The Rise of the Smartphone Fueled SocialMediaAddicted Workplace









































- Slides: 53

The Rise of the Smartphone. Fueled Social-Media-Addicted Workplace Zombies By Daniel A. Schwartz IASA November 2017

Zombies

Nazi Zombies

And Then The Attacks Happened…Again

Zombies!

Workplace Zombies

Warning: They may not look like this.

These Are The Same People…

Who Still Plays Solitaire?

And Made This a Top 10 App…

So, Most of Your Employees…Are Zombies

Smartphone Zombies

Smartphone Zombies • Wikipedia - A smartphone zombie (smombie) is a pedestrian who walks slowly and without attention to their surroundings because they are focused upon their smartphone.

In the Netherlands Pavement lights used at pedestrian crossings

It’s Spreading

Let’s Assume • The rapid adoption of smartphones is changing how people function u They receive information 24/7 u They convey information 24/7 u And they are endlessly informed and distracted

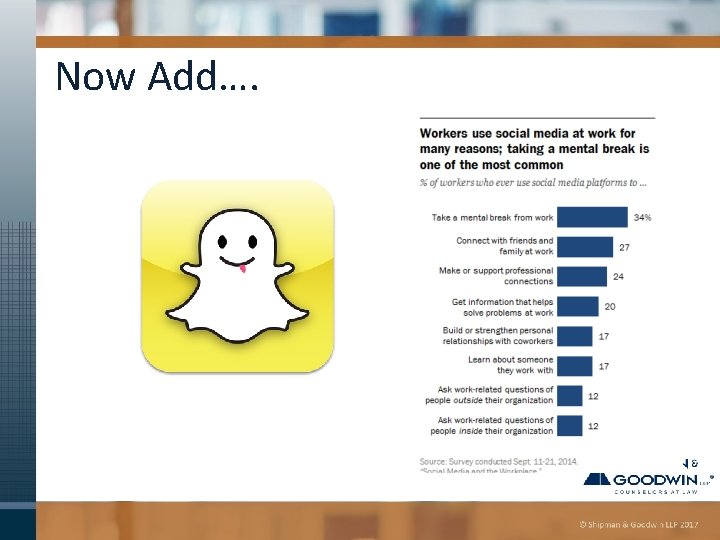
Now Add….

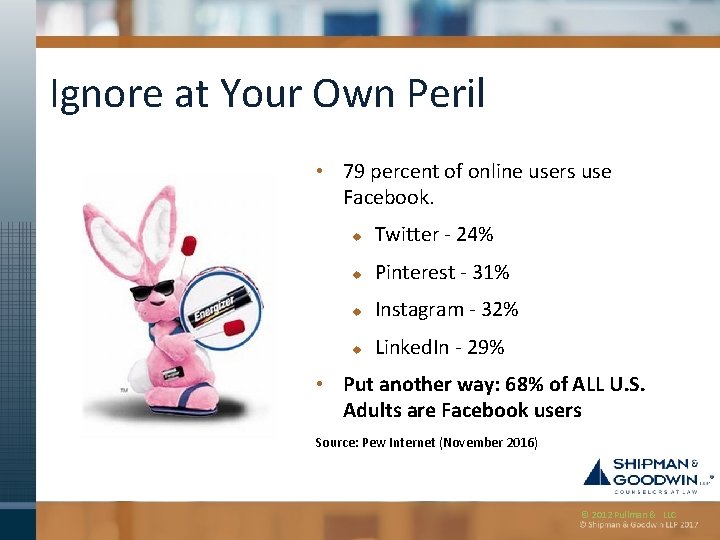
Ignore at Your Own Peril • 79 percent of online users use Facebook. u Twitter - 24% u Pinterest - 31% u Instagram - 32% u Linked. In - 29% • Put another way: 68% of ALL U. S. Adults are Facebook users Source: Pew Internet (November 2016) © 2012 Pullman & LLC

And Messaging Apps Are Next • 29% of smartphone owners use messaging apps such as Whats. App or Kik • 24% use messaging apps that automatically delete sent messages such as Snapchat or Wickr 19

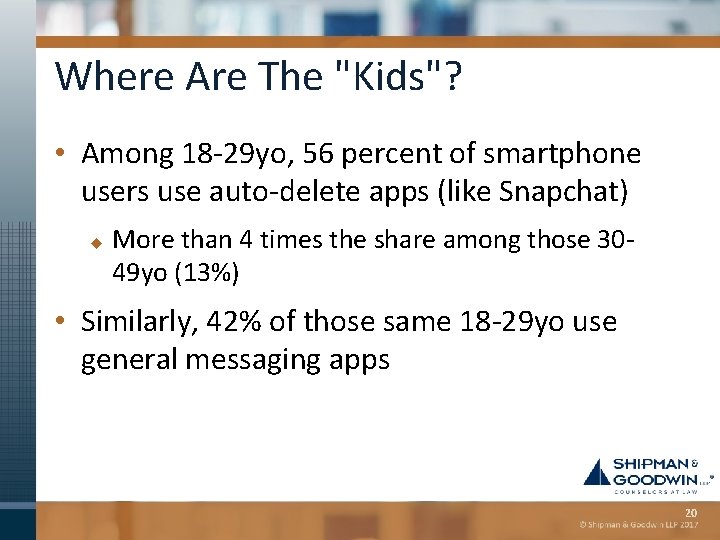
Where Are The "Kids"? • Among 18 -29 yo, 56 percent of smartphone users use auto-delete apps (like Snapchat) u More than 4 times the share among those 3049 yo (13%) • Similarly, 42% of those same 18 -29 yo use general messaging apps 20

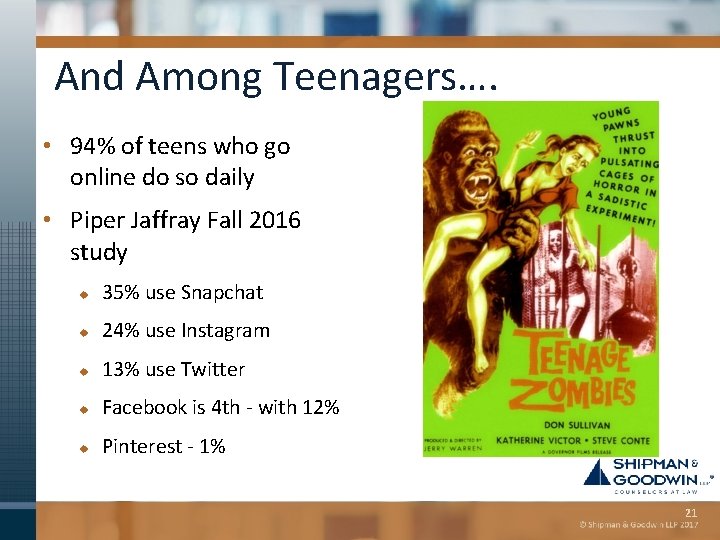
And Among Teenagers…. • 94% of teens who go online do so daily • Piper Jaffray Fall 2016 study u 35% use Snapchat u 24% use Instagram u 13% use Twitter u Facebook is 4 th - with 12% u Pinterest - 1% 21

And Your Workers Too

Guess What? • They’re all either in your office workforce or will soon be there • Either way, you can’t destroy your employee’s brains

What Are The Legal Implications? • Data privacy • Lack of in-person communications • Failure to integrate into culture, including business ethics • A confusion between “at work” and “outside of work” • Using outside systems

DATA PRIVACY & THE WORKPLACE

Whac-a-Mole

As An Aside….

But Zombies In The Workplace…

FBI’s 5/4/17 PSA • Business E-mail Compromise: “Sophisticated scam targeting businesses working with foreign suppliers or businesses that regularly perform wire transfer payments. ” u E-mail Account Compromise now similar • How does it work? Compromises legit business e-mail through social engineering to conduct unauthorized transfer of funds Source: https: //www. ic 3. gov/media/2017/170504. aspx

Five Types of BEC • Business Working with foreign supplier • Business Executive Receiving or Initiating a Request for Wire Transfer • Business Contacts Receiving Fake E-mail • Business Executive/Attorney Impersonation • Data Theft – W-2 s or PII Source: https: //www. ic 3. gov/media/2017/170504. aspx

Trends • W-2 / PII Data Theft • Resurgence of Original Scheme of Int’l Suppliers • Real Estate Transactions u 480 percent increase in complaints by title companies

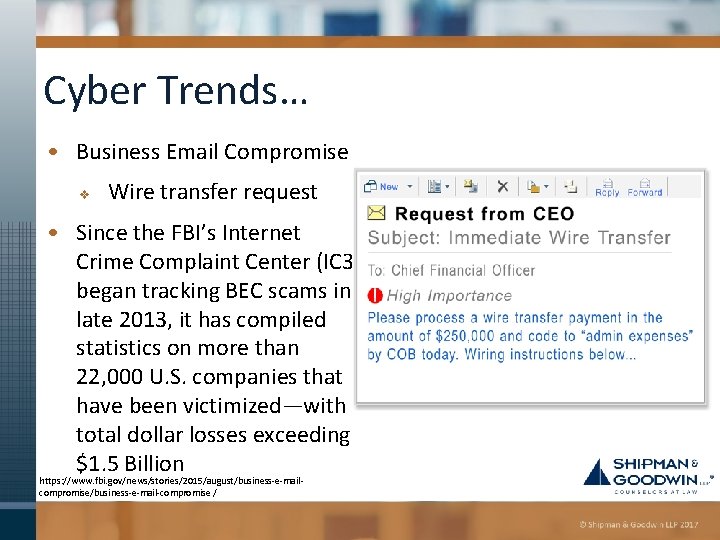
Cyber Trends… • Business Email Compromise v Wire transfer request • Since the FBI’s Internet Crime Complaint Center (IC 3) began tracking BEC scams in late 2013, it has compiled statistics on more than 22, 000 U. S. companies that have been victimized—with total dollar losses exceeding $1. 5 Billion https: //www. fbi. gov/news/stories/2015/august/business-e-mailcompromise/business-e-mail-compromise /

Common Scenario • CFO “sends” e-mail to the business office requesting the W-2 forms on an urgent basis u u u Kindly send me the individual 2016 W-2 (PDF) and earnings summary of all W-2 of our company staff for a quick review. Can you send me the updated list of employees with full details (name, social security number, date of birth, home address, salary). I want you to send me the list of W-2 copy of employees wage and tax statement for 2016, I need them in PDF file type, you can send it as an attachment. Kindly prepare the lists and email them to me ASAP.

Cyber Trends… • Ransomware • • Most popular version, until recently is Cryptolocker Encrypts user data and ransoms the key for a price • Regular backups • Patching (OS and Apps)

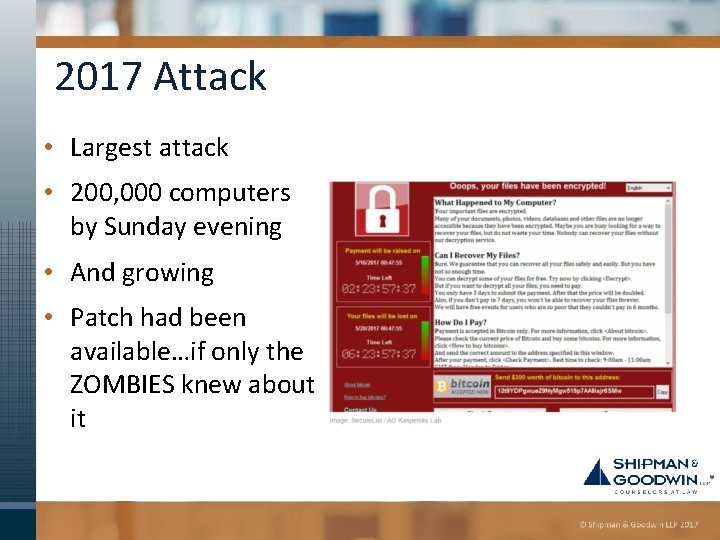
2017 Attack • Largest attack • 200, 000 computers by Sunday evening • And growing • Patch had been available…if only the ZOMBIES knew about it

Ransomware • Companies are by far the biggest target • 21 percent related to espionage u u And of those, 90 percent are linked to stateaffiliated groups Competitors & former employees account for remaining 10 percent Source: Verizon Data Breach Investigations Report 2017

Cyber Trends Phishing Season • E-mail (targeted) • Phone (tech support) Reconnaissance • Social Media • Linked. In Cite: https: //www. lookingglasscyber. com/blo g/phishing/weekly-phishing-activity-may -1 -2017/

Cyber Trends

Examples

Other Breaches in Workplaces • Employee downloads confidential information for more than 450 k participants to home computer • Hacking of plan’s administrative system v Holding such data for ransom • SSNs on documents mailed to wrong addresses or information was made visible to others

Other Breaches of Welfare Plans • Breach resulting from unencrypted information of PHI on laptops • Return of photocopies to leasing agent without erasing data on copier’s hard drives • Lost documents with PHI


• Phishing is successful…because it works • 1 in 14 phishing attacks were successful in that the victim clicked on the link in the email or opened the attachment • Spoofing websites happens, but documents with embedded macros still far more common #1 Zombie Movie? Dawn of the Dead

Workplace Security Fatigue • Over 3 BILLION e-mail addresses, usernames, passwords estimated to be traded and sold on dark net • Have we reached the “peak”?

Can Tech Save Us From Ourselves? • Two main paths u u One - Create technology to take the “people” out of it We keep trying that Ø Spam filters Ø Firewalls Ø Policies and practices

Alternatively… • Rely on the Zombies u Training? u Password changes?

But That May Not Work

Cure For Zombies? • What do we know? • Can they be cured? • Or are we only hoping to contain them?

Bring Back from Dead? • Don’t give up on your employees, but don’t assume they will all magically be “cured” either • Work on systems that reduce the human element u Anytime you ask an employee whether they want to “encrypt” a message, answer will be no

Develop Your Own “Zombies” • Some companies indoctrinate employees into a culture of business ethics • “Protecting” our business has to be part of the mindset • The “Jerry Maguire” version

Solutions are Not New • But the notion that technology will save what ails us can’t be either • Two pronged approach u u Always keeping in mind the legal exposures that exist there Data privacy is but one of a whole host of issues

If Minecraft Can Solve It…

Questions? These materials have been prepared by Shipman & Goodwin LLP for informational purposes only. They are not intended as advertising and should not be considered legal advice. This information is not intended to create, and receipt of it does not create, a lawyer-client relationship. Viewers should not act upon this information without seeking professional counsel.
 Tricky dick: the rise and fall and rise of richard m. nixon
Tricky dick: the rise and fall and rise of richard m. nixon Rise and rise again until lambs become lions
Rise and rise again until lambs become lions A union b example
A union b example Sheep become lions
Sheep become lions Fueled by marcie hans
Fueled by marcie hans Jobs of the respiratory system
Jobs of the respiratory system Rima interna
Rima interna My parent never stop quizzing me
My parent never stop quizzing me Tablet vs smartphone
Tablet vs smartphone Vip smartphone
Vip smartphone Summary mobile phone
Summary mobile phone Csece
Csece Smartphone forensic system
Smartphone forensic system Flamy smartphone
Flamy smartphone Iodé smartphone
Iodé smartphone Smartphone-pentest-framework
Smartphone-pentest-framework Smartphone hardware architecture
Smartphone hardware architecture Smartphone
Smartphone Cycle de vie smartphone
Cycle de vie smartphone Smartphone energy consumption
Smartphone energy consumption Hệ hô hấp
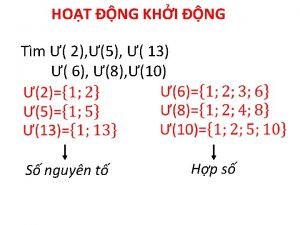
Hệ hô hấp Bảng số nguyên tố lớn hơn 1000
Bảng số nguyên tố lớn hơn 1000 Môn thể thao bắt đầu bằng chữ đua
Môn thể thao bắt đầu bằng chữ đua đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Hát kết hợp bộ gõ cơ thể
Hát kết hợp bộ gõ cơ thể Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới ưu thế lai là gì
ưu thế lai là gì Tư thế ngồi viết
Tư thế ngồi viết Chó sói
Chó sói Cái miệng nó xinh thế
Cái miệng nó xinh thế Mật thư tọa độ 5x5
Mật thư tọa độ 5x5 Tư thế ngồi viết
Tư thế ngồi viết Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Ví dụ về giọng cùng tên
Ví dụ về giọng cùng tên Thẻ vin
Thẻ vin Lp html
Lp html Thơ thất ngôn tứ tuyệt đường luật
Thơ thất ngôn tứ tuyệt đường luật Hổ sinh sản vào mùa nào
Hổ sinh sản vào mùa nào Từ ngữ thể hiện lòng nhân hậu
Từ ngữ thể hiện lòng nhân hậu Diễn thế sinh thái là
Diễn thế sinh thái là Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Chụp tư thế worms-breton
Chụp tư thế worms-breton Phép trừ bù
Phép trừ bù Lời thề hippocrates
Lời thề hippocrates đại từ thay thế
đại từ thay thế Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Bổ thể
Bổ thể Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Cong thức tính động năng
Cong thức tính động năng Sự nuôi và dạy con của hổ
Sự nuôi và dạy con của hổ Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Dạng đột biến một nhiễm là
Dạng đột biến một nhiễm là