The Social Context of Computing Group 1 Introduction























































- Slides: 60

The Social Context of Computing Group 1

Introduction to the Social Implications of Computing John Basias

History of computing n The first fully functioning electronic digital computer was Colossus (1943) n 'first generation' computers n weighed 30 tons and contained 18, 000 electronic valves

Second generation Computing n Transistor was invented in 1947 n 'Second Generation' and computers made their debut the late 1950 s and early 1960 s n still bulky and strictly the domain of Universities and governments

'Third and Fourth Generation' computing the great leap foward n Jack St. Claire Kilby's invention of the integrated circuit or microchip in the 1950’s n 1963 technology was integrated creating the first 3 rd generation computers n Smaller more efficient were used by smaller businesses n Still unavailable or affordable at the individual level

'Third and Fourth Generation' computing the great leap forward (cont. ) n November 15 th, 1971, Intel released the 4004, the world's first commercial microprocessor and the RAM chip n Dawn of the fourth and latest generation of computing

Effects n Drive toward improvement and applicability n The creation of operating systems in the 1980’s that directly translated conceptual action into computer code n Cheap affordable computing became possible to a much larger audience n Revolutionized the job market restructured the inner operations of many businesses. Outdated a lot of technology. n The emergence of hacking and viruses as threats

The Dawn of the Internet n Origionally ARPANET started by the US Dept. of Defense for research into networking sometime in 1969 n Became an object of interest by the 1970’s to large companies and Universities n It wasn’t until 1980’s that technology advanced far enough for there to be any use of this network n DNS – 1984 replacing IP addressing n HTTP and was invented in 1989 by Tim Berners-Lee n Graphical interface and web browsers appeared in the early 1990’s

Effects n Great shift in social status and social boundaries over the net n individual have the liberty to exchange, view ideas and information anonymously n How do we define boundaries? Ethical and moral issues

Effects (cont. ) n New Age of Hacking - everyone is at greater risk - viruses are potentially more destructive - spyware n Priavacy n Internet policing and enforcement and regulation of the netwok - the development of software and hardware to protect against hacking firewalls virus protection

Social Implications of Networked Communications Matt Berger

Networked Communications n n n Take many forms. ¨ E-mail, message boards, IRC. Primary advantage: convenience factor. Social Implications ¨ Community, local and global. ¨ Social Skills. ¨ The future of computer-mediated communication.

Community n Beneficial Effects ¨ Study has shown that networked communications increase both local and global community involvement. n Not intuitive – would expect less local involvement. ¨ Anonymity fosters a global community. n Discrimination is now not a factor. n Potential for this to spread into real life interaction.

Community n Detrimental Effects ¨ Internet communities are not situated anywhere. n Creates a certain level of unease and mistrust. ¨ Transition from group-based societies to network-based societies. n Internet communities contain a very weak level of connectivity.

Social Skills n Advantages of Anonymity ¨ The freedom a person has. n One can gain confidence in using an Internet persona. ¨ Advantageous to normally anti-social people. n Easier for them to express their thoughts – could extend to real life interactions.

Social Skills n Disadvantages of Anonymity ¨ Undergoing an Internet persona to insult others. n Freedom of Internet communication encourages this. ¨ Constant level of distrust. n Obstructs the possibility of developing healthy relationships. ¨ Computer-mediated communication is simply a poor substitute for physical interaction.

Future of Networked Communications n n n Advances under a matter of convenience. Should always be aware of the social consequences. ¨ For instance – recent controversy of using web logs as valid information sources. Ultimately, will never be a substitute for standard person-to-person communication.

Growth of, Control of, and Access to the Internet Luis M. Callejo

Growth of the Internet n Trends of Growth ¨ Adaption into Society ¨ Growing Ethical Considerations n Cyber ethics ¨ Growth of Applications n Website vs. Peer to Peer

Control of the Internet n Autonomous System ¨ Peering ¨ Border Gateway Protocol n Concerns about security

Access to the Internet n n Access to Information ¨ Cyberethics Presentation of Information ¨ Directories ¨ Automation

Conclusion n What will determine the future of the Internet? ¨ Development of Cyberethics ¨ Demands on Architecture

Gender Related Issues of Computing Nick Cavuoto

History of Women in Computing n n Ada Byron Edith Clarke Grace Murray Hopper World War II opened the door

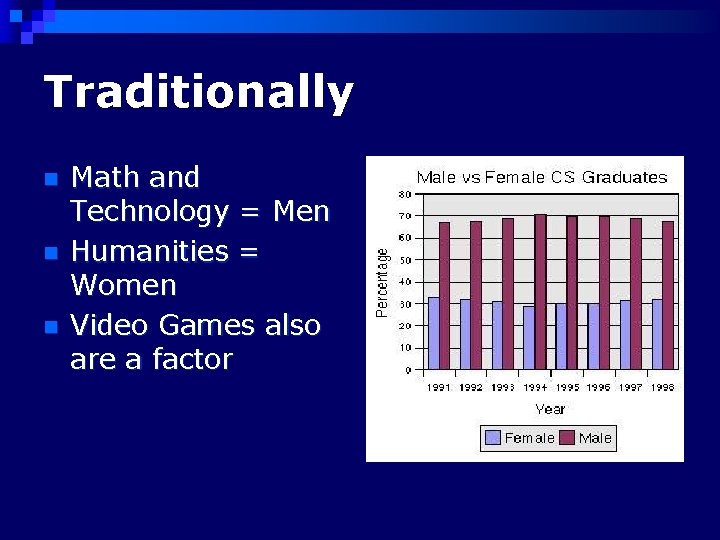
Traditionally n n n Math and Technology = Men Humanities = Women Video Games also are a factor

At the Job n n n Stereotypes in the work place Sex appeal Corporations with women at the helm are more successful

What to do? n n n AWC (Association for Women in Computing) Parents Teachers

International Issue Kefei Chen

Informational Technology (IT) and National Culture n Comparing the different approaches for managing IT between Japanese Culture and Western Culture.

Informational Technology (IT) and National Culture n n n How do they decide what are their business needs? ¨ strategic alignment vs. strategic instinct How will they know whether IT investments are worthwhile? ¨ value for money vs. performance improvement When they are trying to improve a business process, how does technology fit into their thinking? ¨ technology solutions vs. appropriate technology How should IT users and IT specialists connect in their organization? ¨ IT user relations vs. organizational bonding How can they design systems that improve organizational performance? ¨ system design vs. human design

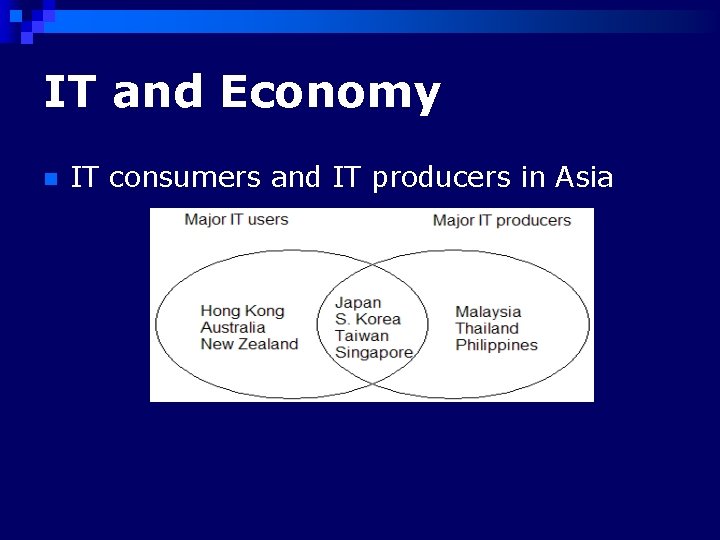
IT and Economy n IT consumers and IT producers in Asia

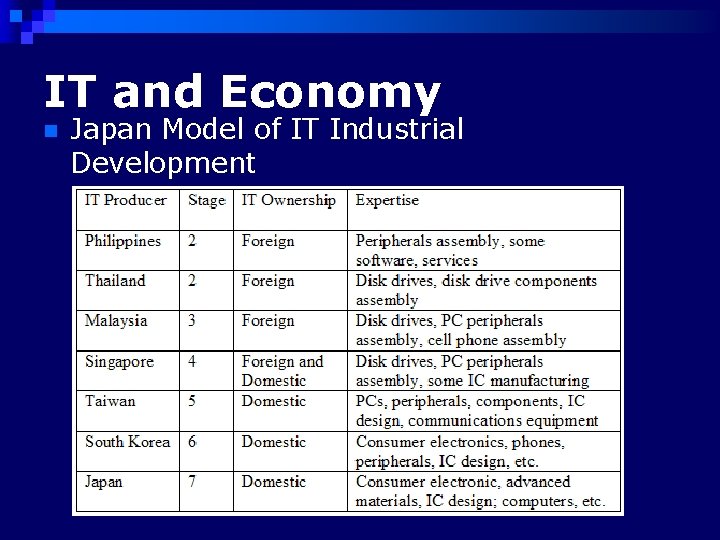
IT and Economy n Japan Model of IT Industrial Development

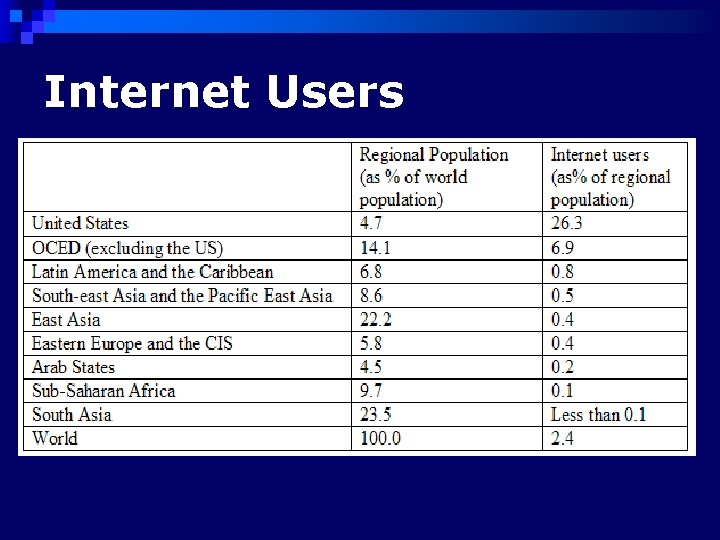
Internet Users

Internet Users n Key factors that determine the use of information technologies on an international basis: ¨ Income ¨ Cost of connection Monthly ¨ Education ¨ Gender ¨ Age ¨ Language

Internet Users n Example: ¨ An African country: Zambia ¨ Reasons of low internet usage: n High Cost of the internet n Low Computer Penetration n Shortage of Trained Personnel n Lack of Awareness of Information Technology

Computer Crime Hodan Egal

Computer Crime n Computer Crime is defined as any illegal act where special knowledge of computer is essential for its perpetration, investigation, or persecution.

Types of Attacks n n n Military and Intelligence attacks Business Attacks Financial Attacks Terrorist Attacks Grudge Attacks Fun Attacks

Military and Intelligence Attacks n n Computer store information ranging from the positioning of Air Force satellites to plans for troop deployment throughout the world. In June 1988, computer cracker Kevin Mitnick (code-named “Condor”) broke in remotely to a defense Department network. He allegedly stole a pre-release version of Digital Equipment Corporations VMS V 5. 0 operating system software and temporarily stored on a Navy computer at the Patuxent Naval Air Station.

Business Attacks n Business are increasingly the target of both competitors and the curious, although most business crimes are still committed by employees. e. g. In December 1987, apple found a virus in its electronic mail system. The virus succeeded in shutting down the system and erasing all Apple’s voice-mail.

Financial Attacks n n Banks are always a tempting target for computer criminals. e. g. Back 1998, seven criminals hatched a plot against the First National Bank of Chicago. The group used a wire transfer scheme to move &25. 37 million belonging to Merrill Lynch and Co, $25 million belonging to United Airlines and $19. 75 million belonging to the Brown-Forman Corporation to a New York bank and then to two separate banks in Vienna.

Terrorist Attacks Even terrorist have gone high-tech. Terrorist were striking at the computer industry, but not for the first time

Grudge & Fun Attacks Not all computers criminals are seeking information. Some simply want to wreak damage and destruction. At one extreme, computer crime can be much more profitable than other forms of fraud and terrorism.

Federal Approaches This section explores the major federal statutes, enforcement strategies and constitutional issues regarding computer related crimes. § Federal Criminal Code § Enforcement Strategies

Prevention of Computer Crime There are many approaches to protect computer system from attack. Ø Identifying Risks Ø Physical Security Ø Personal Security Ø Communication Security Ø Operations Security

Conclusion Computer Crime will increasingly be a challenge faced by all industrialized nations. Solutions that rely solely on international coordination to investigate and prosecute computer criminals will not work.

Computer Crime Prevention Sean Egan

Preventing Computer Crime n n n Use secure software Have a sane password policy Understand how computer crime works

Use Secure Software n n n Regardless of how safe you are, using insecure software puts you at risk Don't use buggy software ¨ Microsoft Windows/IE/Outlook/etc. suck Even bug-free software is dangerous if poorly designed ¨ Telnet vs. SSH

Have a Sane Password Policy n n n Passwords are often the only thing keeping intruders out of your system Choose good passwords ¨ Consider passphrases Handle with care ¨ Change passwords often ¨ Keep passwords secret

Understand How Computer Crime Works n n Keep informed about software vulnerabilities ¨ Bug. Traq mailing list ¨ Operating system announcements ¨ Automatic updates Honeypots ¨ Used to safely monitor illicit activity in the wild ¨ Not limited just to single computers

Conclusion n n Be responsible computer users Make smart choices about software Exhibit responsible behavior about password usage Educate yourself

Diversity in the Workplace Philip Fong

Diversity n Acknowledging, understanding, accepting, valuing, and celebrating differences among people with respect to age, class, ethnicity, gender, physical and mental ability, race, sexual orientation, spiritual practice, and public assistance status

Affirmative Action n n Established by Kennedy Administration Counteract racial discrimination “Reverse Discrimination” Now nearly obsolete

Glass Ceiling n n Barrier that inhibits women and minorities from top-tier job positions The result of conscious and unconscious stereotyping and discrimination

Gender Roles n n n Imposed by tradition and society Men – “Power suit, power tie, power steering. ” Women – 50 times more likely to stay at home to take care of children

Age n n n Elderly employees are paid more with lucrative benefit packages More expensive to keep in the work force Older employees are more educated – important to country’s productivity growth

Diversity is the Future n n n Monochrome work force will not survive into the future Diverse work force promotes creativity, productivity, and competitiveness Diversity reinforces that employees are hired based on skill and talent, not on demographic differences

Diversity is the Future (cont. ) n n n Projected that women will eventually make up 50% of the entire labor force 85% of new workers in 2005 include women and minorities Human resource departments – trained to manage diverse workplace – trained to hire the best talent