The RSA Cryptosystem and Factoring Integers II RongJaye

![OUTLINE § [1] Modular Arithmetic Algorithms [2] The RSA Cryptosystem § [3] Quadratic Residues OUTLINE § [1] Modular Arithmetic Algorithms [2] The RSA Cryptosystem § [3] Quadratic Residues](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-2.jpg)
![n [5] Square Roots Modulo n n n 1. Fact Suppose that p is n [5] Square Roots Modulo n n n 1. Fact Suppose that p is](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-3.jpg)
![n [6] Factoring Algorithms n 1. The Pollard’s p-1 algorithm input: an integer n n [6] Factoring Algorithms n 1. The Pollard’s p-1 algorithm input: an integer n](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-5.jpg)





![n [7] Other Attacks on RSA n Are there possible attacks on RSA other n [7] Other Attacks on RSA n Are there possible attacks on RSA other](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-20.jpg)

![n [8] The Rabin Cryptosystem n 1. Rabin scheme n n n Let p, n [8] The Rabin Cryptosystem n 1. Rabin scheme n n n Let p,](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-22.jpg)


![n [9] Semantic Security of RSA n 1. Potential 3 adversarial goals: n n n [9] Semantic Security of RSA n 1. Potential 3 adversarial goals: n n](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-27.jpg)


- Slides: 29

The RSA Cryptosystem and Factoring Integers (II) Rong-Jaye Chen
![OUTLINE 1 Modular Arithmetic Algorithms 2 The RSA Cryptosystem 3 Quadratic Residues OUTLINE § [1] Modular Arithmetic Algorithms [2] The RSA Cryptosystem § [3] Quadratic Residues](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-2.jpg)
OUTLINE § [1] Modular Arithmetic Algorithms [2] The RSA Cryptosystem § [3] Quadratic Residues § [4] Primality Testing § n n n [5] Square Roots Modulo n [6] Factoring Algorithms [7] Other Attacks on RSA [8] The Rabin Cryptosystem [9] Semantics Security of RSA p 2.
![n 5 Square Roots Modulo n n n 1 Fact Suppose that p is n [5] Square Roots Modulo n n n 1. Fact Suppose that p is](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-3.jpg)
n [5] Square Roots Modulo n n n 1. Fact Suppose that p is an odd prime and gcd(a, n)=1. Then the congruence y 2=a (mod n) has no solutions if (a/p)=-1, and two solutions (mod n) if (a/p)=1. 2. Theorem Suppose that p is an odd prime, e is a positive integer, and gcd(a, p)=1. Then the congruence y 2=a (mod pe) has no solutions if (a/p)=-1, and two solutions (mod pe) if (a/p)=1. p 3.

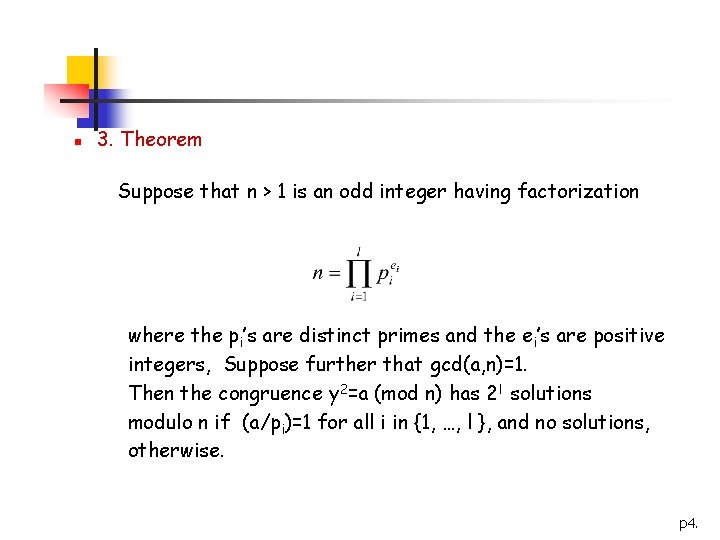
n 3. Theorem Suppose that n > 1 is an odd integer having factorization where the pi’s are distinct primes and the ei’s are positive integers, Suppose further that gcd(a, n)=1. Then the congruence y 2=a (mod n) has 2 l solutions modulo n if (a/pi)=1 for all i in {1, …, l }, and no solutions, otherwise. p 4.
![n 6 Factoring Algorithms n 1 The Pollards p1 algorithm input an integer n n [6] Factoring Algorithms n 1. The Pollard’s p-1 algorithm input: an integer n](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-5.jpg)
n [6] Factoring Algorithms n 1. The Pollard’s p-1 algorithm input: an integer n , and a prespecified “bound” B output:factors of n p 5.

n Why? Suppose p is a prime divisor of n, and suppose that q <= B for every prime power q|(p-1). Then (p-1)|B! At the end of for loop, we have a=2 B! mod n Now 2 p-1=1 mod p (by Fermat’s little Thm) Since (p-1)|B!, it follows a=2 B! =1 mod p and hence p|(a-1). Since we also have p|n, d=gcd(a-1, n) will be a non-trivial divisor of n (unless a=1). p 6.

n E. g. n=15770708441, B=180 a = 2180! = 11620221425 D = gcd(a-1, n) = 135979 In fact, the complete factorization of n into primes is 15770708441 = 135979 x 115979 The factorization succeeds because 135978 has only “small” prime factors: 135978 = 2 x 3 x 131 x 173 p 7.

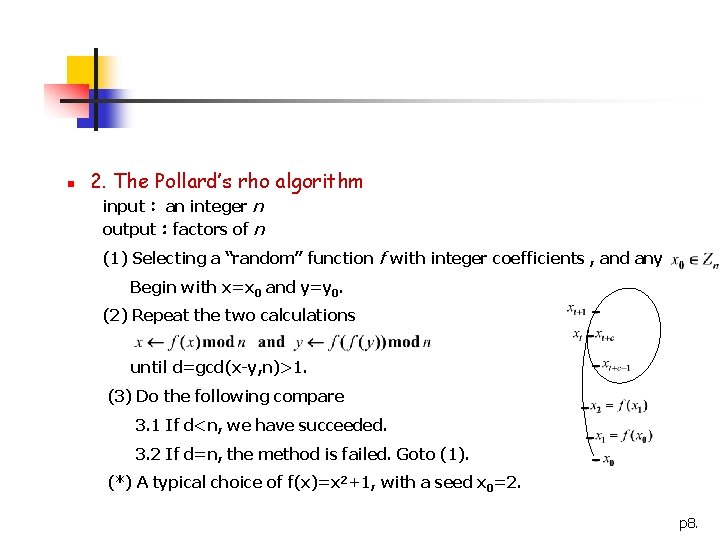
n 2. The Pollard’s rho algorithm input: an integer n output:factors of n (1) Selecting a “random” function f with integer coefficients , and any Begin with x=x 0 and y=y 0. (2) Repeat the two calculations until d=gcd(x-y, n)>1. (3) Do the following compare 3. 1 If d<n, we have succeeded. 3. 2 If d=n, the method is failed. Goto (1). (*) A typical choice of f(x)=x 2+1, with a seed x 0=2. p 8.

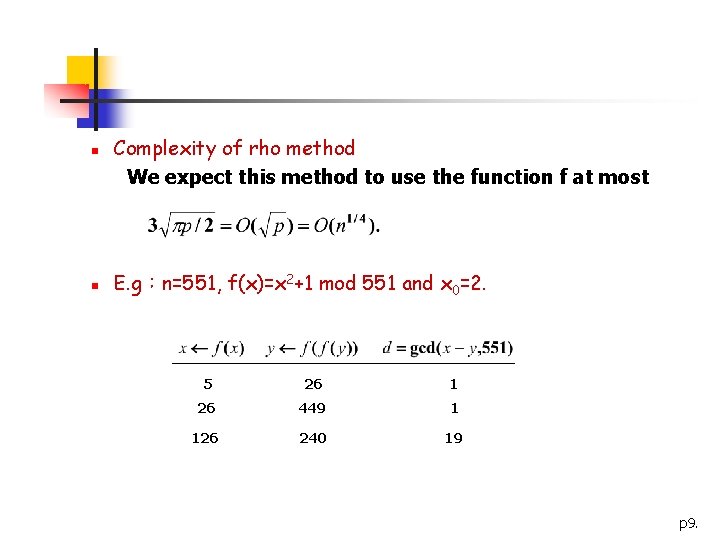
n n Complexity of rho method We expect this method to use the function f at most E. g:n=551, f(x)=x 2+1 mod 551 and x 0=2. 5 26 1 26 449 1 126 240 19 p 9.

n 3. Dixon’s random squares algorithm n The idea is to locate with if gcd(x+y, n) is a nontrivial factor of n. (Why? ) since n|(x-y)(x+y) but neither of x-y or x+y is divisible by n. n Eg. n=15, x=2, y=7 (22=72 mod 15) => gcd(2+7, 15)=3 is a nontrivial factor of n. n Eg. n=77, x=10, y=32 (102=322 mod 77) => gcd(10+32, 77)=7 is a nontrivial factor of n. p 10.

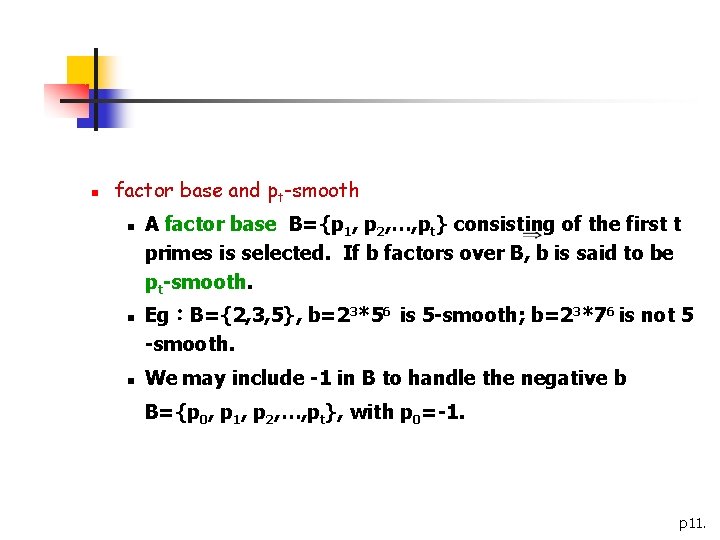
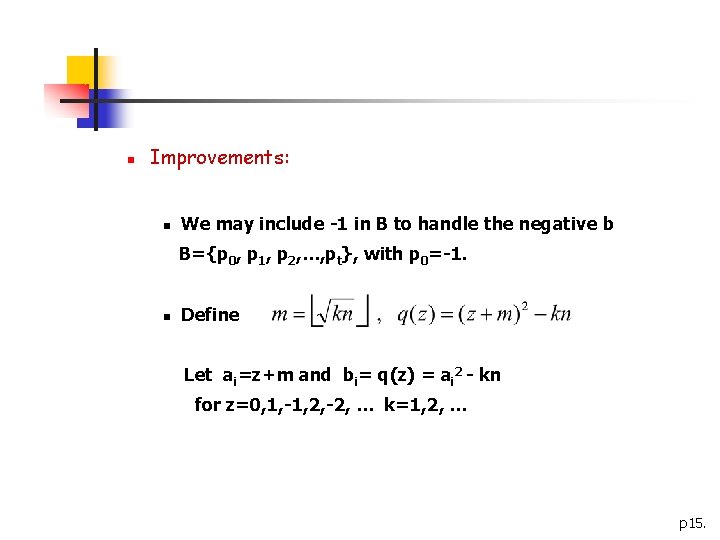
n factor base and pt-smooth n n n A factor base B={p 1, p 2, …, pt} consisting of the first t primes is selected. If b factors over B, b is said to be pt-smooth. Eg:B={2, 3, 5}, b=23*56 is 5 -smooth; b=23*76 is not 5 -smooth. We may include -1 in B to handle the negative b B={p 0, p 1, p 2, …, pt}, with p 0=-1. p 11.

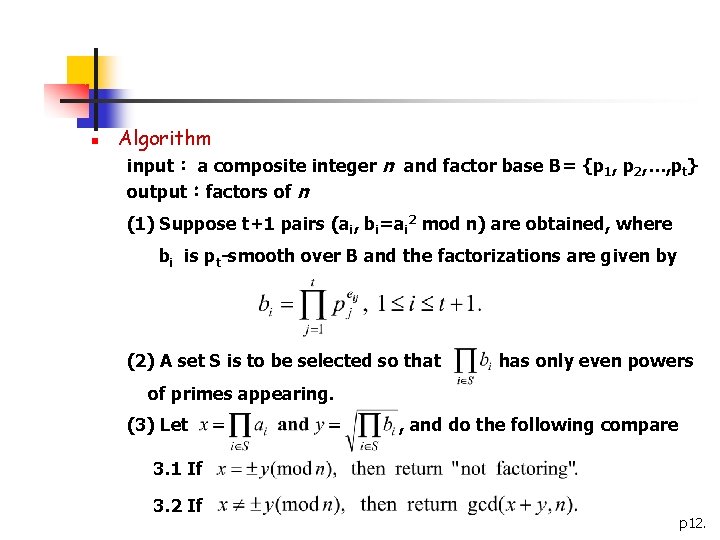
n Algorithm input: a composite integer n and factor base B= {p 1, p 2, …, pt} output:factors of n (1) Suppose t+1 pairs (ai, bi=ai 2 mod n) are obtained, where bi is pt-smooth over B and the factorizations are given by (2) A set S is to be selected so that has only even powers of primes appearing. (3) Let , and do the following compare 3. 1 If 3. 2 If p 12.

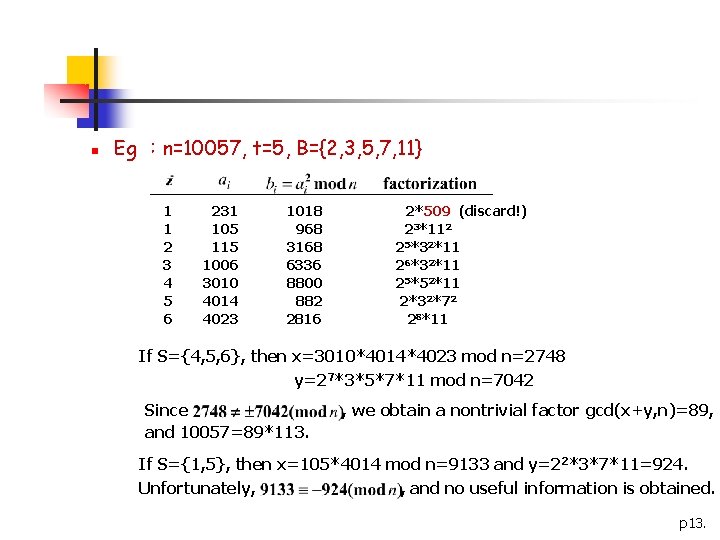
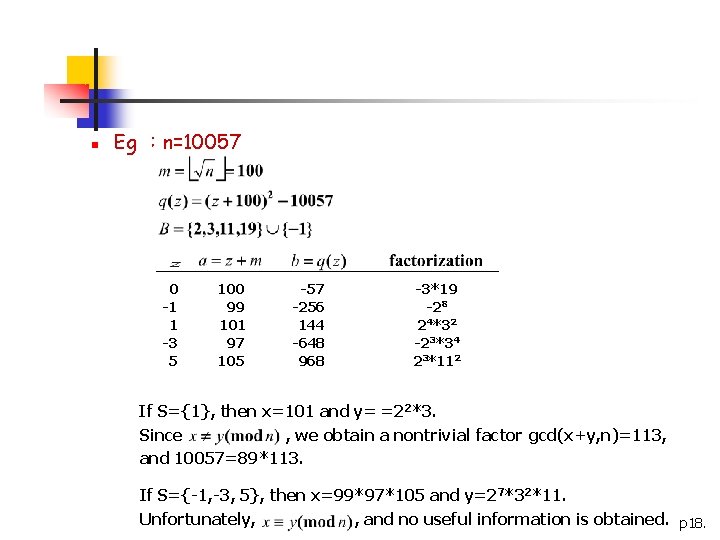
n Eg :n=10057, t=5, B={2, 3, 5, 7, 11} 1 1 2 3 4 5 6 231 105 115 1006 3010 4014 4023 1018 968 3168 6336 8800 882 2816 2*509 (discard!) 23*112 25*32*11 26*32*11 25*52*11 2*32*72 28*11 If S={4, 5, 6}, then x=3010*4014*4023 mod n=2748 y=27*3*5*7*11 mod n=7042 Since and 10057=89*113. , we obtain a nontrivial factor gcd(x+y, n)=89, If S={1, 5}, then x=105*4014 mod n=9133 and y=22*3*7*11=924. Unfortunately, , and no useful information is obtained. p 13.

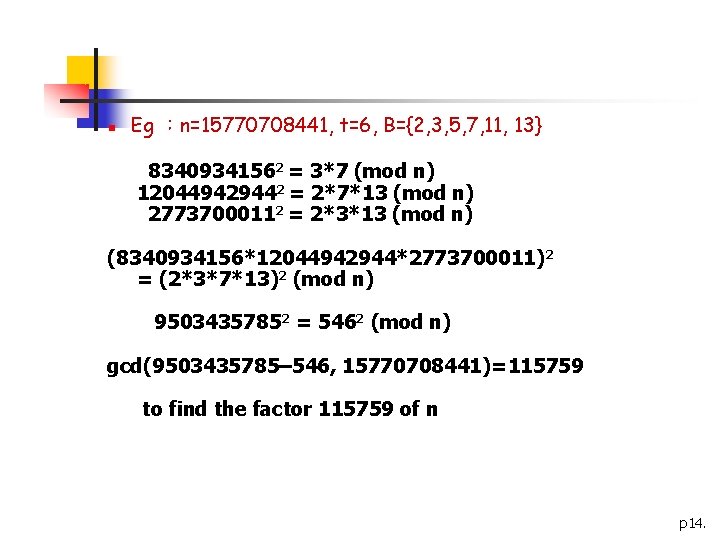
n Eg :n=15770708441, t=6, B={2, 3, 5, 7, 11, 13} 83409341562 = 3*7 (mod n) 120449429442 = 2*7*13 (mod n) 27737000112 = 2*3*13 (mod n) (8340934156*12044942944*2773700011)2 = (2*3*7*13)2 (mod n) 95034357852 = 5462 (mod n) gcd(9503435785– 546, 15770708441)=115759 to find the factor 115759 of n p 14.

n Improvements: n We may include -1 in B to handle the negative b B={p 0, p 1, p 2, …, pt}, with p 0=-1. n Define Let ai=z+m and bi= q(z) = ai 2 - kn for z=0, 1, -1, 2, -2, … k=1, 2, … p 15.

n Quadratic sieve algorithm (simple version) input: a composite integer n output:factors of n (1) choose a suitable P and construct a factor base (2) Define (3) Let ai=z+m and bi=q(z)=ai 2 -n for z=0, 1, -1, 2, -2, … A set S is to be selected so that (4) Let has only even powers of primes appearing. , and do the following p 16.
p 17.

n Eg :n=10057 0 -1 1 -3 5 100 99 101 97 105 -57 -256 144 -648 968 -3*19 -28 24*32 -23*34 23*112 If S={1}, then x=101 and y= =22*3. Since , we obtain a nontrivial factor gcd(x+y, n)=113, and 10057=89*113. If S={-1, -3, 5}, then x=99*97*105 and y=27*32*11. Unfortunately, , and no useful information is obtained. p 18.

n 4. Factoring algorithms in practice (Asymptotic running times) 1. Quadratic sieve 2. Elliptic curve (p is the smallest prime factor of n) 3. Number field sieve p 19.
![n 7 Other Attacks on RSA n Are there possible attacks on RSA other n [7] Other Attacks on RSA n Are there possible attacks on RSA other](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-20.jpg)
n [7] Other Attacks on RSA n Are there possible attacks on RSA other than factoring n? (Yes, see 2. 3. ) 1. Computing (n) is no easier than factoring n For, if n and (n) are known, and n is the product of two primes p, q, then n can be easily factored by solving n=pq (n)=(p-1)(q-1) for the two unknowns p and q. Substituting q=n/p into the 2 nd eq. , We have P 2 -(n- (n)+1)p + n = 0. The two roots will be p and q. p 20.

n n 2. The Decryption Exponent (See sec. 5. 7. 2) 3. Wiener’s Low Decryption Exponent Attack (See sec. 5. 7. 3) p 21.
![n 8 The Rabin Cryptosystem n 1 Rabin scheme n n n Let p n [8] The Rabin Cryptosystem n 1. Rabin scheme n n n Let p,](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-22.jpg)
n [8] The Rabin Cryptosystem n 1. Rabin scheme n n n Let p, q be large primes, n=pq (p, q) be the private key Encryption: c=m 2 mod n Decryption: find the four square roots and one is m 2. Example n n n Consider p=31, q=41, so n=pq=1271 Assume message m=814 so c = m 2 mod n = 8142 mod 1271 = 405 Decryption Solving m 2 405 2 (mod 31) and m 2 405 36 (mod 41) obtain m 8 (mod 31) and m 6 (mod 41) four possible roots: { 240, 457} (mod 1271) p 22.

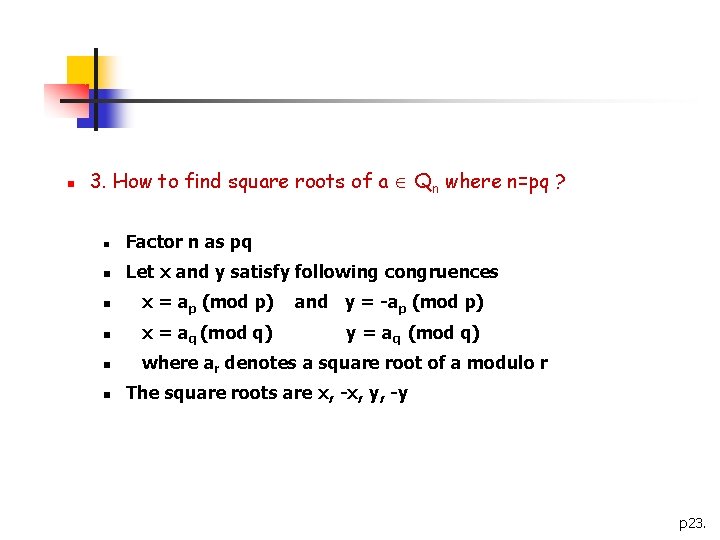
n 3. How to find square roots of a Qn where n=pq ? n Factor n as pq n Let x and y satisfy following congruences n x = ap (mod p) and y = -ap (mod p) n x = aq (mod q) y = aq (mod q) n where ar denotes a square root of a modulo r n The square roots are x, -x, y, -y p 23.

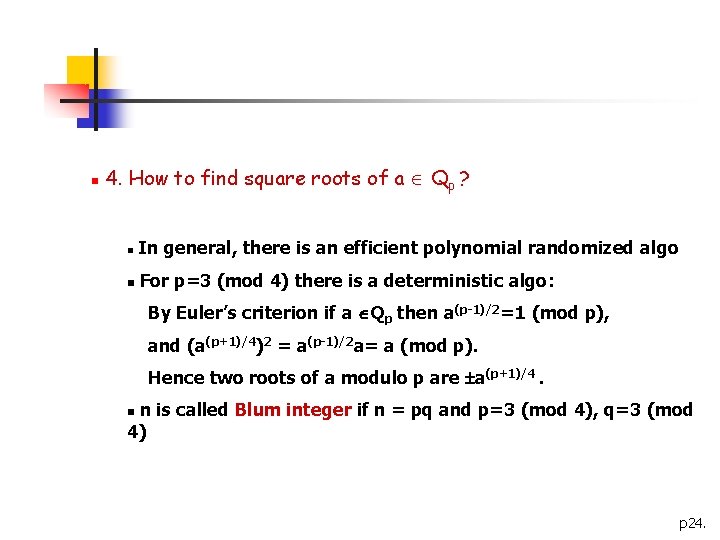
n 4. How to find square roots of a Qp ? n In general, there is an efficient polynomial randomized algo n For p=3 (mod 4) there is a deterministic algo: By Euler’s criterion if a Qp then a(p-1)/2=1 (mod p), and (a(p+1)/4)2 = a(p-1)/2 a= a (mod p). Hence two roots of a modulo p are a(p+1)/4. n is called Blum integer if n = pq and p=3 (mod 4), q=3 (mod 4) n p 24.

n n 5. Definition RABIN: Given n=pq and c=m 2 mod n, find x, s. t. c x 2 (mod n) 6. Theorem RABIN = FACTOR <pf> n (1) RABIN FACTOR Given an oracle for FACTOR 1. Factor n and obtain p, q 2. Solve the square root problems c x 2 (mod p) c x 2 (mod q) 3. Apply CRT and get four roots of RABIN p 25.

n (2) FACTOR RABIN Given an oracle for RABIN 1. Query RABIN oracle twice, get two roots x and y 2. With prob. ½, we can successfully get the factor of n by gcd(x+y, n) p 26.
![n 9 Semantic Security of RSA n 1 Potential 3 adversarial goals n n n [9] Semantic Security of RSA n 1. Potential 3 adversarial goals: n n](https://slidetodoc.com/presentation_image_h2/bdf4f686a06a5b8b40baadcaf0d8386e/image-27.jpg)
n [9] Semantic Security of RSA n 1. Potential 3 adversarial goals: n n Total break The adversary is able to determine Bob’s private key (in the case of a public-key cryptosystem) or the secret key (in the case of a symmetric-key cryptosystem). Partial break The adversary is able to decrypt a previously unseen ciphertext (without knowing the key). Or the adversarial can determine some specific information about the plaintext, given the ciphertext. p 27.

n n Distinguishability of ciphertexts With some prob. > 0. 5, the adversary is able to distinguish between encryptions of 2 given plaintexts, or between an encryption of a given plaintext and a random string. 2. Semantic security A public-key cryptosystem is said to achieve semantic security if the adversary cannot (in polynomial time) distinguish ciphertexts, provided that certain computational assumptions hold. p 28.

n n 3. Partial information concerning plaintext bits (See sec. 5. 9. 1) 4. Optimal Asymmetric encryption padding (See sec. 5. 9. 2) p 29.