The Modern SIEM Key considerations in selecting the








- Slides: 16

The Modern SIEM Key considerations in selecting the platform for the Modern Security Operations Center JESSICA COUTO VP WW Channels Copyright © 2019 JASK

SOC (Security Operations “Capability”) • • Network Analysts • Their job is to find the “bad” and “fix it” − Packet inspection − Identified attacks − Incidents − Investigate Copyright © 2019 JASK System Administrators Software developers Analysts – Level 1, 2 and 3 2

SOC The job of a SOC team is to not stop the instance of an attack; but instead helping to define how to stop whole classes of attacks. SOC analysts spend countless mind numbing man hours reading logs trying to find indicators of an attack or chasing down commodity malware instances. BORING! SOC teams need to figure out a way significantly reduce busy work and focus on the larger scale patterns to be effective Copyright © 2019 JASK 3

Costs for a SOC • • • SOC level 1 - $78, 173* SOC level 3 – 114, 721* SOC level 2 - $96, 477 (avg) • For a 24 X 7 SOC operation you need 10 minimum; but more in the range of 30 for large enterprises The Optimal events per analyst hour (EPAH) should be 8 -12 How many alerts do you have per day • Salary estimated from 21, 105 employees, users, and past and present job advertisements on Indeed in the past 36 months. Last updated: February 18, 2019 - https: //www. indeed. com/salaries/Soc-Analyst-Salaries Copyright © 2019 JASK 4

Scenario 1 10 Analysts (6 level 1, 2 level 2, 2 level 3) • Total Salary = $891, 434 • 8 hour days person at 10 events per hour = 80 − 6 SOC level 1 Analysts * 80 events = 480 events per day • BUT----You are currently receiving 2000 events per day! Copyright © 2019 JASK 5

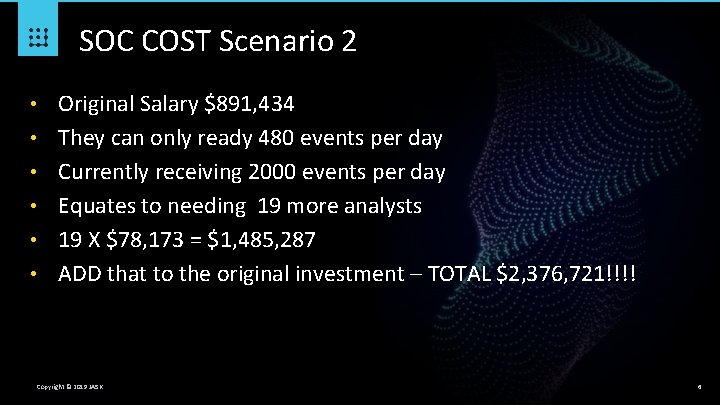
SOC COST Scenario 2 • • • Original Salary $891, 434 They can only ready 480 events per day Currently receiving 2000 events per day Equates to needing 19 more analysts 19 X $78, 173 = $1, 485, 287 ADD that to the original investment – TOTAL $2, 376, 721!!!! Copyright © 2019 JASK 6

Quick Survey How many people think that is the right approach? • Who has unlimited staffing budget? • What if you need to ingest more data– do you keep hiring? • How many think this way is the best approach? • • Are there any other alternatives? Copyright © 2019 JASK 7

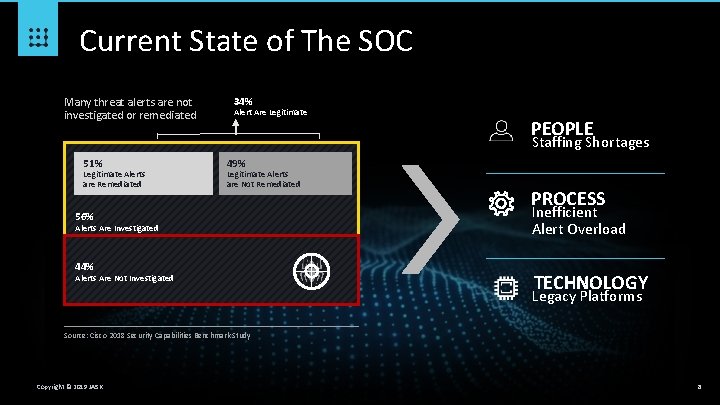
Current State of The SOC Many threat alerts are not investigated or remediated 34% Alert Are Legitimate PEOPLE Staffing Shortages 51% Legitimate Alerts are Remediated 49% Legitimate Alerts are Not Remediated 56% Alerts Are Investigated 44% Alerts Are Not Investigated PROCESS Inefficient Alert Overload TECHNOLOGY Legacy Platforms Source: Cisco 2018 Security Capabilities Benchmark Study Copyright © 2019 JASK 8

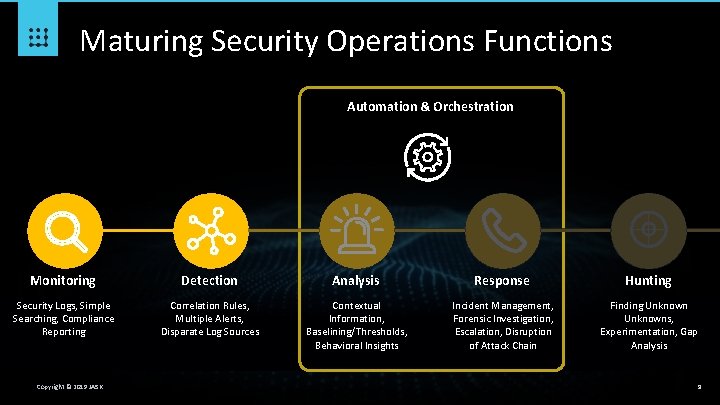
Maturing Security Operations Functions Automation & Orchestration Monitoring Detection Analysis Response Hunting Security Logs, Simple Searching, Compliance Reporting Correlation Rules, Multiple Alerts, Disparate Log Sources Contextual Information, Baselining/Thresholds, Behavioral Insights Incident Management, Forensic Investigation, Escalation, Disruption of Attack Chain Finding Unknowns, Experimentation, Gap Analysis Copyright © 2019 JASK 9

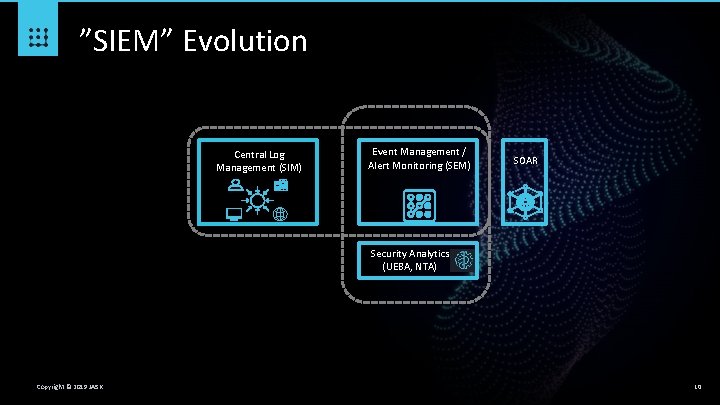
”SIEM” Evolution Central Log Management (SIM) Event Management / Alert Monitoring (SEM) SOAR Security Analytics (UEBA, NTA) Copyright © 2019 JASK 10

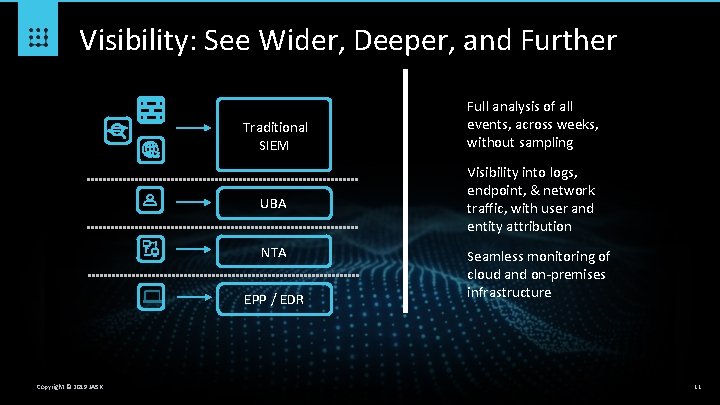
Visibility: See Wider, Deeper, and Further Traditional SIEM UBA NTA EPP / EDR Copyright © 2019 JASK Full analysis of all events, across weeks, without sampling Visibility into logs, endpoint, & network traffic, with user and entity attribution Seamless monitoring of cloud and on-premises infrastructure 11

The Move to Cloud: Pets vs Cattle • Public cloud computing presents an incredible opportunity for businesses with the knowledge and experience to effectively take advantage of the services AND the cost savings. With the right knowledge, a properly architected system can be a MORE secure environment in public cloud than a traditional on-premises infrastructure. • However, security monitoring of the cloud is challenging due to the paradigm shift in building cloud-native applications. Traditional SIEM tools were designed to ingest the core on-premises security solutions: firewalls, IDS/IPS, proxies, etc. These SIEMs don’t understand cloud data, where workloads may come and go within hours. The methodologies that powered the SIEMs to analyze on-premises data streams simply don’t apply to cloud data. Copyright © 2019 JASK 12

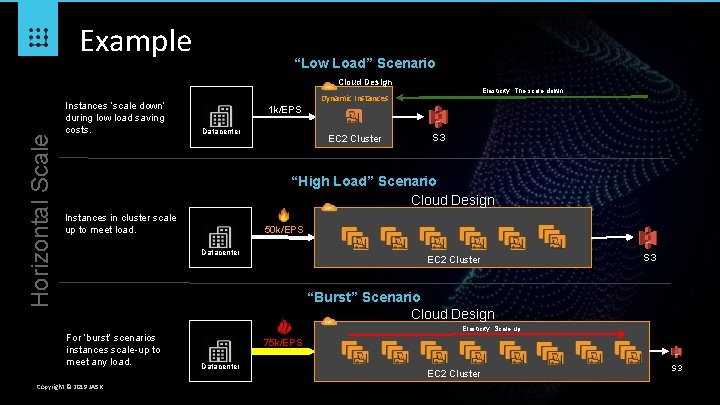
Example “Low Load” Scenario Horizontal Scale Cloud Design Instances ‘scale down’ during low load saving costs. 1 k/EPS Datacenter Elasticity: The scale down Dynamic Instances EC 2 Cluster S 3 “High Load” Scenario Cloud Design Scale up Instances in cluster scale up to meet load. 50 k/EPS Datacenter EC 2 Cluster S 3 “Burst” Scenario Cloud Design Elasticity: Scale up For ‘burst’ scenarios instances scale-up to meet any load. Copyright © 2019 JASK 75 k/EPS Datacenter EC 2 Cluster S 3

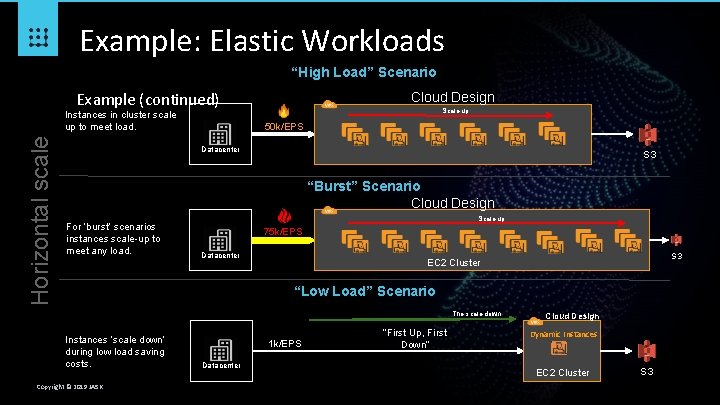
Example: Elastic Workloads “High Load” Scenario Example (continued) Horizontal scale Instances in cluster scale up to meet load. Cloud Design Scale up 50 k/EPS Datacenter S 3 EC 2 Cluster “Burst” Scenario Cloud Design For ‘burst’ scenarios instances scale-up to meet any load. Scale up 75 k/EPS Datacenter S 3 EC 2 Cluster “Low Load” Scenario The scale down Instances ‘scale down’ during low load saving costs. Copyright © 2019 JASK 1 k/EPS Datacenter “First Up, First Down” Cloud Design Dynamic Instances EC 2 Cluster S 3

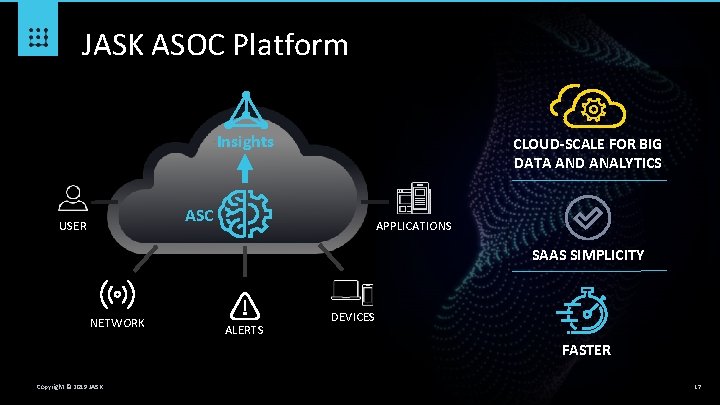
JASK ASOC Platform Insights CLOUD-SCALE FOR BIG DATA AND ANALYTICS ASC USER APPLICATIONS SAAS SIMPLICITY NETWORK ALERTS DEVICES FASTER Copyright © 2019 JASK 17

The future of cybersecurity will depend on AI. Because Humans are the best cyber-defenders we have. Copyright © 2019 JASK 18