What Is the Extent of the Problem?

What Is the Extent of the Problem? • CSI/FBI Computer Crime and Security Survey – It's a big problem, but it's getting better • Hard to tell – Do. D: As few as 10% of cases are reported

Computer Crime Prevention By Joseph Wong

Computer Crime Prevention • Do not connect to anything • Hardware or Physical Level • Software Level • Laws and Lawsuits

Major Threats • Viruses • Hackers • Spyware/Spam • Copyright Infringement • Theft

Methods of Prevention • Hardware – Locks – Firewalls • Hardware based vs. Software based • Filtering – Allow everything vs. Deny everything.

Methods of Prevention • Software – Data Encryption • Firewalls • Wireless – Antivirus • On-access Detection vs. On-demand Detection – Spyware/Spam • Programs available online

Methods of Prevention • Laws – “Can Spam” Act & Spy Act – Computer Fraud and Abuse Act • “knowingly causes the transmission of a program, information, code, or command, and as a result of such conduct, intentionally causes damage without authorization, to a protected computer “ • Copyright Infringement (Piracy) – RIAA & MPAA – Software Companies

Total Prevention - Possible? • Technology Growing Too Fast • Multi-layered prevention • Wireless