the effect of falsename bids in combinatorial auctions

the effect of false-name bids in combinatorial auctions: new fraud in internet auctions Makoto Yokoo Yuko Sakurai Shigeo Matsubara presented by: Wenjie Xiao

outline Introduction n Formalization n Effect of false-name bids in combinatorial auction n Sufficient condition for VCG to be false-nameproof n Discussion n Conclusions and future work n

introduction Internet auction in electronic commerce n Conventional auctions VS Combinatorial auctions n Excellent environment for executing combinatorial auction n New cheating type!! n

introduction False-name bids submitted by a single bidder using multiple identifiers such as multiple e-mail addresses. n False-name-proof we call a protocol is false-name-proof if truthtelling without using false-name bids is a dominant strategy for each bidder. n

introduction Collusion VS false-name bids n restricted subclass of collusion: - false-name bids - group-strategy-proof n False-name proof != group-strategy-proof (talked about later) n
Formalization Model of a combinatorial auction in which false-name bids are possible n Modified the presented model so that it can handle false-name bids n Assume a quasi-linear private value model which no allocative externality n

Formalization Set of bidders N={1, 2, . . n} n Agent 0 is an auctioneer, who is willing to sell a set of goods of A={a 1, a 2 …al} n Each bidder i has his own preferences over subset of A n Privately observes a type θi for each bidder i, θi is drawn from a set Θ n
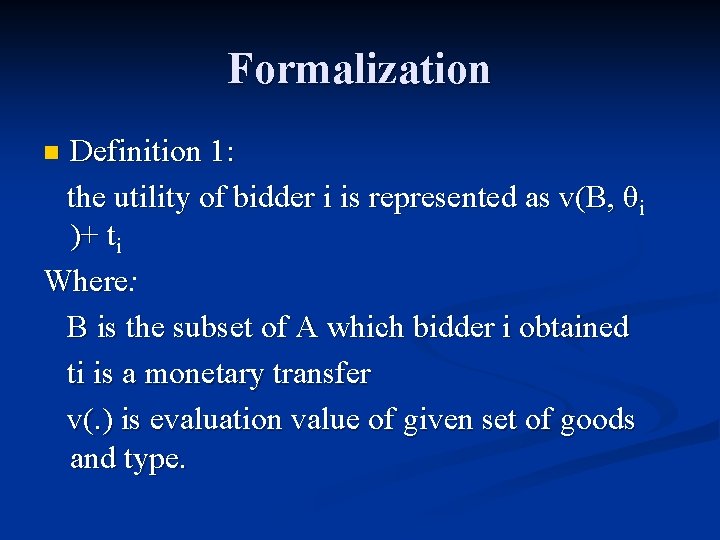
Formalization Definition 1: the utility of bidder i is represented as v(B, θi )+ ti Where: Where B is the subset of A which bidder i obtained ti is a monetary transfer v(. ) is evaluation value of given set of goods and type. n
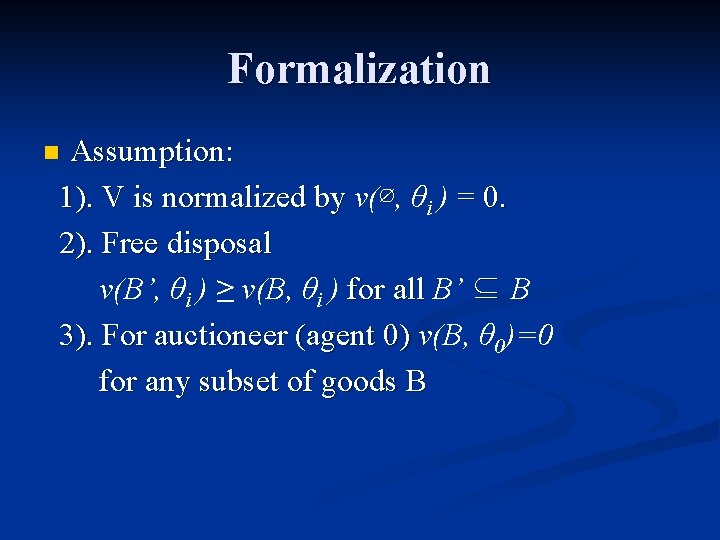
Formalization Assumption: 1). V is normalized by v(∅, θi ) = 0. 2). Free disposal v(B’, θi ) ≥ v(B, θi ) for all B’ ⊆ B 3). For auctioneer (agent 0) v(B, θ 0)=0 for any subset of goods B n
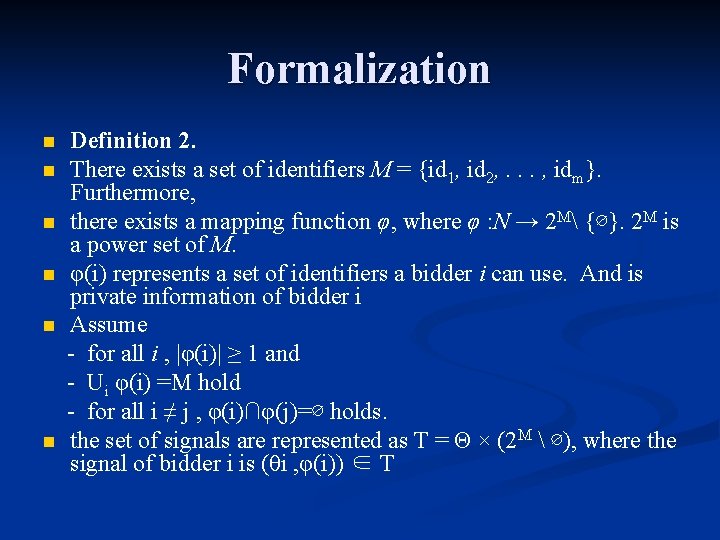
Formalization n n n Definition 2. There exists a set of identifiers M = {id 1, id 2, . . . , idm}. Furthermore, there exists a mapping function φ, where φ : N → 2 M {∅}. 2 M is a power set of M. φ(i) represents a set of identifiers a bidder i can use. And is private information of bidder i Assume - for all i , |φ(i)| ≥ 1 and - Ui φ(i) =M hold - for all i ≠ j , φ(i)∩φ(j)=∅ holds. the set of signals are represented as T = Θ × (2 M ∅), where the signal of bidder i is (θi , φ(i)) ∈ T

Formalization Define a combinatorial auction protocol n Restrict our attention to: - almost anonymous mechanisms - auction protocol, in which the set of messages for each identifier is Θ ∪ {0}, n

Formalization n n n Definition 3. A combinatorial auction protocol is defined by Γ = (k(·), t (·)). We call k(·) allocation function and t (·) transfer function. Let us represent a profile of types, each of which is declared under each identifier as θ = (θid 1, θid 2, . . . , θidm), where θidi ∈ Θ ∪ {0}. 0 is a special type declaration used when a bidder is not willing to participate in the auction: k(θ) = (k 0(θ ), kid 1(θ ), . . . , kidm(θ )), where kidi(θ ) ⊆ A, t (θ) = (t 0(θ ), tid 1(θ ), . . . , tidm(θ )), where t 0(θ ), tidi(θ ) ∈ R. R denotes the set of real numbers. Here, t 0(θ ) represents the revenue of the auctioneer and −tidi(θ ) represents the payment of idi
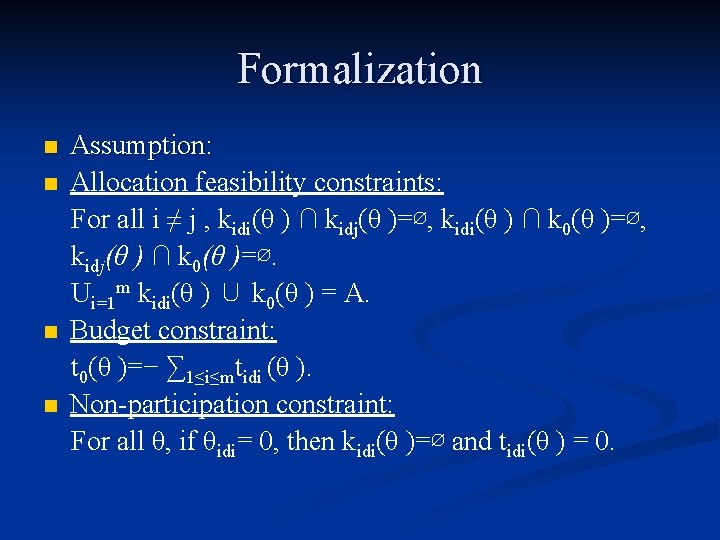
Formalization n n Assumption: Allocation feasibility constraints: For all i ≠ j , kidi(θ ) ∩ kidj(θ )=∅, kidi(θ ) ∩ k 0(θ )=∅, kidj(θ ) ∩ k 0(θ )=∅. Ui=1 m kidi(θ ) ∪ k 0(θ ) = A. Budget constraint: t 0(θ )=− ∑ 1≤i≤mtidi (θ ). Non-participation constraint: For all θ, if θidi= 0, then kidi(θ )=∅ and tidi(θ ) = 0.
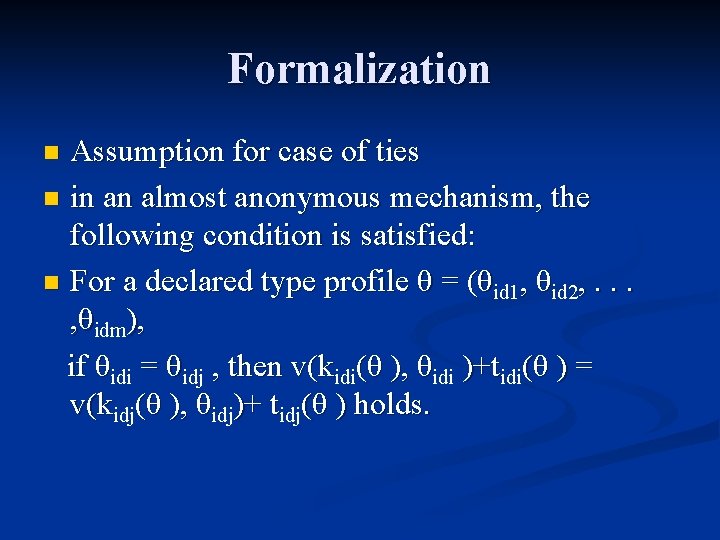
Formalization Assumption for case of ties n in an almost anonymous mechanism, the following condition is satisfied: n For a declared type profile θ = (θid 1, θid 2, . . . , θidm), if θidi = θidj , then v(kidi(θ ), θidi )+tidi(θ ) = v(kidj(θ ), θidj)+ tidj(θ ) holds. n

Formalization Definition 4. For an allocation function k(. ), if for all k = (k 0, kid 1, . . . , kidm), which satisfies the allocation feasibility constraints, and n ∑ 1≤i≤mv(kidi(θ), θidi)≥ ∑ 1≤i≤mv(kidi, θidi) holds. n then k(·) is Pareto efficient n Let us denote a Pareto efficient allocation function as k∗(·). n
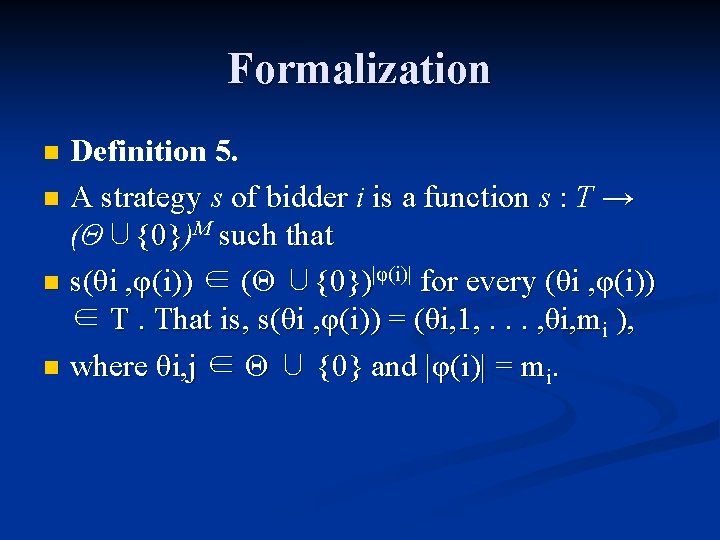
Formalization Definition 5. n A strategy s of bidder i is a function s : T → (Θ∪{0}) {0} M such that n s(θi , φ(i)) ∈ (Θ ∪{0})|φ(i)| for every (θi , φ(i)) ∈ T. That is, s(θi , φ(i)) = (θi, 1, . . . , θi, mi ), n where θi, j ∈ Θ ∪ {0} and |φ(i)| = mi. n
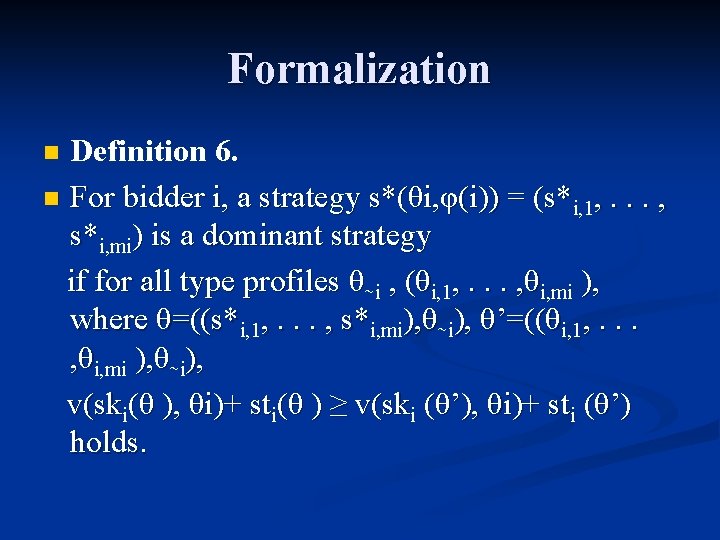
Formalization Definition 6. n For bidder i, a strategy s*(θi, φ(i)) = (s*i, 1, . . . , s*i, mi) is a dominant strategy if for all type profiles θ∼i , (θi, 1, . . . , θi, mi ), where θ=((s*i, 1, . . . , s*i, mi), θ∼i), θ’=((θi, 1, . . . , θi, mi ), θ∼i), v(ski(θ ), θi)+ sti(θ ) ≥ v(ski (θ’), θi)+ sti (θ’) holds. n

Formalization n Definition 7. We say a mechanisms is false-name-proof when for all bidder i , s*(θi , φ(i)) =(θi , 0, . . . , 0) is a dominant strategy.

Effect of false-name bids in combinatorial auctions n n n First consider the effect in VCG Definition 8. In the VCG mechanism, k∗(·) is used for determining the allocation, and the transfer function is determined as follows. tidi(θ)=[∑j≠iv(k*(θ), θidj)]-[∑j≠iv(k*-idi(θ), θidj)]. Where k*-idi(θ) is an allocation k that maximizes ∑j≠iv(kidj, θidj) i. e. in VCG, each bidder is required to pay the decreased amount of the surplus.

Effect of false-name bids in combinatorial auctions Example: n Proposition 1: (generally in combinatorial auctions) in combinatorial auctions, there exists no false-nameproof auction protocol that satisfied pareto efficiency. n Proof by counter example proof: assuming there exists a false-name-proof, pareto efficiency protocol. n
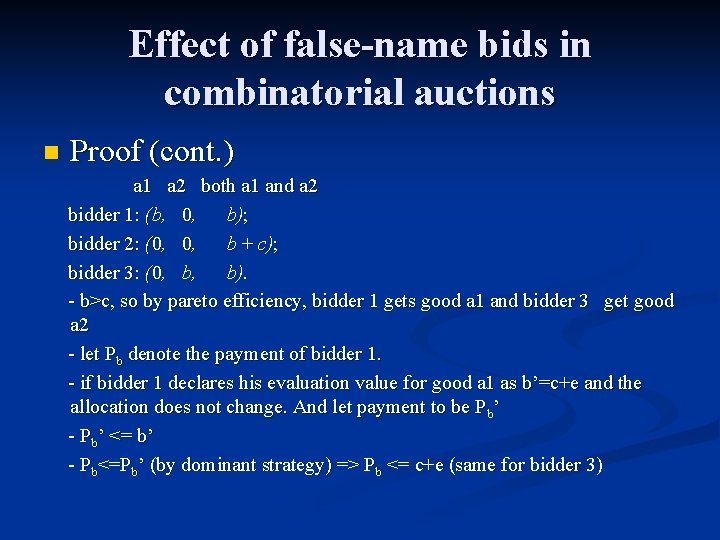
Effect of false-name bids in combinatorial auctions n Proof (cont. ) a 1 a 2 both a 1 and a 2 bidder 1: (b, 0, b); bidder 2: (0, 0, b + c); bidder 3: (0, b, b). - b>c, so by pareto efficiency, bidder 1 gets good a 1 and bidder 3 get good a 2 - let Pb denote the payment of bidder 1. - if bidder 1 declares his evaluation value for good a 1 as b’=c+e and the allocation does not change. And let payment to be Pb’ - Pb’ <= b’ - Pb<=Pb’ (by dominant strategy) => Pb <= c+e (same for bidder 3)
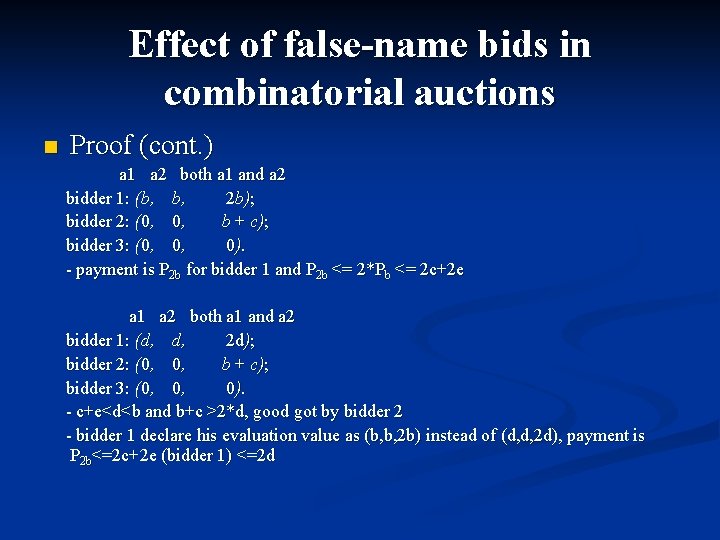
Effect of false-name bids in combinatorial auctions n Proof (cont. ) a 1 a 2 both a 1 and a 2 bidder 1: (b, b, 2 b); bidder 2: (0, 0, b + c); bidder 3: (0, 0, 0). - payment is P 2 b for bidder 1 and P 2 b <= 2*Pb <= 2 c+2 e a 1 a 2 both a 1 and a 2 bidder 1: (d, d, 2 d); bidder 2: (0, 0, b + c); bidder 3: (0, 0, 0). - c+e<d<b and b+c >2*d, good got by bidder 2 - bidder 1 declare his evaluation value as (b, b, 2 b) instead of (d, d, 2 d), payment is P 2 b<=2 c+2 e (bidder 1) <=2 d

Effect of false-name bids in combinatorial auctions Bidder 1 can increase the utility by overstating his true evaluation values n in combinatorial auctions, there exists no false-nameproof auction protocol that satisfied pareto efficiency. n Note: - proposition 1 holds in more general setting. - Relies on the model defined before, but not for free disposal. - Not rely on the fact that the mechanism is almost anonymous n
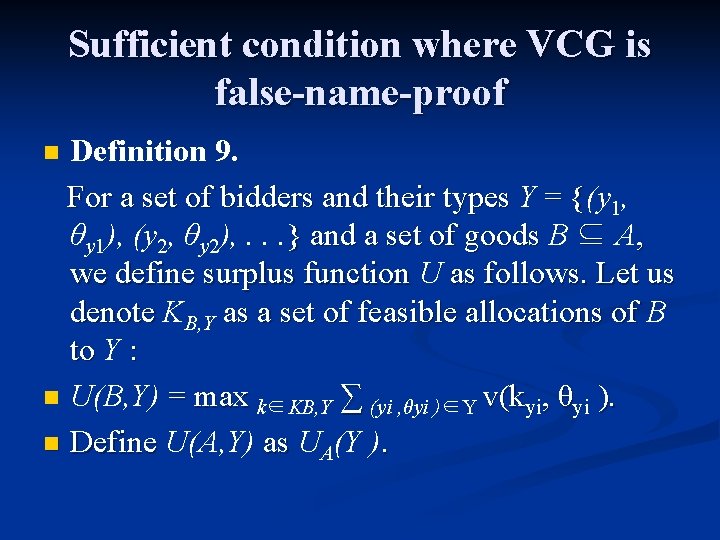
Sufficient condition where VCG is false-name-proof Definition 9. For a set of bidders and their types Y = {(y { 1, θy 1), (y 2, θy 2), . . . } and a set of goods B ⊆ A, we define surplus function U as follows. Let us denote KB, Y as a set of feasible allocations of B to Y : n U(B, Y) = max k∈KB, Y ∑ (yi , θyi )∈Y v(kyi, θyi ). n Define U(A, Y) as UA(Y ). n
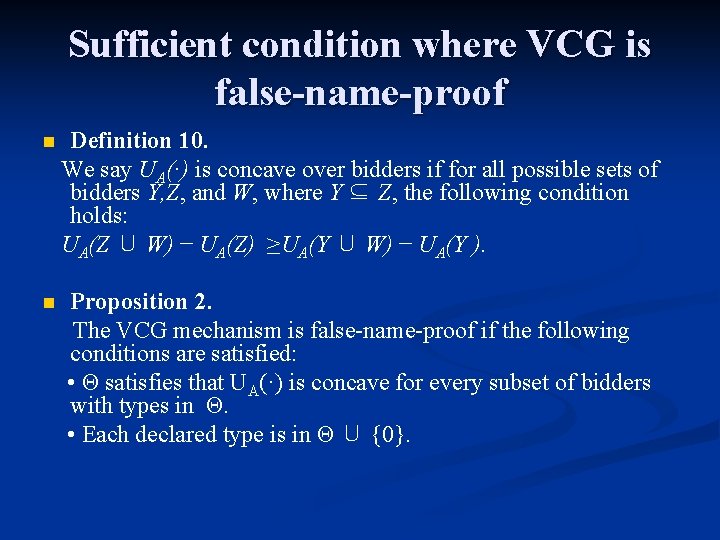
Sufficient condition where VCG is false-name-proof n Definition 10. We say UA(·) is concave over bidders if for all possible sets of bidders Y, Z, and W, where Y ⊆ Z, the following condition holds: UA(Z ∪ W) − UA(Z) ≥UA(Y ∪ W) − UA(Y ). n Proposition 2. The VCG mechanism is false-name-proof if the following conditions are satisfied: • Θ satisfies that UA(·) is concave for every subset of bidders with types in Θ. • Each declared type is in Θ ∪ {0}.
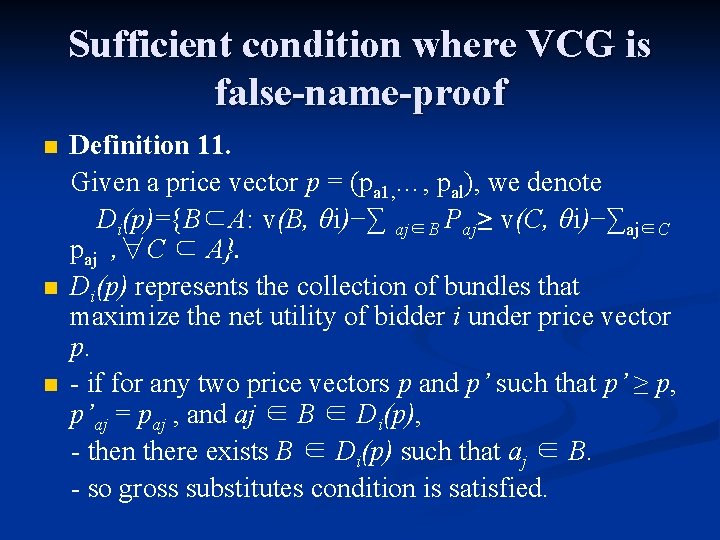
Sufficient condition where VCG is false-name-proof n n n Definition 11. Given a price vector p = (pa 1, …, pal), we denote Di(p)={B⊂A: v(B, θi)−∑ aj∈B Paj≥ v(C, θi)−∑aj∈C paj , ∀C ⊂ A}. Di(p) represents the collection of bundles that maximize the net utility of bidder i under price vector p. - if for any two price vectors p and p’ such that p’ ≥ p, p’aj = paj , and aj ∈ B ∈ Di(p), - then there exists B ∈ Di(p) such that aj ∈ B. - so gross substitutes condition is satisfied.
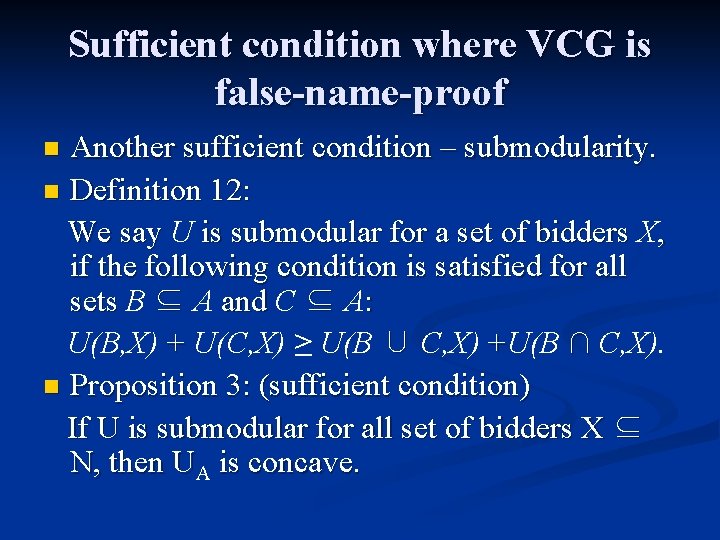
Sufficient condition where VCG is false-name-proof Another sufficient condition – submodularity. n Definition 12: We say U is submodular for a set of bidders X, if the following condition is satisfied for all sets B ⊆ A and C ⊆ A: U(B, X) + U(C, X) ≥ U(B ∪ C, X) +U(B ∩ C, X). n Proposition 3: (sufficient condition) If U is submodular for all set of bidders X ⊆ N, then UA is concave. n
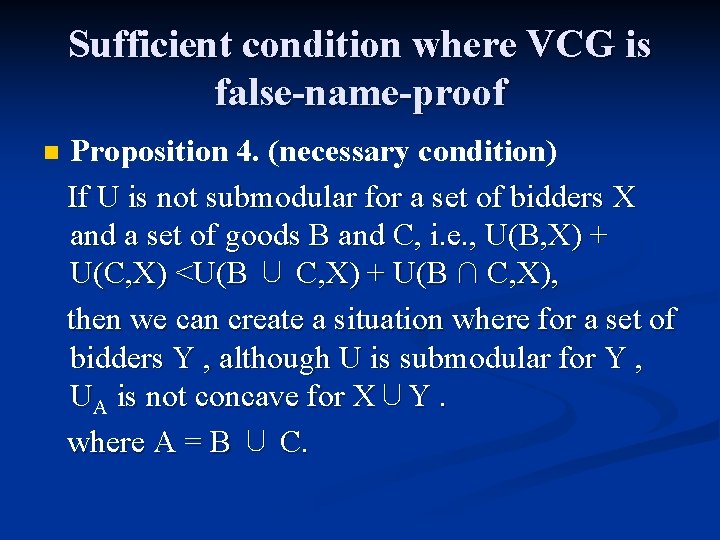
Sufficient condition where VCG is false-name-proof n Proposition 4. (necessary condition) If U is not submodular for a set of bidders X and a set of goods B and C, i. e. , U(B, X) + U(C, X) <U(B ∪ C, X) + U(B ∩ C, X), then we can create a situation where for a set of bidders Y , although U is submodular for Y , UA is not concave for X∪Y. where A = B ∪ C.

Discussion Group-strategy-proof protocols n Group-strategy-proof is not false-name proof n Also, false-name proof not necessary to be group-strategy-proof. n

Discussion n Definition: (group-strategy-proof) An auction protocol is group-strategy proof if there exists no group of bidders that satisfies the following condition. • if telling the false information - Uf(i)≥ Ut(i) for all i in N - at least one i in N s. t Uf(i) > Ut(i)

Discussion n n n if a protocol is false-name-proof, but it is not necessary to be a group-strategy-proof. Example: 2 bidders and 2 goods, Θ = {θ 1, θ 2, θ 3, θ 4}, • θ 1: (10, 9, 18); • θ 2: (9, 10, 18); • θ 3: (10, 0, 10); • θ 4: (0, 10). v({a 1}, θi) + v({a 2}, θi) ≥ v({a 1, a 2}, θi)

Discussion A protocol is group-strategy-proof, but not false-name-proof n Protocol: The auctioneer sets a reservation price p. The winner is chosen randomly from the bidders whose declared evaluation value is larger than p. The winner pays p. n

conclusion False-name bids & False-name proof n Defined model n Connected to VCG n There exists no false-name-proof combinatorial auction protocol that satisfies pareto efficiency. n Point the sufficient condition where the VCG mechanism is false-name-proof n Group-strategy-poof n

Future work Consider the false-name bids in: n no theoretical bound on the efficiency loss n Multi-unit auction n Situation where multiple buyers and sellers bit to exchange a designated good

Question?
- Slides: 35