The Lexicon Risk Management and You John Mc













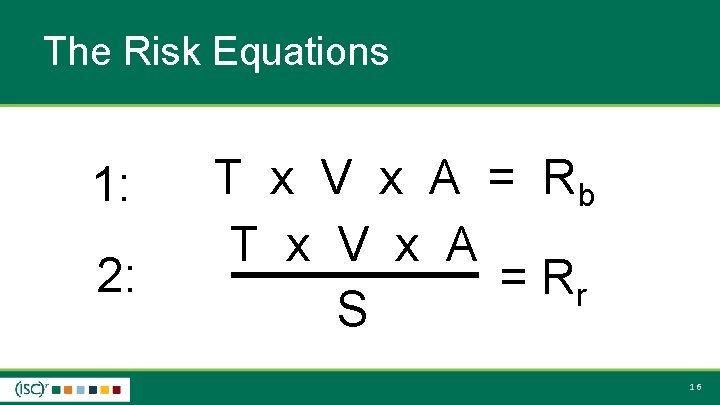








- Slides: 32


The Lexicon, Risk Management, and You John Mc. Cumber (ISC)² Director of Cybersecurity Advocacy, North America 3

Who’s this guy? » » Cybersecurity Advocate? Fellow of (ISC)² Retired Air Force Public and Private Sector Experience 4

What Are We Talking About? » » » What is a lexicon? Why do we need one? Why is it important? Relationships in risk management How you can use this information? 5

The new lexicon 6

But First… Why? 7

Cybersecurity Find out the cause of this effect, Or rather say, the cause of this defect, For this effect defective comes by cause. » - William Shakespeare, Hamlet 8

Thoughts on measurement "When you can measure what you are speaking about, and express it in numbers, you know something about it; But when you cannot measure it, when you cannot express it in numbers, your knowledge is of a meager and unsatisfactory kind: It may be the beginning of knowledge, but you have scarcely in your thoughts advanced to the stage of science. " William Thomson Lord Kelvin (1824 -1907) 9

Where’s the disconnect? Break Image Slide 10

Traditional cybersecurity » » » Technical issues only Vulnerability-centric Probes exterior boundaries Little actual analysis Based on a “state” Recommends point solutions – tied to specific vulnerabilities – based on consultant’s experience 11

Risk management definition The process of designing, developing, sustaining, and modifying operational processes and systems in consideration of applicable risks* to asset confidentiality, integrity, and availability. *Applicable risks are those reasonably expected to be realized and to cause an unacceptable impact. 12

Risk management principles » Incorporates an analytical, systems approach into the entire operational and support cycle. » Provides systems and operational leaders a reliable decision support process. » Encourages protection of only that which requires protection. » Manages cost while achieving significant performance benefits. 13

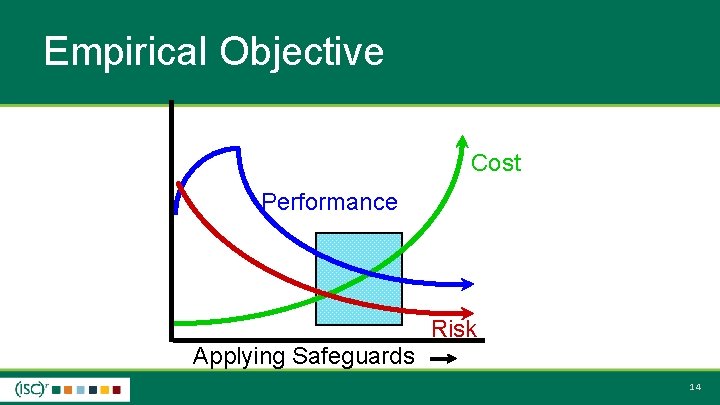
Empirical Objective Cost Performance Risk Applying Safeguards 14

Essential Elements of Risk » » Threats Assets Vulnerabilities Safeguards – – – Products Procedures People 15
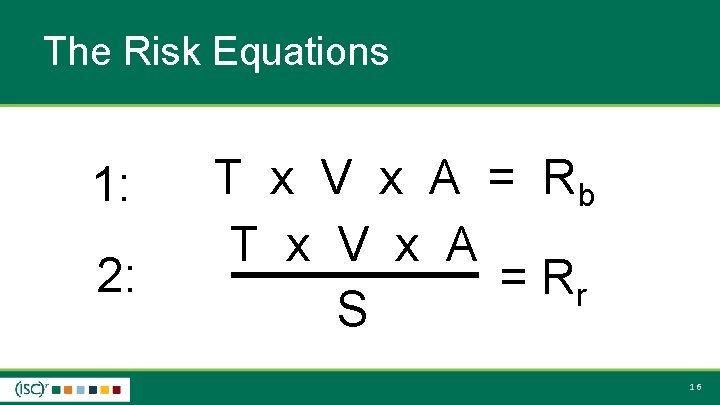
The Risk Equations 1: 2: T x V x A = Rb T x V x A = Rr S 16

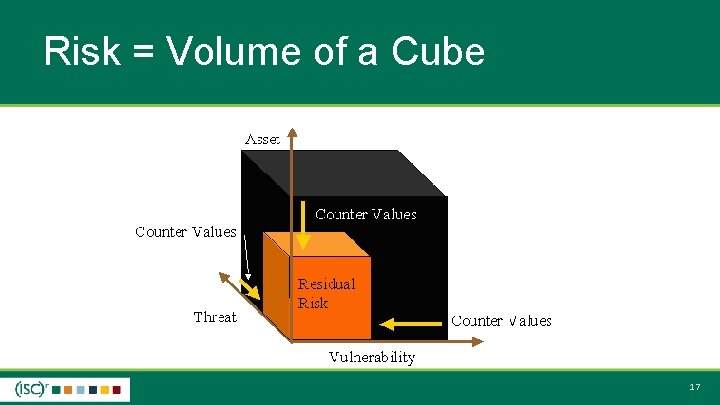
Risk = Volume of a Cube 17

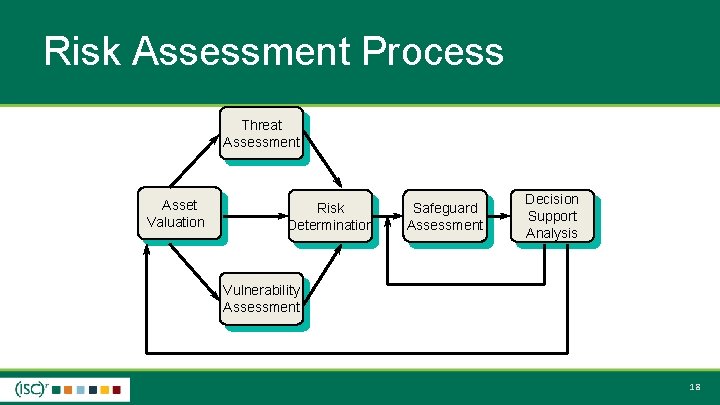
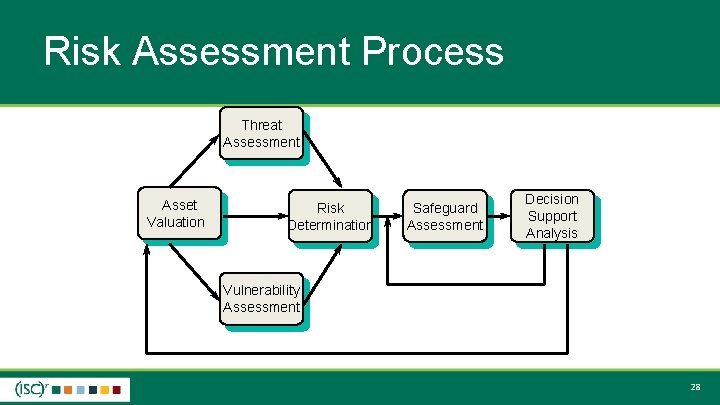
Risk Assessment Process Threat Assessment Asset Valuation Risk Determination Safeguard Assessment Decision Support Analysis Vulnerability Assessment 18

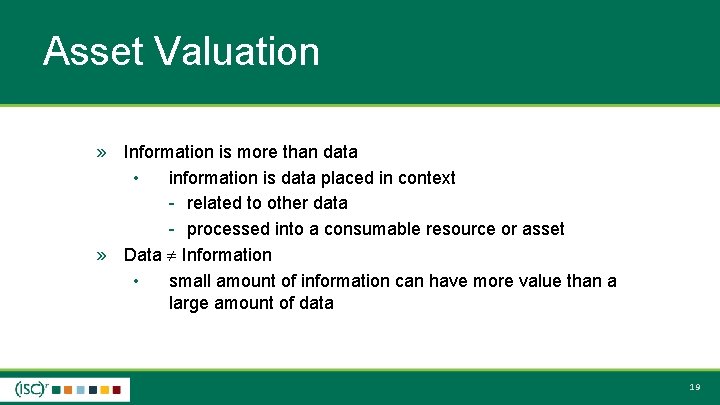
Asset Valuation » Information is more than data • information is data placed in context - related to other data - processed into a consumable resource or asset » Data Information • small amount of information can have more value than a large amount of data 19

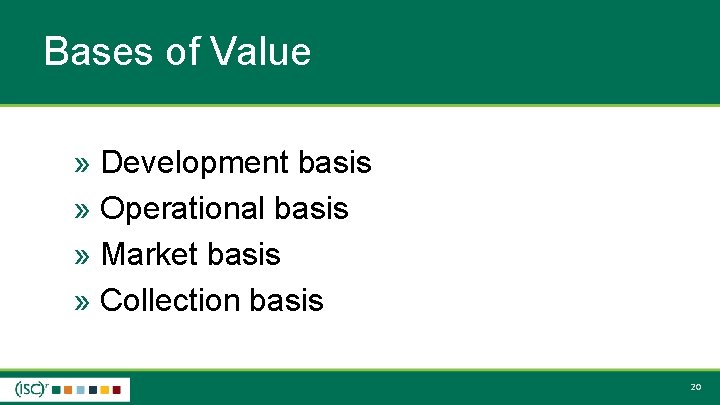
Bases of Value » Development basis » Operational basis » Market basis » Collection basis 20

Defining Operational Requirements » Capture the users needs - such as performance, mission requirements, and constraints. » Collect user perception of incident/unacceptable impact. » Have owners, consumers, and maintainers of the assets rate the areas of operational concern (confidentiality, integrity, and availability). » Asset value is the first component of risk. 21

Threat Determination » Threat factors are a product of historical data and trend projections. » Statistical and expert analysis provide default threat factor ratings. » Purpose is to identify and rank those threats that apply specifically to the assets or organization. 22

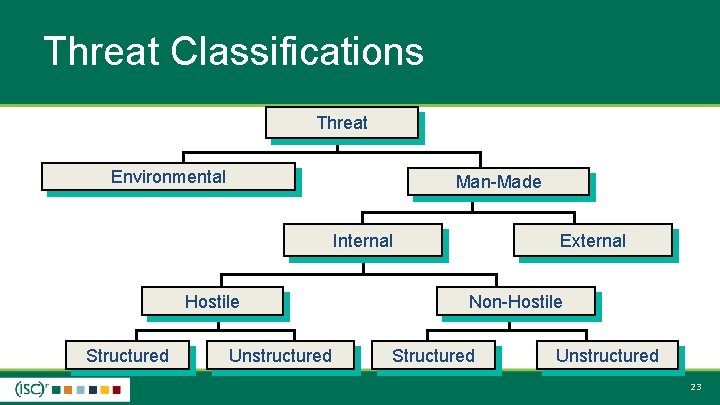
Threat Classifications Threat Environmental Man-Made Internal Hostile Structured Unstructured External Non-Hostile Structured Unstructured 23

Vulnerability Determination » Vulnerabilities are those specific technical weaknesses which can be exploited to impact an asset. • System and network hardware • System and network operating systems • System and network applications • Network protocols • Connectivity • Current safeguards • Physical environment » Necessary to identify and rank vulnerabilities 24

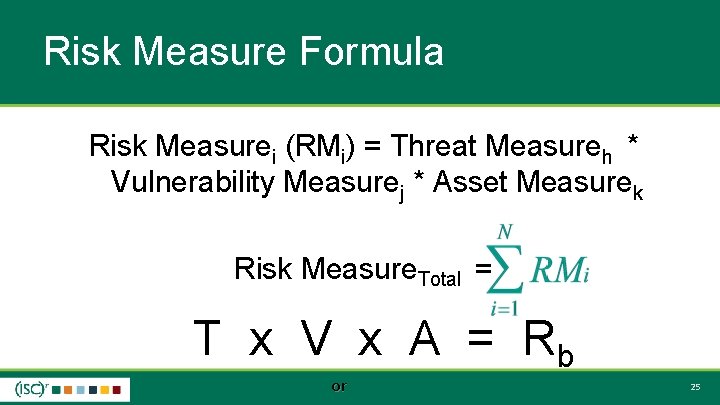
Risk Measure Formula Risk Measurei (RMi) = Threat Measureh * Vulnerability Measurej * Asset Measurek Risk Measure. Total = T x V x A = Rb or 25

Safeguard Determination » Identify applicable safeguards by considering system specific threats, vulnerabilities, assets and components. » Produce a list of valid safeguards to support the decision support cycle. 26

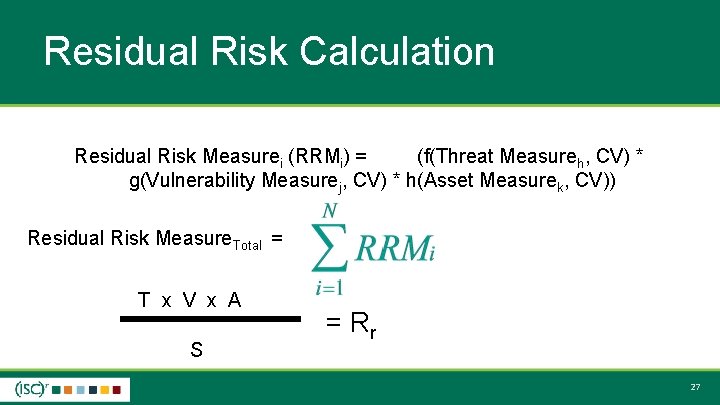
Residual Risk Calculation Residual Risk Measurei (RRMi) = (f(Threat Measureh, CV) * g(Vulnerability Measurej, CV) * h(Asset Measurek, CV)) Residual Risk Measure. Total = T x V x A S = Rr 27

Risk Assessment Process Threat Assessment Asset Valuation Risk Determination Safeguard Assessment Decision Support Analysis Vulnerability Assessment 28

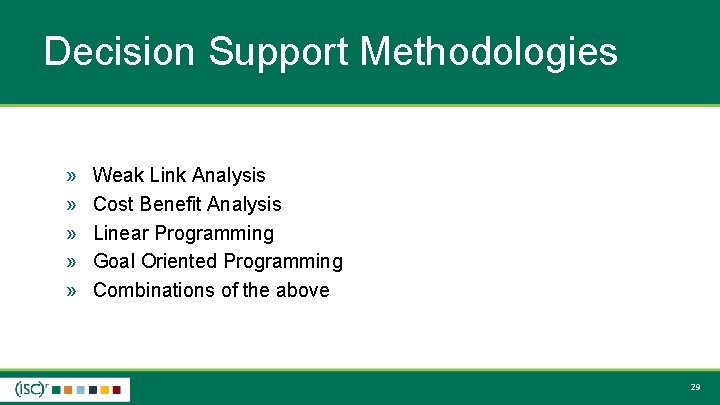
Decision Support Methodologies » » » Weak Link Analysis Cost Benefit Analysis Linear Programming Goal Oriented Programming Combinations of the above 29

Conclusion » If you can measure, you can: • justify • target • control • predict » If you can measure, you can MANAGE, and move cybersecurity from art to science. 30

What did we learn? Break Image Language is important to our 1. 2. 3. 4. 5. understanding. We need to use terms accurately. Many common risk terms have mathematical relationships. Threats should be categorized. You have an important role. 31

Learn More & Get Involved » Get the full report Hiring and Retaining Top Cybersecurity Talent at www. isc 2. org » Engage a local (ISC)² Chapter » Join community. isc 2. org » Help make a difference at www. isc 2. org/cybersecurity-advocates 32

» The End 33