The Internet and Java Sockets ICW Lecture 5
















- Slides: 36

The Internet and Java Sockets ICW Lecture 5 Tom Chothia

Reminder of Last Time: • Encryption can be public key or symmetric. • Use a Cipher Object in Java to encrypt and decrypt. • Keep your keys in a Key. Store

This Time: • How the Internet works. – Some History – TCP/IP – DNS • How to make socket connections between computers using Java. • How to send Strings and Objects.

Before the Internet • Life was solitary, poor, nasty, brutish and short. • Computer Networks: – local networks, – telephone line connections, – leased line.

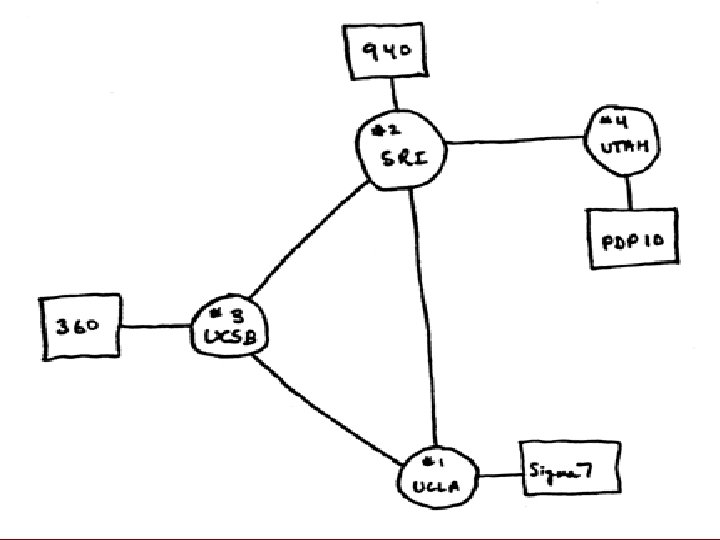
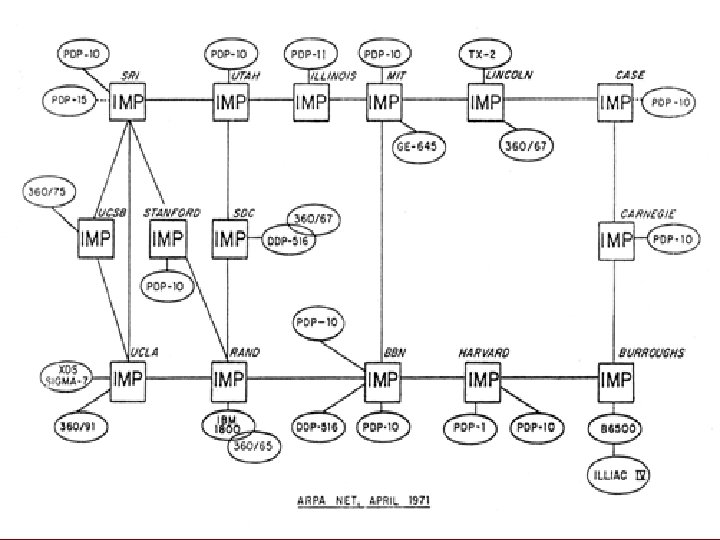
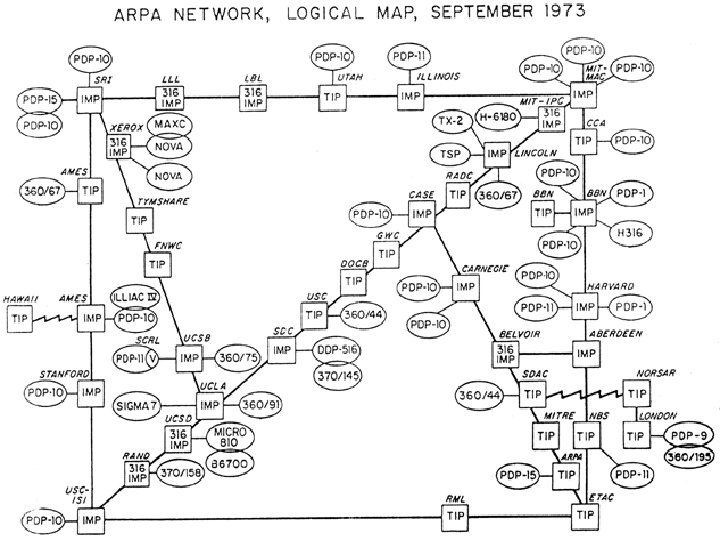
The Start 1969 • The US Defense Advanced Research Projects Agency (then ARPA now DARPA) gives research grants to universities to buy computers. • The decide to link their computers. • But how?

The Problem With Leased Lines A C B D

The Problem With Leased Lines A C B D

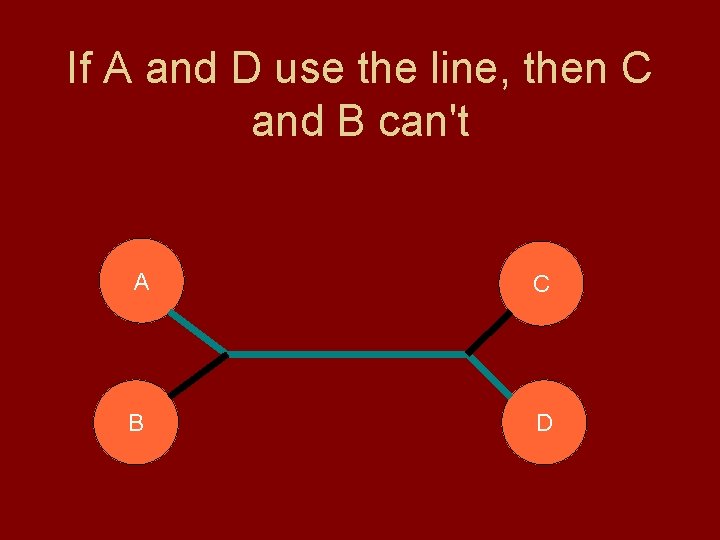
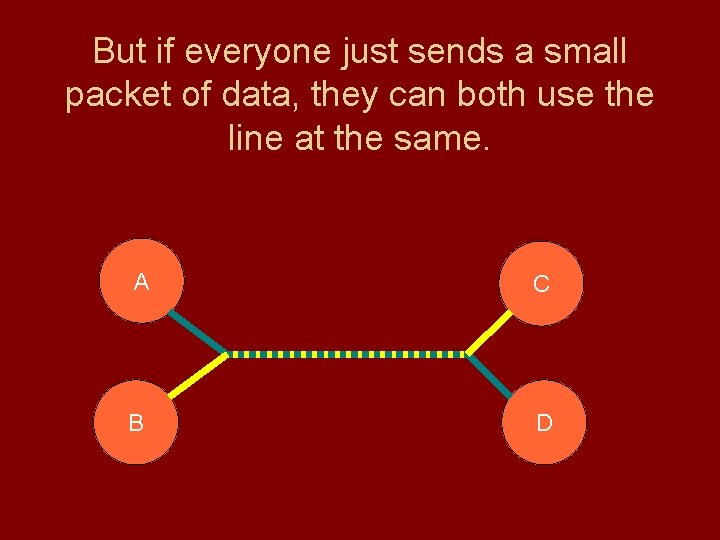
If A and D use the line, then C and B can't A C B D

But if everyone just sends a small packet of data, they can both use the line at the same. A C B D


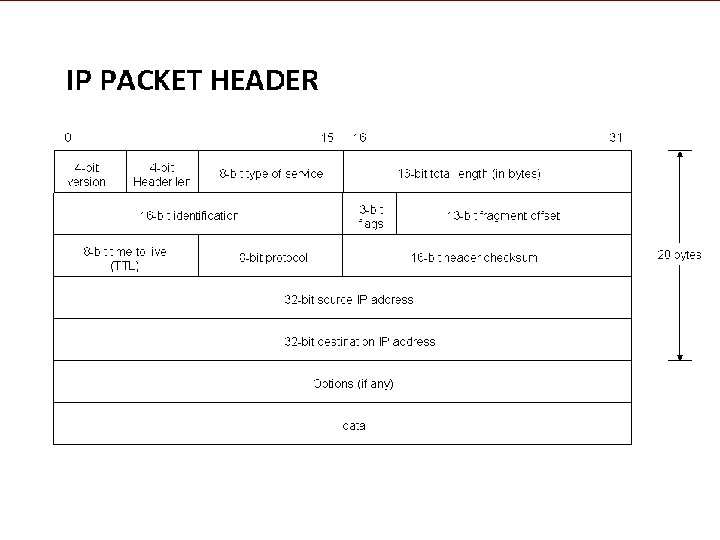
The Internet Protocol Packet

IP Addresses • Every computer has an IP address. e. g. 147. 188. 193. 15 • Every router on the Internet keeps a list of which connection it should use for which addresses.



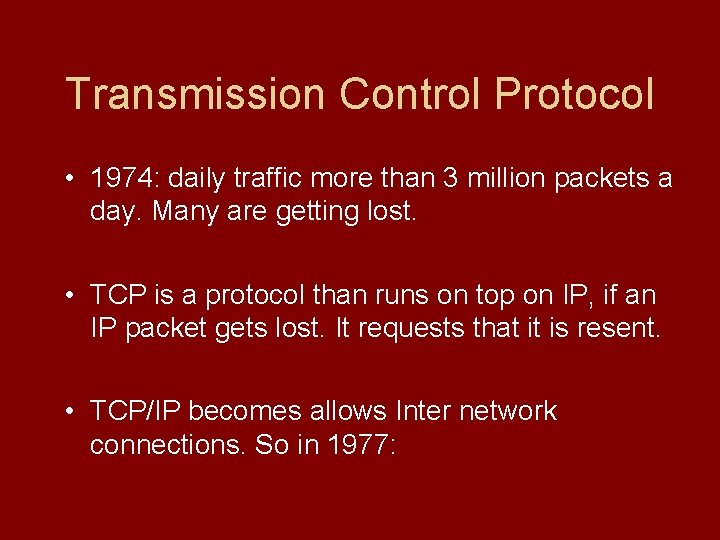
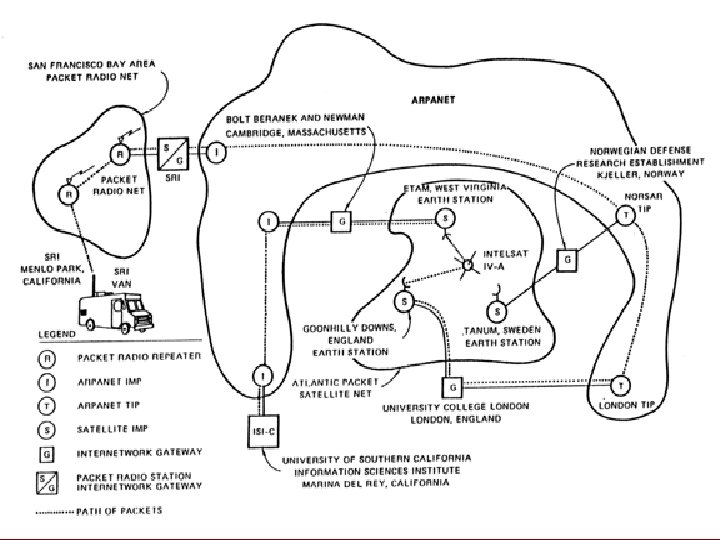
Transmission Control Protocol • 1974: daily traffic more than 3 million packets a day. Many are getting lost. • TCP is a protocol than runs on top on IP, if an IP packet gets lost. It requests that it is resent. • TCP/IP becomes allows Inter network connections. So in 1977:


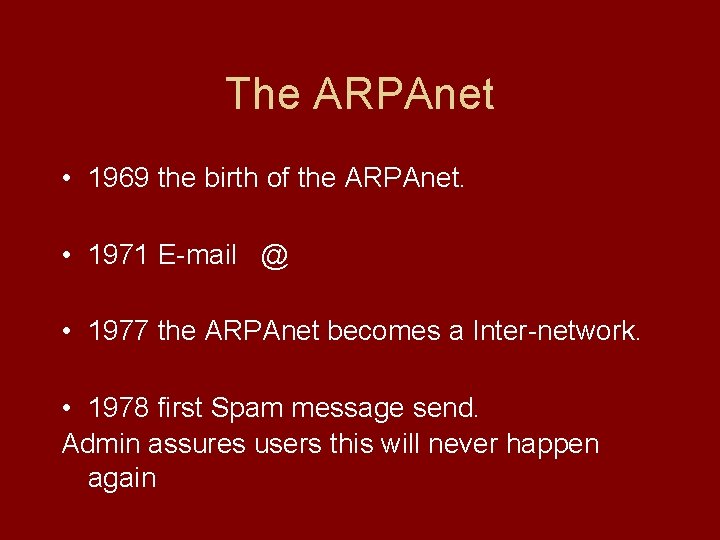
The ARPAnet • 1969 the birth of the ARPAnet. • 1971 E-mail @ • 1977 the ARPAnet becomes a Inter-network. • 1978 first Spam message send. Admin assures users this will never happen again

The Internet • 1982 : -) • 1983 TCP/IP becomes standard. • By 1990 most of Europe, India and South Africa have joined.


Domain Name Servers (DNS) • Remembering IP address is to hard. • So people associate names with addresses. e. g. news. bbc. com → 212. 58. 226. 141 • A hierarchy of servers list handle requests • The route for most of Europe is RIPE based in Amsterdam.

The Internet • 1988 The Morris Worm, CERT formed. • 1989 The Web: HTTP and HTML. • 1992 The first ISPs and Mosaic the first web browser. • 1994 Yahoo




Today • All computers on the Internet have an IP address. • Key Internet Protocols: TCP/IP • DNS to turn names into numbers.

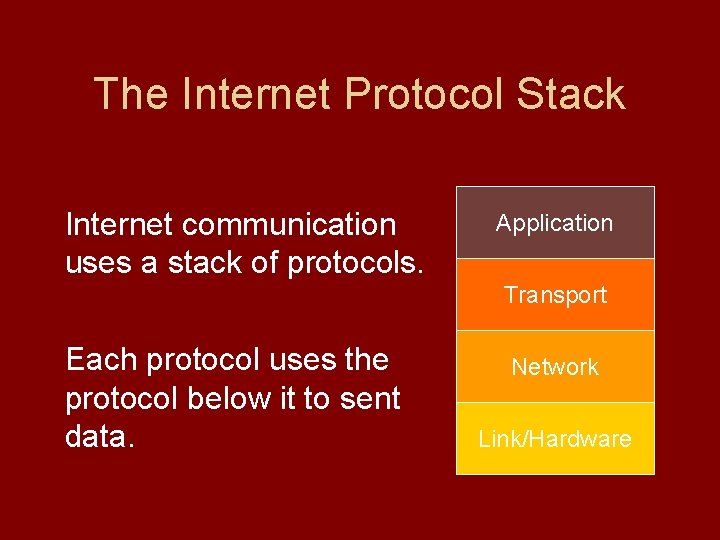
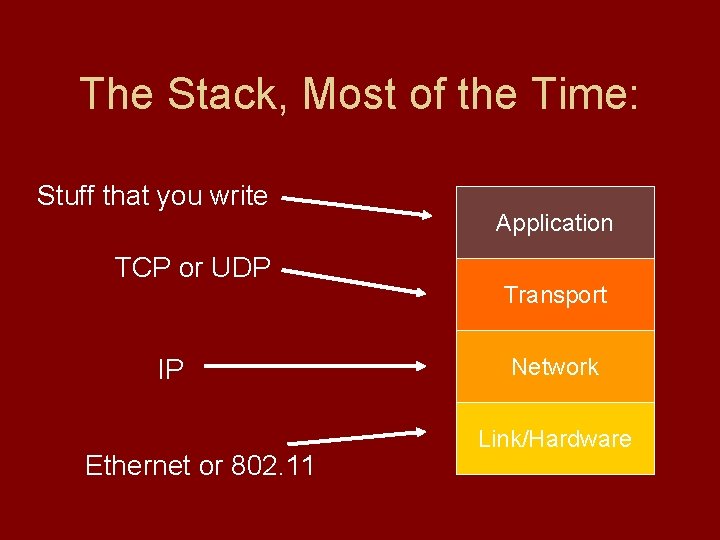
The Internet Protocol Stack Internet communication uses a stack of protocols. Application Transport Each protocol uses the protocol below it to sent data. Network Link/Hardware

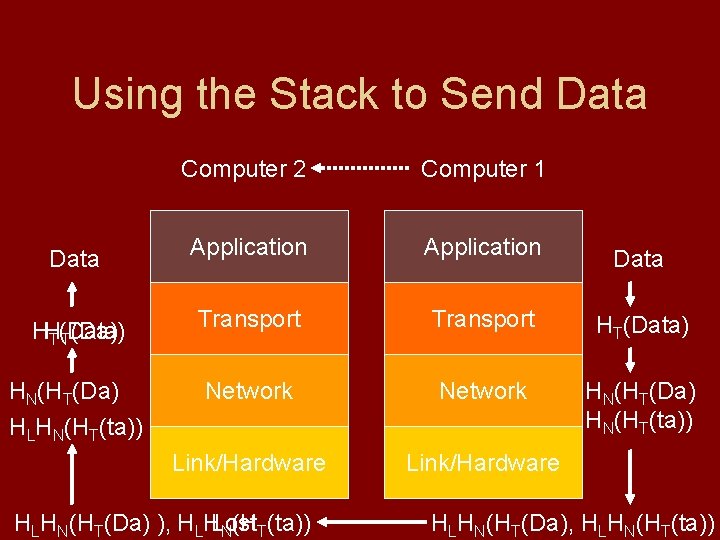
Using the Stack to Send Data HHT(Data) T(Da) HN(HT(Da) HLHN(HT(ta)) Computer 2 Computer 1 Application Transport HT(Data) Network HN(HT(Da) HN(HT(ta)) Link/Hardware HLHN(HT(Da) ), HLHLost N(HT(ta)) Data HLHN(HT(Da), HLHN(HT(ta))

The Stack, Most of the Time: Stuff that you write TCP or UDP IP Ethernet or 802. 11 Application Transport Network Link/Hardware

Sockets • • • A computer is Identified by an IP address. To allow multiple connections each computer has a port number. WWW runs on port 80, ssh on port 22, dns on 53, (free wifi). A simple connection between two computers is called a socket. Sockets are uniquely identified by (IP sender, port sender, IP receiver, port receiver).

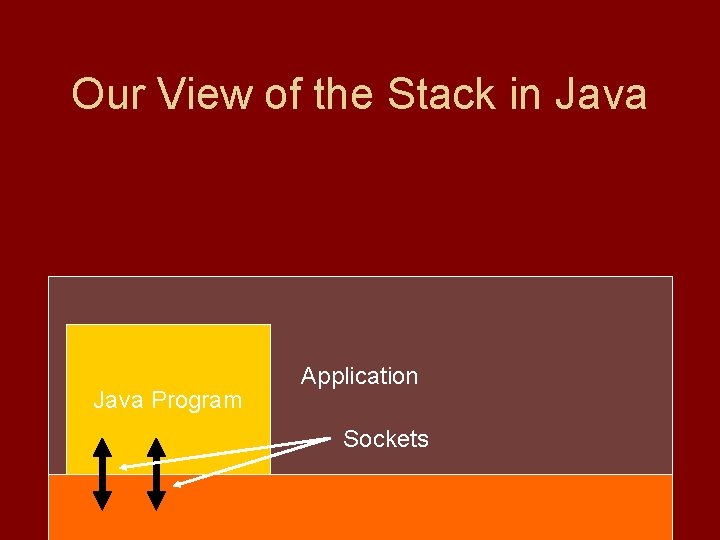
Our View of the Stack in Java Program Application Sockets

Sockets in Java • Use java. io. Socket to make a socket that connects to a remote computer. • Use java. io. Server. Socket to make a socket that listens for an incoming connection. • Sockets just give bytes, so then need a wrapper.

Code Demo • Simple socket connections

Multi-Threaded Servers • To receive multiple connections you can use threads. • See demo. • More on Threads in Lecture 11.

Sending an Object • Java lets you send an object over a socket. • The Object must be Serializable and have a UID (see demo). • Use the Object. Stream wrapper to send Objects.

Conclusion • • The Internet uses a packet based routing system IP. Sockets are an easy way to connect between machines. Use the Socket and Server. Socket Class. Use a wrapper for the socket for different data types.

Next Time: All the data send was total insecure. Next lecture I will show you how to make encrypted sockets, how to know who your talking to. i. e. what exactly does the little padlock main in my web browser?