The Memory Hierarchy CENG 331 Introduction to Computer






![A Higher Level Example int sum_array_rows(double a[16]) { int i, j; double sum = A Higher Level Example int sum_array_rows(double a[16]) { int i, j; double sum =](https://slidetodoc.com/presentation_image_h/2cbb9f24cb5e6f207b481c8468877a27/image-79.jpg)



- Slides: 111

The Memory Hierarchy CENG 331: Introduction to Computer Systems 10 th Lecture Instructor: Erol Sahin Acknowledgement: Most of the slides are adapted from the ones prepared by R. E. Bryant, D. R. O’Hallaron of Carnegie-Mellon Univ.

Overview Topics n n n Storage technologies and trends Locality of reference Caching in the memory hierarchy – 2–

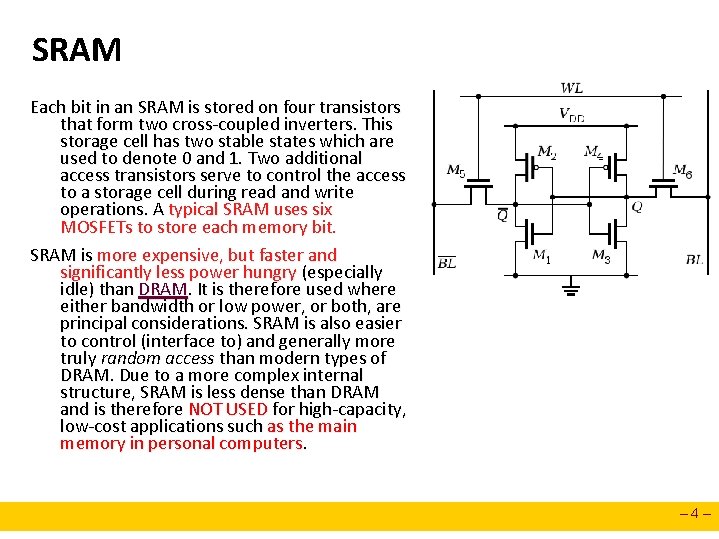
Random-Access Memory (RAM) Key features n n n RAM is packaged as a chip. Basic storage unit is a cell (one bit per cell). Multiple RAM chips form a memory. Static RAM (SRAM) n n Each cell stores bit with a six-transistor circuit. Retains value indefinitely, as long as it is kept powered. Relatively insensitive to disturbances such as electrical noise. Faster and more expensive than DRAM. Dynamic RAM (DRAM) n n Each cell stores bit with a capacitor and transistor. Value must be refreshed every 10 -100 ms. Sensitive to disturbances. Slower and cheaper than SRAM. – 3–

SRAM Each bit in an SRAM is stored on four transistors that form two cross-coupled inverters. This storage cell has two stable states which are used to denote 0 and 1. Two additional access transistors serve to control the access to a storage cell during read and write operations. A typical SRAM uses six MOSFETs to store each memory bit. SRAM is more expensive, but faster and significantly less power hungry (especially idle) than DRAM. It is therefore used where either bandwidth or low power, or both, are principal considerations. SRAM is also easier to control (interface to) and generally more truly random access than modern types of DRAM. Due to a more complex internal structure, SRAM is less dense than DRAM and is therefore NOT USED for high-capacity, low-cost applications such as the main memory in personal computers. – 4–

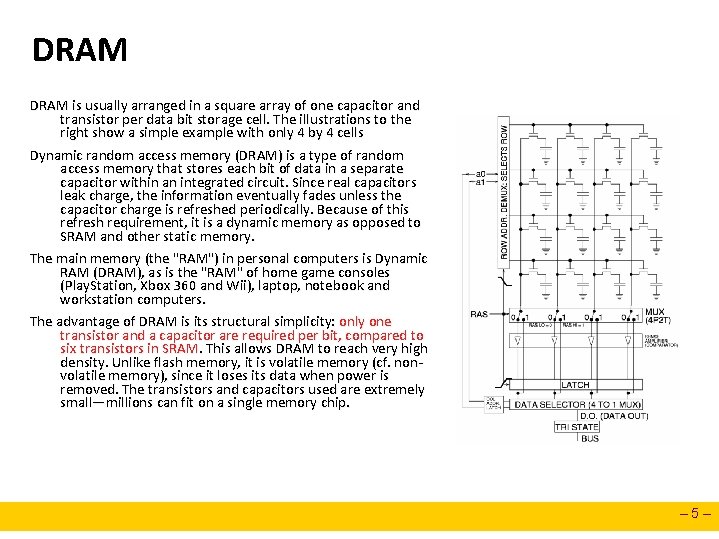
DRAM is usually arranged in a square array of one capacitor and transistor per data bit storage cell. The illustrations to the right show a simple example with only 4 by 4 cells Dynamic random access memory (DRAM) is a type of random access memory that stores each bit of data in a separate capacitor within an integrated circuit. Since real capacitors leak charge, the information eventually fades unless the capacitor charge is refreshed periodically. Because of this refresh requirement, it is a dynamic memory as opposed to SRAM and other static memory. The main memory (the "RAM") in personal computers is Dynamic RAM (DRAM), as is the "RAM" of home game consoles (Play. Station, Xbox 360 and Wii), laptop, notebook and workstation computers. The advantage of DRAM is its structural simplicity: only one transistor and a capacitor are required per bit, compared to six transistors in SRAM. This allows DRAM to reach very high density. Unlike flash memory, it is volatile memory (cf. nonvolatile memory), since it loses its data when power is removed. The transistors and capacitors used are extremely small—millions can fit on a single memory chip. – 5–

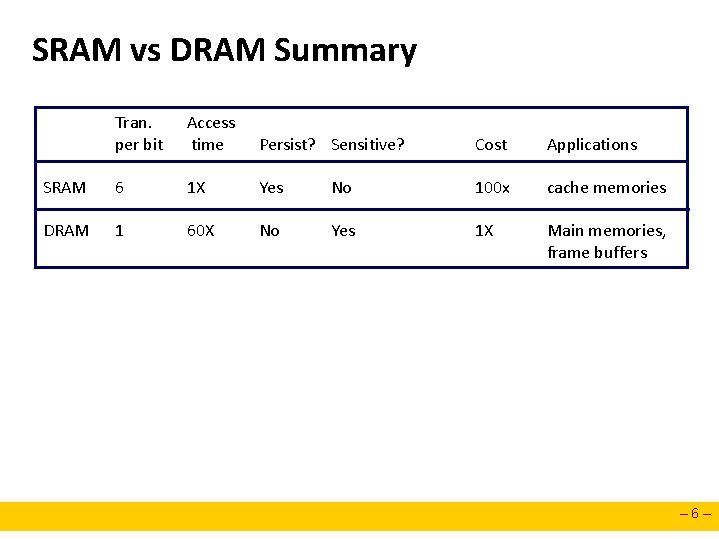
SRAM vs DRAM Summary Tran. per bit Access time Persist? Sensitive? Cost Applications SRAM 6 1 X Yes No 100 x cache memories DRAM 1 60 X No Yes 1 X Main memories, frame buffers – 6–

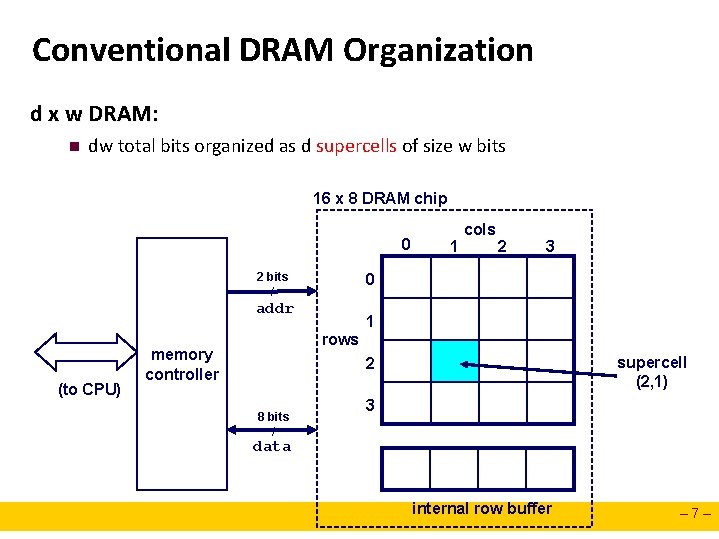
Conventional DRAM Organization d x w DRAM: n dw total bits organized as d supercells of size w bits 16 x 8 DRAM chip 0 2 bits / 2 3 0 addr (to CPU) 1 cols 1 rows memory controller supercell (2, 1) 2 8 bits / 3 data internal row buffer – 7–

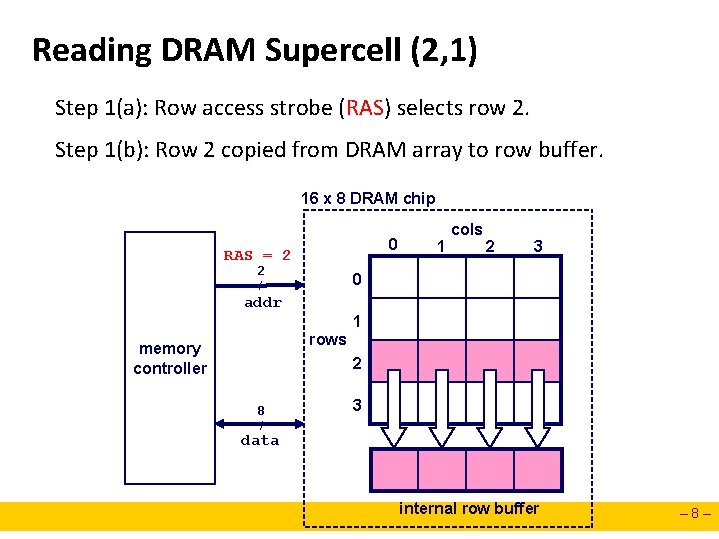
Reading DRAM Supercell (2, 1) Step 1(a): Row access strobe (RAS) selects row 2. Step 1(b): Row 2 copied from DRAM array to row buffer. 16 x 8 DRAM chip 0 RAS = 2 2 / 1 cols 2 3 0 addr 1 rows memory controller 2 8 / 3 data internal row buffer – 8–

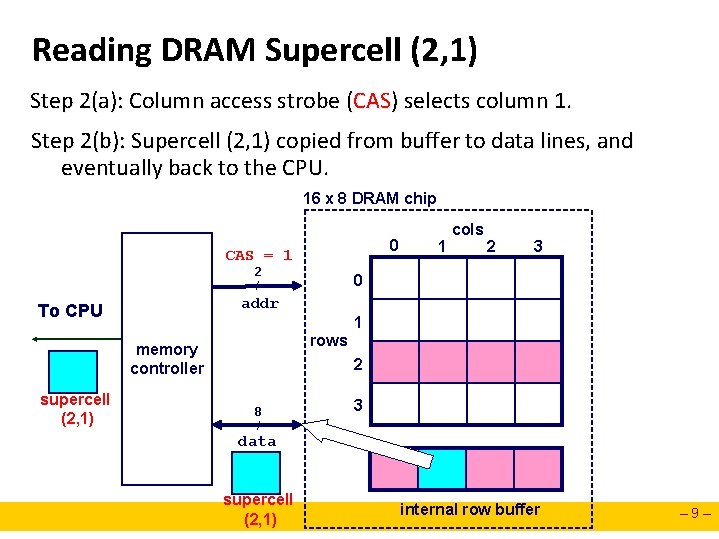
Reading DRAM Supercell (2, 1) Step 2(a): Column access strobe (CAS) selects column 1. Step 2(b): Supercell (2, 1) copied from buffer to data lines, and eventually back to the CPU. 16 x 8 DRAM chip 0 CAS = 1 2 / 2 3 0 addr To CPU 1 rows memory controller supercell (2, 1) 1 cols 2 8 / 3 data supercell (2, 1) internal row buffer – 9–

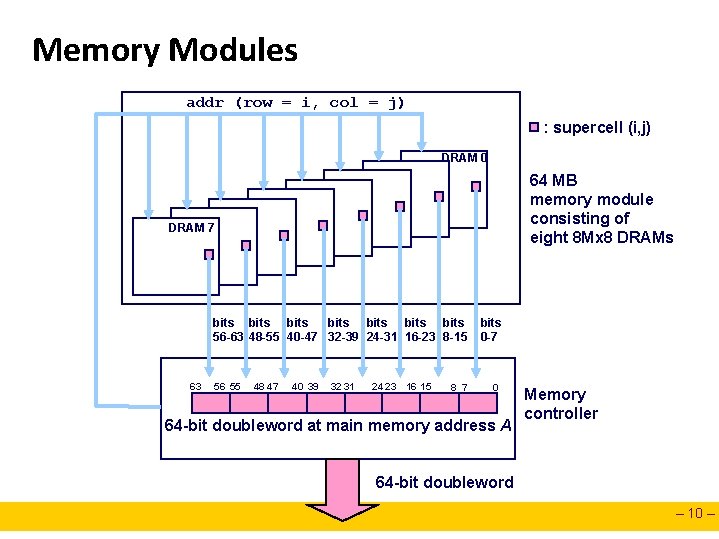
Memory Modules addr (row = i, col = j) : supercell (i, j) DRAM 0 64 MB memory module consisting of eight 8 Mx 8 DRAMs DRAM 7 bits bits 56 -63 48 -55 40 -47 32 -39 24 -31 16 -23 8 -15 63 56 55 48 47 40 39 32 31 24 23 16 15 8 7 bits 0 -7 0 64 -bit doubleword at main memory address A Memory controller 64 -bit doubleword – 10 –

Enhanced DRAMs All enhanced DRAMs are built around the conventional DRAM core. n Fast page mode DRAM (FPM DRAM) l Access contents of row with [RAS, CAS, CAS] instead of [(RAS, CAS), (RAS, CAS)]. n Extended data out DRAM (EDO DRAM) l Enhanced FPM DRAM with more closely spaced CAS signals. n Synchronous DRAM (SDRAM) l Driven with rising clock edge instead of asynchronous control signals. n Double data-rate synchronous DRAM (DDR SDRAM) l Enhancement of SDRAM that uses both clock edges as control signals. n Video RAM (VRAM) l Like FPM DRAM, but output is produced by shifting row buffer l Dual ported (allows concurrent reads and writes) – 11 –

Nonvolatile Memories DRAM and SRAM are volatile memories n Lose information if powered off. Nonvolatile memories retain value even if powered off. n n Generic name is read-only memory (ROM). Misleading because some ROMs can be read and modified. Types of ROMs n n Programmable ROM (PROM) Erasable programmable ROM (EPROM) Electrically erase PROM (EEPROM) Flash memory Firmware n Program stored in a ROM l Boot time code, BIOS (basic input/ouput system) l graphics cards, disk controllers. – 12 –

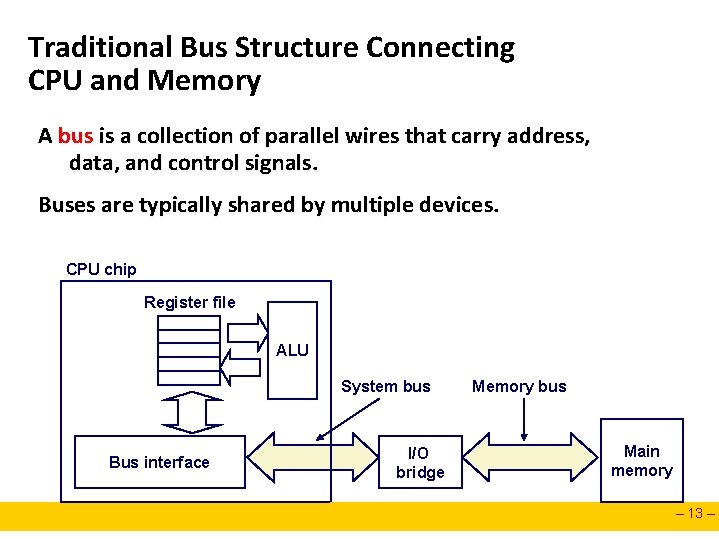
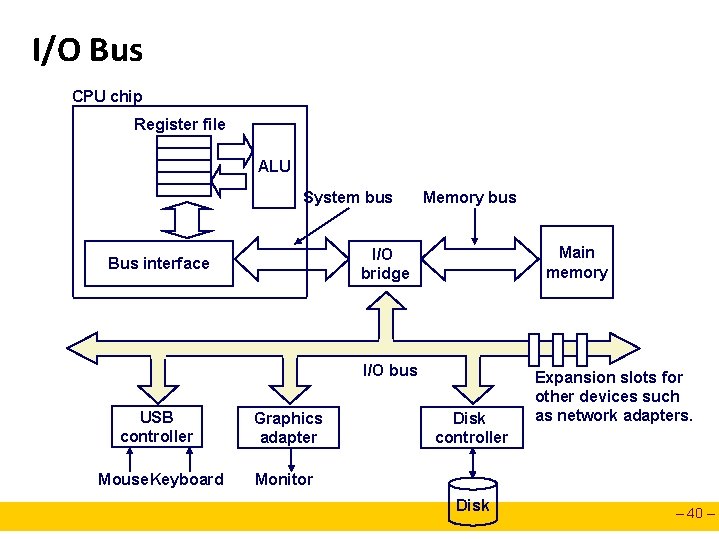
Traditional Bus Structure Connecting CPU and Memory A bus is a collection of parallel wires that carry address, data, and control signals. Buses are typically shared by multiple devices. CPU chip Register file ALU System bus Bus interface I/O bridge Memory bus Main memory – 13 –

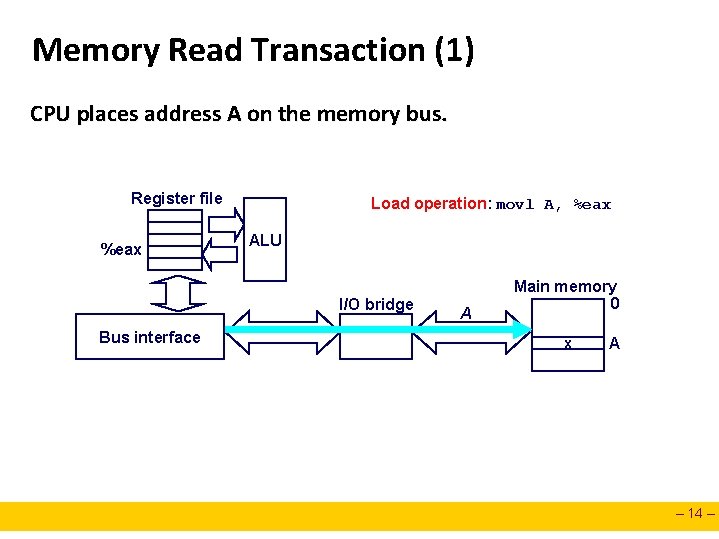
Memory Read Transaction (1) CPU places address A on the memory bus. Register file %eax Load operation: movl A, %eax ALU I/O bridge Bus interface A Main memory 0 x A – 14 –

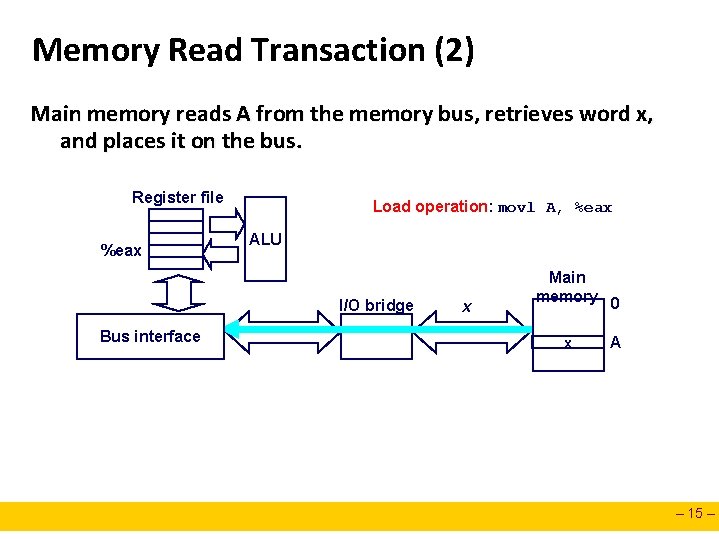
Memory Read Transaction (2) Main memory reads A from the memory bus, retrieves word x, and places it on the bus. Register file %eax Load operation: movl A, %eax ALU I/O bridge Bus interface x Main memory 0 x A – 15 –

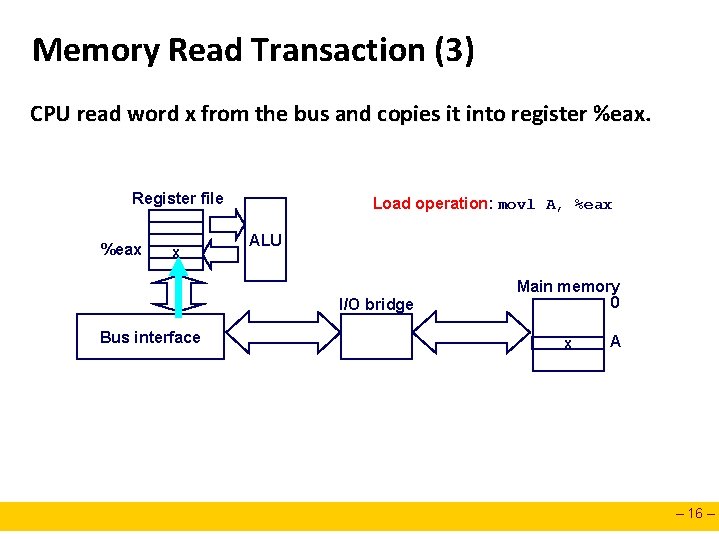
Memory Read Transaction (3) CPU read word x from the bus and copies it into register %eax. Register file %eax x Load operation: movl A, %eax ALU I/O bridge Bus interface Main memory 0 x A – 16 –

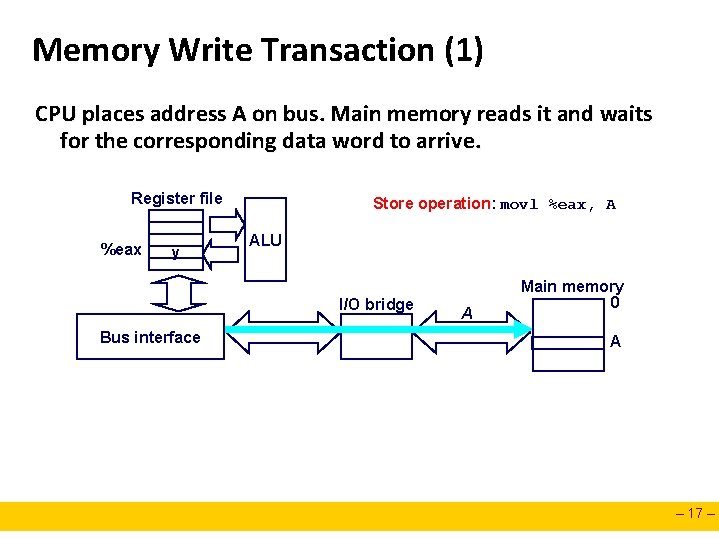
Memory Write Transaction (1) CPU places address A on bus. Main memory reads it and waits for the corresponding data word to arrive. Register file %eax y Store operation: movl %eax, A ALU I/O bridge Bus interface A Main memory 0 A – 17 –

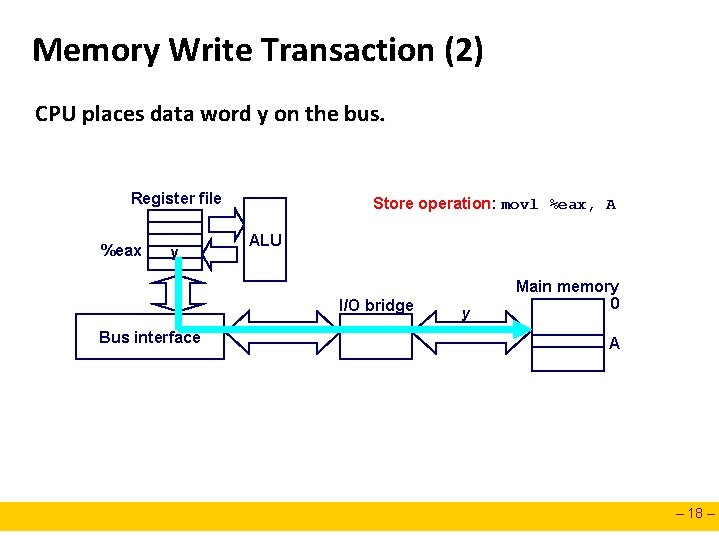
Memory Write Transaction (2) CPU places data word y on the bus. Register file %eax y Store operation: movl %eax, A ALU I/O bridge Bus interface y Main memory 0 A – 18 –

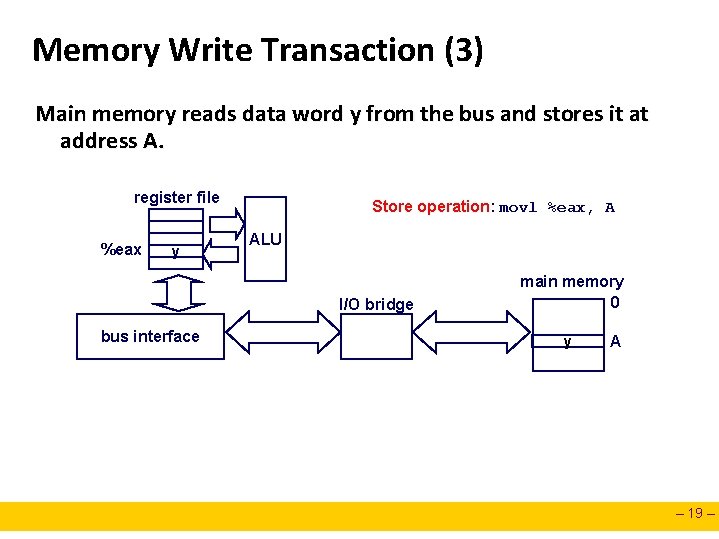
Memory Write Transaction (3) Main memory reads data word y from the bus and stores it at address A. register file %eax y Store operation: movl %eax, A ALU I/O bridge bus interface main memory 0 y A – 19 –

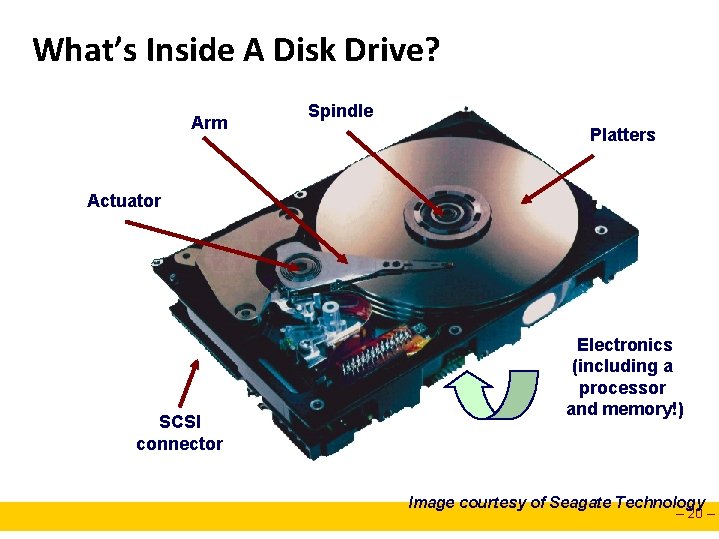
What’s Inside A Disk Drive? Arm Spindle Platters Actuator SCSI connector Electronics (including a processor and memory!) Image courtesy of Seagate Technology – 20 –

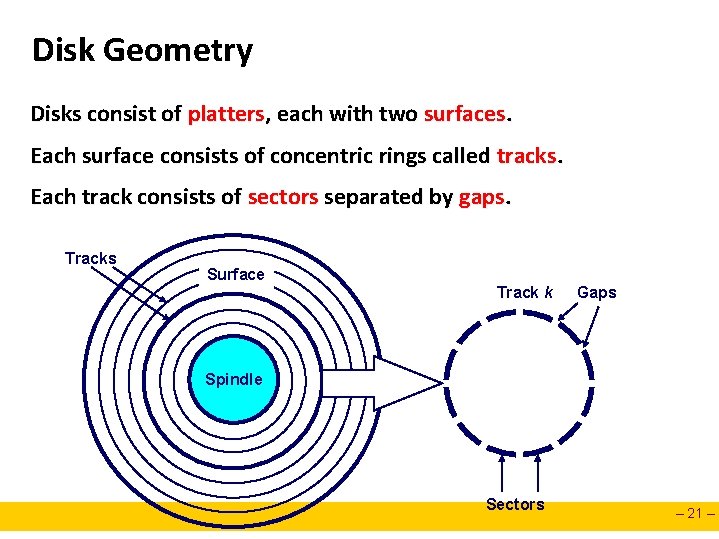
Disk Geometry Disks consist of platters, each with two surfaces. Each surface consists of concentric rings called tracks. Each track consists of sectors separated by gaps. Tracks Surface Track k Gaps Spindle Sectors – 21 –

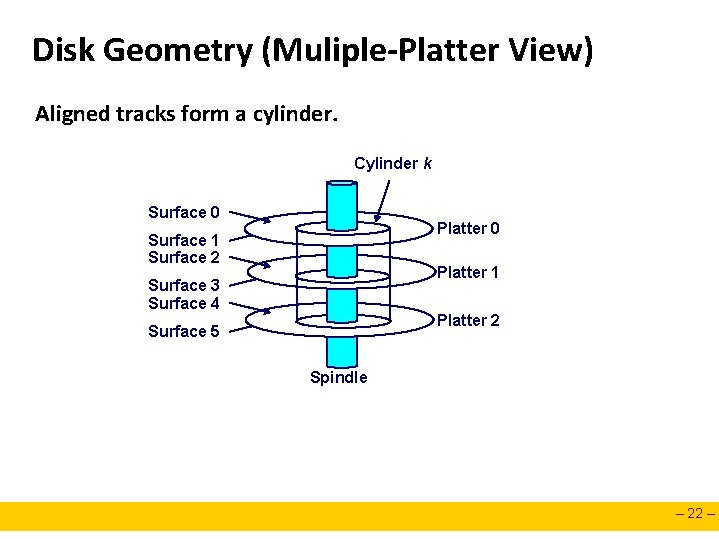
Disk Geometry (Muliple-Platter View) Aligned tracks form a cylinder. Cylinder k Surface 0 Platter 0 Surface 1 Surface 2 Platter 1 Surface 3 Surface 4 Platter 2 Surface 5 Spindle – 22 –

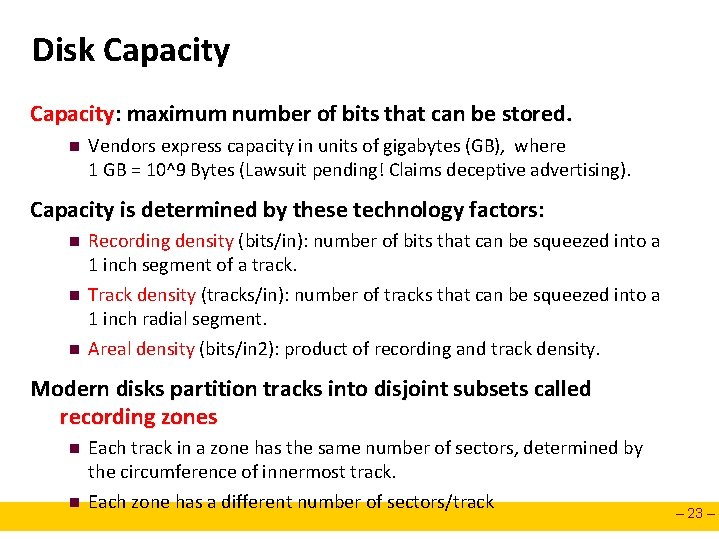
Disk Capacity: maximum number of bits that can be stored. n Vendors express capacity in units of gigabytes (GB), where 1 GB = 10^9 Bytes (Lawsuit pending! Claims deceptive advertising). Capacity is determined by these technology factors: n n n Recording density (bits/in): number of bits that can be squeezed into a 1 inch segment of a track. Track density (tracks/in): number of tracks that can be squeezed into a 1 inch radial segment. Areal density (bits/in 2): product of recording and track density. Modern disks partition tracks into disjoint subsets called recording zones n n Each track in a zone has the same number of sectors, determined by the circumference of innermost track. Each zone has a different number of sectors/track – 23 –

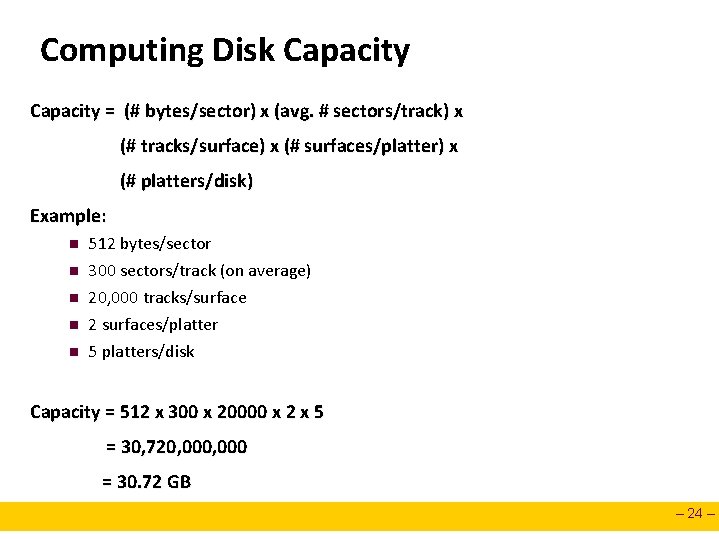
Computing Disk Capacity = (# bytes/sector) x (avg. # sectors/track) x (# tracks/surface) x (# surfaces/platter) x (# platters/disk) Example: n n n 512 bytes/sector 300 sectors/track (on average) 20, 000 tracks/surface 2 surfaces/platter 5 platters/disk Capacity = 512 x 300 x 20000 x 2 x 5 = 30, 720, 000 = 30. 72 GB – 24 –

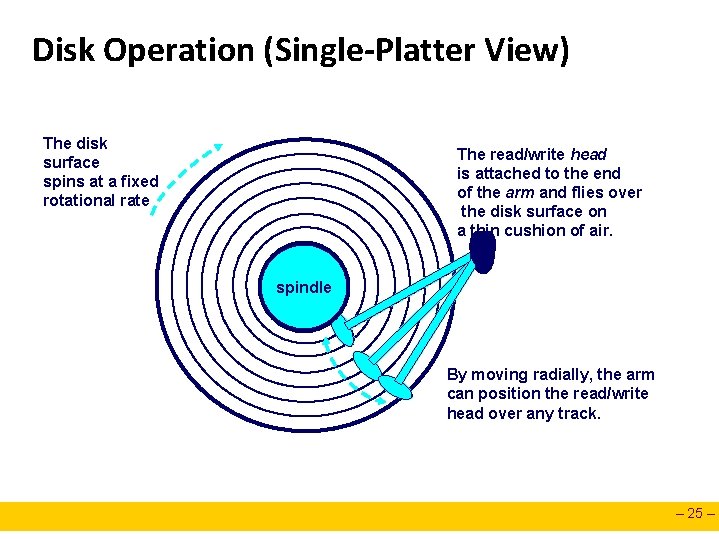
Disk Operation (Single-Platter View) The disk surface spins at a fixed rotational rate The read/write head is attached to the end of the arm and flies over the disk surface on a thin cushion of air. spindle By moving radially, the arm can position the read/write head over any track. – 25 –

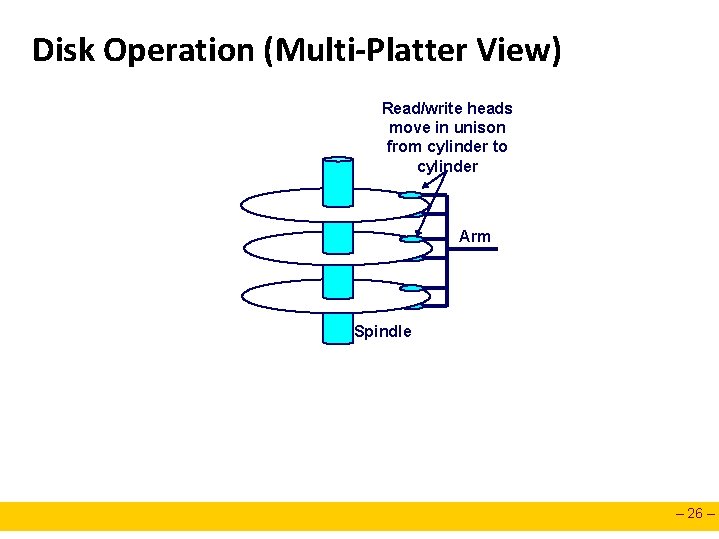
Disk Operation (Multi-Platter View) Read/write heads move in unison from cylinder to cylinder Arm Spindle – 26 –

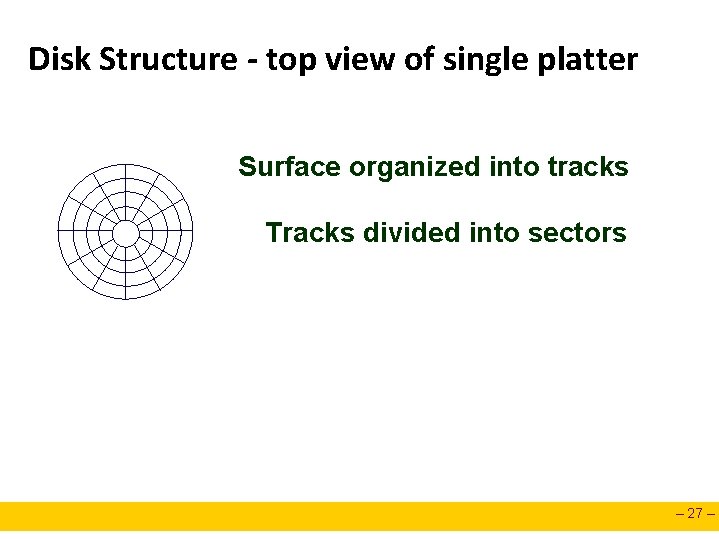
Disk Structure - top view of single platter Surface organized into tracks Tracks divided into sectors – 27 –

Disk Access Head in position above a track – 28 –

Disk Access Rotation is counter-clockwise – 29 –

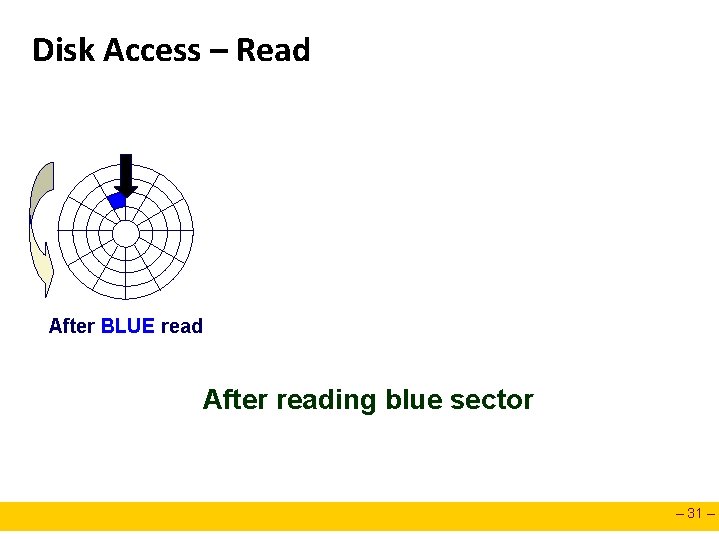
Disk Access – Read About to read blue sector – 30 –

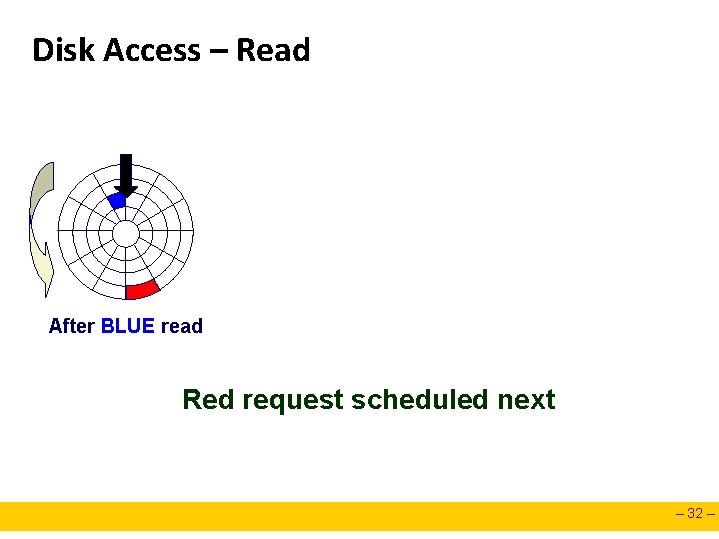
Disk Access – Read After BLUE read After reading blue sector – 31 –

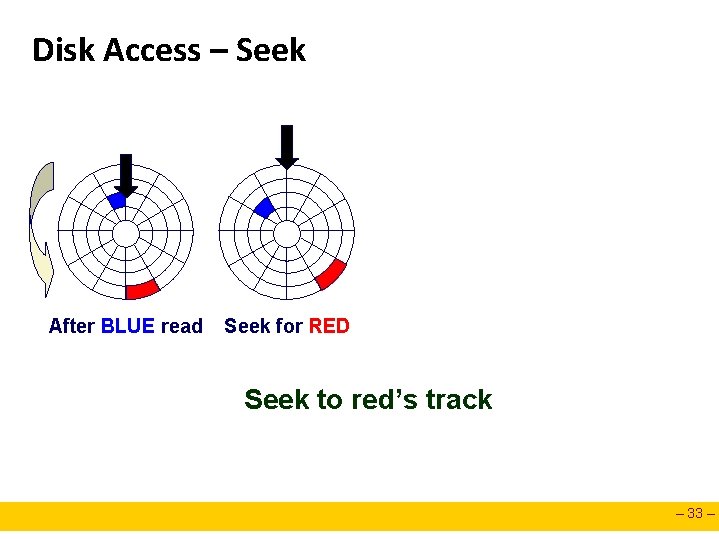
Disk Access – Read After BLUE read Red request scheduled next – 32 –

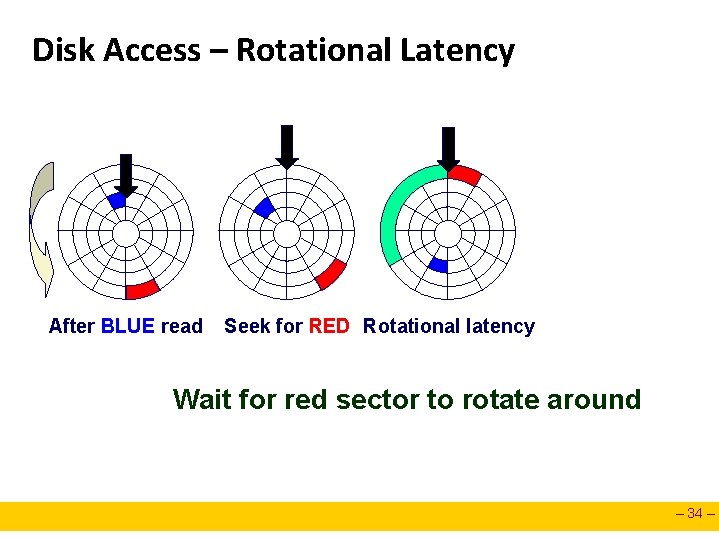
Disk Access – Seek After BLUE read Seek for RED Seek to red’s track – 33 –

Disk Access – Rotational Latency After BLUE read Seek for RED Rotational latency Wait for red sector to rotate around – 34 –

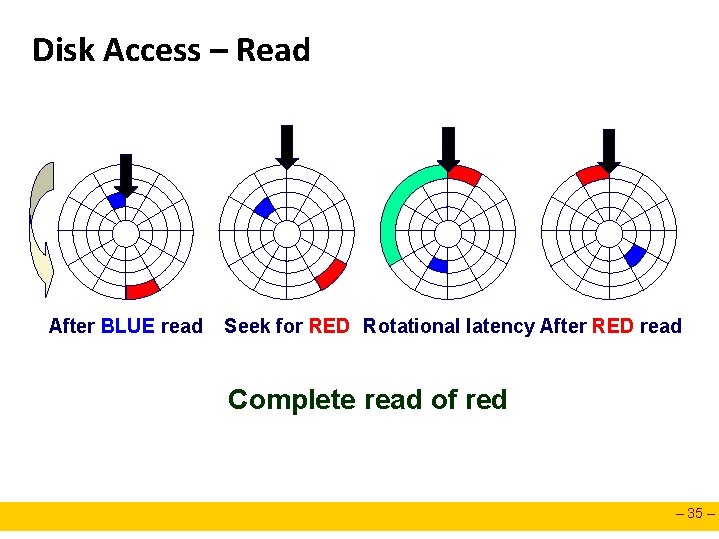
Disk Access – Read After BLUE read Seek for RED Rotational latency After RED read Complete read of red – 35 –

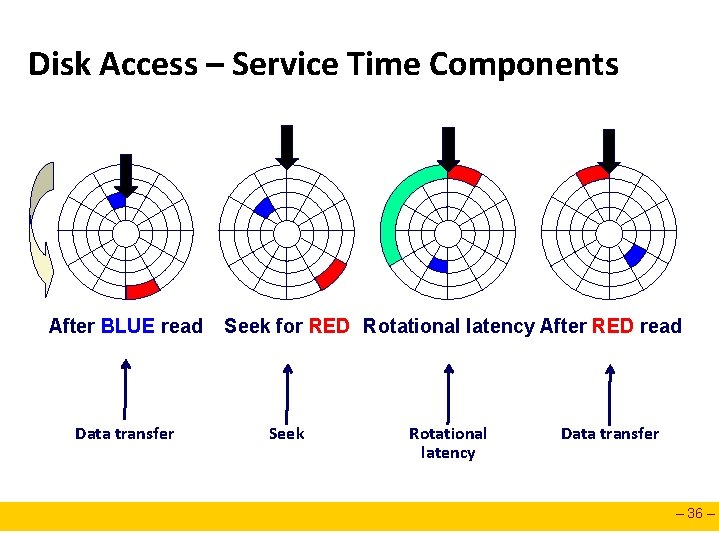
Disk Access – Service Time Components After BLUE read Data transfer Seek for RED Rotational latency After RED read Seek Rotational latency Data transfer – 36 –

Disk Access Time Average time to access some target sector approximated by : n Taccess = Tavg seek + Tavg rotation + Tavg transfer Seek time (Tavg seek) n n Time to position heads over cylinder containing target sector. Typical Tavg seek is 3— 9 ms Rotational latency (Tavg rotation) n n n Time waiting for first bit of target sector to pass under r/w head. Tavg rotation = 1/2 x 1/RPMs x 60 sec/1 min Typical Tavg rotation = 7200 RPMs Transfer time (Tavg transfer) n n Time to read the bits in the target sector. Tavg transfer = 1/RPM x 1/(avg # sectors/track) x 60 secs/1 min. – 37 –

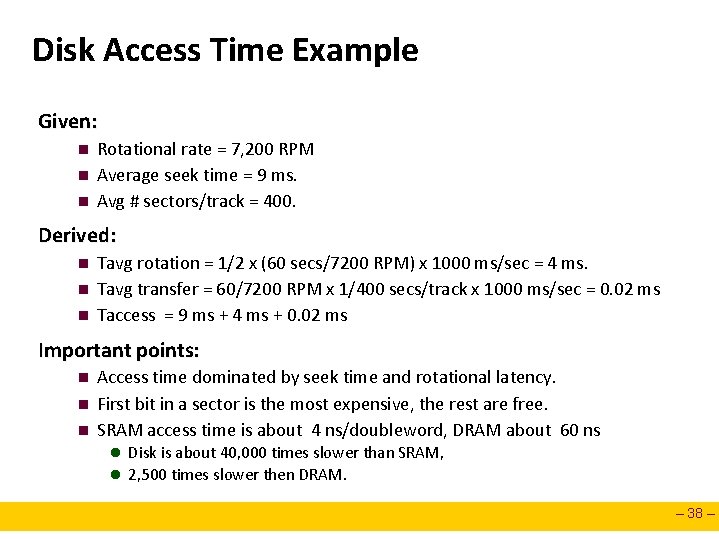
Disk Access Time Example Given: n n n Rotational rate = 7, 200 RPM Average seek time = 9 ms. Avg # sectors/track = 400. Derived: n n n Tavg rotation = 1/2 x (60 secs/7200 RPM) x 1000 ms/sec = 4 ms. Tavg transfer = 60/7200 RPM x 1/400 secs/track x 1000 ms/sec = 0. 02 ms Taccess = 9 ms + 4 ms + 0. 02 ms Important points: n n n Access time dominated by seek time and rotational latency. First bit in a sector is the most expensive, the rest are free. SRAM access time is about 4 ns/doubleword, DRAM about 60 ns l Disk is about 40, 000 times slower than SRAM, l 2, 500 times slower then DRAM. – 38 –

Logical Disk Blocks Modern disks present a simpler abstract view of the complex sector geometry: n The set of available sectors is modeled as a sequence of b-sized logical blocks (0, 1, 2, . . . ) Mapping between logical blocks and actual (physical) sectors n n Maintained by hardware/firmware device called disk controller. Converts requests for logical blocks into (surface, track, sector) triples. Allows controller to set aside spare cylinders for each zone. n Accounts for the difference in “formatted capacity” and “maximum capacity”. – 39 –

I/O Bus CPU chip Register file ALU System bus Memory bus Main memory I/O bridge Bus interface I/O bus USB controller Graphics adapter Mouse. Keyboard Monitor Disk controller Disk Expansion slots for other devices such as network adapters. – 40 –

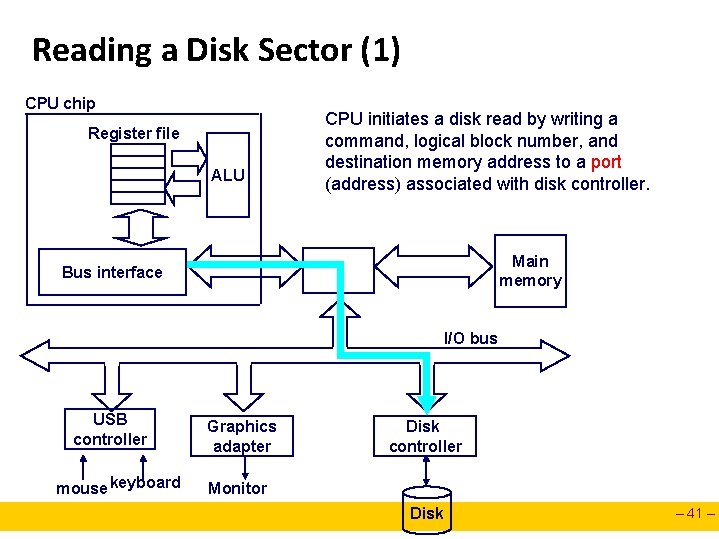
Reading a Disk Sector (1) CPU chip Register file ALU CPU initiates a disk read by writing a command, logical block number, and destination memory address to a port (address) associated with disk controller. Main memory Bus interface I/O bus USB controller mouse keyboard Graphics adapter Disk controller Monitor Disk – 41 –

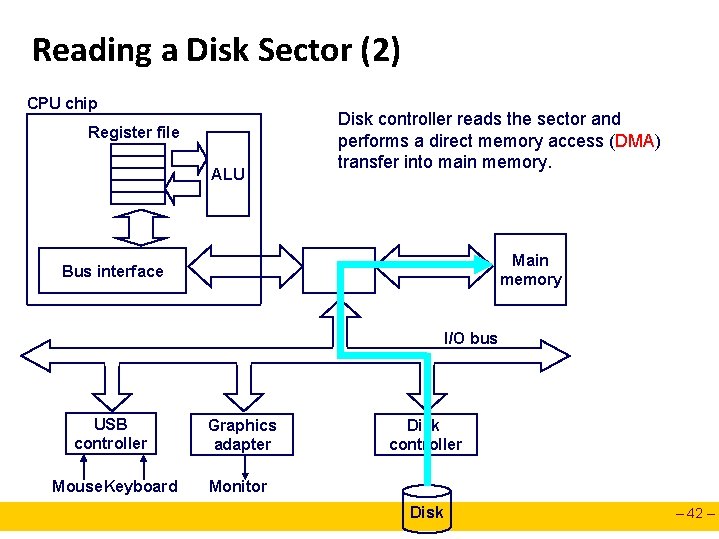
Reading a Disk Sector (2) CPU chip Register file ALU Disk controller reads the sector and performs a direct memory access (DMA) transfer into main memory. Main memory Bus interface I/O bus USB controller Graphics adapter Mouse. Keyboard Monitor Disk controller Disk – 42 –

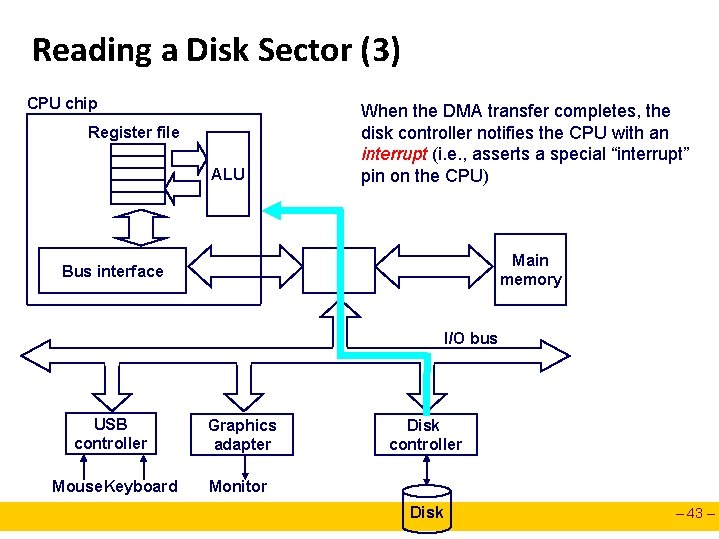
Reading a Disk Sector (3) CPU chip Register file ALU When the DMA transfer completes, the disk controller notifies the CPU with an interrupt (i. e. , asserts a special “interrupt” pin on the CPU) Main memory Bus interface I/O bus USB controller Graphics adapter Mouse. Keyboard Monitor Disk controller Disk – 43 –

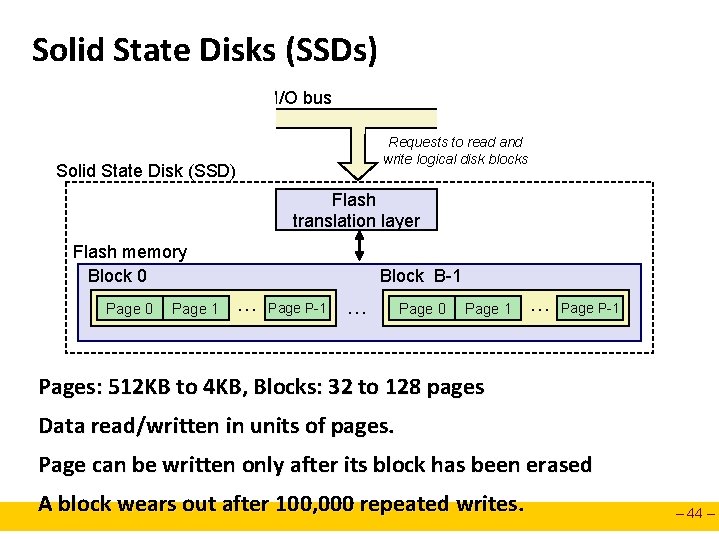
Solid State Disks (SSDs) I/O bus Requests to read and write logical disk blocks Solid State Disk (SSD) Flash translation layer Flash memory Block 0 Page 1 Block B-1 … Page P-1 … Page 0 Page 1 … Page P-1 Pages: 512 KB to 4 KB, Blocks: 32 to 128 pages Data read/written in units of pages. Page can be written only after its block has been erased A block wears out after 100, 000 repeated writes. – 44 –

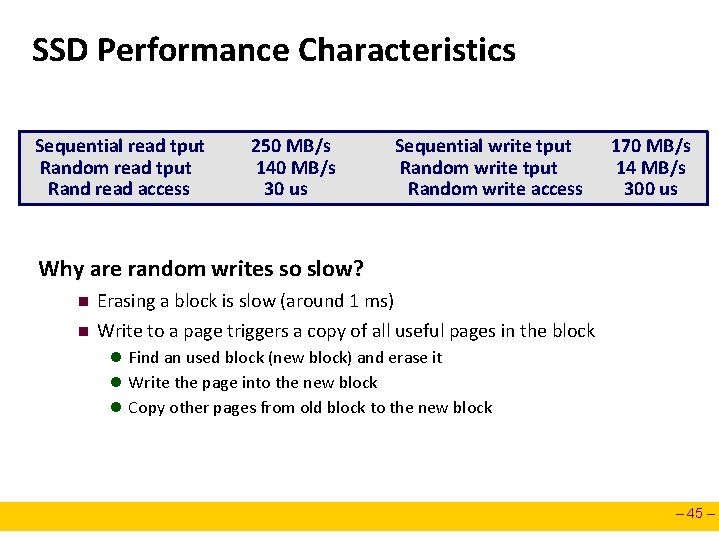
SSD Performance Characteristics Sequential read tput Random read tput Rand read access 250 MB/s 140 MB/s 30 us Sequential write tput Random write access 170 MB/s 14 MB/s 300 us Why are random writes so slow? n n Erasing a block is slow (around 1 ms) Write to a page triggers a copy of all useful pages in the block l Find an used block (new block) and erase it l Write the page into the new block l Copy other pages from old block to the new block – 45 –

SSD Tradeoffs vs Rotating Disks Advantages n No moving parts faster, less power, more rugged Disadvantages n Have the potential to wear out l Mitigated by “wear leveling logic” in flash translation layer l E. g. Intel X 25 guarantees 1 petabyte (10^15 bytes) of random writes before they wear out n In 2010, about 100 times more expensive per byte Applications n n MP 3 players, smart phones, laptops Beginning to appear in desktops and servers – 46 –

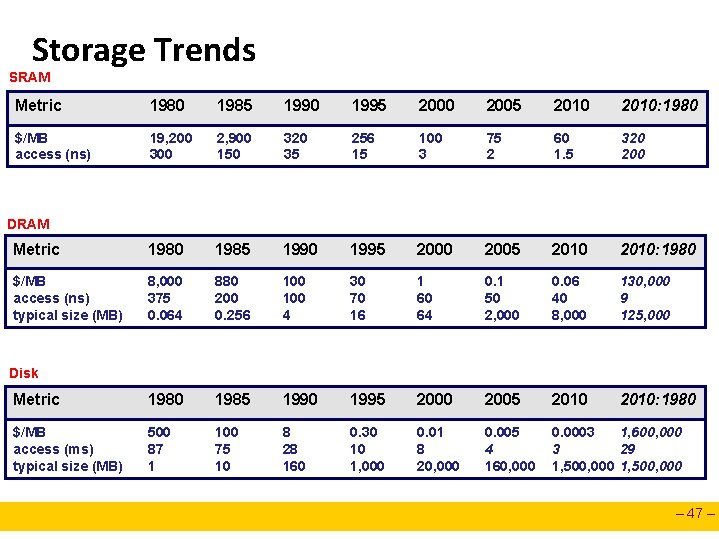
Storage Trends SRAM Metric 1980 1985 1990 1995 2000 2005 2010: 1980 $/MB access (ns) 19, 200 300 2, 900 150 320 35 256 15 100 3 75 2 60 1. 5 320 200 Metric 1980 1985 1990 1995 2000 2005 2010: 1980 $/MB access (ns) typical size (MB) 8, 000 375 0. 064 880 200 0. 256 100 4 30 70 16 1 60 64 0. 1 50 2, 000 0. 06 40 8, 000 130, 000 9 125, 000 Metric 1980 1985 1990 1995 2000 2005 2010: 1980 $/MB access (ms) typical size (MB) 500 87 1 100 75 10 8 28 160 0. 30 10 1, 000 0. 01 8 20, 000 0. 005 4 160, 000 0. 0003 1, 600, 000 3 29 1, 500, 000 DRAM Disk – 47 –

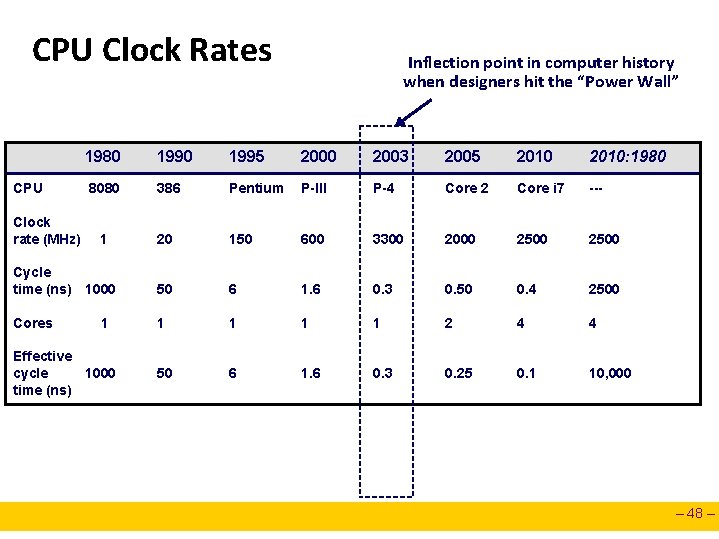
CPU Clock Rates Inflection point in computer history when designers hit the “Power Wall” 1980 1995 2000 2003 2005 2010: 1980 8080 386 Pentium P-III P-4 Core 2 Core i 7 --- 1 20 150 600 3300 2000 2500 Cycle time (ns) 1000 50 6 1. 6 0. 3 0. 50 0. 4 2500 Cores 1 1 2 4 4 50 6 1. 6 0. 3 0. 25 0. 1 10, 000 CPU Clock rate (MHz) 1 Effective cycle 1000 time (ns) – 48 –

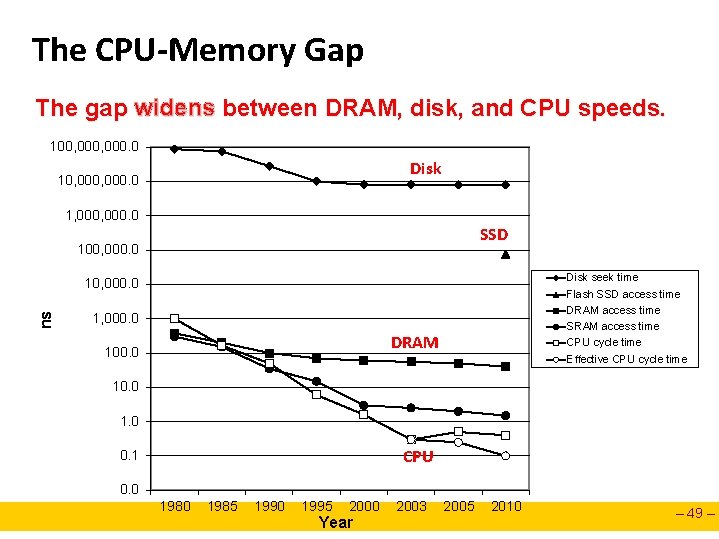
The CPU-Memory Gap The gap widens between DRAM, disk, and CPU speeds. 100, 000. 0 Disk 10, 000. 0 1, 000. 0 SSD 100, 000. 0 Disk seek time Flash SSD access time DRAM access time SRAM access time CPU cycle time Effective CPU cycle time ns 10, 000. 0 1, 000. 0 DRAM 100. 0 1. 0 CPU 0. 1 0. 0 1985 1990 1995 2000 Year 2003 2005 2010 – 49 –

Locality to the Rescue! The key to bridging this CPU-Memory gap is a fundamental property of computer programs known as locality – 50 –

Locality Principle of Locality: Programs tend to use data and instructions with addresses near or equal to those they have used recently Temporal locality: n Recently referenced items are likely to be referenced again in the near future Spatial locality: n Items with nearby addresses tend to be referenced close together in time – 51 –

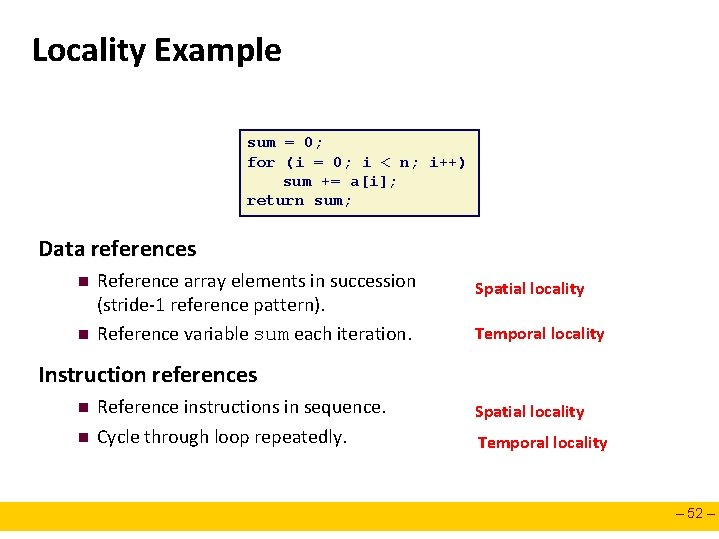
Locality Example sum = 0; for (i = 0; i < n; i++) sum += a[i]; return sum; Data references n n Reference array elements in succession (stride-1 reference pattern). Reference variable sum each iteration. Spatial locality Temporal locality Instruction references n n Reference instructions in sequence. Cycle through loop repeatedly. Spatial locality Temporal locality – 52 –

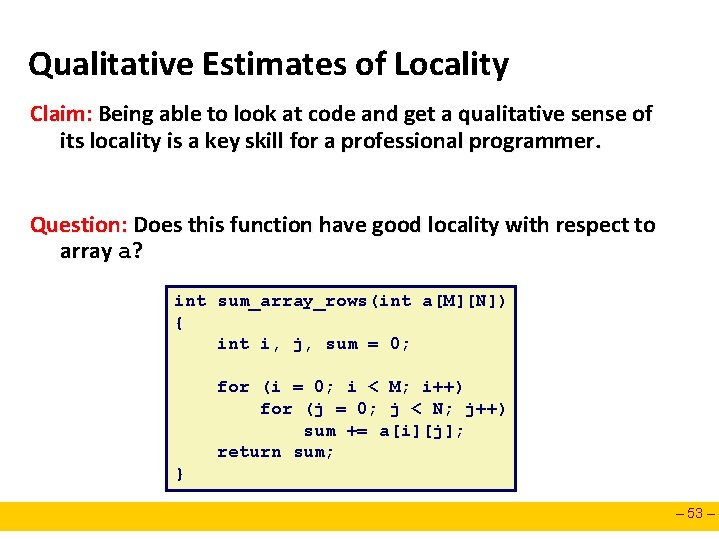
Qualitative Estimates of Locality Claim: Being able to look at code and get a qualitative sense of its locality is a key skill for a professional programmer. Question: Does this function have good locality with respect to array a? int sum_array_rows(int a[M][N]) { int i, j, sum = 0; for (i = 0; i < M; i++) for (j = 0; j < N; j++) sum += a[i][j]; return sum; } – 53 –

Locality Example Question: Does this function have good locality with respect to array a? int sum_array_cols(int a[M][N]) { int i, j, sum = 0; for (j = 0; j < N; j++) for (i = 0; i < M; i++) sum += a[i][j]; return sum; } – 54 –

Locality Example Question: Can you permute the loops so that the function scans the 3 -d array a with a stride-1 reference pattern (and thus has good spatial locality)? int sum_array_3 d(int a[M][N][N]) { int i, j, k, sum = 0; for (i = 0; i < M; i++) for (j = 0; j < N; j++) for (k = 0; k < N; k++) sum += a[k][i][j]; return sum; } – 55 –

Memory Hierarchies Some fundamental and enduring properties of hardware and software: n n n Fast storage technologies cost more per byte, have less capacity, and require more power (heat!). The gap between CPU and main memory speed is widening. Well-written programs tend to exhibit good locality. These fundamental properties complement each other beautifully. They suggest an approach for organizing memory and storage systems known as a memory hierarchy. – 56 –

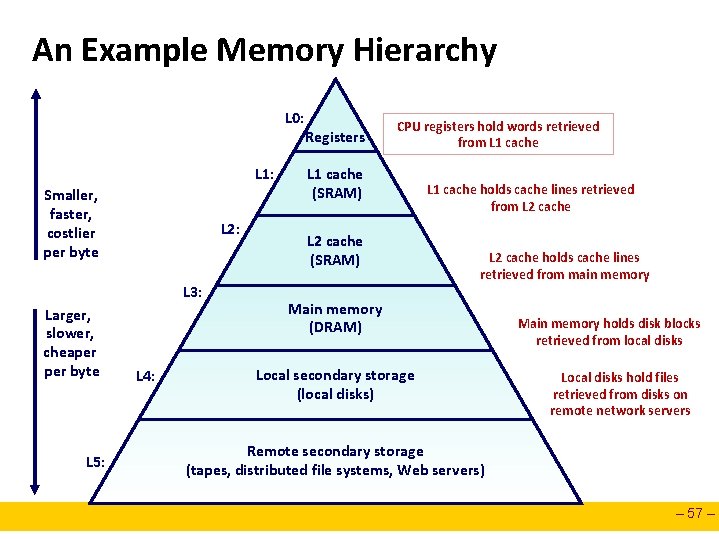
An Example Memory Hierarchy L 0: L 1: Smaller, faster, costlier per byte L 2: L 3: Larger, slower, cheaper byte L 5: L 4: Registers CPU registers hold words retrieved from L 1 cache (SRAM) L 2 cache (SRAM) L 1 cache holds cache lines retrieved from L 2 cache holds cache lines retrieved from main memory Main memory (DRAM) Local secondary storage (local disks) Main memory holds disk blocks retrieved from local disks Local disks hold files retrieved from disks on remote network servers Remote secondary storage (tapes, distributed file systems, Web servers) – 57 –

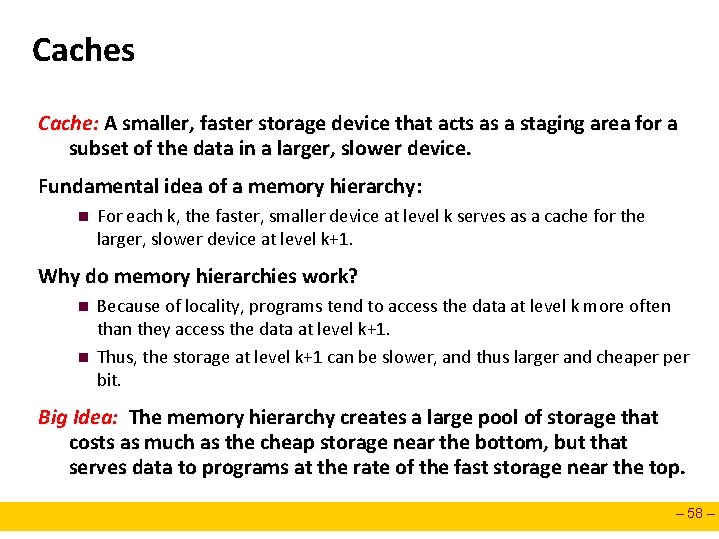
Caches Cache: A smaller, faster storage device that acts as a staging area for a subset of the data in a larger, slower device. Fundamental idea of a memory hierarchy: n For each k, the faster, smaller device at level k serves as a cache for the larger, slower device at level k+1. Why do memory hierarchies work? n n Because of locality, programs tend to access the data at level k more often than they access the data at level k+1. Thus, the storage at level k+1 can be slower, and thus larger and cheaper bit. Big Idea: The memory hierarchy creates a large pool of storage that costs as much as the cheap storage near the bottom, but that serves data to programs at the rate of the fast storage near the top. – 58 –

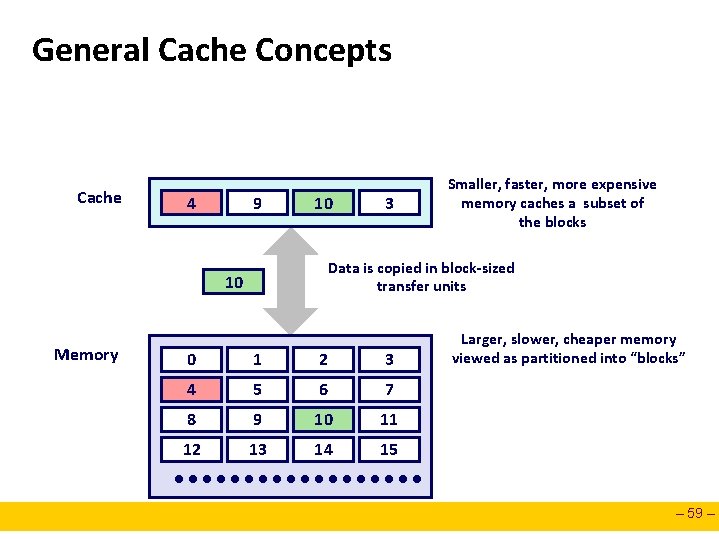
General Cache Concepts Cache 8 4 9 14 10 Data is copied in block-sized transfer units 10 4 Memory 3 Smaller, faster, more expensive memory caches a subset of the blocks 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Larger, slower, cheaper memory viewed as partitioned into “blocks” – 59 –

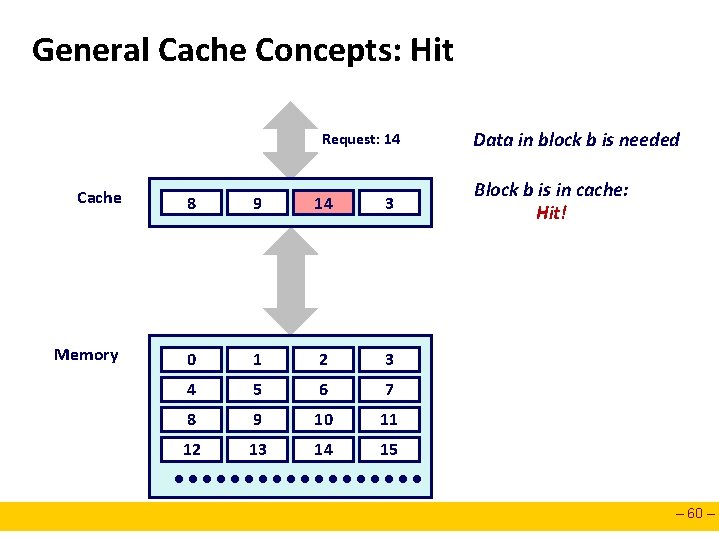
General Cache Concepts: Hit Request: 14 Cache 8 9 14 3 Memory 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Data in block b is needed Block b is in cache: Hit! – 60 –

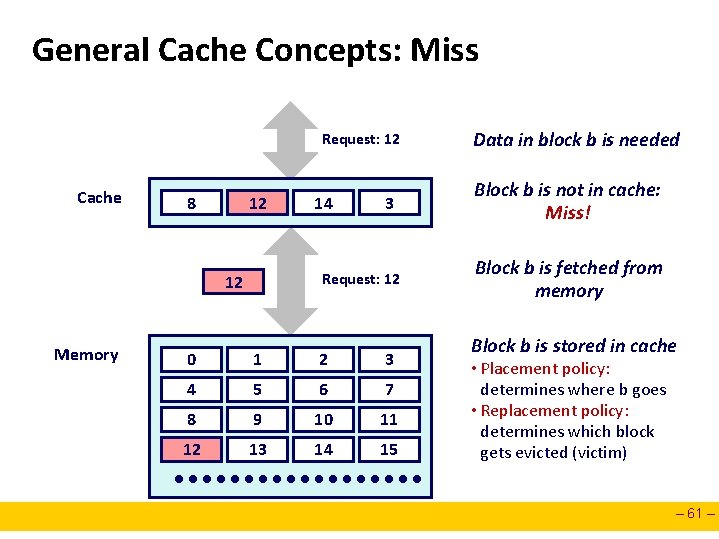
General Cache Concepts: Miss Request: 12 Cache 8 9 12 3 Request: 12 12 Memory 14 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Data in block b is needed Block b is not in cache: Miss! Block b is fetched from memory Block b is stored in cache • Placement policy: determines where b goes • Replacement policy: determines which block gets evicted (victim) – 61 –

General Caching Concepts: Types of Cache Misses Cold (compulsory) miss n Cold misses occur because the cache is empty. Conflict miss n Most caches limit blocks at level k+1 to a small subset (sometimes a singleton) of the block positions at level k. l E. g. Block i at level k+1 must be placed in block (i mod 4) at level k. n Conflict misses occur when the level k cache is large enough, but multiple data objects all map to the same level k block. l E. g. Referencing blocks 0, 8, . . . would miss every time. Capacity miss n Occurs when the set of active cache blocks (working set) is larger than the cache. – 62 –

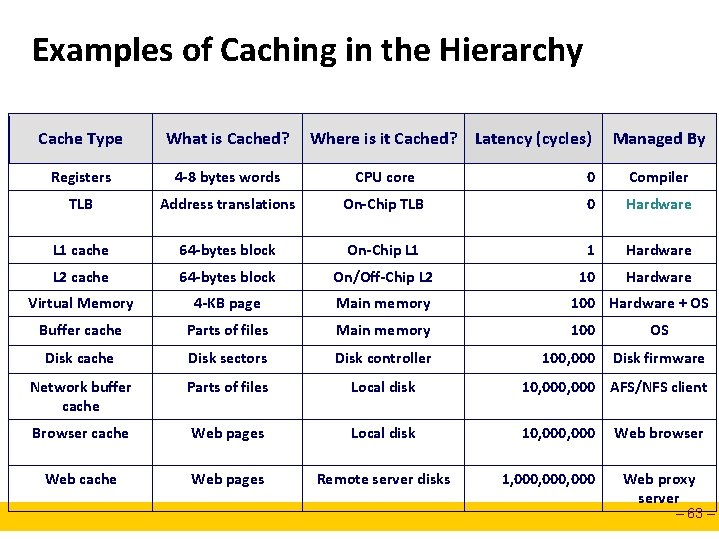
Examples of Caching in the Hierarchy Cache Type What is Cached? Where is it Cached? Latency (cycles) Registers 4 -8 bytes words CPU core 0 Compiler TLB Address translations On-Chip TLB 0 Hardware L 1 cache 64 -bytes block On-Chip L 1 1 Hardware L 2 cache 64 -bytes block On/Off-Chip L 2 10 Hardware Virtual Memory 4 -KB page Main memory 100 Hardware + OS Buffer cache Parts of files Main memory 100 Disk cache Disk sectors Disk controller 100, 000 Network buffer cache Parts of files Local disk 10, 000 AFS/NFS client Browser cache Web pages Local disk 10, 000 Web cache Web pages Remote server disks 1, 000, 000 Managed By OS Disk firmware Web browser Web proxy server – 63 –

Summary The speed gap between CPU, memory and mass storage continues to widen. Well-written programs exhibit a property called locality. Memory hierarchies based on caching close the gap by exploiting locality. – 64 –

Cache Memories CENG 331: Introduction to Computer Systems 10 th Lecture. Instructor: Erol Sahin

Today Cache memory organization and operation Performance impact of caches n The memory mountain Rearranging loops to improve spatial locality n Using blocking to improve temporal locality n – 66 –

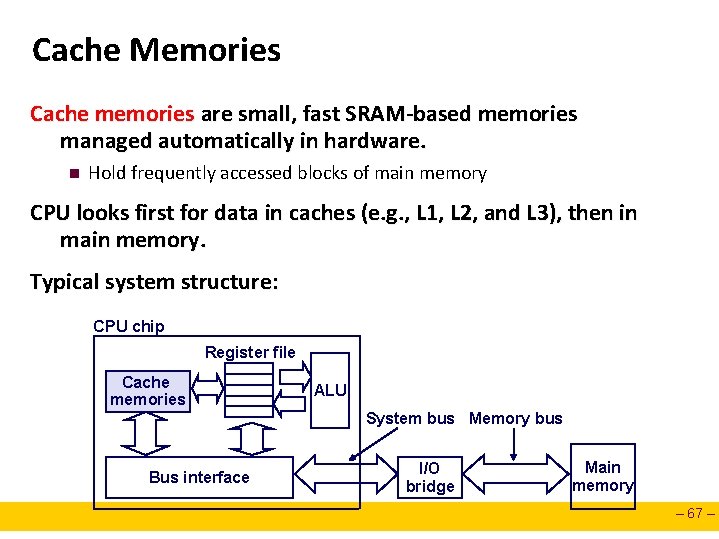
Cache Memories Cache memories are small, fast SRAM-based memories managed automatically in hardware. n Hold frequently accessed blocks of main memory CPU looks first for data in caches (e. g. , L 1, L 2, and L 3), then in main memory. Typical system structure: CPU chip Register file Cache memories ALU System bus Memory bus Bus interface I/O bridge Main memory – 67 –

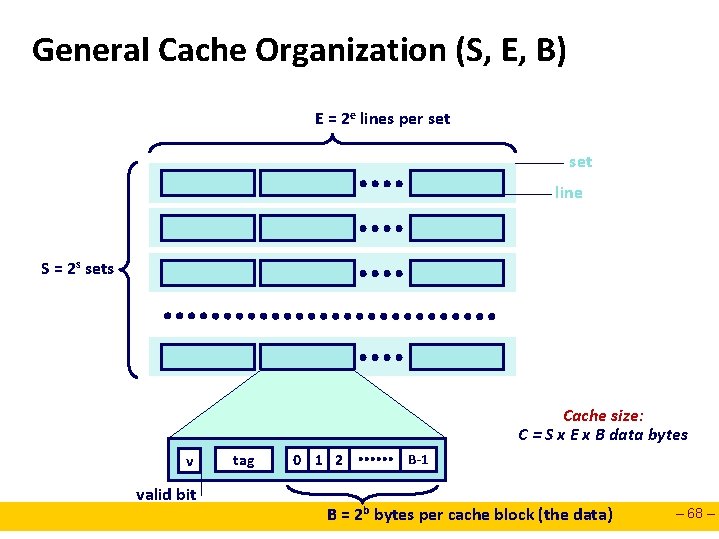
General Cache Organization (S, E, B) E = 2 e lines per set line S = 2 s sets Cache size: C = S x E x B data bytes v valid bit tag 0 1 2 B-1 B = 2 b bytes per cache block (the data) – 68 –

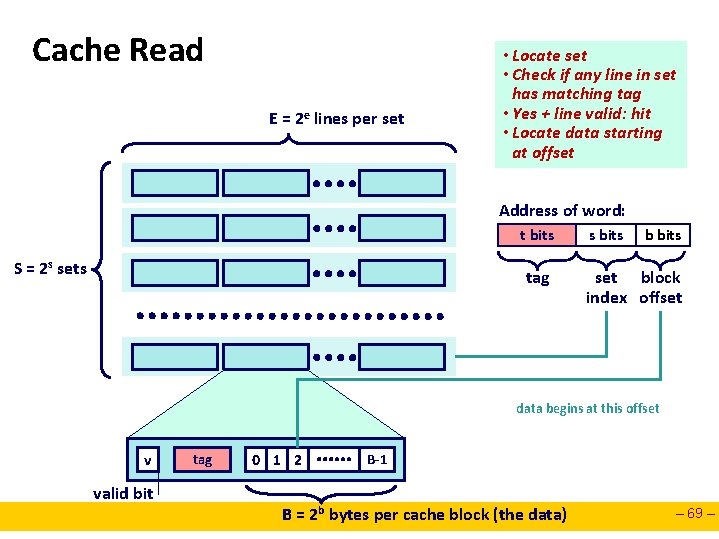
Cache Read E = 2 e lines per set • Locate set • Check if any line in set has matching tag • Yes + line valid: hit • Locate data starting at offset Address of word: t bits S = 2 s sets tag s bits b bits set block index offset data begins at this offset v valid bit tag 0 1 2 B-1 B = 2 b bytes per cache block (the data) – 69 –

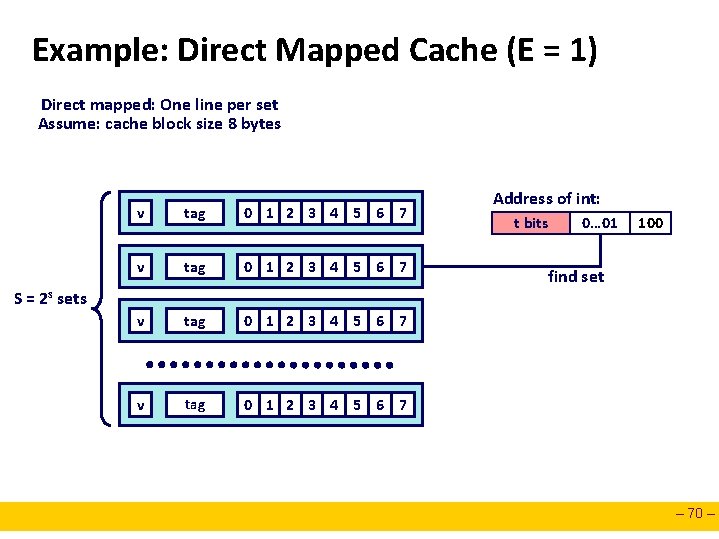
Example: Direct Mapped Cache (E = 1) Direct mapped: One line per set Assume: cache block size 8 bytes v tag 0 1 2 3 4 5 6 7 Address of int: t bits 0… 01 100 find set S = 2 s sets – 70 –

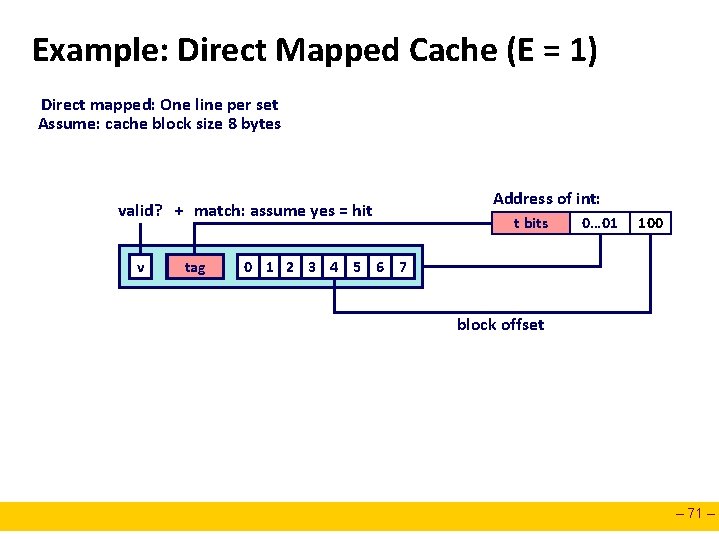
Example: Direct Mapped Cache (E = 1) Direct mapped: One line per set Assume: cache block size 8 bytes valid? + match: assume yes = hit v tag Address of int: t bits 0… 01 100 0 1 2 3 4 5 6 7 block offset – 71 –

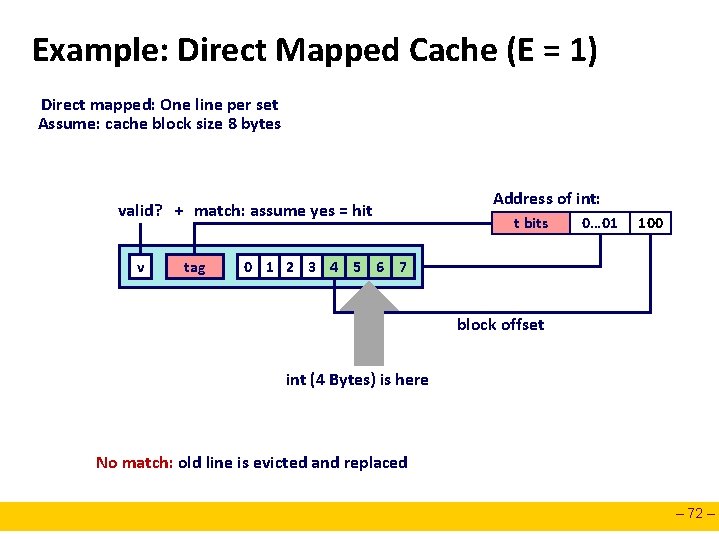
Example: Direct Mapped Cache (E = 1) Direct mapped: One line per set Assume: cache block size 8 bytes valid? + match: assume yes = hit v tag Address of int: t bits 0… 01 100 0 1 2 3 4 5 6 7 block offset int (4 Bytes) is here No match: old line is evicted and replaced – 72 –

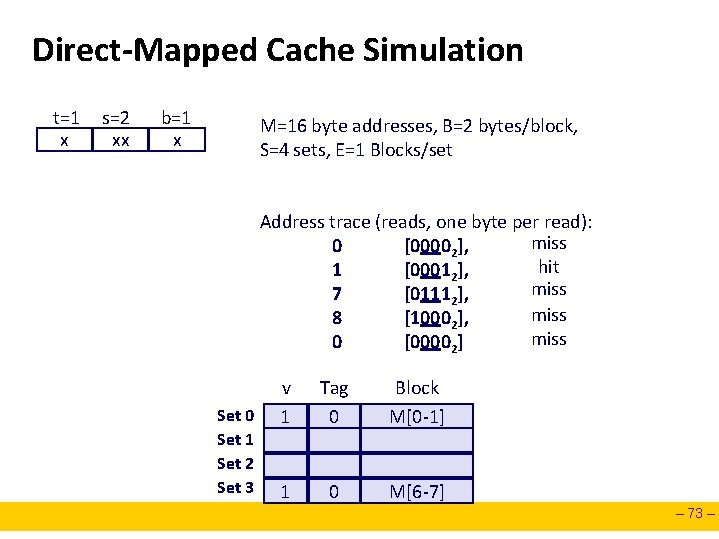
Direct-Mapped Cache Simulation t=1 x s=2 xx b=1 x M=16 byte addresses, B=2 bytes/block, S=4 sets, E=1 Blocks/set Address trace (reads, one byte per read): miss 0 [00002], hit 1 [00012], miss 7 [01112], miss 8 [10002], miss 0 [00002] Set 0 Set 1 Set 2 Set 3 v 0 1 Tag 1? 0 Block ? M[8 -9] M[0 -1] 1 0 M[6 -7] – 73 –

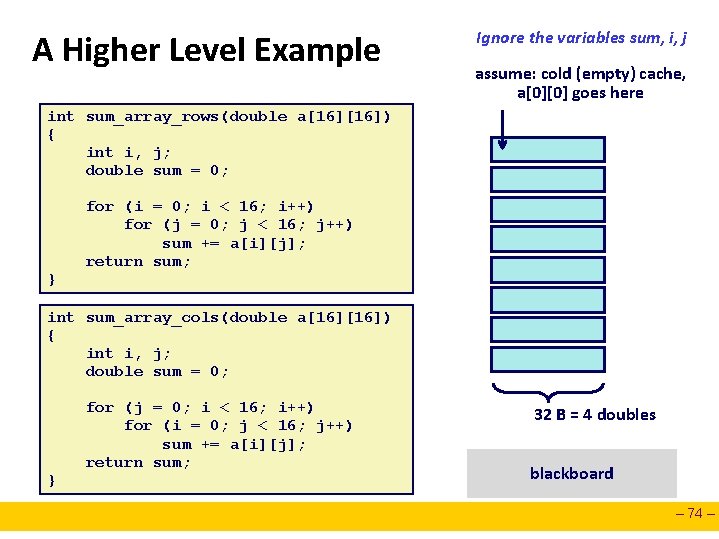
A Higher Level Example Ignore the variables sum, i, j assume: cold (empty) cache, a[0][0] goes here int sum_array_rows(double a[16]) { int i, j; double sum = 0; } for (i = 0; i < 16; i++) for (j = 0; j < 16; j++) sum += a[i][j]; return sum; int sum_array_cols(double a[16]) { int i, j; double sum = 0; } for (j = 0; i < 16; i++) for (i = 0; j < 16; j++) sum += a[i][j]; return sum; 32 B = 4 doubles blackboard – 74 –

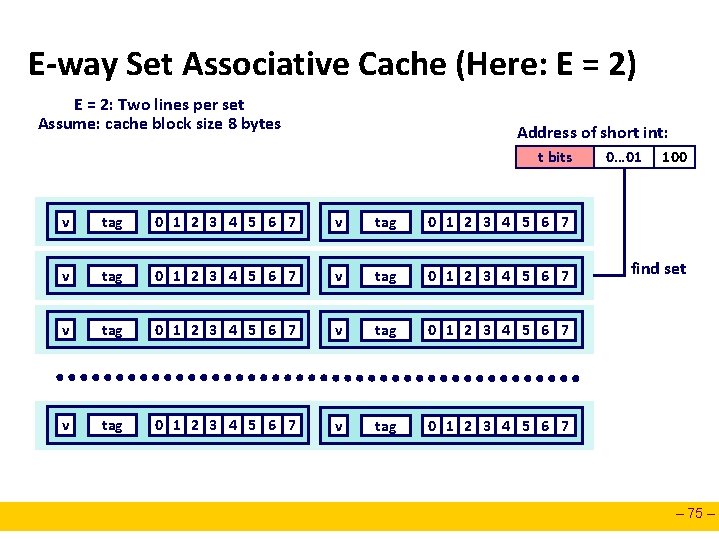
E-way Set Associative Cache (Here: E = 2) E = 2: Two lines per set Assume: cache block size 8 bytes Address of short int: t bits v tag 0 1 2 3 4 5 6 7 v tag 0 1 2 3 4 5 6 7 0… 01 100 find set – 75 –

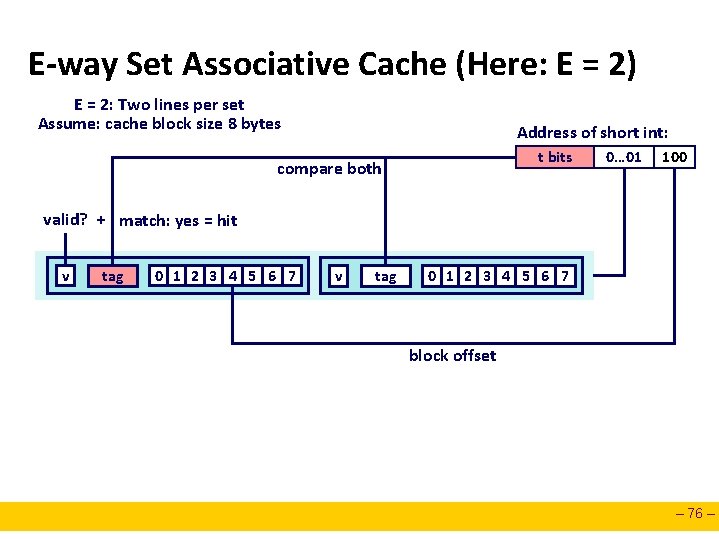
E-way Set Associative Cache (Here: E = 2) E = 2: Two lines per set Assume: cache block size 8 bytes Address of short int: t bits compare both 0… 01 100 valid? + match: yes = hit v tag 0 1 2 3 4 5 6 7 block offset – 76 –

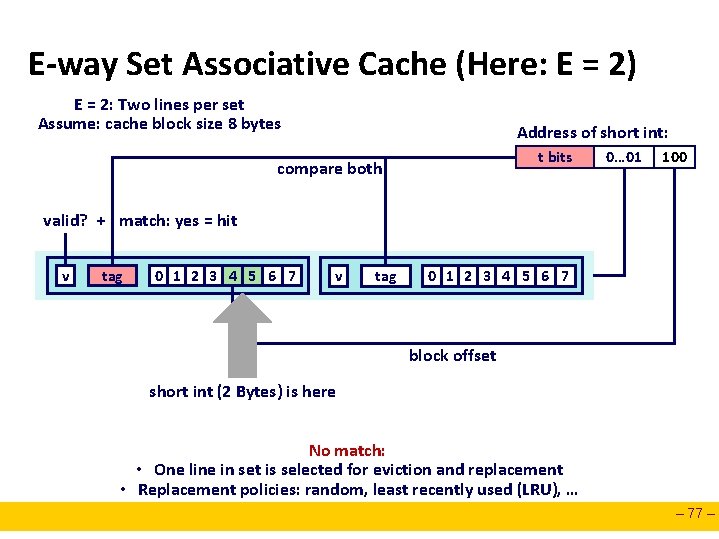
E-way Set Associative Cache (Here: E = 2) E = 2: Two lines per set Assume: cache block size 8 bytes Address of short int: t bits compare both 0… 01 100 valid? + match: yes = hit v tag 0 1 2 3 4 5 6 7 block offset short int (2 Bytes) is here No match: • One line in set is selected for eviction and replacement • Replacement policies: random, least recently used (LRU), … – 77 –

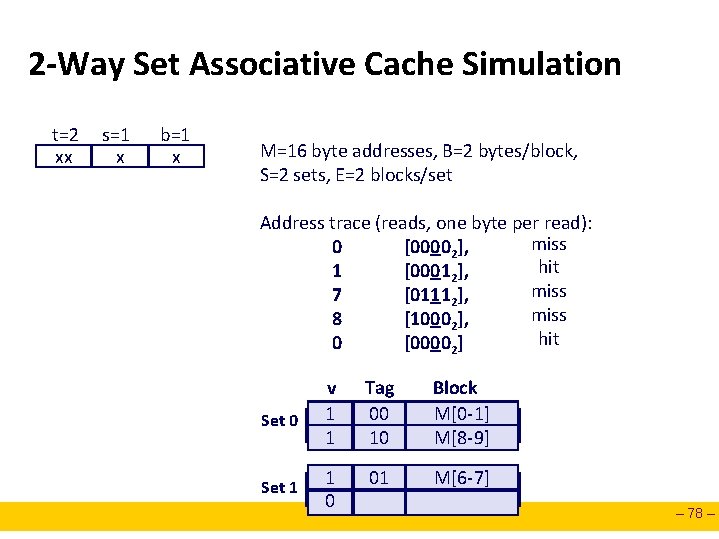
2 -Way Set Associative Cache Simulation t=2 xx s=1 x b=1 x M=16 byte addresses, B=2 bytes/block, S=2 sets, E=2 blocks/set Address trace (reads, one byte per read): miss 0 [00002], hit 1 [00012], miss 7 [01112], miss 8 [10002], hit 0 [00002] Set 0 v 0 1 Tag ? 00 10 Block ? M[0 -1] M[8 -9] Set 1 0 01 M[6 -7] – 78 –
![A Higher Level Example int sumarrayrowsdouble a16 int i j double sum A Higher Level Example int sum_array_rows(double a[16]) { int i, j; double sum =](https://slidetodoc.com/presentation_image_h/2cbb9f24cb5e6f207b481c8468877a27/image-79.jpg)
A Higher Level Example int sum_array_rows(double a[16]) { int i, j; double sum = 0; } assume: cold (empty) cache, a[0][0] goes here for (i = 0; i < 16; i++) for (j = 0; j < 16; j++) sum += a[i][j]; return sum; int sum_array_rows(double a[16]) { int i, j; double sum = 0; } Ignore the variables sum, i, j for (j = 0; i < 16; i++) for (i = 0; j < 16; j++) sum += a[i][j]; return sum; 32 B = 4 doubles blackboard – 79 –

What about writes? Multiple copies of data exist: n L 1, L 2, Main Memory, Disk What to do on a write-hit? n n Write-through (write immediately to memory) Write-back (defer write to memory until replacement of line) l Need a dirty bit (line different from memory or not) What to do on a write-miss? n Write-allocate (load into cache, update line in cache) l Good if more writes to the location follow n No-write-allocate (writes immediately to memory) Typical n n Write-through + No-write-allocate Write-back + Write-allocate – 80 –

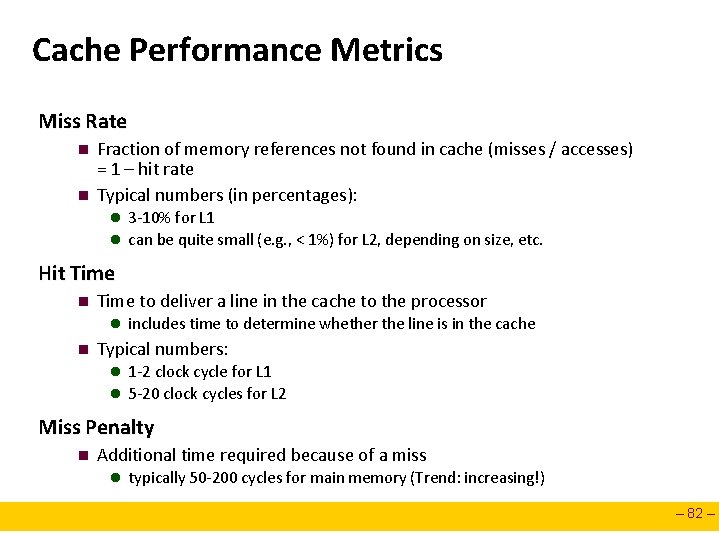
Intel Core i 7 Cache Hierarchy Processor package Core 0 Regs L 1 d-cache L 1 i-cache and d-cache: 32 KB, 8 -way, Access: 4 cycles Core 3 Regs L 1 i-cache … L 2 unified cache L 1 d-cache L 1 i-cache L 2 unified cache L 3 unified cache (shared by all cores) Main memory L 2 unified cache: 256 KB, 8 -way, Access: 11 cycles L 3 unified cache: 8 MB, 16 -way, Access: 30 -40 cycles Block size: 64 bytes for all caches. – 81 –

Cache Performance Metrics Miss Rate n n Fraction of memory references not found in cache (misses / accesses) = 1 – hit rate Typical numbers (in percentages): l 3 -10% for L 1 l can be quite small (e. g. , < 1%) for L 2, depending on size, etc. Hit Time n Time to deliver a line in the cache to the processor l includes time to determine whether the line is in the cache n Typical numbers: l 1 -2 clock cycle for L 1 l 5 -20 clock cycles for L 2 Miss Penalty n Additional time required because of a miss l typically 50 -200 cycles for main memory (Trend: increasing!) – 82 –

Lets think about those numbers Huge difference between a hit and a miss n Could be 100 x, if just L 1 and main memory Would you believe 99% hits is twice as good as 97%? n Consider: cache hit time of 1 cycle miss penalty of 100 cycles n Average access time: 97% hits: 1 cycle + 0. 03 * 100 cycles = 4 cycles 99% hits: 1 cycle + 0. 01 * 100 cycles = 2 cycles This is why “miss rate” is used instead of “hit rate” – 83 –

Writing Cache Friendly Code Make the common case go fast n Focus on the inner loops of the core functions Minimize the misses in the inner loops n n Repeated references to variables are good (temporal locality) Stride-1 reference patterns are good (spatial locality) Key idea: Our qualitative notion of locality is quantified through our understanding of cache memories. – 84 –

Today Cache organization and operation Performance impact of caches n The memory mountain Rearranging loops to improve spatial locality n Using blocking to improve temporal locality n – 85 –

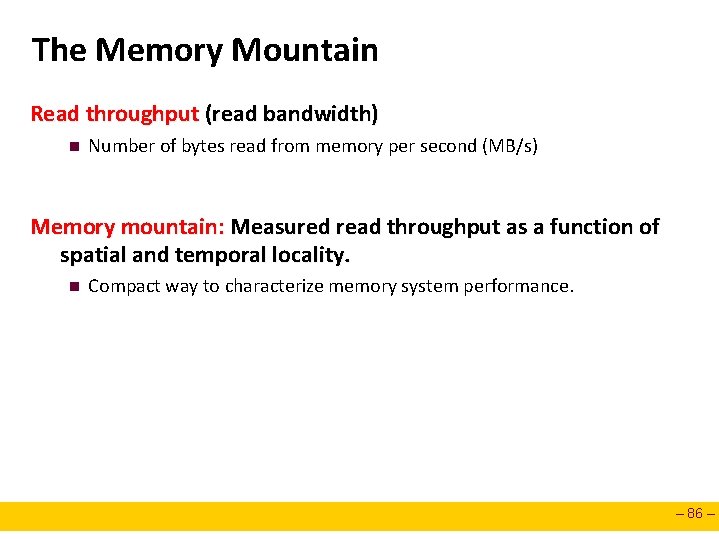
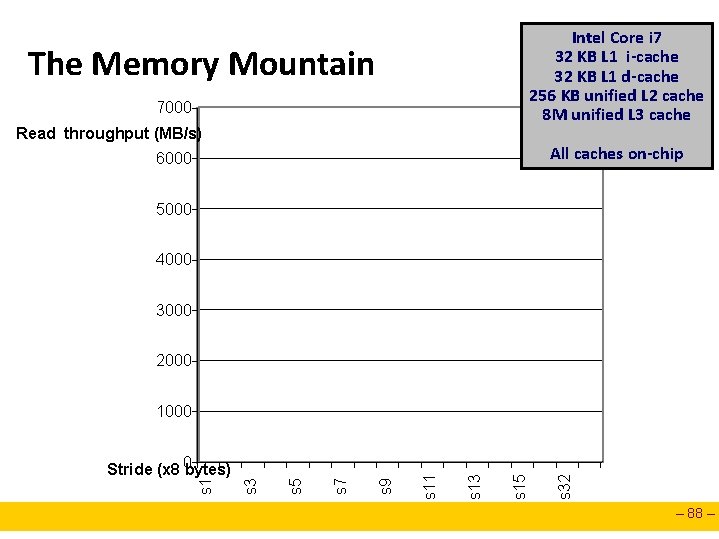
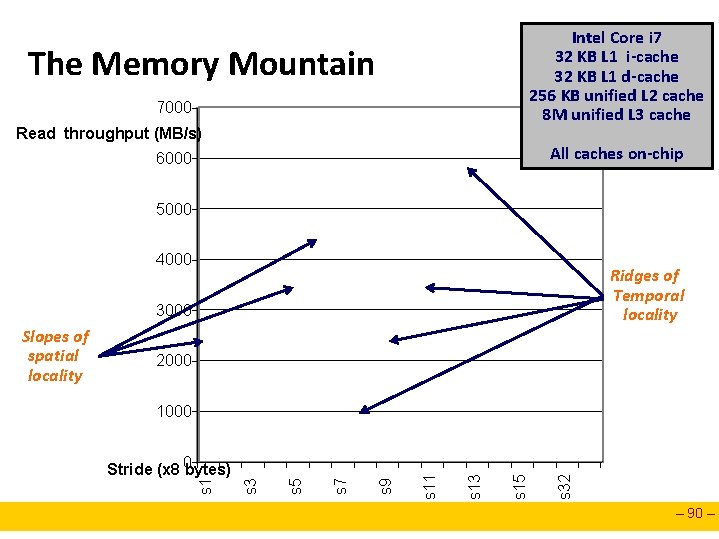
The Memory Mountain Read throughput (read bandwidth) n Number of bytes read from memory per second (MB/s) Memory mountain: Measured read throughput as a function of spatial and temporal locality. n Compact way to characterize memory system performance. – 86 –

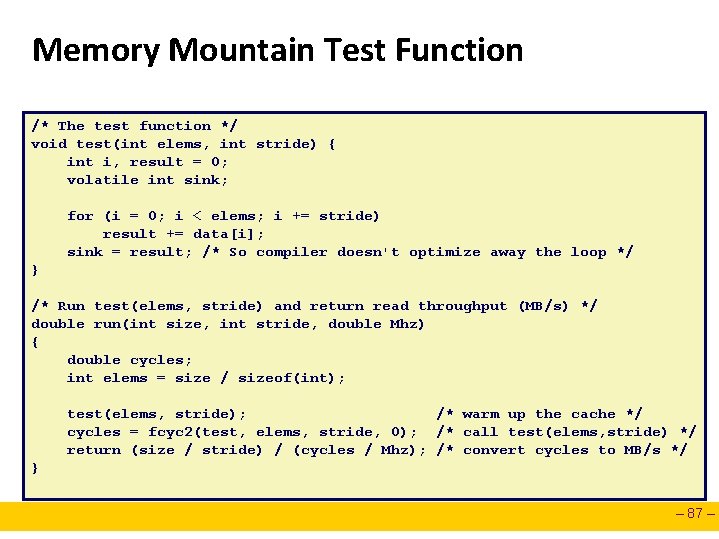
Memory Mountain Test Function /* The test function */ void test(int elems, int stride) { int i, result = 0; volatile int sink; for (i = 0; i < elems; i += stride) result += data[i]; sink = result; /* So compiler doesn't optimize away the loop */ } /* Run test(elems, stride) and return read throughput (MB/s) */ double run(int size, int stride, double Mhz) { double cycles; int elems = size / sizeof(int); test(elems, stride); /* warm up the cache */ cycles = fcyc 2(test, elems, stride, 0); /* call test(elems, stride) */ return (size / stride) / (cycles / Mhz); /* convert cycles to MB/s */ } – 87 –

Intel Core i 7 32 KB L 1 i-cache 32 KB L 1 d-cache 256 KB unified L 2 cache 8 M unified L 3 cache The Memory Mountain 7000 Read throughput (MB/s) All caches on-chip 6000 5000 4000 3000 2000 s 32 s 15 s 13 s 9 s 7 s 5 s 3 s 1 Stride (x 8 0 bytes) s 11 1000 – 88 –

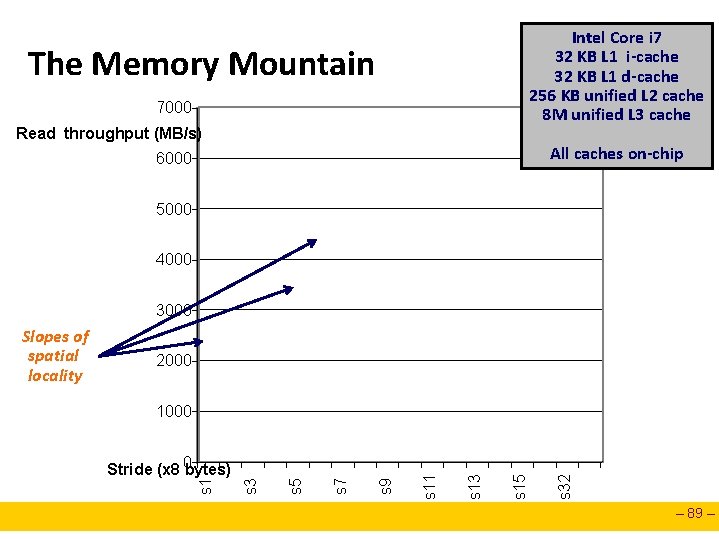
Intel Core i 7 32 KB L 1 i-cache 32 KB L 1 d-cache 256 KB unified L 2 cache 8 M unified L 3 cache The Memory Mountain 7000 Read throughput (MB/s) All caches on-chip 6000 5000 4000 3000 2000 s 32 s 15 s 13 s 9 s 7 s 5 s 3 Stride (x 8 0 bytes) s 11 1000 s 1 Slopes of spatial locality – 89 –

Intel Core i 7 32 KB L 1 i-cache 32 KB L 1 d-cache 256 KB unified L 2 cache 8 M unified L 3 cache The Memory Mountain 7000 Read throughput (MB/s) All caches on-chip 6000 5000 4000 Ridges of Temporal locality 3000 2000 s 32 s 15 s 13 s 9 s 7 s 5 s 3 Stride (x 8 0 bytes) s 11 1000 s 1 Slopes of spatial locality – 90 –

Today Cache organization and operation Performance impact of caches n The memory mountain Rearranging loops to improve spatial locality n Using blocking to improve temporal locality n – 91 –

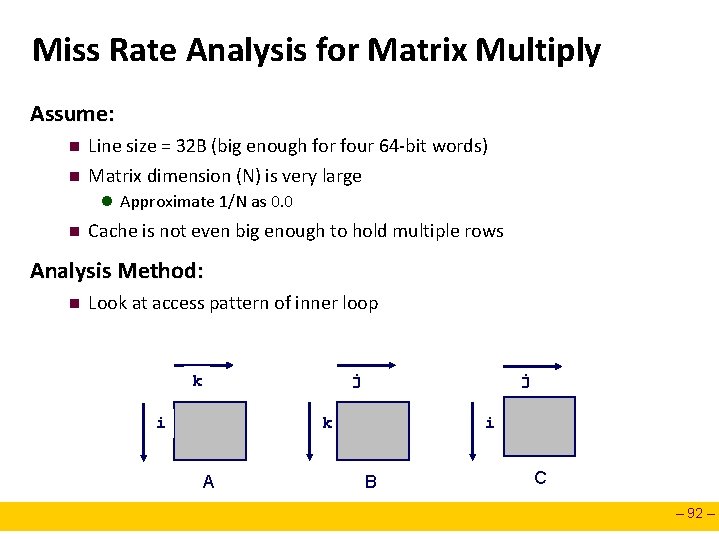
Miss Rate Analysis for Matrix Multiply Assume: n n Line size = 32 B (big enough for four 64 -bit words) Matrix dimension (N) is very large l Approximate 1/N as 0. 0 n Cache is not even big enough to hold multiple rows Analysis Method: n Look at access pattern of inner loop j k i j i k A B C – 92 –

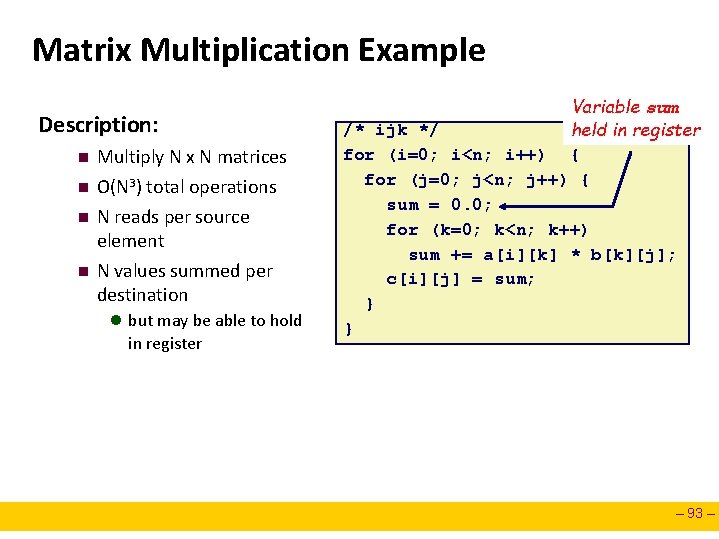
Matrix Multiplication Example Description: n n Multiply N x N matrices O(N 3) total operations N reads per source element N values summed per destination l but may be able to hold in register Variable sum /* ijk */ held in register for (i=0; i<n; i++) { for (j=0; j<n; j++) { sum = 0. 0; for (k=0; k<n; k++) sum += a[i][k] * b[k][j]; c[i][j] = sum; } } – 93 –

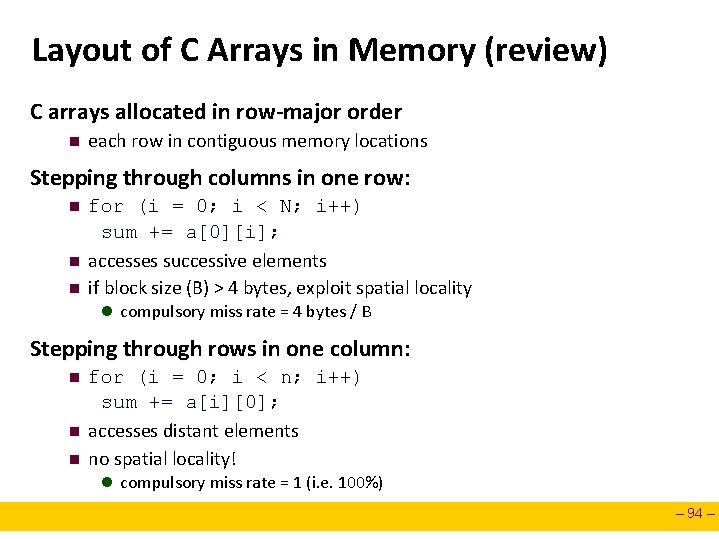
Layout of C Arrays in Memory (review) C arrays allocated in row-major order n each row in contiguous memory locations Stepping through columns in one row: n n n for (i = 0; i < N; i++) sum += a[0][i]; accesses successive elements if block size (B) > 4 bytes, exploit spatial locality l compulsory miss rate = 4 bytes / B Stepping through rows in one column: n n n for (i = 0; i < n; i++) sum += a[i][0]; accesses distant elements no spatial locality! l compulsory miss rate = 1 (i. e. 100%) – 94 –

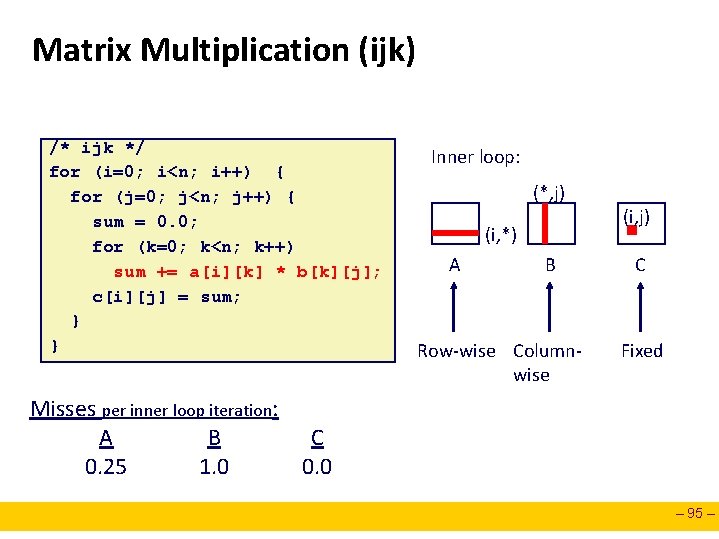
Matrix Multiplication (ijk) /* ijk */ for (i=0; i<n; i++) { for (j=0; j<n; j++) { sum = 0. 0; for (k=0; k<n; k++) sum += a[i][k] * b[k][j]; c[i][j] = sum; } } Inner loop: (*, j) (i, *) A B Row-wise Columnwise (i, j) C Fixed Misses per inner loop iteration: A B C 0. 25 1. 0 0. 0 – 95 –

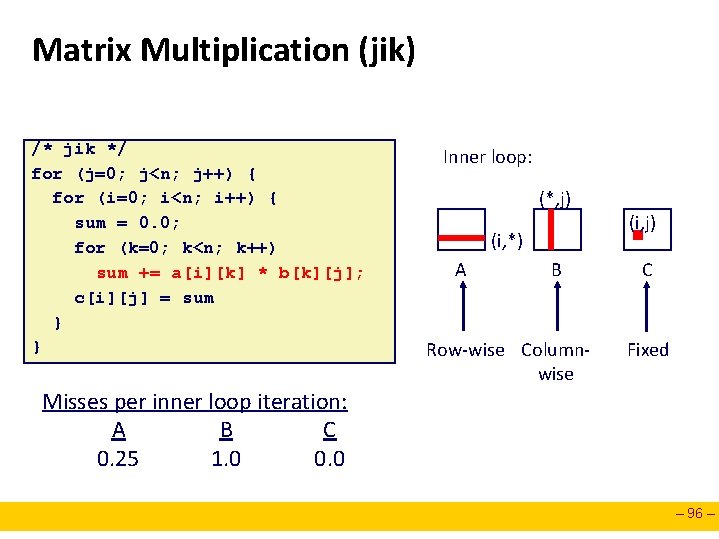
Matrix Multiplication (jik) /* jik */ for (j=0; j<n; j++) { for (i=0; i<n; i++) { sum = 0. 0; for (k=0; k<n; k++) sum += a[i][k] * b[k][j]; c[i][j] = sum } } Inner loop: (*, j) (i, *) A B Row-wise Columnwise (i, j) C Fixed Misses per inner loop iteration: A B C 0. 25 1. 0 0. 0 – 96 –

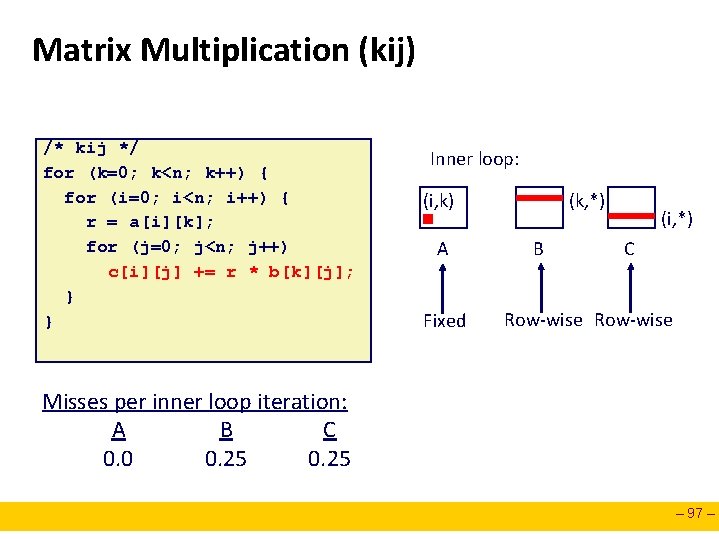
Matrix Multiplication (kij) /* kij */ for (k=0; k<n; k++) { for (i=0; i<n; i++) { r = a[i][k]; for (j=0; j<n; j++) c[i][j] += r * b[k][j]; } } Inner loop: (i, k) A Fixed (k, *) B (i, *) C Row-wise Misses per inner loop iteration: A B C 0. 0 0. 25 – 97 –

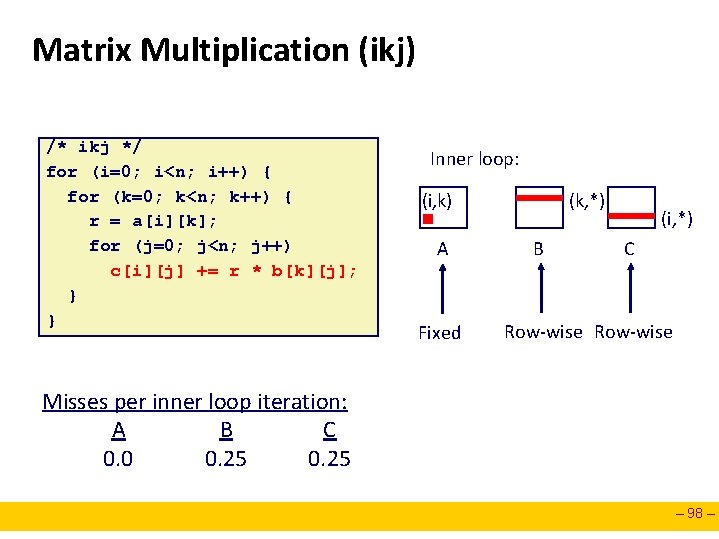
Matrix Multiplication (ikj) /* ikj */ for (i=0; i<n; i++) { for (k=0; k<n; k++) { r = a[i][k]; for (j=0; j<n; j++) c[i][j] += r * b[k][j]; } } Inner loop: (i, k) A Fixed (k, *) B (i, *) C Row-wise Misses per inner loop iteration: A B C 0. 0 0. 25 – 98 –

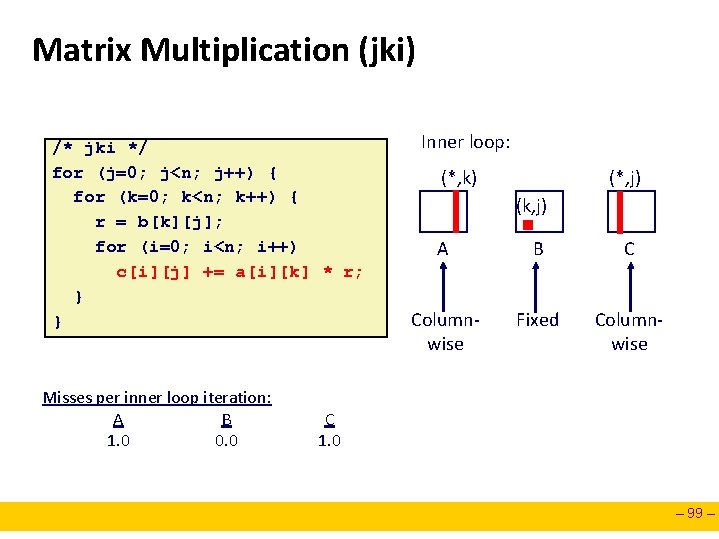
Matrix Multiplication (jki) /* jki */ for (j=0; j<n; j++) { for (k=0; k<n; k++) { r = b[k][j]; for (i=0; i<n; i++) c[i][j] += a[i][k] * r; } } Misses per inner loop iteration: A B 1. 0 0. 0 Inner loop: (*, k) (*, j) (k, j) A B C Columnwise Fixed Columnwise C 1. 0 – 99 –

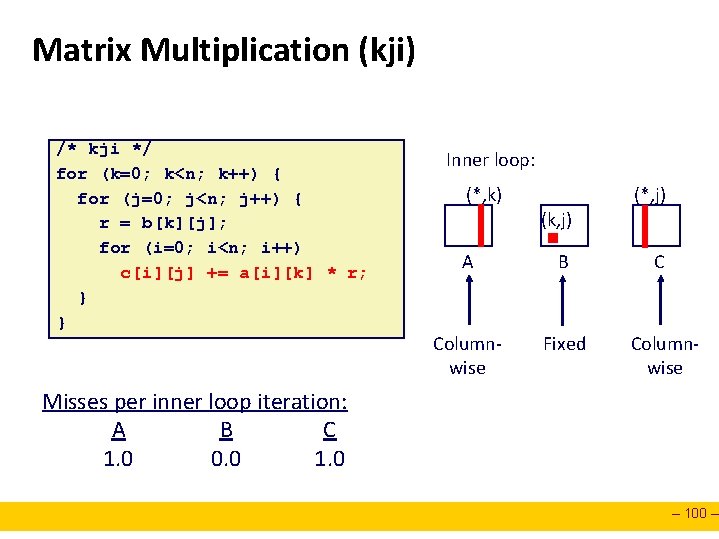
Matrix Multiplication (kji) /* kji */ for (k=0; k<n; k++) { for (j=0; j<n; j++) { r = b[k][j]; for (i=0; i<n; i++) c[i][j] += a[i][k] * r; } } Inner loop: (*, k) (*, j) (k, j) A B C Columnwise Fixed Columnwise Misses per inner loop iteration: A B C 1. 0 0. 0 1. 0 – 100 –

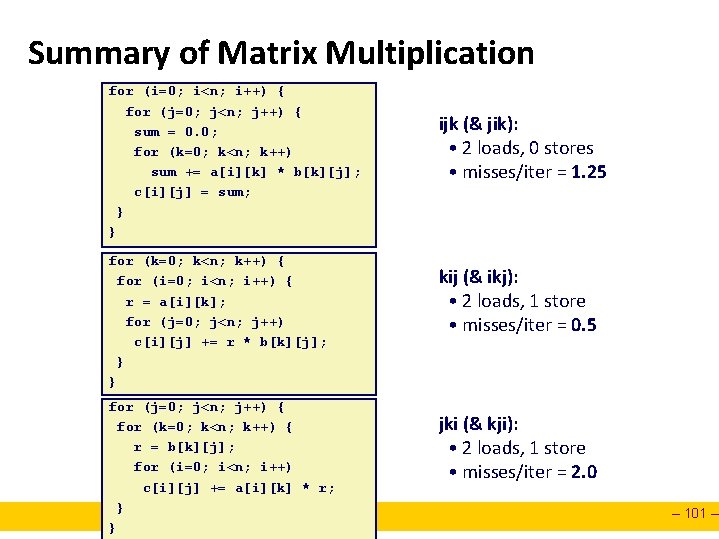
Summary of Matrix Multiplication for (i=0; i<n; i++) { for (j=0; j<n; j++) { sum = 0. 0; for (k=0; k<n; k++) sum += a[i][k] * b[k][j]; c[i][j] = sum; } } for (k=0; k<n; k++) { for (i=0; i<n; i++) { r = a[i][k]; for (j=0; j<n; j++) c[i][j] += r * b[k][j]; } } for (j=0; j<n; j++) { for (k=0; k<n; k++) { r = b[k][j]; for (i=0; i<n; i++) c[i][j] += a[i][k] * r; } } ijk (& jik): • 2 loads, 0 stores • misses/iter = 1. 25 kij (& ikj): • 2 loads, 1 store • misses/iter = 0. 5 jki (& kji): • 2 loads, 1 store • misses/iter = 2. 0 – 101 –

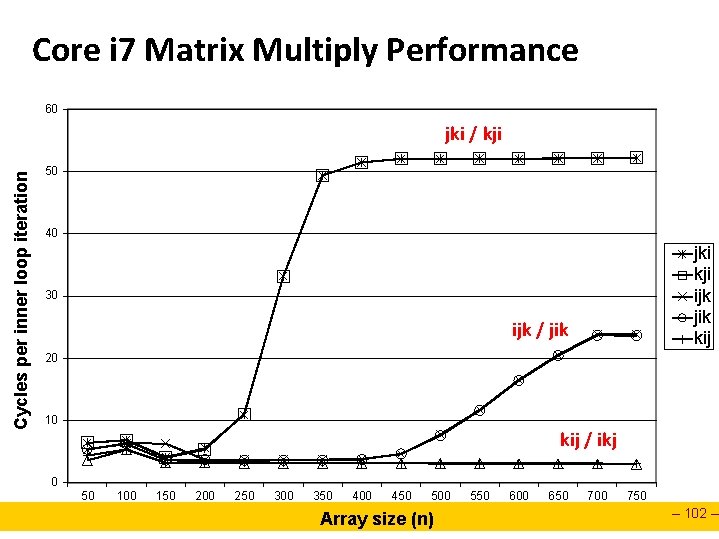
Core i 7 Matrix Multiply Performance 60 Cycles per inner loop iteration jki / kji 50 40 jki kji ijk jik kij 30 ijk / jik 20 10 kij / ikj 0 50 100 150 200 250 300 350 400 450 500 Array size (n) 550 600 650 700 750 – 102 –

Today Cache organization and operation Performance impact of caches n The memory mountain Rearranging loops to improve spatial locality n Using blocking to improve temporal locality n – 103 –

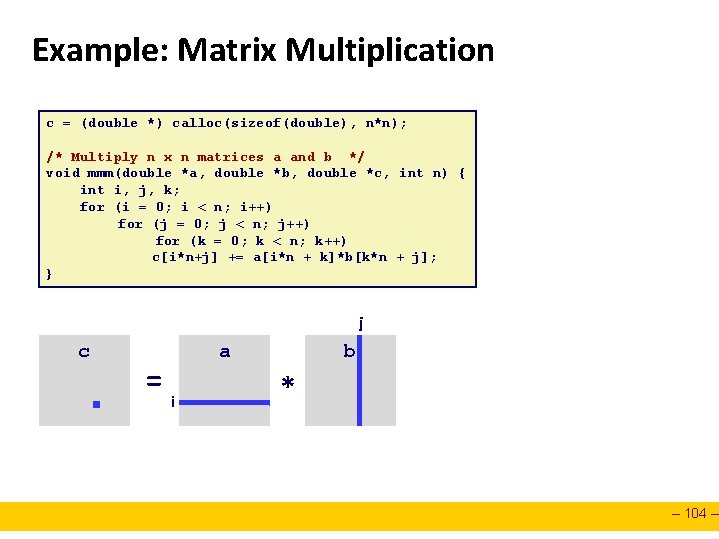
Example: Matrix Multiplication c = (double *) calloc(sizeof(double), n*n); /* Multiply n x n matrices a and b */ void mmm(double *a, double *b, double *c, int n) { int i, j, k; for (i = 0; i < n; i++) for (j = 0; j < n; j++) for (k = 0; k < n; k++) c[i*n+j] += a[i*n + k]*b[k*n + j]; } j c = a i b * – 104 –

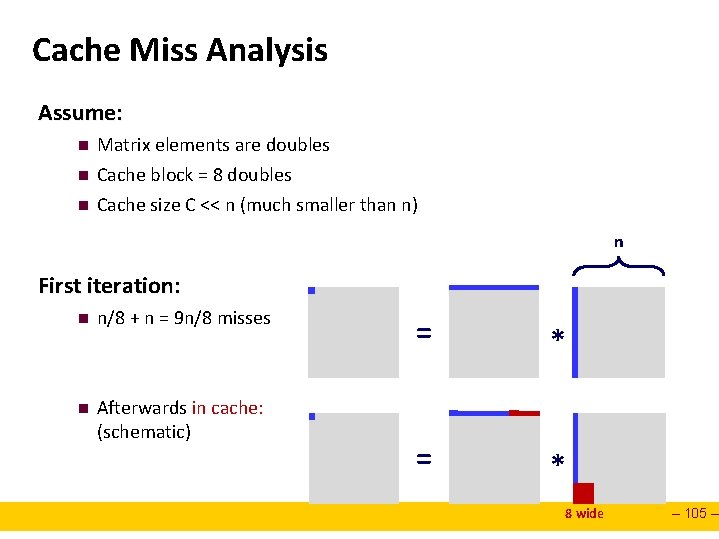
Cache Miss Analysis Assume: n n n Matrix elements are doubles Cache block = 8 doubles Cache size C << n (much smaller than n) n First iteration: n n/8 + n = 9 n/8 misses n Afterwards in cache: (schematic) = * 8 wide – 105 –

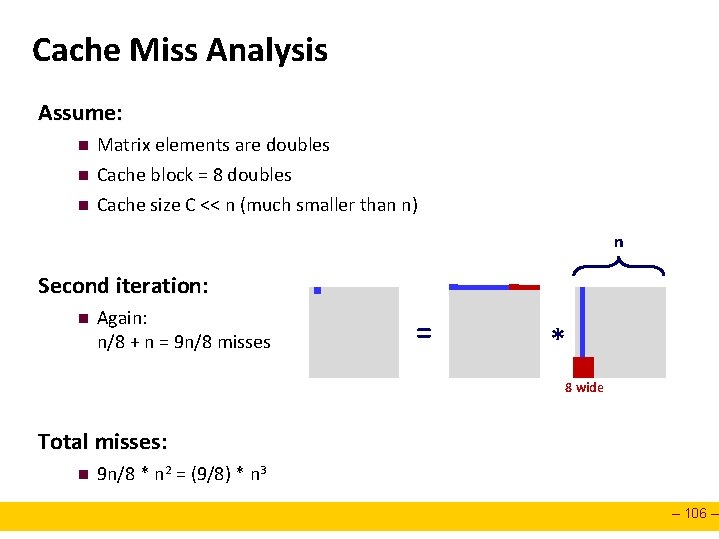
Cache Miss Analysis Assume: n n n Matrix elements are doubles Cache block = 8 doubles Cache size C << n (much smaller than n) n Second iteration: n Again: n/8 + n = 9 n/8 misses = * 8 wide Total misses: n 9 n/8 * n 2 = (9/8) * n 3 – 106 –

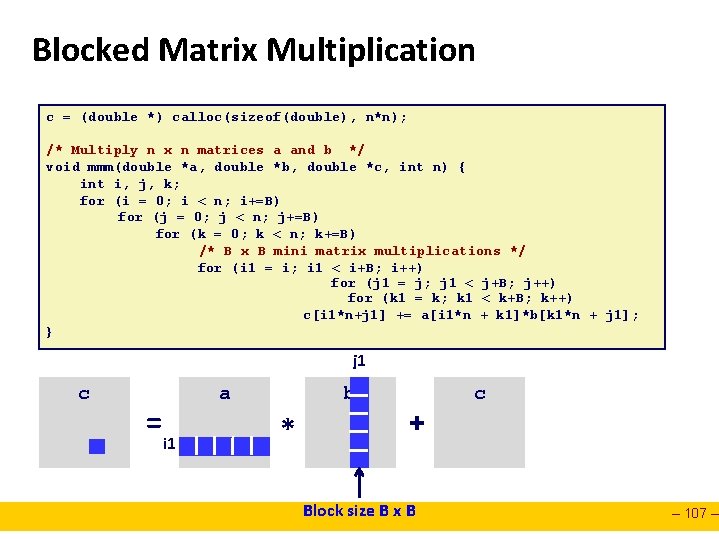
Blocked Matrix Multiplication c = (double *) calloc(sizeof(double), n*n); /* Multiply n x n matrices a and b */ void mmm(double *a, double *b, double *c, int n) { int i, j, k; for (i = 0; i < n; i+=B) for (j = 0; j < n; j+=B) for (k = 0; k < n; k+=B) /* B x B mini matrix multiplications */ for (i 1 = i; i 1 < i+B; i++) for (j 1 = j; j 1 < j+B; j++) for (k 1 = k; k 1 < k+B; k++) c[i 1*n+j 1] += a[i 1*n + k 1]*b[k 1*n + j 1]; } j 1 c = a i 1 b * + Block size B x B c – 107 –

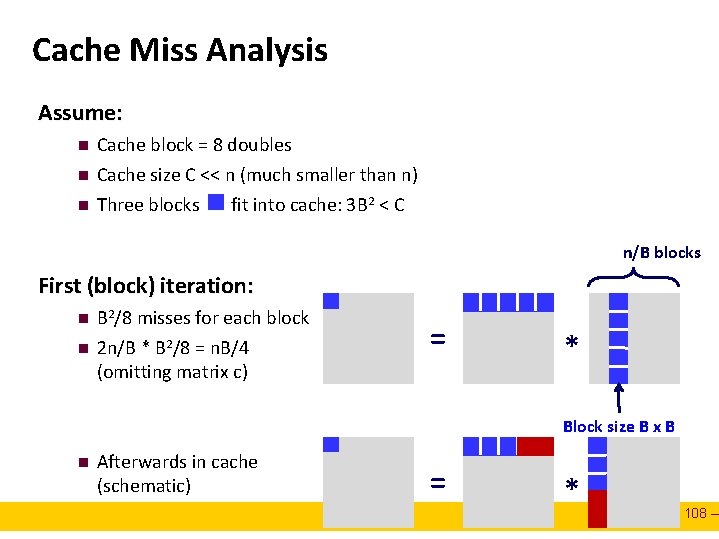
Cache Miss Analysis Assume: n n n Cache block = 8 doubles Cache size C << n (much smaller than n) Three blocks fit into cache: 3 B 2 < C n/B blocks First (block) iteration: n n B 2/8 misses for each block 2 n/B * B 2/8 = n. B/4 (omitting matrix c) = * Block size B x B n Afterwards in cache (schematic) = * – 108 –

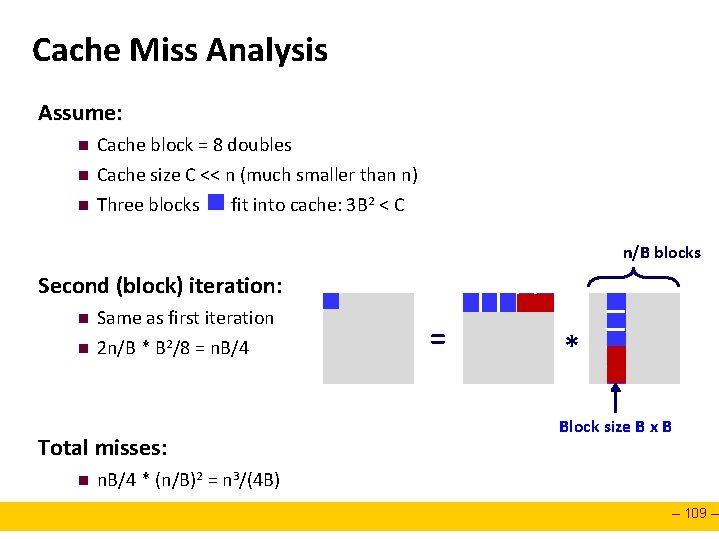
Cache Miss Analysis Assume: n n n Cache block = 8 doubles Cache size C << n (much smaller than n) Three blocks fit into cache: 3 B 2 < C n/B blocks Second (block) iteration: n n Same as first iteration 2 n/B * B 2/8 = n. B/4 Total misses: n = * Block size B x B n. B/4 * (n/B)2 = n 3/(4 B) – 109 –

Summary No blocking: (9/8) * n 3 Blocking: 1/(4 B) * n 3 Suggest largest possible block size B, but limit 3 B 2 < C! Reason for dramatic difference: n Matrix multiplication has inherent temporal locality: l Input data: 3 n 2, computation 2 n 3 l Every array elements used O(n) times! n But program has to be written properly – 110 –

Concluding Observations Programmer can optimize for cache performance n n How data structures are organized How data are accessed l Nested loop structure l Blocking is a general technique All systems favor “cache friendly code” n Getting absolute optimum performance is very platform specific l Cache sizes, line sizes, associativities, etc. n Can get most of the advantage with generic code l Keep working set reasonably small (temporal locality) l Use small strides (spatial locality) – 111 –