The Parkerian Hexad CSH 6 Chapter 3 Toward













- Slides: 18

The Parkerian Hexad CSH 6 Chapter 3 “Toward a New Framework for Information Security” Donn B. Parker 1 Copyright © 2019 M. E. Kabay. All rights reserved.

Topics Ø The Classic Triad Ø Parkerian Hexad q. Confidentiality q. Possession q. Integrity q. Authenticity q. Availability q. Utility Ø Functions of INFOSEC Personnel 2 Copyright © 2019 M. E. Kabay. All rights reserved. CSH 6 Ch 3

The Classic Triad C–I–A 3 Copyright © 2019 M. E. Kabay. All rights reserved.

The Parkerian Hexad Protect the 6 atomic elements of INFOSEC: Ø Confidentiality Ø Possession or control Ø Integrity Ø Authenticity Ø Availability Ø Utility 4 Copyright © 2019 M. E. Kabay. All rights reserved.

Why “Parkerian? ” 5 Copyright © 2019 M. E. Kabay. All rights reserved.

Confidentiality Restricting access to data Ø Protecting against unauthorized disclosure of existence of data q. E. g. , allowing industrial spy to deduce nature of clientele by looking at directory names Ø Protecting against unauthorized disclosure of details of data q. E. g. , allowing 13 -yr old girl to examine HIV+ records in Florida clinic 6 Copyright © 2019 M. E. Kabay. All rights reserved.

Possession Control over information Ø Preventing physical contact with data q. E. g. , case of thief who recorded ATM PINs by radio (but never looked at them) Ø Preventing copying or unauthorized use of intellectual property q. E. g. , violations by software pirates 7 Copyright © 2019 M. E. Kabay. All rights reserved.

Confidentiality & Possession Losses Ø Ø Ø Ø Ø Locating Disclosing Observing, monitoring, and acquiring Copying Taking or controlling Claiming ownership or custodianship Inferring Exposing to all of the other losses Endangering by exposing to any of the other losses Ø Failure to engage in or to allow any of the other losses to occur when instructed to do so 8 Copyright © 2019 M. E. Kabay. All rights reserved.

Integrity Internal consistency, validity, fitness for use Ø Avoiding physical corruption q. E. g. , database pointers trashed or data garbled Ø Avoiding logical corruption q. E. g. , inconsistencies between order header total sale & sum of costs of details 9 Copyright © 2019 M. E. Kabay. All rights reserved.

Authenticity Correspondence to intended meaning Ø Avoiding nonsense q. E. g. , part number field actually contains cost Ø Avoiding fraud q. E. g. , sender’s name on e-mail is changed to someone else’s 10 Copyright © 2019 M. E. Kabay. All rights reserved.

Integrity & Authenticity Losses Ø Insertion, use, or production of false or unacceptable data Ø Modification, replacement, removal, appending, aggregating, separating, or reordering Ø Misrepresentation Ø Repudiation (rejecting as untrue) Ø Misuse or failure to use as required 11 Copyright © 2019 M. E. Kabay. All rights reserved.

Availability Ø Timely access to data q. Contextual q. No absolutes q. Depends on needs & expectations Ø Delays can cause problems q. Losses due to decreasing value of information (e. g. , stock trading) q. Medical informatics – dangers q. Critical infrastructure – SCADA q. Ordering supplies q. Taking orders 12 Copyright © 2019 M. E. Kabay. All rights reserved.

Utility Usefulness for specific purposes Ø Avoid conversion to less useful form q. E. g. , replacing dollar amounts by foreign currency equivalent q. Using inconsistent metrics (e. g. , meters instead of yards without documentation) q. Printing information in wrong font; e. g. , Cyrillic instead of Roman Ø Prevent impenetrable transforms q. E. g. , employee encrypts source code and loses decryption key 13 Copyright © 2019 M. E. Kabay. All rights reserved.

Availability & Utility Losses Ø Destruction , damage, or contamination Ø Denial, prolongation, acceleration, or delay in use or acquisition Ø Movement or misplacement Ø Conversion or obscuration 14 Copyright © 2019 M. E. Kabay. All rights reserved.

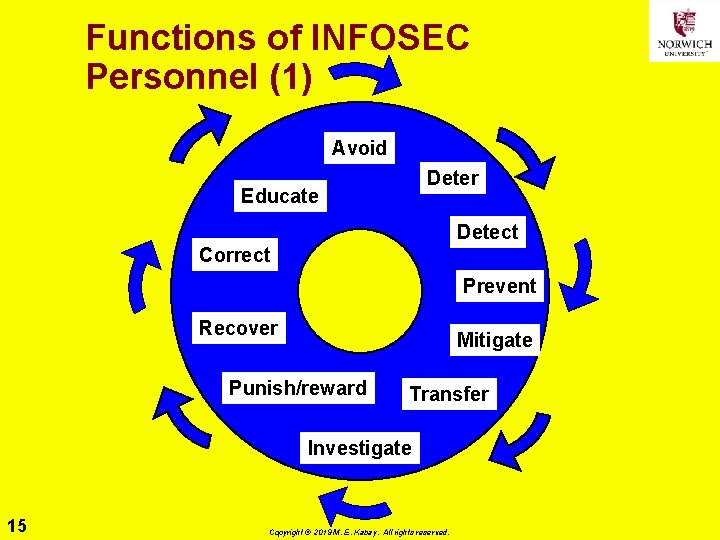
Functions of INFOSEC Personnel (1) Avoid Deter Educate Detect Correct Prevent Recover Mitigate Punish/reward Transfer Investigate 15 Copyright © 2019 M. E. Kabay. All rights reserved.

Functions of INFOSEC Personnel (2) Ø Avoidance: e. g. , prevent vulnerabilities and exposures Ø Deterrence: make attack less likely Ø Detection: quickly spot attack Ø Prevention: prevent exploit Ø Mitigation: reduce damage Ø Transference: shift control for resolution https: //pbs. twimg. com/media/CTp 2 u. FKUw. A 16 A 2 My 8. jpg Copyright © 2019 M. E. Kabay. All rights reserved.

Functions of INFOSEC Personnel (3) Ø Investigation: characterize incident Ø Sanctions & rewards: punish guilty, encourage effective responders Ø Recovery: immediate response, repair Ø Correction: never again Ø Education: advance knowledge and teach others 17 https: //cloudcomputingfuture. files. wordpress. co m/2014/06/virtustream-when-securitymatters. jpg? w=840 Copyright © 2019 M. E. Kabay. All rights reserved.

Now go and study 18 Copyright © 2019 M. E. Kabay. All rights reserved.