The EAuthentication Initiative Federal eAuthentication Initiative Federated Identity





- Slides: 18

The E-Authentication Initiative Federal e-Authentication Initiative: Federated Identity and Interoperability David Temoshok Director, Identity Policy and Management GSA Office of Governmentwide Policy August 20, 2004

President’s Management Agenda • • 1 st Priority: Make Government citizen-centered. 5 Key Government-wide Initiatives: ü Strategic Management of Human Capital ü Competitive Sourcing ü Improved Financial performance ü Expanded Electronic Government ü Budget and Performance Integration The E-Authentication Initiative 2

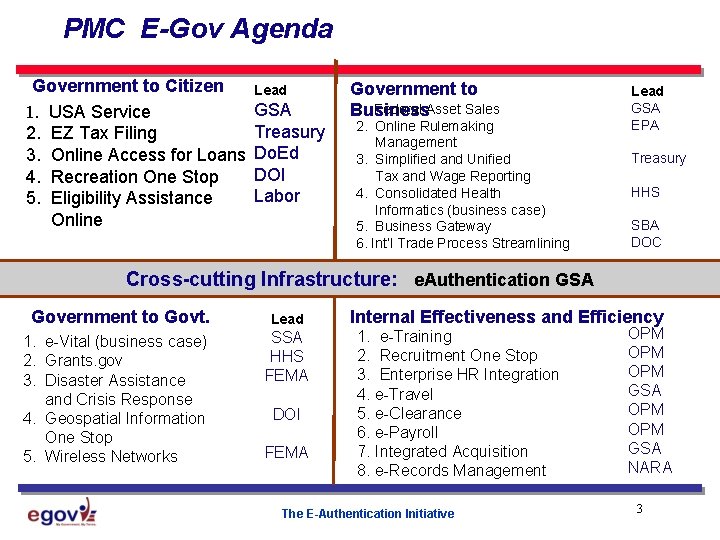
PMC E-Gov Agenda Government to Citizen 1. USA Service 2. EZ Tax Filing 3. Online Access for Loans 4. Recreation One Stop 5. Eligibility Assistance Online Lead GSA Treasury Do. Ed DOI Labor Government to 1. Federal Asset Sales Business 2. Online Rulemaking Management 3. Simplified and Unified Tax and Wage Reporting 4. Consolidated Health Informatics (business case) 5. Business Gateway 6. Int’l Trade Process Streamlining Lead GSA EPA Treasury HHS SBA DOC Cross-cutting Infrastructure: e. Authentication GSA Government to Govt. 1. e-Vital (business case) 2. Grants. gov 3. Disaster Assistance and Crisis Response 4. Geospatial Information One Stop 5. Wireless Networks Lead SSA HHS FEMA DOI FEMA Internal Effectiveness and Efficiency 1. e-Training 2. Recruitment One Stop 3. Enterprise HR Integration 4. e-Travel 5. e-Clearance 6. e-Payroll 7. Integrated Acquisition 8. e-Records Management The E-Authentication Initiative OPM OPM GSA NARA 3

The Starting Place for e-Authentication: Key Policy Points For Governmentwide deployment: u No National ID. u No National unique identifier. u No central registry of personal information, attributes, or authorization privileges. u Different authentication assurance levels are needed for different types of transactions. And for e-Authentication technical approach: u No single proprietary solution u Deploy multiple COTS products -- users choice u Products must interoperate together u Controls must protect privacy of personal information. The E-Authentication Initiative 4

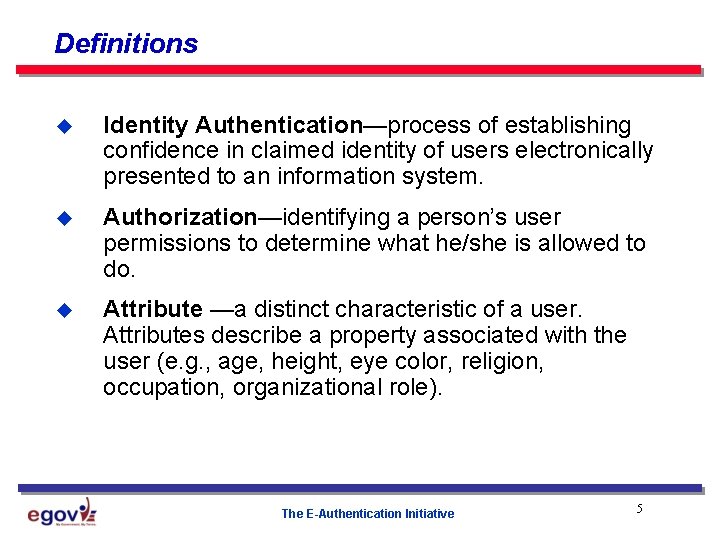
Definitions u Identity Authentication—process of establishing confidence in claimed identity of users electronically presented to an information system. u Authorization—identifying a person’s user permissions to determine what he/she is allowed to do. u Attribute —a distinct characteristic of a user. Attributes describe a property associated with the user (e. g. , age, height, eye color, religion, occupation, organizational role). The E-Authentication Initiative 5

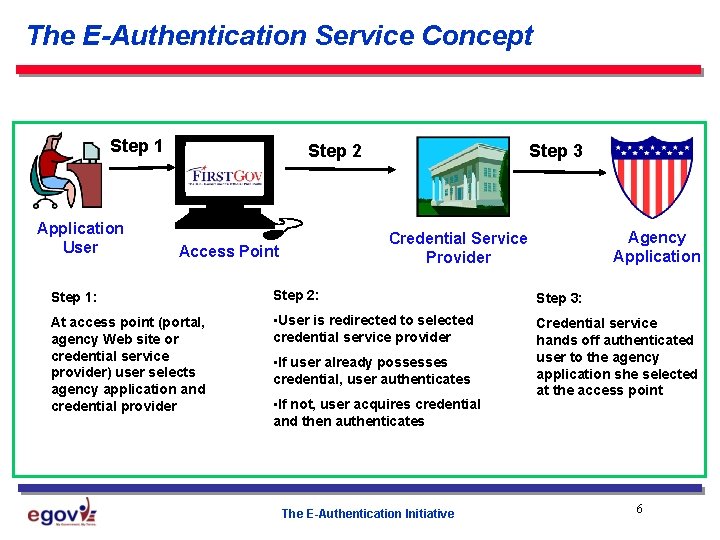
The E-Authentication Service Concept Step 1 Application User Step 2 Step 3 Agency Application Credential Service Provider Access Point Step 1: Step 2: Step 3: At access point (portal, agency Web site or credential service provider) user selects agency application and credential provider • User is redirected to selected credential service provider Credential service hands off authenticated user to the agency application she selected at the access point • If user already possesses credential, user authenticates • If not, user acquires credential and then authenticates The E-Authentication Initiative 6

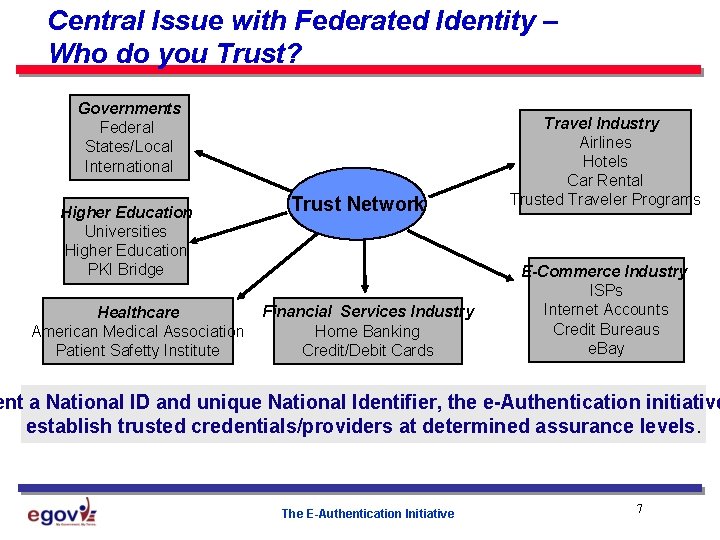
Central Issue with Federated Identity – Who do you Trust? Governments Federal States/Local International Higher Education Universities Higher Education PKI Bridge Healthcare American Medical Association Patient Safetty Institute Trust Network Financial Services Industry Home Banking Credit/Debit Cards Travel Industry Airlines Hotels Car Rental Trusted Traveler Programs E-Commerce Industry ISPs Internet Accounts Credit Bureaus e. Bay ent a National ID and unique National Identifier, the e-Authentication initiative establish trusted credentials/providers at determined assurance levels. The E-Authentication Initiative 7

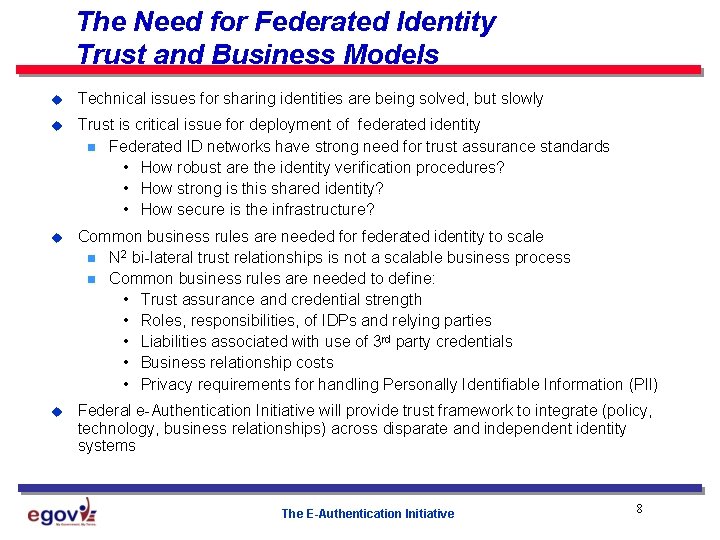
The Need for Federated Identity Trust and Business Models u Technical issues for sharing identities are being solved, but slowly u Trust is critical issue for deployment of federated identity n Federated ID networks have strong need for trust assurance standards • How robust are the identity verification procedures? • How strong is this shared identity? • How secure is the infrastructure? u Common business rules are needed for federated identity to scale n N 2 bi-lateral trust relationships is not a scalable business process n Common business rules are needed to define: • Trust assurance and credential strength • Roles, responsibilities, of IDPs and relying parties • Liabilities associated with use of 3 rd party credentials • Business relationship costs • Privacy requirements for handling Personally Identifiable Information (PII) u Federal e-Authentication Initiative will provide trust framework to integrate (policy, technology, business relationships) across disparate and independent identity systems The E-Authentication Initiative 8

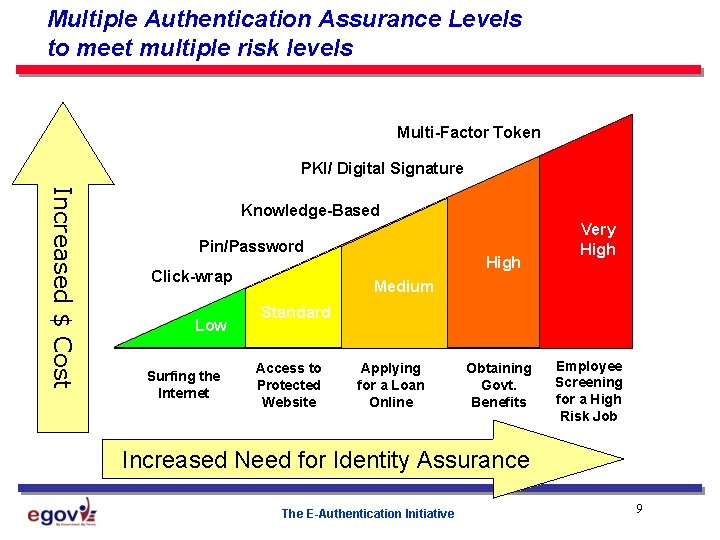
Multiple Authentication Assurance Levels to meet multiple risk levels Multi-Factor Token PKI/ Digital Signature Increased $ Cost Knowledge-Based Pin/Password Click-wrap Low Surfing the Internet High Very High Medium Standard Access to Protected Website Applying for a Loan Online Obtaining Govt. Benefits Employee Screening for a High Risk Job Increased Need for Identity Assurance The E-Authentication Initiative 9

Authentication Assurance Levels M-04 -04: E-Authentication Guidance for Federal Agencies establishes 4 authentication assurance levels Level 1 Level 2 Level 3 Level 4 Little or no confidence in asserted identity Some confidence in asserted identity (e. g. PIN/Password) High confidence in asserted identity (e. g. digital cert) Very high confidence in the asserted identity (e. g. Smart Card) (e. g. self identified user/password) NIST SP 800 -63 Electronic Authentication NIST technical guidance to match technology implementation to a level The E-Authentication Initiative 10

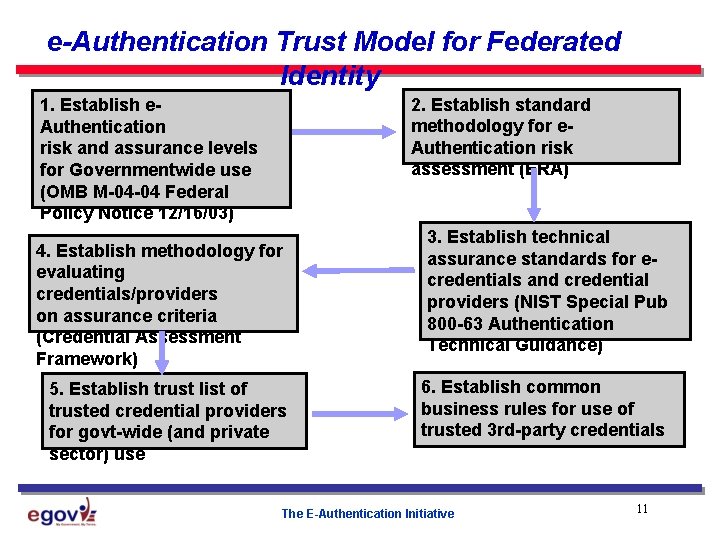
e-Authentication Trust Model for Federated Identity 2. Establish standard methodology for e. Authentication risk assessment (ERA) 1. Establish e. Authentication risk and assurance levels for Governmentwide use (OMB M-04 -04 Federal Policy Notice 12/16/03) 4. Establish methodology for evaluating credentials/providers on assurance criteria (Credential Assessment Framework) 5. Establish trust list of trusted credential providers for govt-wide (and private sector) use 3. Establish technical assurance standards for ecredentials and credential providers (NIST Special Pub 800 -63 Authentication Technical Guidance) 6. Establish common business rules for use of trusted 3 rd-party credentials The E-Authentication Initiative 11

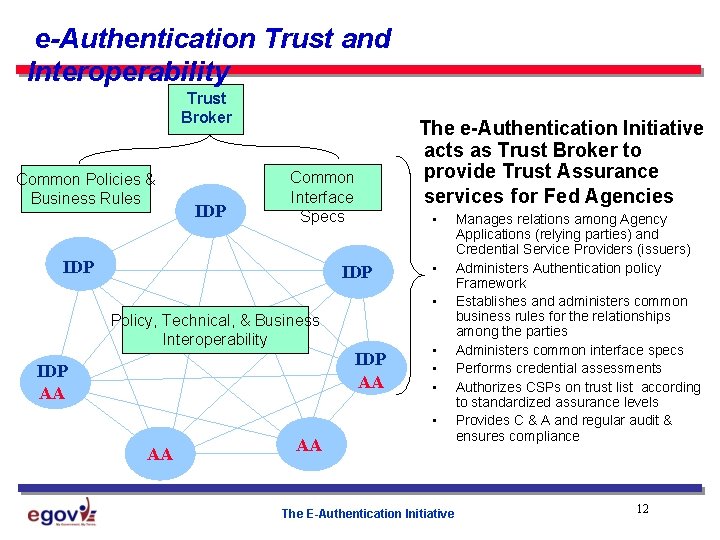
e-Authentication Trust and Interoperability Trust Broker Common Policies & Business Rules IDP The e-Authentication Initiative acts as Trust Broker to provide Trust Assurance services for Fed Agencies Common Interface Specs IDP • • Policy, Technical, & Business Interoperability IDP AA • • AA AA The E-Authentication Initiative Manages relations among Agency Applications (relying parties) and Credential Service Providers (issuers) Administers Authentication policy Framework Establishes and administers common business rules for the relationships among the parties Administers common interface specs Performs credential assessments Authorizes CSPs on trust list according to standardized assurance levels Provides C & A and regular audit & ensures compliance 12

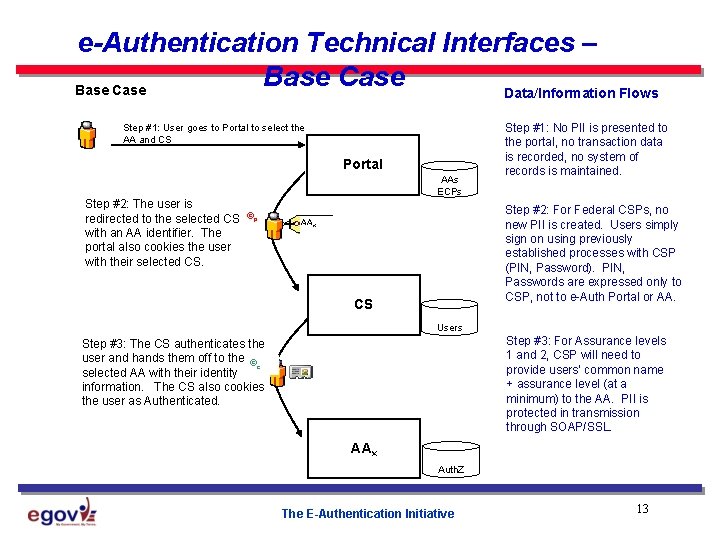
e-Authentication Technical Interfaces – Base Case Data/Information Flows Step #1: User goes to Portal to select the AA and CS Portal Step #2: The user is redirected to the selected CS ©p with an AA identifier. The portal also cookies the user with their selected CS. AAs ECPs Step #1: No PII is presented to the portal, no transaction data is recorded, no system of records is maintained. Step #2: For Federal CSPs, no new PII is created. Users simply sign on using previously established processes with CSP (PIN, Password). PIN, Passwords are expressed only to CSP, not to e-Auth Portal or AA. AAx CS Users Step #3: For Assurance levels 1 and 2, CSP will need to provide users’ common name + assurance level (at a minimum) to the AA. PII is protected in transmission through SOAP/SSL. Step #3: The CS authenticates the user and hands them off to the © c selected AA with their identity information. The CS also cookies the user as Authenticated. AAx Auth. Z The E-Authentication Initiative 13

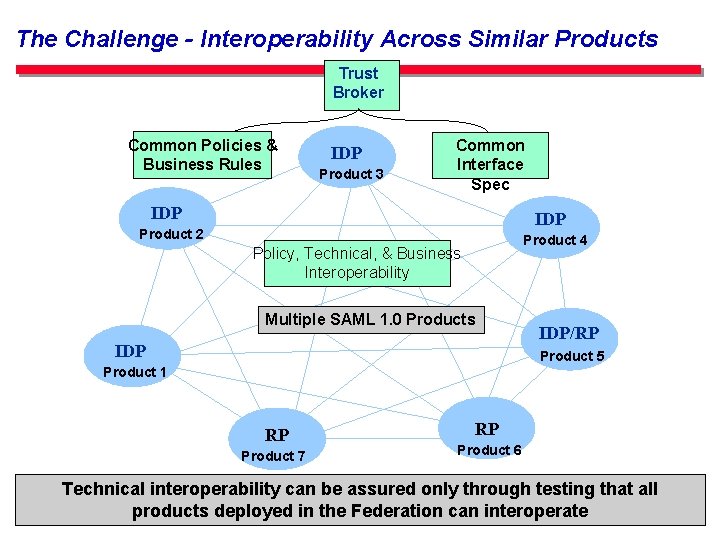
The Challenge - Interoperability Across Similar Products Trust Broker Common Policies & Business Rules IDP Product 3 Common Interface Spec IDP Product 2 Product 4 Policy, Technical, & Business Interoperability Multiple SAML 1. 0 Products IDP/RP Product 5 Product 1 RP Product 7 RP Product 6 Technical interoperability can be assured only through testing that all 14 products deployed the Federation can interoperate Thein E-Authentication Initiative

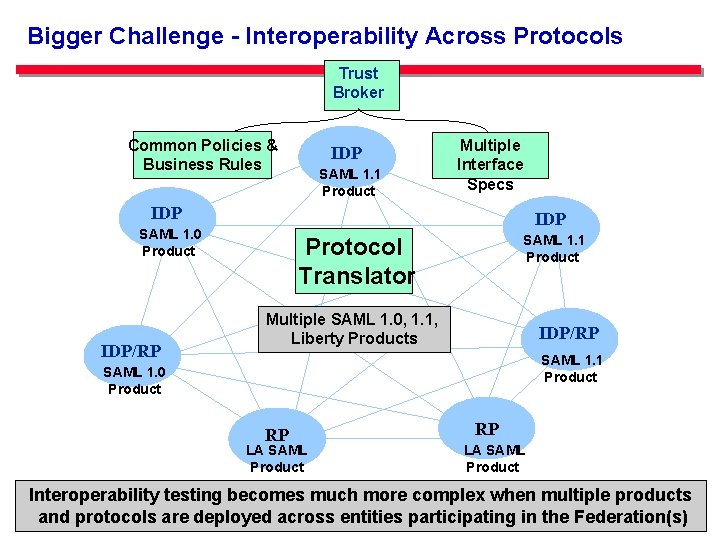
Bigger Challenge - Interoperability Across Protocols Trust Broker Common Policies & Business Rules IDP SAML 1. 1 Product Multiple Interface Specs IDP SAML 1. 0 Product IDP/RP SAML 1. 1 Product Protocol Translator Multiple SAML 1. 0, 1. 1, Liberty Products IDP/RP SAML 1. 1 Product SAML 1. 0 Product RP LA SAML Product Interoperability testing becomes much more complex when multiple products 15 The E-Authentication and protocols are deployed across entities Initiative participating in the Federation(s)

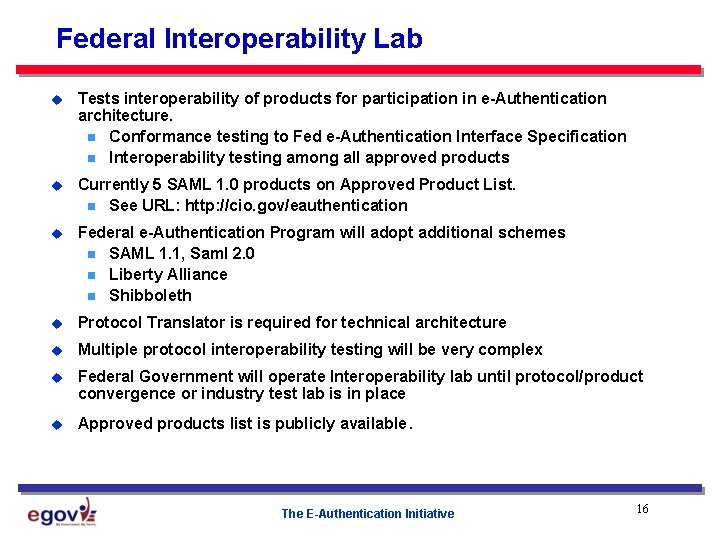
Federal Interoperability Lab u Tests interoperability of products for participation in e-Authentication architecture. n Conformance testing to Fed e-Authentication Interface Specification n Interoperability testing among all approved products u Currently 5 SAML 1. 0 products on Approved Product List. n See URL: http: //cio. gov/eauthentication u Federal e-Authentication Program will adopt additional schemes n SAML 1. 1, Saml 2. 0 n Liberty Alliance n Shibboleth u Protocol Translator is required for technical architecture u Multiple protocol interoperability testing will be very complex u Federal Government will operate Interoperability lab until protocol/product convergence or industry test lab is in place u Approved products list is publicly available. The E-Authentication Initiative 16

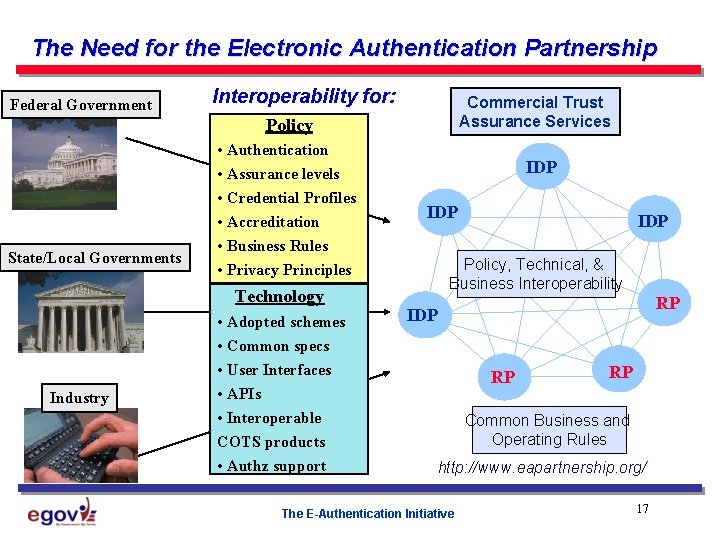
The Need for the Electronic Authentication Partnership Federal Government Interoperability for: Commercial Trust Assurance Services Policy State/Local Governments • Authentication • Assurance levels • Credential Profiles • Accreditation • Business Rules • Privacy Principles Technology Industry • Adopted schemes • Common specs • User Interfaces • APIs • Interoperable COTS products • Authz support IDP IDP Policy, Technical, & Business Interoperability RP IDP RP RP Common Business and Operating Rules http: //www. eapartnership. org/ The E-Authentication Initiative 17

For More Information Phone David Temoshok E-mail 202 -208 -7655 david. temoshok@gsa. gov Websites http: //cio. gov/eauthentication http: //www. eapartnership. org/ http: //cio. gov/fpkipa The E-Authentication Initiative
 Eauthentication
Eauthentication Usda eauthentication level 2
Usda eauthentication level 2 Ibm esso
Ibm esso Ucf federated identity
Ucf federated identity What is fssi
What is fssi Social identity mapping
Social identity mapping Federated database system
Federated database system Benefits of federated search
Benefits of federated search Federated search ui
Federated search ui Federated discovery
Federated discovery Centralized vs distributed database
Centralized vs distributed database Federated service solutions
Federated service solutions Federated data mart
Federated data mart Federated search examples
Federated search examples Federated search vs discovery
Federated search vs discovery Federated learning
Federated learning Federated architecture avionics
Federated architecture avionics Federated messaging
Federated messaging Federated search
Federated search