The INFOSEC Research Council Carl Piechowski Chair IRC

















- Slides: 21

The INFOSEC Research Council Carl Piechowski Chair IRC, DOE Dr. Douglas Maughan IRC Program Manager, DARPA John C. Davis Executive Agent IRC, Mitretek

2 The INFOSEC Research Council (IRC) l Charter Ø Informally chartered, government sponsored, voluntary organization l Goals Ø Facilitate communication and collaboration between participating organizations Ø Enable knowledgeable and intelligent information security research investments Ø Increase efficiency and effectiveness of U. S. Government INFOSEC research Ø Support consolidated identification of high value research targets l The IRC provides an opportunity for participants to: Ø Ø Discuss critical information security issues Convey members’ research needs Describe current research activities and planned research investments Informally examine concepts and approaches against a body of experience and knowledge l Benefit to members Ø Helps them to focus their INFOSEC research investments through coordination with other relevant individuals and organizations

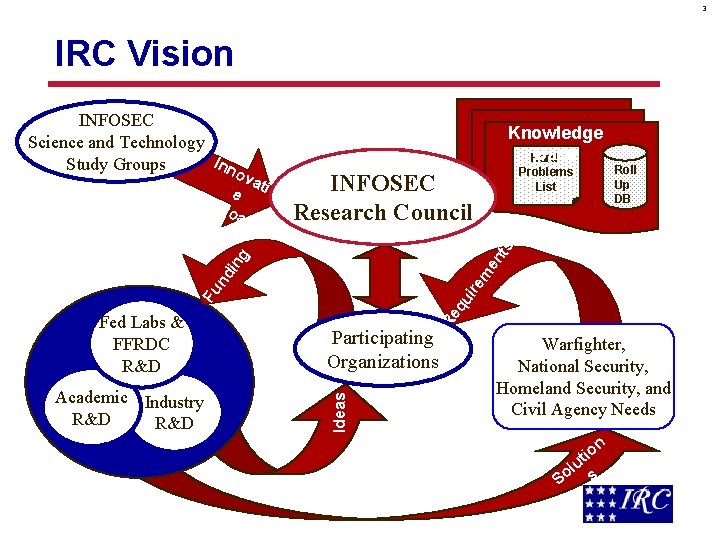
3 IRC Vision pp en ui Re q Participating Organizations Ideas Academic Industry R&D Roll Up DB re m in Fu nd Fed Labs & FFRDC R&D Problems List INFOSEC Research Council g roa es ch Knowledge Base Hard ts INFOSEC Science and Technology Inn Study Groups ov a e tiv A Warfighter, National Security, Homeland Security, and Civil Agency Needs tio u l So s n

4 IRC Background l First organized by NSA R 2 in May 1996 l IRC activities are sponsored by most of the participating organizations, as led and coordinated by DARPA l U. S. Department of Energy provides the current chairperson

5 IRC Participants l Representatives from U. S. Government organizations that sponsor information security research l Current Members Ø DOD: BMDO, DTRA, NCS, DARPA, NSA, OSD Ø Air Force: AFRL, AFIWC Ø Army: ARL, CECOM Ø Navy: NRL, ONR, SPAWAR Ø Intelligence Community: CIA, NRO, ARDA Ø Civilian Agencies: DOE, NIST, NSF, FBI, FAA, DOJ, NRC

6 IRC Activities l Bimonthly meetings Ø Ø l l Program discussions Relevant technical presentations Review new developments Events Developed the INFOSEC “Hard Problems List” Developing an R&D Database Developed R&D Summary Report Created and maintain IRC websites Ø www. infosec-research. org l Initiate INFOSEC Science and Technology Study Groups (ISTSG)

7 INFOSEC Science and Technology Study Groups l Studies Ø Issues of particular import Ø Issues of shared interest Ø Benefit from the contributions of recognized experts l Studies Completed Ø Information Assurance Vision / End State Ø Malicious Code l Studies Proposed Ø Self Healing Networks Ø Technology Transfer Ø Network Study

8 Recent Briefings l Institute for Information Infrastructure Protection (I 3 P) – Michael Vatis, Dartmouth University l National Strategy to Secure Cyberspace – Marcus Sachs, Director for Communication Infrastructure Protection l NIAP Certification of Linux and Security-Enhanced Linux – Tony Stanco, George Washington University l Homeland Security: In Pursuit of the Asymmetric Advantage – Ruth David, Analytic Services, Inc. (ANSER) l The State of Information Security within the Civil Agencies – Keith A. Rhodes, GAO

9 Recent Briefings l Large Network Security – Dr. Ed Amoroso, AT&T l Know Your Enemy: Modeling and Predicting Hacker Behavior– the Honeynet Project l Fortune 500 Corporate Security – Head of Security of F 500 company l "DUSD (S&T)'s Software Protection Initiative" – Jeff Hughes l MAC OS Security -- Shawn Geddis, Apple Federal l Microsoft XP Security – Sean Finnegan, Microsoft

10 INFOSEC Research Hard Problems List l Why define the “hard problems? ” Ø Identify important roadblocks to effective information security Ø Guide research program planning Ø Achieve consensus on identifying especially difficult/persistent information security issues l How was it done? Ø Discussion and e-mail exchanges among members Ø Contributions from national experts

11 What makes INFOSEC problems hard? Ø Technical factors o o o Need for COTS solutions Need for wide deployment of security technology Need to manage complex, networked systems securely Need to support dynamic security policy environments Growing technical sophistication of threats Ø IT Market and user perception factors o COTS provides more function, less assurance o Declining government influence on COTS information technology o User belief COTS security will suffice – Unrealistic assumptions (e. g. detect new attack)

12 IRC’s Hard Problem List Design & Development Operational l Secure system composition l High assurance development l Metrics for security l Intrusion and misuse detection l Intrusion and misuse response l Security of foreign and mobile code l Controlled sharing of sensitive information l Application security l Denial of service l Communications security l Security management infrastructure l Infosec for mobile warfare

13 Program R&D Database l Originally in hardcopy: l Now being automated Ø Each member organization provides R&D summary info Ø Project records will target: o o Summary technical info / URL Contact information Non-sensitive budget info Relationship to Hard Problems list l Benefits: identify resources being applied to hard problems, support gap analysis

14 R&D Study l Collected information about Federal INFOSEC R&D Programs l Identified key INFOSEC issues facing the U. S. Ø Fundamental flaws in much of the nation’s deployed information infrastructure that leave systems open to exploitation Ø Decreasing diversity in the software components of that infrastructure, and diminishing ability to assure that hardware communications paths are diverse, which causes any flaw to be very wide-spread Ø Lack of effective means for detecting the exploitation of these flaws, both tactically and strategically Ø Lack of controllable, graduated responses to such exploitations l Synthesized the data l Performed Gap Analysis

15 IRC Websites -- Overview l Provide the infrastructure for communicating research priorities and sharing research results l Mitretek Systems maintains three IRC websites for various audiences Ø Public - http: //www. infosec-research. org Ø IRC Meeting Participants Ø IRC Members l Implemented using open source software l Websites are hosted at Mitretek Systems in Falls Church, VA

16 IRC Public Website l Only publicly accessible IRC website l Provides an overview of the organization and objectives l Website contents Ø Ø IRC Charter Member Organizations Upcoming Meeting Date and Location Public Documents o Hard Problems List o IRC Overview (Power. Point and Word Document) Ø Contact Information

17 IRC Meeting Participants Website l Access controlled by username/password l Separate username/password issued for each meeting to all participants l SSL used for encrypted communication l Website contents Ø Schedule of future meetings Ø Meeting agendas Ø Abbreviated minutes -- contents from Closed Sessions are removed Ø Presentations from Open Sessions

18 IRC Members Website l l Access limited to Federal employees and IPAs PKI client certificates are used for website authentication SSL used for encrypted communication Website contents Ø Ø Ø Ø Schedule of future meetings Meeting agendas Complete minutes Presentations from all sessions ISTSG results / Draft documents for review Calendar of upcoming meetings and conferences Infrastructure to support the R&D database o Search R&D summary information o Update R&D project information

19 IRC Benefits While it is understood that each participating agency will have its own research priorities, the IRC helps identify and organize high priority INFOSEC problem areas and related research opportunities. The IRC: Ø Promotes more efficient and effective use of research funds Ø Shares expertise Ø Supports corporate memory beyond organization Ø Helps identify common problems Ø Helps avoid redundant efforts

20 QUESTIONS ? ? ?

21 Thank You Chair, Infosec Research Council Carl Piechowski U. S. Department of Energy SO-13 19901 Germantown Rd Germantown, MD 20874 -1290 Phone: 301 -903 -4053 carl. piechowski@hq. doe. gov IRC Executive Agent John Davis (703) 610 -1945 Mitretek Systems, Inc MS F 220 3150 Fairview Park Drive South Falls Church, VA 22042 Fax: (703) 610 -1699 john. davis@mitretek. org
 Piechowski energy
Piechowski energy Infosec management models
Infosec management models Corrective controls examples
Corrective controls examples Java irc
Java irc Smart simple irc
Smart simple irc Irc chapter 11
Irc chapter 11 Irc 469
Irc 469 Java irc
Java irc Codal alignment
Codal alignment Geometric design of highways
Geometric design of highways Traguardi per lo sviluppo delle competenze irc
Traguardi per lo sviluppo delle competenze irc Target allocation partnership
Target allocation partnership Irc n
Irc n Irc
Irc Irc
Irc Jorge brenes dittel
Jorge brenes dittel Incremental risk definition
Incremental risk definition Dialisis
Dialisis Dese irc
Dese irc Irc
Irc Tchat chaat irc
Tchat chaat irc Research council oman
Research council oman