The Internet Intranets and Extranets Chapter 7 Chapter


















































- Slides: 87

The Internet, Intranets, and Extranets Chapter 7

Chapter 7, The Internet, Intranets, and Extranets, covers the Internet and its use and effects. After studying chapter 7, you should be able to address the learning objectives described in the next 3 slides. Chapter 7 Principles of Information Systems, Fifth Edition Slide 2

Learning Objectives Define how the Internet works Describe the services associated with the Internet Describe the World Wide Web Define the terms intranet and extranet and discuss how organizations use them Chapter 7 Principles of Information Systems, Fifth Edition Slide 3

The Internet is relatively young, and its services and features are evolving. Technologies pioneered by the Internet are currently being used by organizations to create intranets and extranets. Chapter 7 Principles of Information Systems, Fifth Edition Slide 4

Learning Objectives Identify who is using the Web to conduct business Discuss some pros and cons of Web shopping Identify several issues associated with the use of networks Chapter 7 Principles of Information Systems, Fifth Edition Slide 5

Before the Internet is routinely used for business, many issues, such as those related to service, privacy, and security, must be resolved. Chapter 7 Principles of Information Systems, Fifth Edition Slide 6

Learning Objectives Outline a process for creating web pages Describe Java and its potential impact on the software world Chapter 7 Principles of Information Systems, Fifth Edition Slide 7

The Internet is impacting business and individuals. It’s important to understand some of its underlying technologies, such as web page creation and Java. Chapter 7 Principles of Information Systems, Fifth Edition Slide 8

Use and Functioning of the Internet

The Internet is an international collection of computer networks connected together by routers. Devices use specific protocols to communicate over the Internet and individuals and business access it through Internet Service Providers, or ISPs. Chapter 7 Principles of Information Systems, Fifth Edition Slide 10

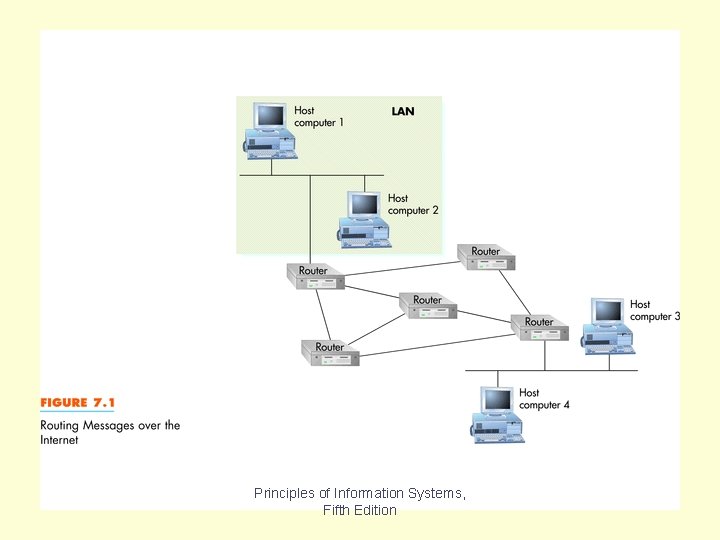
Use and Functioning of the Internet Fig 7. 1 Principles of Information Systems, Fifth Edition

Figure 7. 1 shows how the Internet is composed of many networks. These networks are connected together using routers. Chapter 7 Principles of Information Systems, Fifth Edition Slide 12

Use and Functioning of the Internet Interconnected networks Global though US is the largest user Internet Protocol (IP) Research for a faster Internet l Internet 2 (I 2) l Next Generation Internet (NGI) l Corporate efforts Chapter 7 Principles of Information Systems, Fifth Edition Slide 13

The United States is the largest user of the Internet today, although use by other nations is increasing rapidly. There is no single point of registration and control for the network; it has no central infrastructure. The many networks communicate by using the Internet Protocol, common standards for routing messages. Universities, corporations, and the government are conducting research to speed Internet access. The Next Generation Internet, or Internet 2, is probably the most publicized effort. Chapter 7 Principles of Information Systems, Fifth Edition Slide 14

How the Internet Works Hosts Routers forward packets to other networks Internet Protocol Stack (TCP/IP) Internet Protocol (IP) l Transport Control Protocol (TCP) l Backbones Chapter 7 Principles of Information Systems, Fifth Edition Slide 15

Computers on the Internet, whether mainframes or PCs, are called hosts. Routers forward messages in pieces, called packets, on the Internet, from one network to another, using the Internet Protocol. When a host sends a message to a computer on a different network, it goes first to a router. The router sends it to another network, where another router may pass it on. All networks connected to the Internet use the Internet Protocol stack, also called TCP/IP. IP is the network layer protocol that helps route packets from one network to another. Chapter 7 Principles of Information Systems, Fifth Edition Slide 16

TCP, Transport Control Protocol, is one of several other protocols included in the Internet Protocol stack used by most hosts on the Internet. Networks using TCP/IP standards connect to one of the Internet’s fast, long distance communications links, a backbone, to communicate with other networks on the Internet. Chapter 7 Principles of Information Systems, Fifth Edition Slide 17

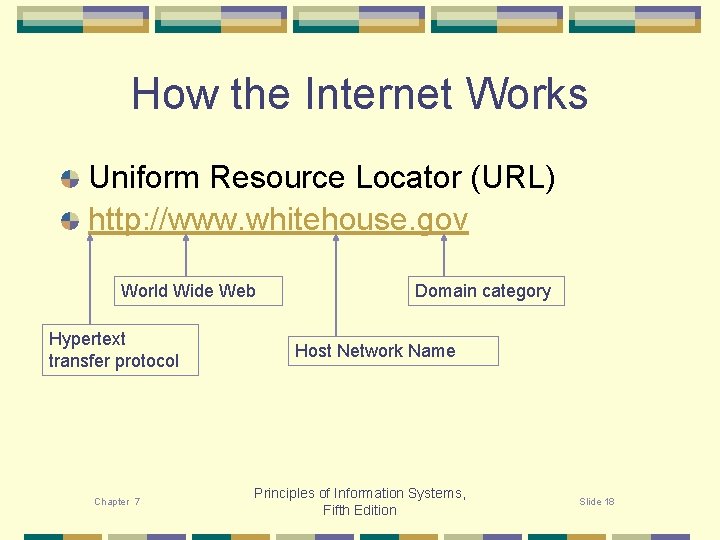
How the Internet Works Uniform Resource Locator (URL) http: //www. whitehouse. gov World Wide Web Hypertext transfer protocol Chapter 7 Domain category Host Network Name Principles of Information Systems, Fifth Edition Slide 18

Each host on the Internet has been assigned a unique address to distinguish it from other computers on the Internet. The address is a long sequence of numbers – easy for computers and routers to process, but hard for people. Unique logical names, called URLs, or uniform resource locators, are also assigned to correspond with the numeric address, making it easier for people to remember. Chapter 7 Principles of Information Systems, Fifth Edition Slide 19

Consider the URL for the White House, http: //www. whitehouse. gov/. The “http” signifies a specific Internet protocol used by most web browser and web server software. The “www” means this site is part of the “World Wide Web”, one of several Internet services. “Whitehouse. gov” is the domain name. Domain names follow specific rules. Dots separate the components of the address, and there will be at least two components, as in whitehouse. gov. Chapter 7 Principles of Information Systems, Fifth Edition Slide 20

With the exception of most US domain names, the rightmost part is typically a country designator. For example, the National Library of Australia has the URL http: //www. nla. gov. au/, where “au” designates Australia. The leftmost part of the domain name identifies the host network, such as “nla” or “whitehouse”. The rightmost part of a US domain name (and the part next to the country code for a non. US name) designates the category, or type, of the site. Here, the category is “gov”, for government. Chapter 7 Principles of Information Systems, Fifth Edition Slide 21

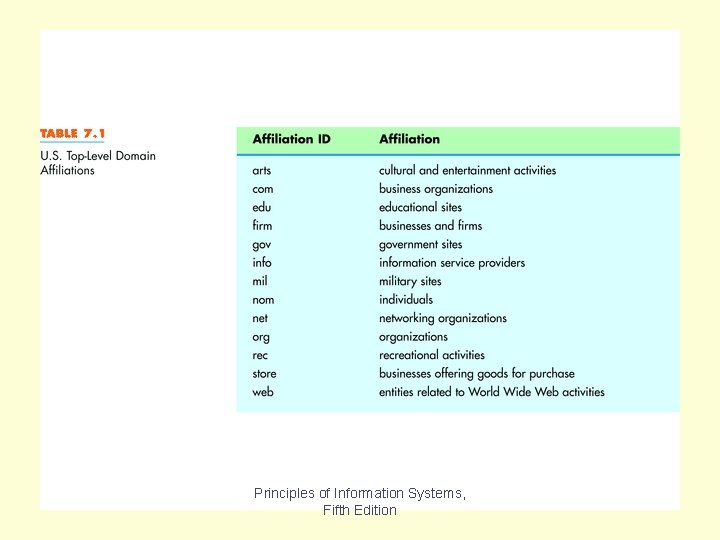
Table 7. 1 Principles of Information Systems, Fifth Edition

Table 7. 1 shows various top-level domain extensions. Chapter 7 Principles of Information Systems, Fifth Edition Slide 23

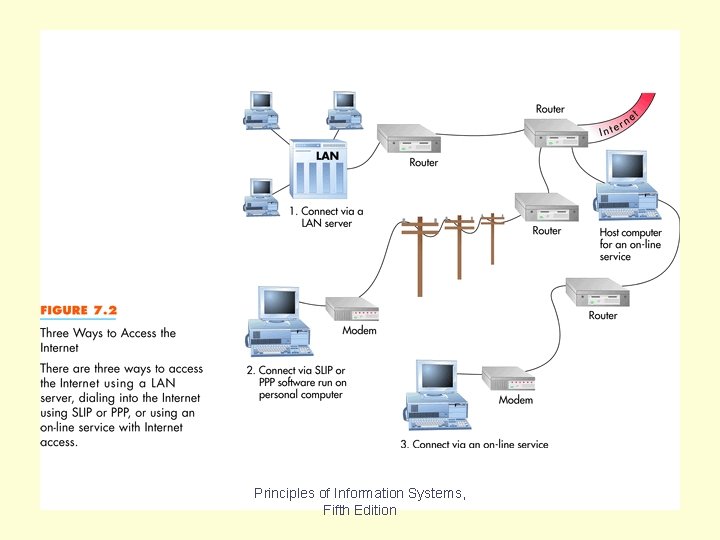
Accessing the Internet Fig 7. 2 Principles of Information Systems, Fifth Edition

As shown in Figure 7. 2, there are 3 ways to access the Internet. First, you can connect to the Internet using a LAN server. This is often found in businesses or schools where individual PCs are connected to Local Area Networks, or LANs. One of the nodes on the LAN is a server connected to the Internet, generally at 56 kbps or faster. Using your residential phone line, you can connect to and Internet Service Provider using SLIP or PPP, 2 data link layer protocols used for dial-up Internet access. You can also connect from a home phone using an on-line service provider such as America Online or Microsoft Network. Chapter 7 Principles of Information Systems, Fifth Edition Slide 25

The latter two ways access the Internet at speeds lower than 56 kilobits per seconds. In many parts of the country, residential Internet access is also available through cable modems, satellite, ISDN or DSL services. These connections are typically faster than dialing up an ISP using your normal phone service. Chapter 7 Principles of Information Systems, Fifth Edition Slide 26

Internet Service Providers (ISPs) Provide Internet access to account holders Monthly fee varies Some are free Chapter 7 Principles of Information Systems, Fifth Edition Slide 27

An ISP is any company that provides internet access to individuals or organizations. ISPs don’t normally offer services as extensive as those on on-line services such as America Online, although ISP’s offerings are continually becoming more extensive. Some ISPs, such as Netzero, offer no-fee Internet access to subscribers. Free ISPs typically have more ads on their websites than do others, since they earn income from the ads. Chapter 7 Principles of Information Systems, Fifth Edition Slide 28

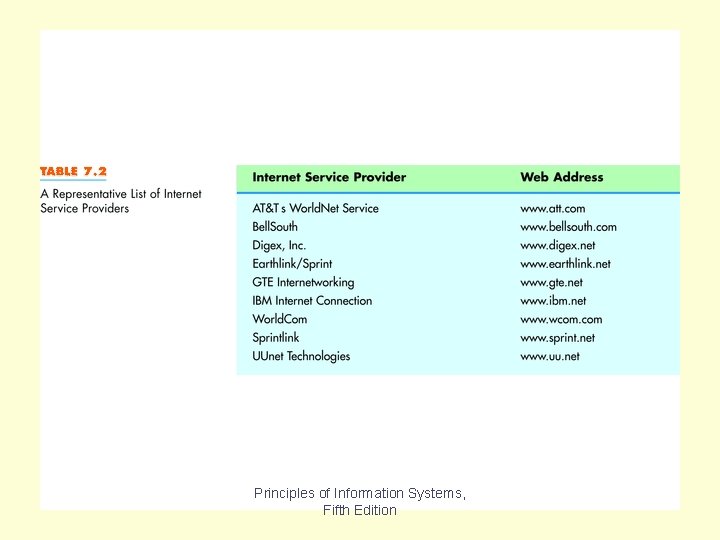
Table 7. 2 Principles of Information Systems, Fifth Edition

Table 7. 2 shows a representative list of ISPs which charge customers a monthly fee. Often, fee-based ISPs, provide faster connections to the Internet, since free ISPs are often used by numerous people. Chapter 7 Principles of Information Systems, Fifth Edition Slide 30

Internet Services

The Internet has impacted business and individuals because of the many uses and services it provides. Chapter 7 Principles of Information Systems, Fifth Edition Slide 32

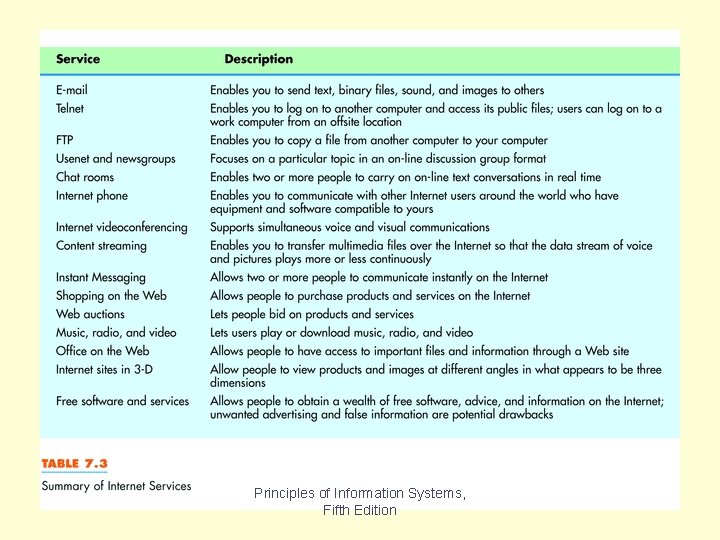
Table 7. 3 Principles of Information Systems, Fifth Edition

Table 7. 3 summarizes services offered on the Internet. This list is continually expanding as the Internet is put to new uses. We’ll discuss some of the more frequently used services in the next few slides. Chapter 7 Principles of Information Systems, Fifth Edition Slide 34

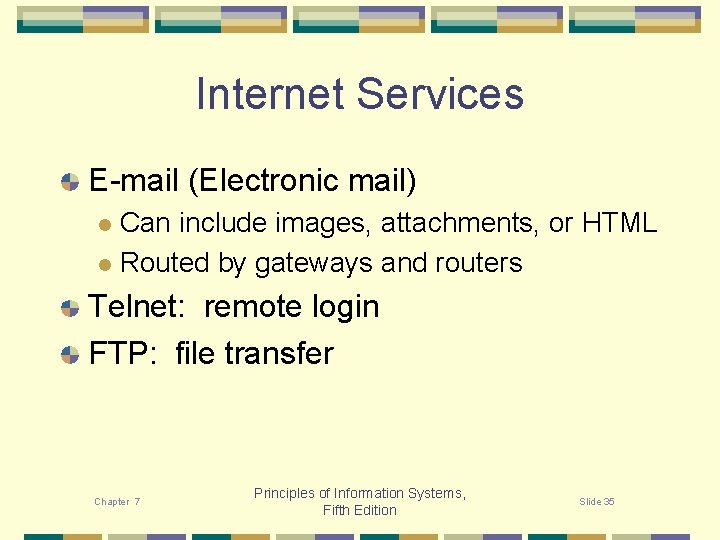
Internet Services E-mail (Electronic mail) Can include images, attachments, or HTML l Routed by gateways and routers l Telnet: remote login FTP: file transfer Chapter 7 Principles of Information Systems, Fifth Edition Slide 35

Since e-mail travels across multiple networks, gateways may be used to translate the format of an e-mail message into one the next network can understand. Routers and gateways use the address on the “to” line of the e-mail message to send the message to networks that get it to its destination. E-mail has changed the way people communicate. Unlike using the telephone, e-mail communications can be handled on your schedule, at your pace. Chapter 7 Principles of Information Systems, Fifth Edition Slide 36

Telnet, or remote login, is a terminal emulation protocol that lets you log on to remote computers on the Internet & access public files. FTP, or file transfer protocol, is a protocol for transferring files between computers on the Internet. FTP allows you to copy files, such as software, from a remote computer. Before the existence of the world wide web, Telnet and FTP were the main way to access resources on the Internet. Chapter 7 Principles of Information Systems, Fifth Edition Slide 37

Internet Services Table 7. 4 Principles of Information Systems, Fifth Edition

A Usenet is a virtual asynchronous forum for an electronic group, or Newsgroup, to share messages about particular topics. Users send e-mail to the Usenet server, where all e-mail is stored and can be read by all group members. Representative Usenet Newsgroups, such as those focusing on Elvis, the LA Lakers, or music, are listed in Table 7. 4. Some newsgroups are moderated; that is, a person screens incoming email before it is posted to be sure it is appropriate. However, many are unmoderated. Chapter 7 Principles of Information Systems, Fifth Edition Slide 39

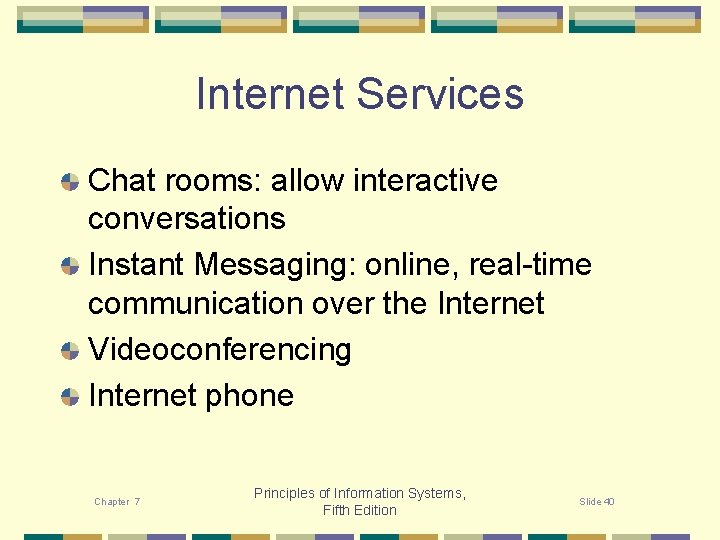
Internet Services Chat rooms: allow interactive conversations Instant Messaging: online, real-time communication over the Internet Videoconferencing Internet phone Chapter 7 Principles of Information Systems, Fifth Edition Slide 40

Chat rooms allow two or more people to “converse” interactively over the Internet. Most often the conversation is typed; however, in some chat rooms, with the appropriate equipment, voice chat is possible. Instant messaging allows individuals to interact online, just as chat rooms allow real-time communication. However, instant messaging is on a smaller scale than a chat room. Some instant messaging programs also allow voice communication. Chapter 7 Principles of Information Systems, Fifth Edition Slide 41

With the appropriate hardware and software, it is possible to make phone calls over the Internet. This is an attractive option for long distance calls to avoid, or reduce, charges. Videoconferencing allows both voice and video image to be displayed in real-time for an interactive meeting. A codec is hardware used in both Internet phone and videoconferencing applications. Codecs are used to convert analog inputs, such as voice conversations or videos, into digital signals for transmission over the Internet. Chapter 7 Principles of Information Systems, Fifth Edition Slide 42

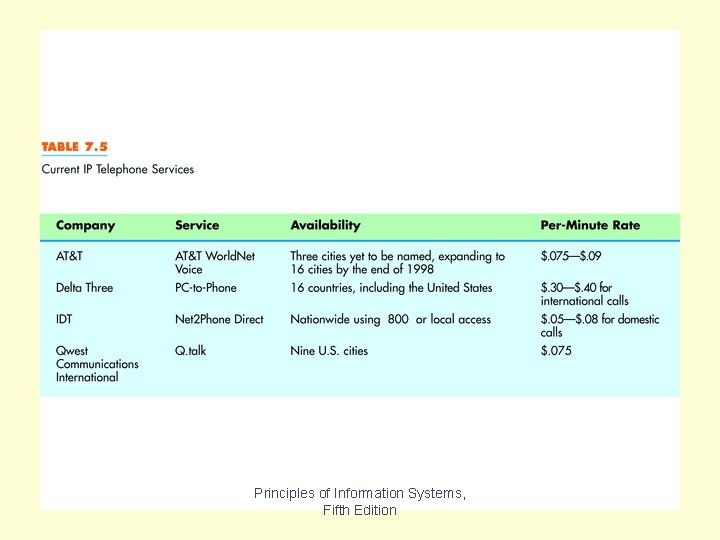
Table 7. 5 Principles of Information Systems, Fifth Edition

Table 7. 5 lists current phone service available over the Internet. Use of voice over IP may increase as new uses are found for sending voice, video and data concurrently. Chapter 7 Principles of Information Systems, Fifth Edition Slide 44

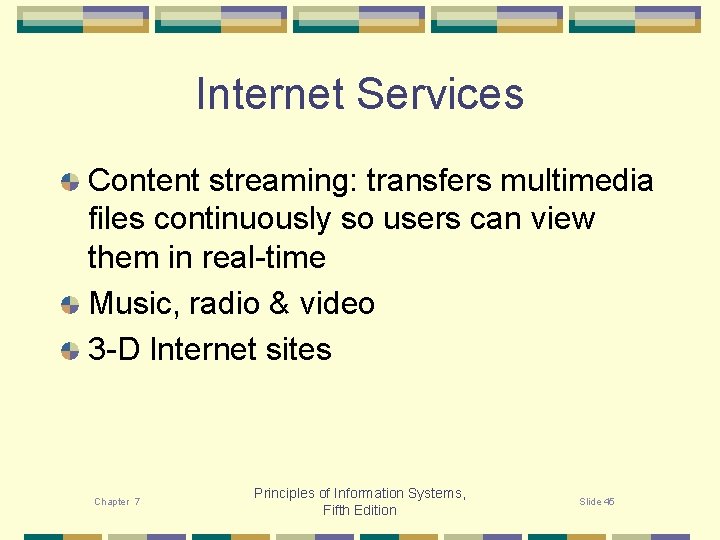
Internet Services Content streaming: transfers multimedia files continuously so users can view them in real-time Music, radio & video 3 -D Internet sites Chapter 7 Principles of Information Systems, Fifth Edition Slide 45

Content streaming is a method of transferring multimedia files so that users can view them in real-time without breaks or pauses. Large multimedia files, such as video clips, have long download times and a user might need to wait an hour before she could play the video on her machine. Content streaming allows the video to be viewed as it is being received. Music is rapidly expanding on the Internet. MP 3 is a popular format for compressed music, allowing it to be easily downloaded from the web, stored, and listened to. Chapter 7 Principles of Information Systems, Fifth Edition Slide 46

The ability to download music and movies from the Internet has the music and video industry concerned about copyright violations and reduced income. It is clear that the Internet will have a big role in shaping the music and video industries – exactly how will be seen in the next few years. Virtual reality types of applications are now on the web, and likely to increase in the near future. For example, on some sites, potential buyers can take a virtual tour of homes. People can see and interact with products, such as cars or computers, online. Chapter 7 Principles of Information Systems, Fifth Edition Slide 47

Internet Services Shopping on the Web Bots: web search tools Web Auctions Office on the web Chapter 7 Principles of Information Systems, Fifth Edition Slide 48

More and more people and business are buying on the Internet. Although the online retailers started having trouble in late 2000 and many have, and will, fail or be acquired, commerce over the Internet will increase. Bots, short for “knowledge robots”, can help you find what you want on the Internet or find the best prices. Auction websites have become very popular on the Internet auction sites, such as e. Bay, enable individuals to post items they wish to sell and receive offers, or bids from potential buyers. Chapter 7 Principles of Information Systems, Fifth Edition Slide 49

Some websites allow you to set up a virtual office for a monthly fee. Companies and individuals do this to provide contact lists, calendars, and file storage space to employees, especially those who travel. Chapter 7 Principles of Information Systems, Fifth Edition Slide 50

The World Wide Web

The World Wide Web was originally developed as an internal document management system. It has grown to a huge, global collection of independent computers, or web servers, and is the most famous Internet service. Using hypertext links, or hypermedia, a type of crossindexing tool, users can jump from one web server to another immediately. To the user, the entire web is like one giant computer. You can jump from a page on one web server to a page on a related topic that is stored on the other side of the world. Hypertext links are maintained using URLs. Chapter 7 Principles of Information Systems, Fifth Edition Slide 52

A URL is the logical address, such as www. course. com, that you type in your browser when going to a website. Web pages on web servers can contain data in any format – from ASCII characters to video images. Chapter 7 Principles of Information Systems, Fifth Edition Slide 53

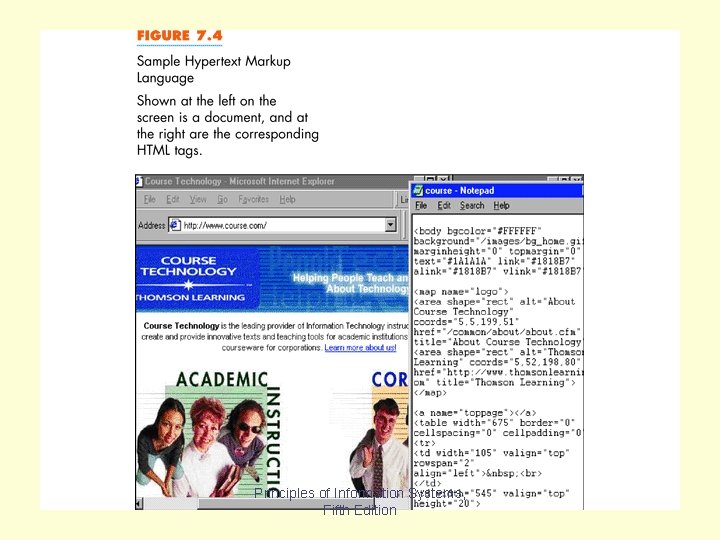
Fig 7. 4 Principles of Information Systems, Fifth Edition

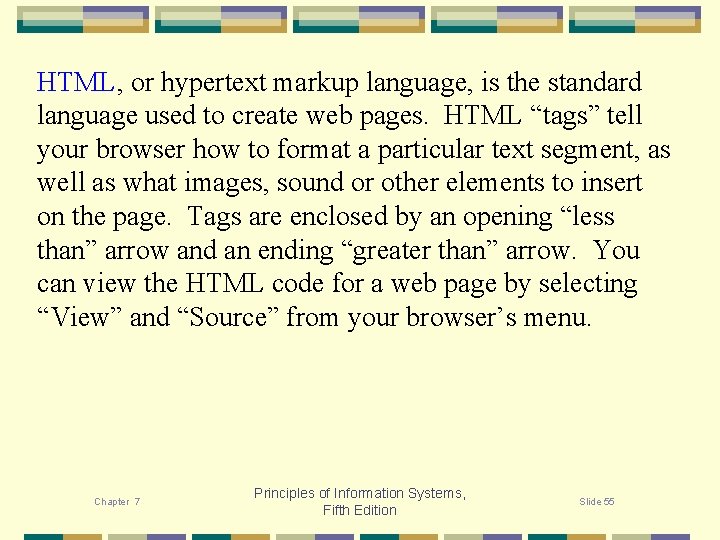
HTML, or hypertext markup language, is the standard language used to create web pages. HTML “tags” tell your browser how to format a particular text segment, as well as what images, sound or other elements to insert on the page. Tags are enclosed by an opening “less than” arrow and an ending “greater than” arrow. You can view the HTML code for a web page by selecting “View” and “Source” from your browser’s menu. Chapter 7 Principles of Information Systems, Fifth Edition Slide 55

Web Software Web browsers Search engines Keyword indexes: fast & broad l Subject indexes: focused searches l Chapter 7 Principles of Information Systems, Fifth Edition Slide 56

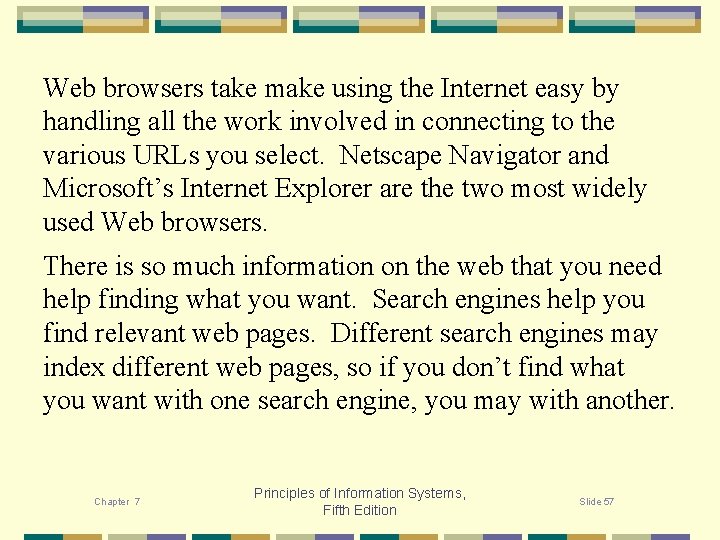
Web browsers take make using the Internet easy by handling all the work involved in connecting to the various URLs you select. Netscape Navigator and Microsoft’s Internet Explorer are the two most widely used Web browsers. There is so much information on the web that you need help finding what you want. Search engines help you find relevant web pages. Different search engines may index different web pages, so if you don’t find what you want with one search engine, you may with another. Chapter 7 Principles of Information Systems, Fifth Edition Slide 57

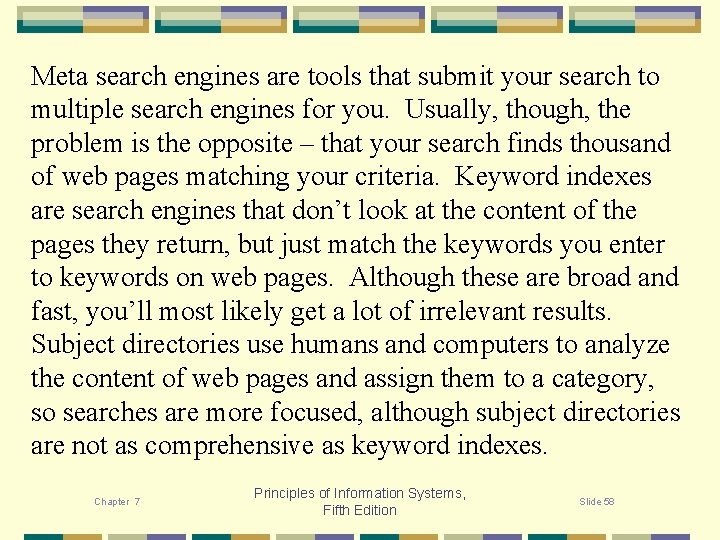
Meta search engines are tools that submit your search to multiple search engines for you. Usually, though, the problem is the opposite – that your search finds thousand of web pages matching your criteria. Keyword indexes are search engines that don’t look at the content of the pages they return, but just match the keywords you enter to keywords on web pages. Although these are broad and fast, you’ll most likely get a lot of irrelevant results. Subject directories use humans and computers to analyze the content of web pages and assign them to a category, so searches are more focused, although subject directories are not as comprehensive as keyword indexes. Chapter 7 Principles of Information Systems, Fifth Edition Slide 58

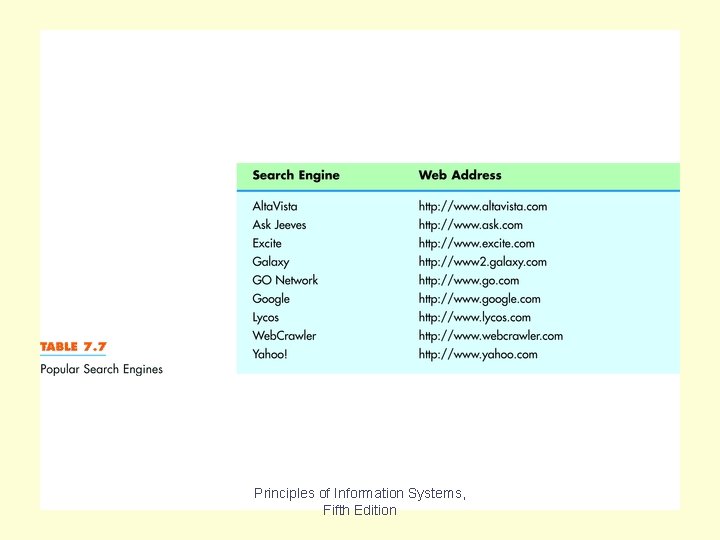
Table 7. 7 Principles of Information Systems, Fifth Edition

Table 7. 7 lists some of the popular search engines available. You’ll find more as you surf the web. Chapter 7 Principles of Information Systems, Fifth Edition Slide 60

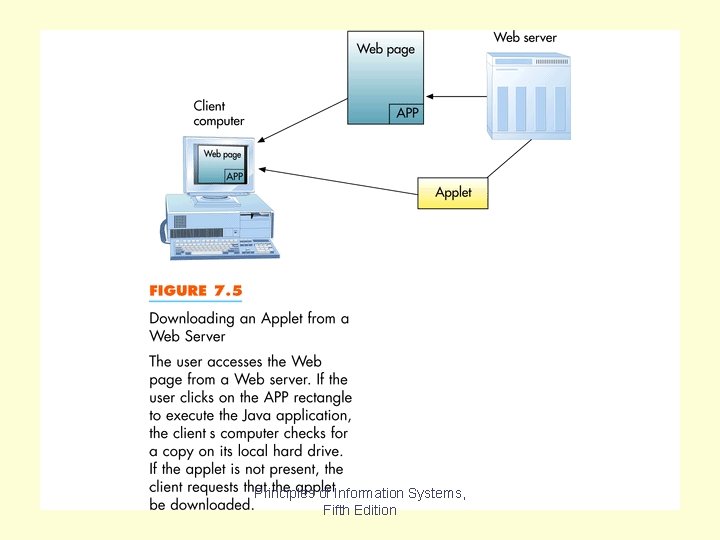
Figure 7. 5 Principles of Information Systems, Fifth Edition

Java is an object-oriented programming language that allows small programs – called applets – to be included in HTML documents. Applets are small programs that are downloaded to, and run on, the user’s computer, the client computer. Java-enabled web pages can include animation and real-time updates. Figure 7. 5 shows how an applet works. When the user accesses a web page, it is downloaded to his computer. If the web page includes HTML tags indicating a Java applet, if the tag is activated by the users clicking on an area of an HTML web page to execute the program, the client’s browser software checks to see if the applet is already stored on the client. Chapter 7 Principles of Information Systems, Fifth Edition Slide 62

If not, it is downloaded from the web server and executed on the client. Java applets can run on any hardware and operating system platform. Chapter 7 Principles of Information Systems, Fifth Edition Slide 63

Webcasting aka Push Technology Consolidates information according to a user’s profile & displays in the browser Chapter 7 Principles of Information Systems, Fifth Edition Slide 64

Although users can search for sites on the Internet, push technology can automatically provide customized content to individuals. Webcasting, or push technology, gathers information and brings it to the client computer. Chapter 7 Principles of Information Systems, Fifth Edition Slide 65

Developing Web Content Tools Word processors l HTML editor l HTML Template l Text editor l View your page Add effects judiciously Chapter 7 Principles of Information Systems, Fifth Edition Slide 66

HTML standards are evolving, with new tags being added frequently. Not all browsers, or even versions of the same browser, work the same way when viewing a web page, since each may be based on a different set of standards. You can create a web page in several ways. You can create a document using word processing software, such as Microsoft Word, and then convert the document to HTML. Most word processors have an option to save a document as a web page, making this an easy way to create web pages. Chapter 7 Principles of Information Systems, Fifth Edition Slide 67

You can use web site development software, such as Microsoft’ Front. Page or Macromedia’s Dream. Weaver, to create professional-looking websites without much more difficulty than using a word processor. You can also develop use an HTML editor, writing text and adding tags, or using an ordinary text editor to write text and type in tags. Additionally, there are many existing HTML templates that simplify HTML creation. Chapter 7 Principles of Information Systems, Fifth Edition Slide 68

After you create a webpage, always view it with a browser. In fact, it is best to view your page in different browsers and different versions of the same browser, to ensure your page can be viewed by users who aren’t using the latest version. Images, audio, animation or video can be used to enhance the page or add content. However, keep in mind that the more such effects you have, the longer it will take to open the web page. When finished, upload you web page to a web server. Typically, file transfer protocol, or FTP, is used for this. Chapter 7 Principles of Information Systems, Fifth Edition Slide 69

Many ISPs give subscribers a small amount of space on a web server. Additionally, there are free web hosting sites, such as geocities and angelfire offer limited space for a web site, although ads will appear on your web page. Chapter 7 Principles of Information Systems, Fifth Edition Slide 70

Intranets and Extranets

An intranet is an internal organizational network that uses Internet and World Wide Web standards and technologies. An intranet can be local or may connect all of a corporation’s worldwide resources. These private networks are used to provide employees or other internal users information and to handle administrative tasks. For example, in some firms employees can complete and file forms such as travel reports over the intranet. Since so many people are familiar with the Internet and World Wide Web, they need little help in using intranets effectively. Chapter 7 Principles of Information Systems, Fifth Edition Slide 72

Intranets are integrating computers, software and databases that are dispersed throughout businesses together – a feat that has eluded technologists and managers until now. An increasing number of organizations are offering limited access to their intranet to specific customers or suppliers. These networks, called extranets, connect external people to those in the company, based on the technologies of the Web. Chapter 7 Principles of Information Systems, Fifth Edition Slide 73

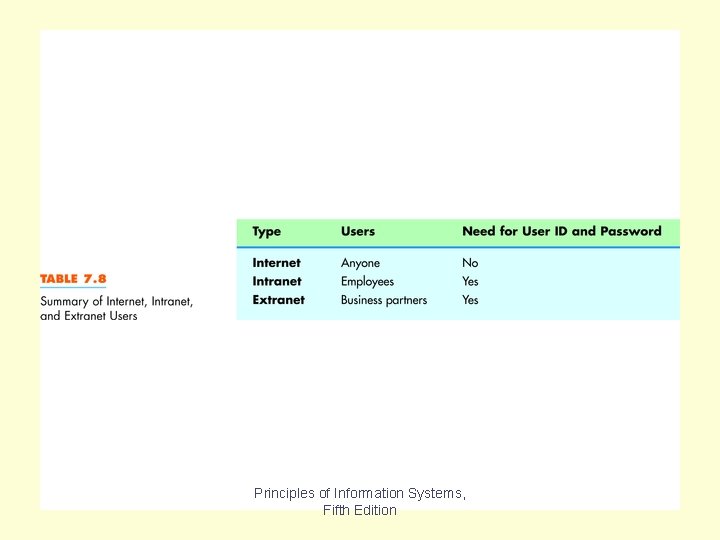
Table 7. 8 Principles of Information Systems, Fifth Edition

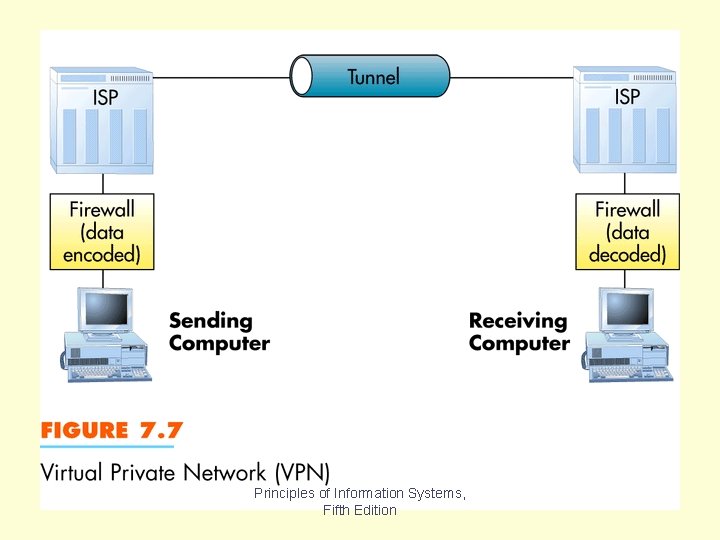
Table 7. 8 summarizes the difference between the Internet, intranets and extranets. Security and privacy concerns are even more critical for an extranet than an intranet. In order to secure an intranet or extranet, many organizations use a Virtual Private Network, which is a secure network over the Internet. Chapter 7 Principles of Information Systems, Fifth Edition Slide 75

Fig 7. 7 Principles of Information Systems, Fifth Edition

Figure 7. 7 shows how a virtual private network operates. In a virtual private network, messages are encoded when the are sent across the virtual private network and decoded upon receipt. Virtual private networks are often available from Internet service providers. Chapter 7 Principles of Information Systems, Fifth Edition Slide 77

Net Issues

All types of networks – the Internet, intranets, extranets, LANs and WANs - are all affected by control, access, hardware and security issues. Since there is no central governing body for the Internet, issues such as privacy or offensive or sensitive material being placed on the Internet are difficult to address. These issues are easier to deal with for corporate networks. Chapter 7 Principles of Information Systems, Fifth Edition Slide 79

Net Issues Service bottlenecks Firewalls Privacy & security Cookies l Cryptography l Encryption l Digital signature l Chapter 7 Principles of Information Systems, Fifth Edition Slide 80

Most service bottlenecks on the Internet and corporate intranets alike are caused by the rapid growth of usage. When setting up a web server for internal or external use, organizations often underestimate the volume and frequency with which it will be accessed. Growth in Internet traffic is also causing service problems. Internet traffic is usually carried by multiple providers – some have good service and some don’t. For instance, links to Pacific Rim countries have been slow due to the limited bandwidth. The routers connecting the many networks of the Internet also slow traffic. Chapter 7 Principles of Information Systems, Fifth Edition Slide 81

Routers must consult a destination table for each packet routed and can become overloaded. When packets are lost, they must be retransmitted, which increases the traffic on the Internet, further straining the routers. Backbone providers and equipment manufacturers are trying to improve Internet service by improving the technology. Prioritization of traffic is also being considered – customers could pay more for guaranteed delivery speed. Chapter 7 Principles of Information Systems, Fifth Edition Slide 82

Firewalls are a combination of computer hardware and software that connect internal networks to the Internet and limit access to and from the organization’s network based on a defined policy. Firewalls filter incoming traffic and can be configured to limit access to certain computers, certain networks, or certain types of traffic. Inappropriate traffic is refused. Before the Internet becomes a widespread way to do business, individuals and business want to see security and privacy issues adequately addressed. Chapter 7 Principles of Information Systems, Fifth Edition Slide 83

For instance, when you visit a website, a cookie may be placed on your computer. Cookies are text files that contain information about your usage of the website. Cookies enable websites to customize the page you see, not only with content based on your interests or your pattern of using the website, but also by using your name. However, companies can also use the information cookies collect to assemble a detailed profile of you. Most browsers allow you to reject cookies; however, some websites don’t work correctly if you do. Chapter 7 Principles of Information Systems, Fifth Edition Slide 84

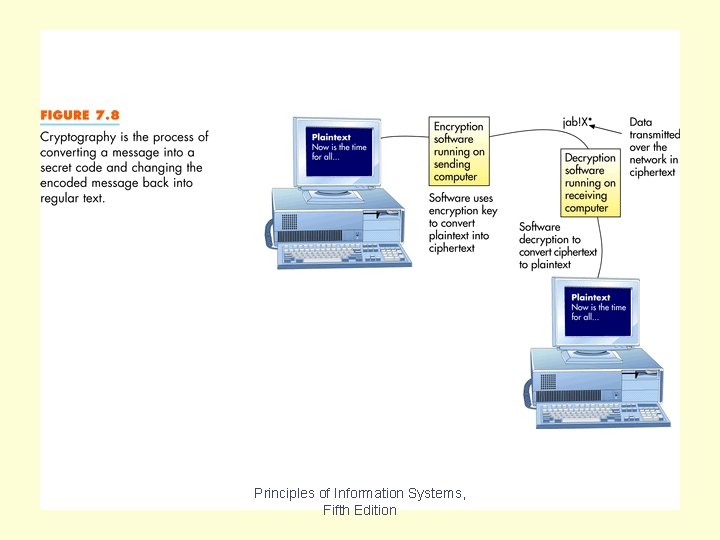
Cryptography involves encoding, or encrypting, a message so that it can’t be read without the correct key, and then decoding it with the key. The unencoded message is called plaintext, and the encoded message is called ciphertext. Good ciphertext appears to be a random string of characters, so it is useless to anyone intercepting it. Corporations are increasingly using cryptography to ensure data security. Cryptography requires specialized software. A digital signature is a special encoding technique used to verify the sender’s identity. Chapter 7 Principles of Information Systems, Fifth Edition Slide 85

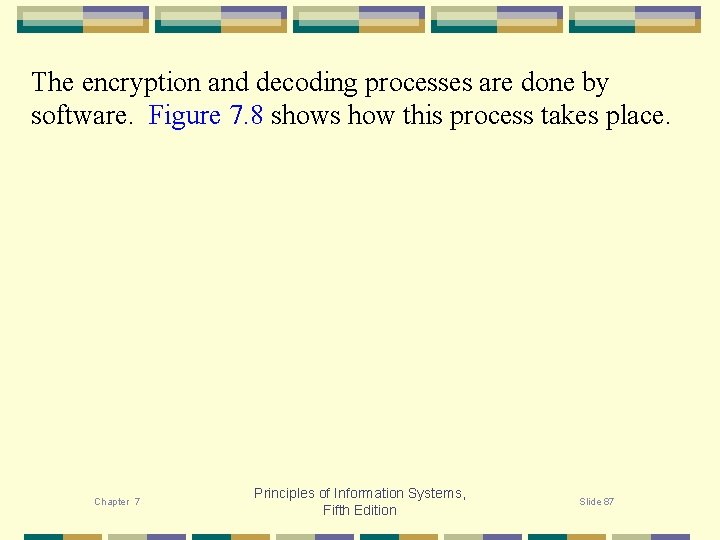
Fig 7. 8 Principles of Information Systems, Fifth Edition

The encryption and decoding processes are done by software. Figure 7. 8 shows how this process takes place. Chapter 7 Principles of Information Systems, Fifth Edition Slide 87