The Privacy Cycle A FiveStep Process to Improve




















- Slides: 27

The Privacy Cycle A Five-Step Process to Improve Your Privacy Culture Presented By Tim Burris Product Manager, Iatric Systems

Today’s Speaker Tim Burris Product Manager Iatric Systems

The Privacy Cycle Continuous process that relates regulations to meaningful actions in Healthcare organizations

5 Key Steps to the Privacy Cycle 1. Policy and Procedure Review 2. Auditing 3. Documentation 4. Trend Analysis 5. Corrective Action

Step 1 Policy & Procedure Review

Step 1: Policy & Procedure Review Know Your Regulatory Requirements HIPAA Security Rule, 45 CFR 164. 308(a)(1)(i) Security management process Organizations must implement policies and procedures to prevent, detect, contain and correct security violations HIPAA Security Rule, 45 CFR 164. 312(b) Audit controls Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use e. PHI HIPAA Security Rule, 308(a)(1)(ii)(D) Information system activity review Implement procedures to regularly review records of information systems activity, such as audit logs, access reports, and security incident tracking reports

Step 1: Policy & Procedure Review OCR Guidance It is imperative for Covered Entities and Business Associates to review their audit trails regularly, both particularly after security incidents or breaches, and during real-time operations. Regular review of information system activity should promote awareness of any information system activity that could suggest a security incident or breach.

Step 1: Policy & Procedure Review Considerations • Determine “reasonable and appropriate” measures to implement • Conduct a comprehensive Risk Assessment • Risk vs. Likelihood • Additional Considerations: • Technical infrastructure • Software capabilities • Staffing and expertise

Step 1: Policy & Procedure Review Considerations • Effective and Enforceable • Include Process to Routinely Review • Remember the Real Goal – Promote Culture

Step 2 Auditing

Step 2: Auditing Know Your Data • Use Risk Assessment results to determine what systems need to be routinely audited • What systems are within scope • What is the overall risk of each system • What audit tools/features are available

Step 2: Auditing Know Your Users • Do you know who is using these systems? (Accountability) • What details do you have on each system user (Identity Management) • Consider Non-employees, Physicians, Contractors, and Students • Have you documented what each user or role should have access to?

Step 2: Auditing Develop a Sustainable Program • • Who is responsible? Scope of Audits Frequency of Audits Procedures for investigation, escalation, and follow-up Example — Weekly proactive auditing program with procedures for investigation of complaints or issues related to known security incidents.

Step 2: Auditing Proactive Auditing – What To Look For • Known relationships • Neighbor, Coworker, Relative, Roommate, etc. • Suspicious Access Volumes • Number of Logs Generated • Number of Unique Patients Accessed • Irregular Behaviors • Suspicious screens or events for a specific job title. (Registrar Accessing Clinical Notes/Orders)

Step 2: Auditing Consider Audit Solutions A comprehensive audit solution can help save a lot of time by consolidating systems and helping to automate detection of suspicious activity

Step 3 Documentation

Step 3: Documentation Types of documentation Incident documentation This documentation should provide details of every investigated incident. May also include investigations that resulted in no inappropriate actions. Breach Risk Assessment This is used to determine if a confirmed incident is an actionable breach Breach Documentation Specifically included those incidents that identified a reportable breach Documentation of Breach notification actions Record when were required notifications were provided.

Step 3: Documentation Document considerations • Capture additional information that could benefit later review • How the incident was identified? • Details about the user — Job Title, Department, Hire Date, and Shift • Relationship between user and patient

Step 4 Research & Trend Analysis

Step 4: Research & Trend Analysis Routine Review documentation over time to identify trends in data

Step 4: Research & Trend Analysis Predict Future Incidents Who Patterns in Job Title, Role, Age Group, Experience, Hire Date, etc. What parts of chart are viewed, or what data is typically accessed as a part of an inappropriate event When Most common times when incidents occur Where Facilities, departments, workstations, or remote workplaces that have the most incidents Why Determine motives – Snooping, Bored, Names in Media, Local VIPs/Celebrities, Information harvesting, malicious intent How What systems are they using? What path do they take? Do they take precautions to minimize their risk? Do they bypass securities? Are they exploiting a particular feature or function?

Step 5 Corrective Action

Step 5: Corrective Action Sanctions An effective and consistent sanction policy should be a priority

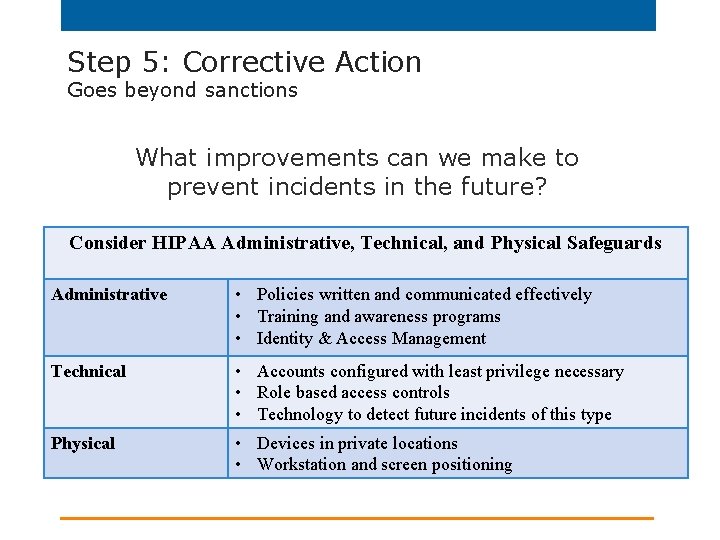
Step 5: Corrective Action Goes beyond sanctions What improvements can we make to prevent incidents in the future? Consider HIPAA Administrative, Technical, and Physical Safeguards Administrative • Policies written and communicated effectively • Training and awareness programs • Identity & Access Management Technical • Accounts configured with least privilege necessary • Role based access controls • Technology to detect future incidents of this type Physical • Devices in private locations • Workstation and screen positioning

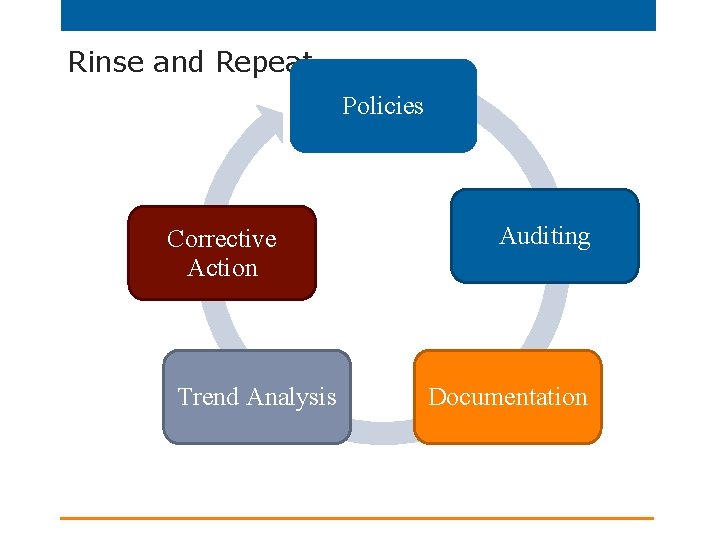
Rinse and Repeat Policies Corrective Action Trend Analysis Auditing Documentation

Questions & Discussion

Takeaways 1. Strategy to tie Policies and Procedures to an effective, continuous process to improve your organizations Privacy Culture 2. Tips for building a successful proactive auditing and documentation program 3. An approach to routinely analyze incidents for patterns so that future incidents can be prevented through realistic corrective action measures