The NET Runtime and IIS Presented by Chris

The. NET Runtime and IIS Presented by Chris Dickey – cdickey. net consulting www. cdickey. net

Topics Installing the. NET runtime n The role of IIS as the application server n. NET Remoting and Web Services n How the. NET runtime works with IIS 5. 0 n Significance of the HTTP Pipeline n Security n Whats coming with IIS 6. 0 n

Installing the. NET Runtime http: //msdn. microsoft. com/netframework/d ownloads/default. asp n Windows Update Service n. NET Runtime n. NET SDK + Runtime n Visual Studio. NET n

IIS is the Application Server Static Pages n ISAPI n ASP. NET n Web Services n Remoting n Connection Point to SQL Server n

ASP. NET Web Pages What most people think of as ASP. NET n Compiled web pages n Huge advance over previous ASP version n Lots of well known features n

Web Services Communication between diverse systems n SOAP packets transported using HTTP and SMTP protocols n Application connectivity protocol n IIS is the client connection point n Takes advantage of the HTTP Runtime n

. NET Remoting Replacement for DCOM n tailored for. NET-to-. NET communications n Can be hosted by ASP. NET runtime n Takes advantage of the HTTP Runtime n

. NET compatibility and interoperability ASP. NET coexists with IIS 5. 0 and ASP n Runs in a separate process n Doesn’t use the registry n Routed through IIS ISAPI n Can’t share sessions – 2 separate systems n
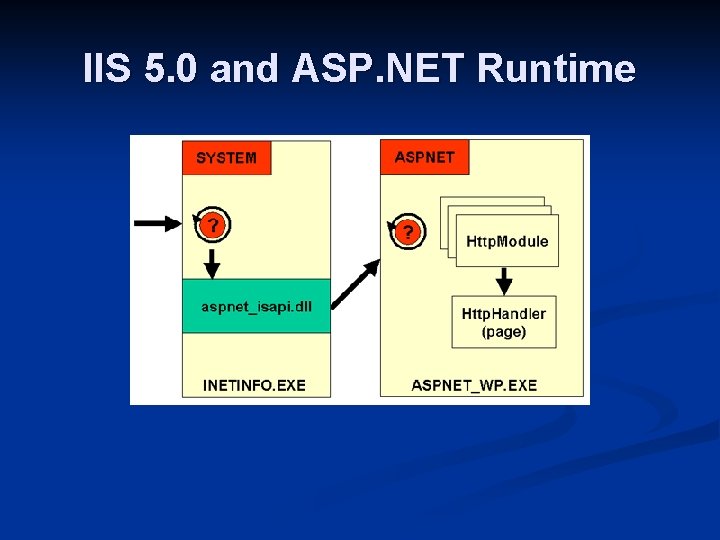
IIS 5. 0 and ASP. NET Runtime
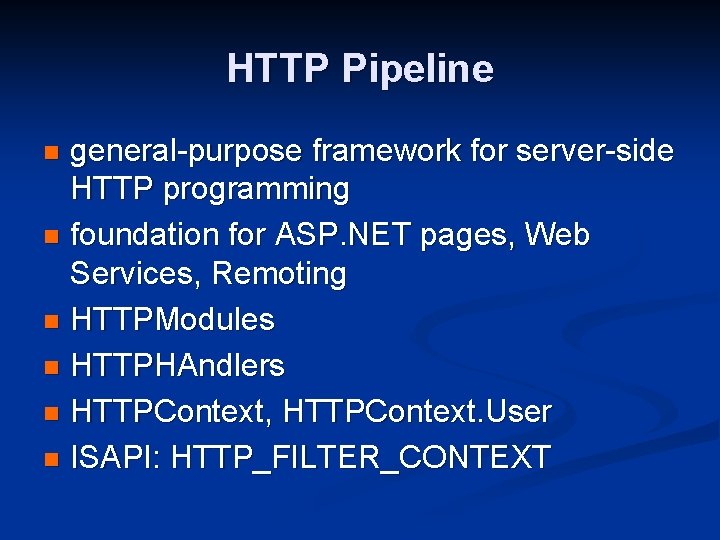
HTTP Pipeline general-purpose framework for server-side HTTP programming n foundation for ASP. NET pages, Web Services, Remoting n HTTPModules n HTTPHAndlers n HTTPContext, HTTPContext. User n ISAPI: HTTP_FILTER_CONTEXT n
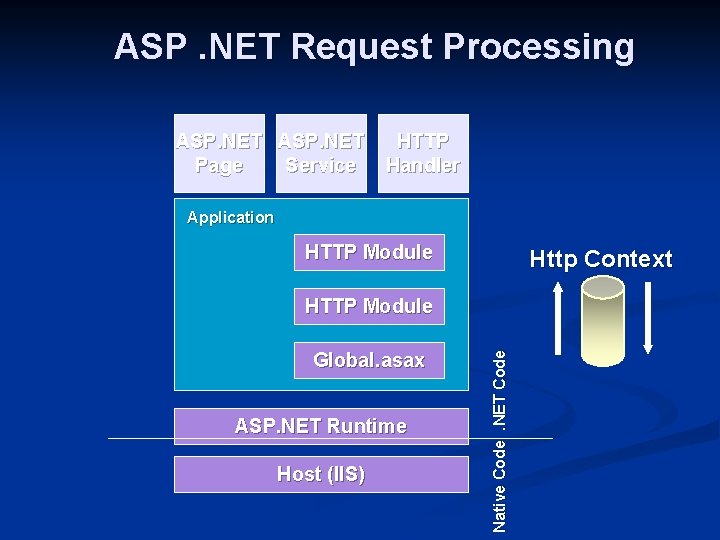
ASP. NET Request Processing ASP. NET Page Service HTTP Handler Application HTTP Module Http Context Global. asax ASP. NET Runtime Host (IIS) Native Code. NET Code HTTP Module
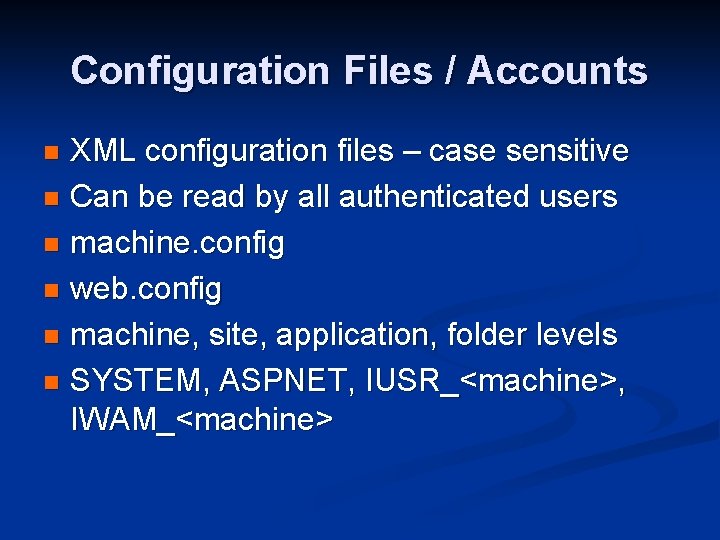
Configuration Files / Accounts XML configuration files – case sensitive n Can be read by all authenticated users n machine. config n web. config n machine, site, application, folder levels n SYSTEM, ASPNET, IUSR_<machine>, IWAM_<machine> n

Demo Run. net app – HTTPHandler n Show IIS 5. 0 config n Show aspnet_wp. exe process – only 1 n *. config files n

Security Services n ASP. NET support for authentication and authorization n Extensible and customizable Authentication scheme transparency Simple deployment model Support for granular declarative and imperative authorizations n Uses CLR Evidence-Based Security n Supports application layer security n
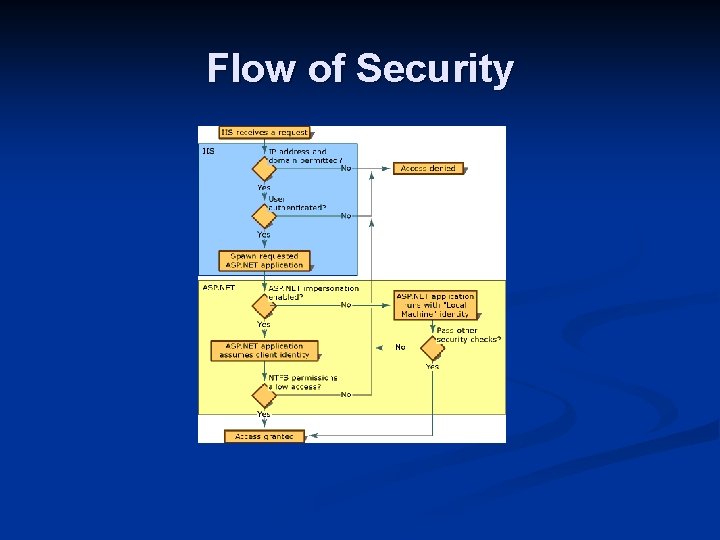
Flow of Security

Process Identity n Windows® 2000: Default is ASPNET n n Can also run with SYSTEM account or configured account using <process. Model> Windows. NET Server n n n Uses IIS 6 process model Default is Network. Service App Pools are configurable, identity is configurable

HTTP Pipeline

Authentication n ASP. NET is an ISAPI extension n n Windows Authentication (via IIS) n n n Basic, Digest, NTLM, Kerberos, IIS Certificate Support Forms-based (Cookie) Authentication n n Only receives requests for mapped content Application credential verification Supports Microsoft® Passport Authentication Custom Authentication
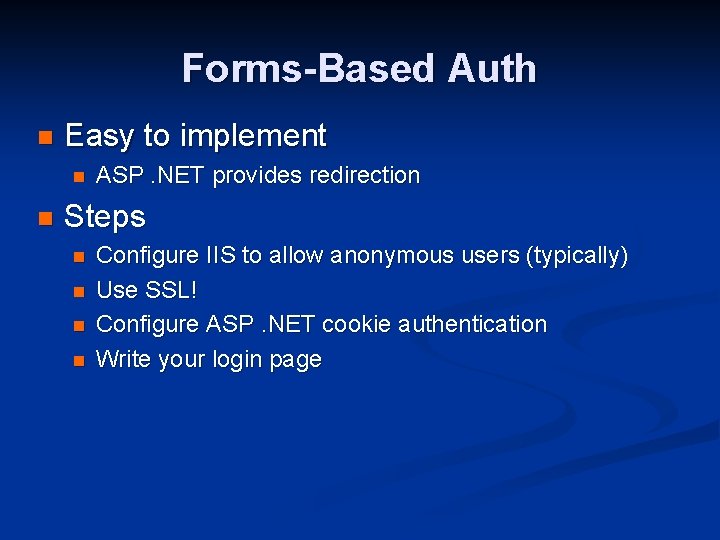
Forms-Based Auth n Easy to implement n n ASP. NET provides redirection Steps n n Configure IIS to allow anonymous users (typically) Use SSL! Configure ASP. NET cookie authentication Write your login page
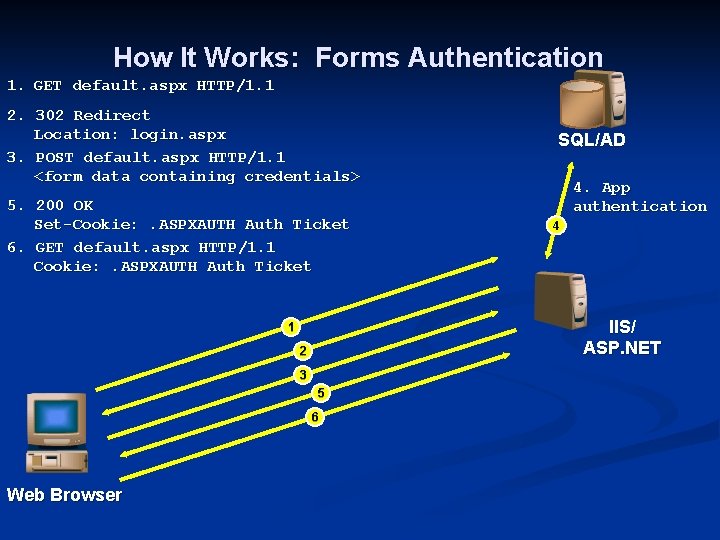
How It Works: Forms Authentication 1. GET default. aspx HTTP/1. 1 2. 302 Redirect Location: login. aspx 3. POST default. aspx HTTP/1. 1 <form data containing credentials> 5. 200 OK Set-Cookie: . ASPXAUTH Auth Ticket 6. GET default. aspx HTTP/1. 1 Cookie: . ASPXAUTH Auth Ticket 4. App authentication 4 IIS/ ASP. NET 1 2 3 5 6 Web Browser SQL/AD

Custom Web Authentication n Handle Authenticate. Request event n n n Application level (global. asax) or Http Module (implement IHttp. Module) Scenarios: n n n Custom SOAP authentication n E. g. , application defined scheme based on SOAP headers Forms authentication for mobile devices without cookies Customize forms authentication

Authorization Strategies n Windows Security and ACLs n n ACLs checked for Windows auth Independent of impersonation COM+ Roles n URL Authorization n Custom Authorization n Windows. NET Auth. Z Framework n Explicit imperative/declarative checks n
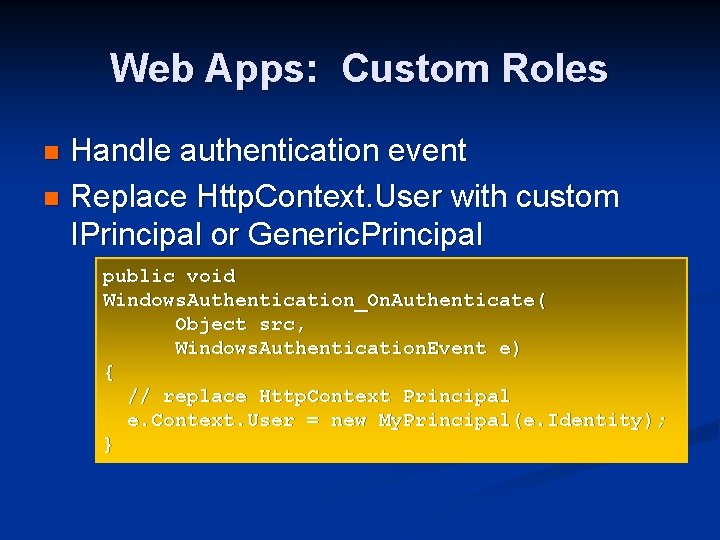
Web Apps: Custom Roles Handle authentication event n Replace Http. Context. User with custom IPrincipal or Generic. Principal n public void Windows. Authentication_On. Authenticate( Object src, Windows. Authentication. Event e) { // replace Http. Context Principal e. Context. User = new My. Principal(e. Identity); }
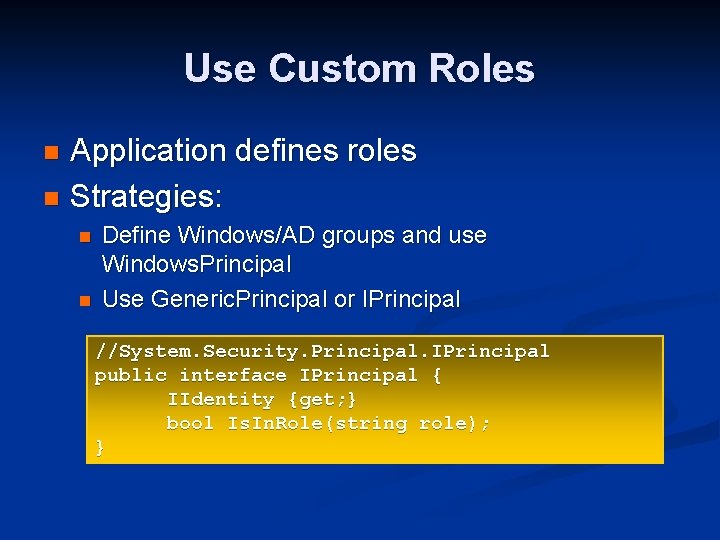
Use Custom Roles Application defines roles n Strategies: n n n Define Windows/AD groups and use Windows. Principal Use Generic. Principal or IPrincipal //System. Security. Principal. IPrincipal public interface IPrincipal { IIdentity {get; } bool Is. In. Role(string role); }

Custom Web Authorization n Handle Authorize. Request event n n n Application level (global. asax) or Http Module (implement IHttp. Module) Scenarios: n n n Implement per-request billing system Restrict access based on business rules Restrict access based on dynamic behaviors (e. g. , implement a per-day access limit, etc).

Internet Information Services 6 Complete rearchitecture n Kernel-mode HTTP n Web server security lockdown wizard n Worker process application pools n
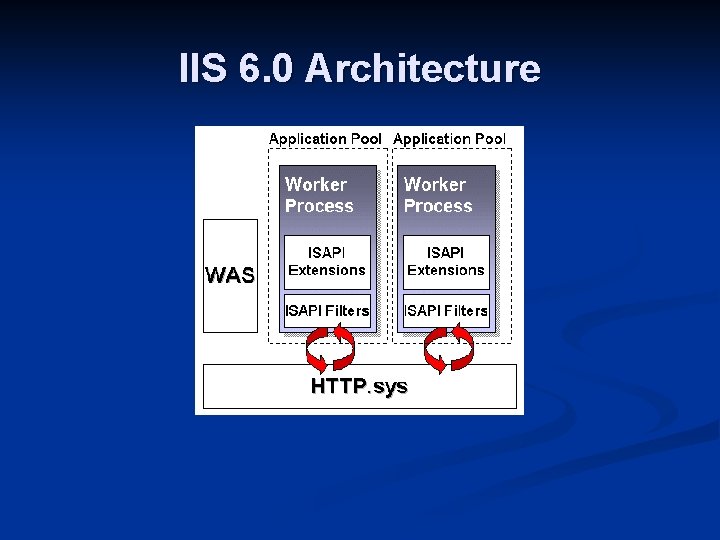
IIS 6. 0 Architecture
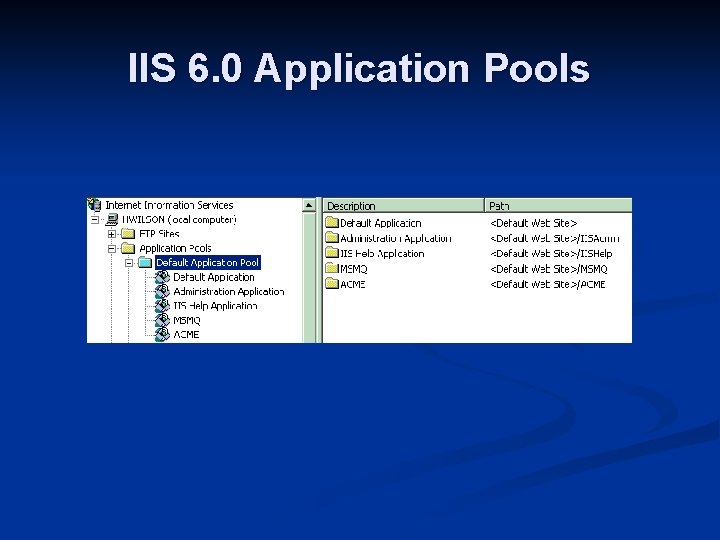
IIS 6. 0 Application Pools
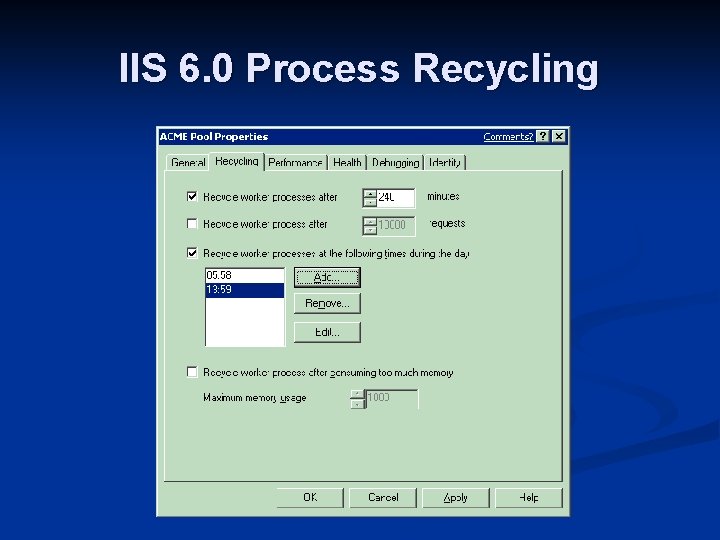
IIS 6. 0 Process Recycling

References n n n MSDN Magazine - September 2002 www. Windows. Web. Solutions. com Keith Brown - portals. devx. com/Summit. Days/Article/6666 Tim Ewald msdn. microsoft. com/msdnmag/issues/02/09/HTTPPipeline s/default. aspx Technical Overview of IIS 6. 0 www. microsoft. com/windows. netserver/techinfo/overview/ii s. mspx Windows. NET Server Devcon www. microsoft. com/misc/external/serverdevcon/
- Slides: 30