The GAIT Methodology A Guide to Assessing the

























- Slides: 42

The GAIT Methodology A Guide to Assessing the Scope of IT General Controls A Top-Down, Risk-Based Approach to the Scoping of Key ITGC

GAIT Topics Covered: ü ü Problems with IT SOX Compliance Overview / Advantages of GAIT The Four Principles The Methodologies – Five Phases ü Bonus discussion ü Implementation ü Examples

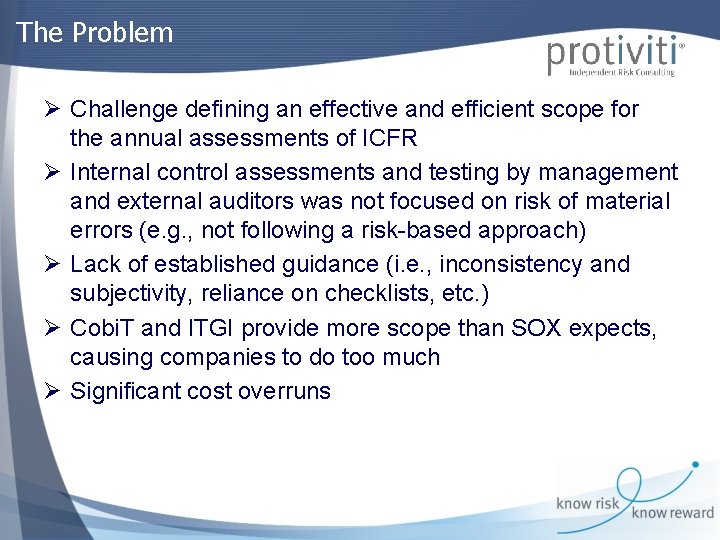
The Problem Ø Challenge defining an effective and efficient scope for the annual assessments of ICFR Ø Internal control assessments and testing by management and external auditors was not focused on risk of material errors (e. g. , not following a risk-based approach) Ø Lack of established guidance (i. e. , inconsistency and subjectivity, reliance on checklists, etc. ) Ø Cobi. T and ITGI provide more scope than SOX expects, causing companies to do too much Ø Significant cost overruns

Why was GAIT formed? Ø Difficulty defining the key IT general controls required to address risks of material errors to financial reports Ø Based on these problems, the IIA noticed the need to help companies identify key IT general controls where a failure indirectly result in a material error to the financial statements 4

Who helped with GAIT? Core team of 7 people wrote and edited the documents • • Christine Bellino, Jefferson Wells Ed Hill, Protiviti Fawn Weaver, Intel Gene Kim, Tripwire Heriot Prentice, The IIA Norman Marks, Business Objects Steve Mar, Microsoft – Team Leader Advisory Board • CPA Firms – Big Four, Mid-sized Firms • SEC Registrants • Regulators 5

Who is a part of GAIT? The Institute of Internal Auditors • IIA Support Staff • Advanced Technology Committee Others • American Institute of Certified Public Accountants (AICPA) • International Federation of Accountants (IFAC)

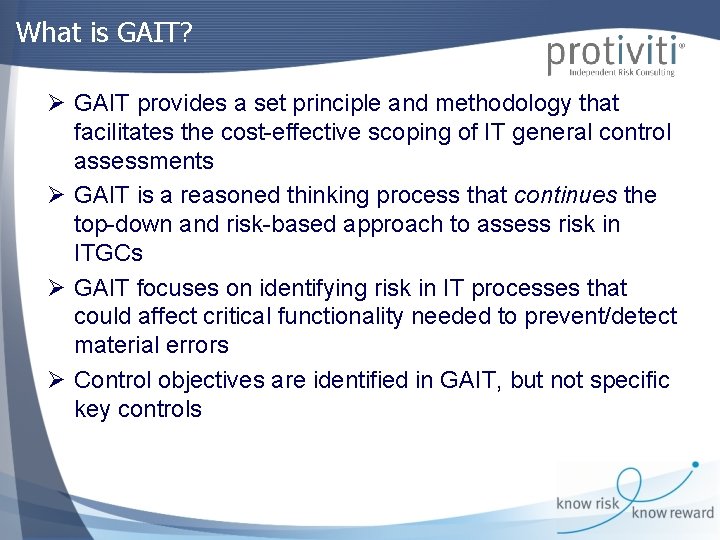
What is GAIT? Ø GAIT provides a set principle and methodology that facilitates the cost-effective scoping of IT general control assessments Ø GAIT is a reasoned thinking process that continues the top-down and risk-based approach to assess risk in ITGCs Ø GAIT focuses on identifying risk in IT processes that could affect critical functionality needed to prevent/detect material errors Ø Control objectives are identified in GAIT, but not specific key controls

How does GAIT work? Ø The GAIT document has two main parts: Ø Four Core Principles Define the relationship between business risk, IT general controls risk, and the IT general controls that can mitigate these threats as they pertain to financial reporting objectives Ø Five Phase Methodology Helps organizations to examine each financially significant application and determine whether failures in the IT general control processes at each layer of the IT infrastructure represent a likely threat to the consistent operation of the application's critical functionality – HOW TO APPLY THE PRINCIPLES

Advantages of Applying GAIT Ø Two Primary Advantages Ø Improves cost effectiveness of IT General Controls auditing by including within audit scope only the elements or layers of infrastructure and IT general control processes that are relevant to financial control risks. Ø Aids in the documentation of scoping decisions.

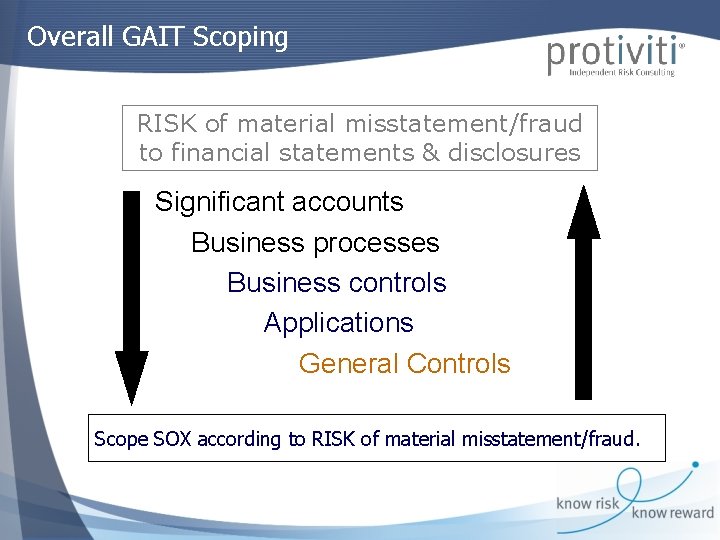
Overall GAIT Scoping RISK of material misstatement/fraud to financial statements & disclosures Significant accounts Business processes Business controls Applications General Controls Scope SOX according to RISK of material misstatement/fraud.

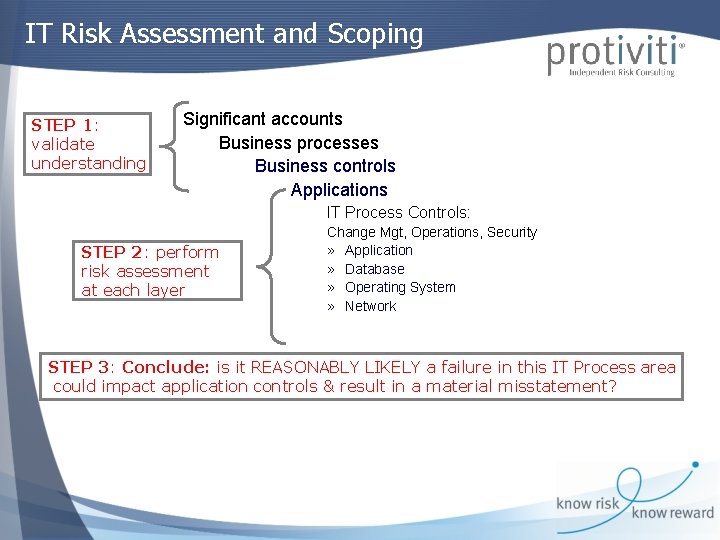
IT Risk Assessment and Scoping STEP 1: validate understanding Significant accounts Business processes Business controls Applications IT Process Controls: STEP 2: perform risk assessment at each layer Change Mgt, Operations, Security » Application » Database » Operating System » Network STEP 3: Conclude: is it REASONABLY LIKELY a failure in this IT Process area could impact application controls & result in a material misstatement?

Reasonableness Risk is not eliminated; is it reduced to a REASONABLE level.

Risk of not using GAIT Ignoring a top-down and risk based approach starting at the financial statements and significant account level, increases the likelihood that: Ø Ø Controls may be assessed and tested that are not critical, resulting in unnecessary cost and diversion of resources Controls that are key may not be tested, or may be tested late in the process, presenting a risk to the assessment or audit

GAIT’s Four Principles • The identification of risks and related controls in IT business processes should be a continuation of the topdown and risk-based approach used to identify significant accounts, risks to those accounts, and key controls in the business processes. • The IT general control process risks that need to be identified are those that affect critical IT functionality in financially significant applications and related data.

GAIT’s Four Principles • The IT general control process risks that need to be identified exist in processes and at various IT layers: application program code, databases, operating systems, and network. 4. Risks in IT general control processes are mitigated by the achievement of IT control objectives, not individual controls.

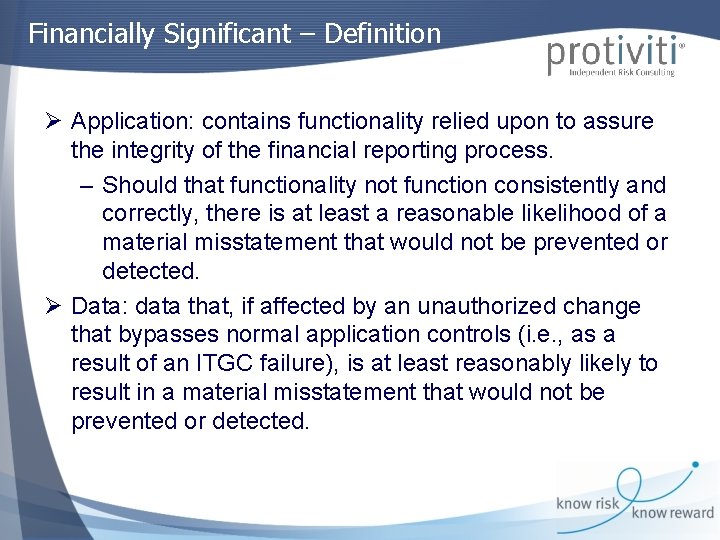
Financially Significant – Definition Ø Application: contains functionality relied upon to assure the integrity of the financial reporting process. – Should that functionality not function consistently and correctly, there is at least a reasonable likelihood of a material misstatement that would not be prevented or detected. Ø Data: data that, if affected by an unauthorized change that bypasses normal application controls (i. e. , as a result of an ITGC failure), is at least reasonably likely to result in a material misstatement that would not be prevented or detected.

The GAIT Methodology. . . guides you by asking three questions: • • • What IT functionality in the financially significant applications is critical to the properation of the business process key controls that prevent/detect material misstatement? For each IT process at each layer in the stack, is there a reasonable likelihood that a process failure would cause the critical functionality to fail — indirectly representing a risk of material misstatement? If such IT business process risks exist, what are the relevant IT control objectives?

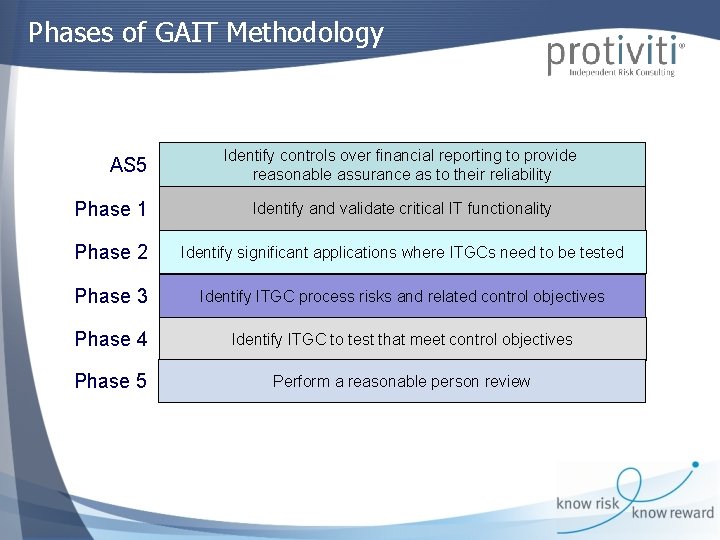
Phases of GAIT Methodology AS 5 Identify controls over financial reporting to provide reasonable assurance as to their reliability Phase 1 Identify and validate critical IT functionality Phase 2 Identify significant applications where ITGCs need to be tested Phase 3 Identify ITGC process risks and related control objectives Phase 4 Identify ITGC to test that meet control objectives Phase 5 Perform a reasonable person review

AS 5 Top Down Approach Ø Effective internal control over financial reporting provides reasonable assurance regarding the reliability of financial reporting and the preparation of financial statements. Ø The auditor should use a top-down approach to the audit of internal control over financial reporting to select the controls to test. A top-down approach begins at the financial statement level and with the auditor's understanding of the overall risks to internal control over financial reporting.

AS 5 (cont’d) Role of IT Ø The auditor should assess the extent of information technology ("IT") involvement in the period-end financial reporting process; Ø The identification of risks and controls within IT should not be a separate evaluation but, rather, an integral part of the auditor's top down risk assessment, including identification of significant accounts and disclosures and their relevant assertions, as well as the controls to test.

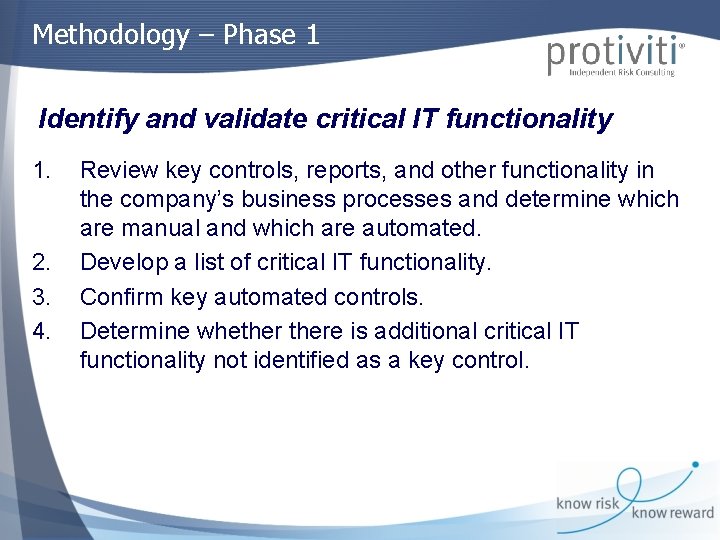
Methodology – Phase 1 Identify and validate critical IT functionality 1. 2. 3. 4. Review key controls, reports, and other functionality in the company’s business processes and determine which are manual and which are automated. Develop a list of critical IT functionality. Confirm key automated controls. Determine whethere is additional critical IT functionality not identified as a key control.

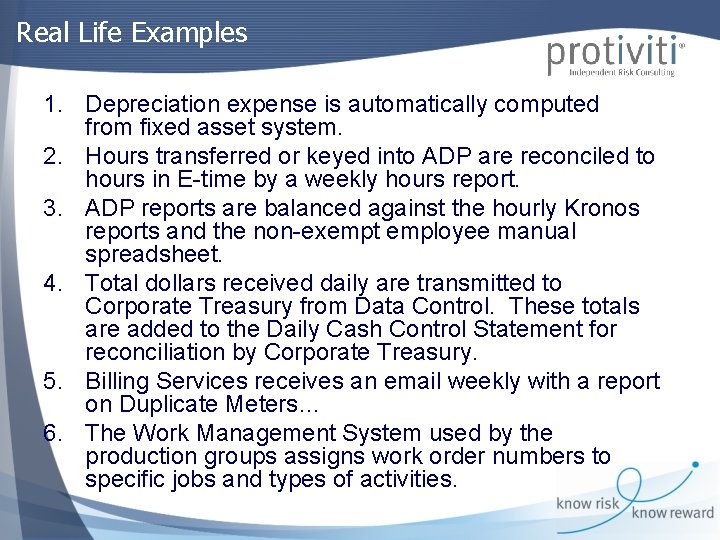
Real Life Examples 1. Depreciation expense is automatically computed from fixed asset system. 2. Hours transferred or keyed into ADP are reconciled to hours in E-time by a weekly hours report. 3. ADP reports are balanced against the hourly Kronos reports and the non-exempt employee manual spreadsheet. 4. Total dollars received daily are transmitted to Corporate Treasury from Data Control. These totals are added to the Daily Cash Control Statement for reconciliation by Corporate Treasury. 5. Billing Services receives an email weekly with a report on Duplicate Meters… 6. The Work Management System used by the production groups assigns work order numbers to specific jobs and types of activities.

Real Life Examples (cont’d) 7. The Treasury Department records interest expense using the STX system. 8. Based on the actuary reports and payroll data, a memo is prepared and sent prior to January closing by the Lead Accountant to the Controller, Director of Accounting … 9. At the end of each month-end close, capital stock amounts are verified by Corporate Accounting with reports prepared by Investor Relations/ Treasury. 10. A pocket database is created that stores the last 15 days of read data and is maintained internally by IT. In the event of connectivity problems with Meter. Net, these reads can be utilized to complete billing activities. 11. Meter read data is auto validated by the Validator-2000 application (meter reads are compared to meter pulse data) …

Some Systems Hiding Places “Additional critical IT functionality not identified as a key control” Some places to look: q Stock options q Taxes q Hedging activities (fuel, currency, inventory) q Depreciation q Reserves (warranty, pension, etc. ) q Bonds/loans q _____________

GAIT Bonus – Key Spreadsheets Many organizations wrestle with properly identifying (scoping) and testing key spreadsheets Ø Overwhelmed by the number of spreadsheets Ø Some define key based on complexity, not necessarily significance Ø (Don’t forget Access databases, etc. ) Ø GAIT approach offers a good approach to begin: What financial controls indicate spreadsheets?

Key Spreadsheets - Examples 1. Comparison of prepaid amounts to forecast and budget is performed monthly by the Staff Accountants. 2. Each month, Accounting will run a miscellaneous query and review the adjustments charged to the Dollar Scholar general ledger account. 3. Billing Services also populates an Excel spreadsheet in the Accounting E: drive with the reissued check number and amount. 4. An accountant in the Corporate Accounting Department maintains an Excel worksheet for fixed rate long-term debt, and an Excel worksheet for interest expense related to variable rate long-term debt. 5. Equity compensation worksheets and totals are reconciled to the Long Term Incentive Plan (LTIP) file from the Corporate Secretary’s office quarterly.

Methodology – Phase 2 Identify significant applications where ITGCs need to be tested 1. 2. Sort the critical IT functionality by application. Identify the financially significant applications that are in scope for ITGC.

Methodology – Phase 2 Continue only with financially significant applications (AND the applications used by IT to administer the ITGC)

Methodology – Phase 3 Identify ITGC process risks and related control objectives Risk of IT Process Failures 1. What is the likelihood of an IT process failure occurring and what is the potential impact? 2. What is the likelihood of the IT process failing in such a way that it would cause the critical IT functionality to fail? 3. Is it at least reasonably likely that the critical functionality would fail without prompt detection and result in a material error in the financial statements?

Methodology – Phase 4 Identify ITGC to test that meet control objectives 1. Consider the pervasiveness of ITGC. . . § Are there risks that may affect multiple applications and their critical IT functionality? 2. Select Key IT general controls to test. 1. Consider the entire stack 2. Consider the nature of the stack 3. Are their common stacks 3. Link each key IT general control to the control objectives identified through GAIT.

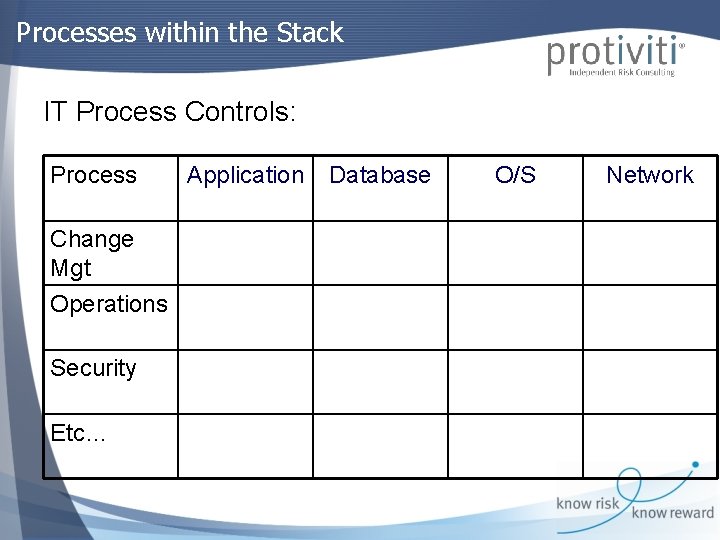
Processes within the Stack IT Process Controls: Process Change Mgt Operations Security Etc… Application Database O/S Network

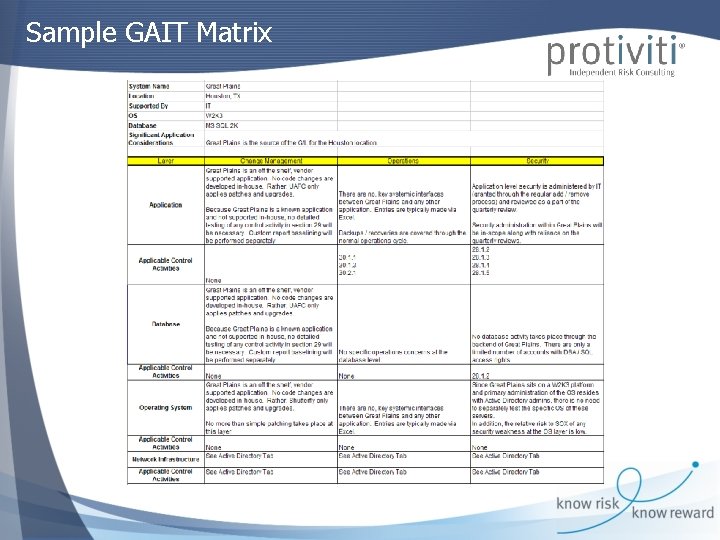
Sample GAIT Matrix

Methodology – Phase 5 Perform a reasonable person review 1. Confirm that the risks and key controls represent a reasonable view of risk to financial reporting. 2. Ensure that the selection of risks is reasonable, given the organization’s risk tolerance in their 404 scope. 33

Risk Factors that affect the risk associated with a control include: • The degree to which the control relies on the effectiveness of other controls (e. g. , the control environment or information technology general controls); • Whether the control relies on performance by an individual or is automated (i. e. , an automated control would generally be expected to be lower risk if relevant information technology general controls are effective);

Case Study 1 Energy Trading Company • • Key IT general controls reduced from 48 to 20 Able to consolidate many of the controls Added 2 applications due to reliance of financial controls Identified other risk areas related to a key application

Case Study 2 Financial Institution • Eliminated 3 systems from scope – no controls dependent upon the systems • Able to eliminate all Network related controls except for access • Some controls were added back at management’s request due to the immaturity of the processes • At another financial institution was able to eliminate a whole class of servers and corresponding infrastructure

Case Study 3 Utility Company • Reduced key IT general controls from 49 to 18 • Reduction had significant potential for reducing administrative overhead • Paved the way for self assessment program • Able to provide good rationale for in-scope applications

Implementation GAIT Ø Prior to implementing GAIT, companies should perform a top-down, risk-based assessment of their business processes and identify the key controls in those processes. Ø GAIT will utilize the information gathered from this assessment and define what functionality within the IT applications is critical and to see what IT applications provide this functionality.

Maximizing GAIT’s Implementation Tips and Techniques q Start with a top-down, risk-based assessment of each risk and key control in the business process being evaluated q Build a team of internal controls experts with both business and IT knowledge to complete or review GAIT results q Engage external auditor q Perform GAIT assessment early in the process q Focus on getting scope right, not just on reductions q Document results carefully and be sure to explain what is and is not in scope

More Information. . . Ø GAIT Resources www. theiia. org Ø Questions? Ask Dr. GAIT drgait@theiia. org

Questions?

• Feel free to contact me with questions: Bill Mc. Spadden, CISA Protiviti 913 -685 -6200 or 913 -661 -7403 Bill. mcspadden@protiviti. com