The Law of Government Honeypots Anthony V Teelucksingh

















- Slides: 17

The Law of Government Honeypots Anthony V. Teelucksingh Computer Crime and Intellectual Property Section U. S. Department of Justice (202) 202 -514 -1026

Honeypots; Topics Legal Issues Search & Seizure Electronic Surveillance Charging Entrapment Collateral Damage

Honeypots Generally Uncharted Legal Water Get Counsel Involved Pre-Development

Honeypots; Legal Issues Honeypot are Undercover Operations Search & Seizure & Electronic Surveillance n n Fourth Amendment Wiretap Act Pen Register/Trap and Trace Electronic Communications Privacy Act

Honeypots; The Constitution Fourth Amendment: Unreasonable Search and Seizure Collection of Electronic Communications can be a search and seizure Test: Reasonable Expectation of Privacy n n Hackers Do Not Have Such Expectation But Other Users on Honeypot May

Honeypots; The Wiretap Act Value Derived from Monitoring Activity of Would-Be Attackers To Legally Intercept Communications, Exception to Wiretap Act Must Apply Consider These Exceptions Computer Trespasser Exception Party to the Communication or Consent of a Party to the Communication Exception Provider Exception (System Protection)

Honeypots; The Computer Trespasser Exception Government may monitor “trespasser” No contractual relationship or authority to be on computer Use care if “advertising” honeypot; may imply authority to use Provider must authorized interception Government must do the monitoring Only trespasser’s communications intercepted Relevant to an ongoing “investigation”

Honeypots; Party and Consent of a Party Exception A party to a communication can intercept or give consent to intercept Two ways this may help Banner the System (but is imperfect solution) The honeypot may be a party in some cases (but risky in other cases, e. g. , IRC)

Honeypots; The Provider Exception To Apply, the Monitoring Must be Done to Protect the Provider’s Rights or Property May have Some Limited Application to Honeypots Helpful Facts: Separate Sys Admin Tasks from Investigatory Functions Honeypot Associated with Production Servers

Honeypots; Examples Suspicious Traffic Routed Hide Among Production Servers

Honeypots; Pen/Trap Monitoring only addressing information (to the exclusion of content), then the Pen Register, Trap and Trace statute would apply If have exception to Wiretap Act to intercept communications, then have argument that ok to collect related info

Honeypots; ECPA Rules May Limit Voluntary Disclosure of Info Stored on Honeypot Process Necessary to Compel Production Do Voluntary Disclosure Limits Apply? Only if services offered “to the public” Not Clear what this Condition Means Avoid Rapid Collection of Info that, although in Stored State, has been Stored only Short Time; Looks Like Wiretap

Honeypots; Other Rules Other Laws May Apply Too E-Government Act of 2002 Rules on Use of Cookies Rules on Privacy Policies Internal Agency Regulations on Internet Resources Populating Honeypot with Contraband Make Sure You Know What Rules Apply and What Waivers are Available DOD-Specific Rules

Honeypots; Charges Know your Goal before Designing If Purpose to Prosecute n n Identify Charges of Interest Attempt (Impossibility) Other Victims Warez, etc. Consider Jury Appeal

Honeypots; Entrapment is a potential factor in any undercover To find entrapment in most jurisdictions: The government induced the illegal conduct and The defendant was not predisposed to engage in the illegal conduct. Entrapment is unlikely a good defense in pure honeypot cases Still, keep it in mind Trappings of Honeypot (e. g. , promotion, password or vulnerability distribution) If core of charge is based on gov’t supplying necessary item available only through the government

Honeypots; Collateral Damage Do No Harm Potential lawsuits Downstream victims of intrusions Launch Pad for Denial of Service Attack Drop or Distribution Site for Contraband Plan Ahead Evidence of Criminal Activity Evidence of National Security Breach Victim Notification Issues Can Take Significant Resources

Where To Get More Information Computer Crime Section: (202) 514 -1026 E-Mail: anthony. teelucksingh@usdoj. gov Computer Crime Section’s Web page:
 Anthony teelucksingh
Anthony teelucksingh Honeypots and honeynets
Honeypots and honeynets Newton's first law and second law and third law
Newton's first law and second law and third law Si unit of newton's first law
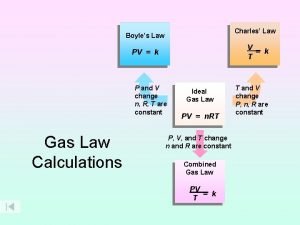
Si unit of newton's first law Boyle's law charles law avogadro's law
Boyle's law charles law avogadro's law Constant of avogadro's law
Constant of avogadro's law National government vs federal government
National government vs federal government Hát kết hợp bộ gõ cơ thể
Hát kết hợp bộ gõ cơ thể Ng-html
Ng-html Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Tư thế worm breton
Tư thế worm breton Hát lên người ơi alleluia
Hát lên người ơi alleluia Môn thể thao bắt đầu bằng từ chạy
Môn thể thao bắt đầu bằng từ chạy Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công của trọng lực
Công của trọng lực