The Cryptographic Module Validation Program and FIPS 140



















- Slides: 37

The Cryptographic Module Validation Program and FIPS 140 -2

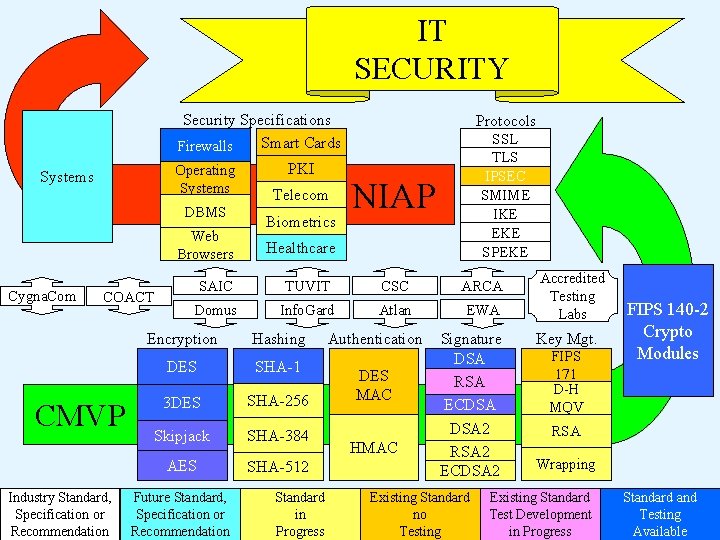
IT SECURITY Security Specifications Smart Cards Firewalls Operating Systems DBMS Web Browsers Cygna. Com COACT CMVP Industry Standard, Specification or Recommendation PKI Telecom Biometrics Protocols SSL TLS IPSEC SMIME IKE EKE SPEKE NIAP Healthcare SAIC TUVIT CSC ARCA Domus Info. Gard Atlan EWA Encryption Hashing DES SHA-1 3 DES SHA-256 Skipjack SHA-384 AES SHA-512 Future Standard, Specification or Recommendation Standard in Progress Authentication DES MAC HMAC Signature DSA RSA ECDSA 2 RSA 2 ECDSA 2 Existing Standard no Testing Accredited Testing Labs Key Mgt. FIPS 171 D-H MQV FIPS 140 -2 Crypto Modules RSA Wrapping Existing Standard Test Development in Progress Standard and Testing Available


Cryptographic Module Validation Program (CMVP) n n n Established by NIST and the Communications Security Establishment (CSE) in 1995 Original FIPS 140 -1 requirements and updated FIPS 140 -2 requirements developed with industry input Six NVLAP-accredited testing laboratories n n True independent 3 rd party accredited testing laboratories Can not test and provide design assistance

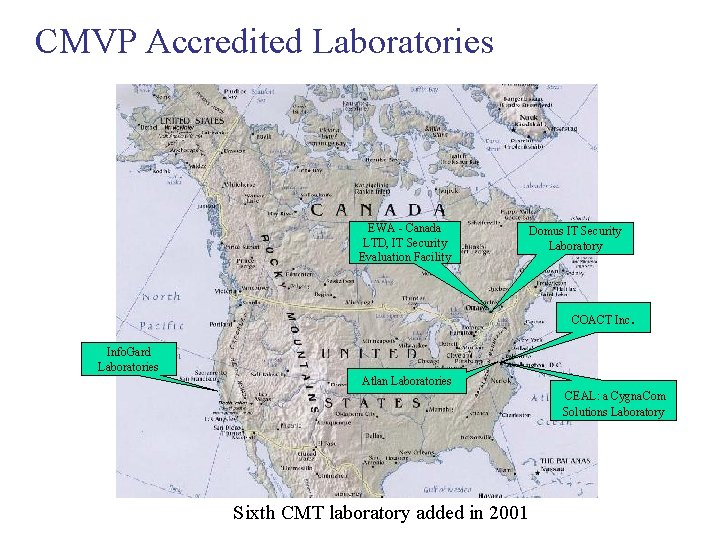
CMVP Accredited Laboratories EWA - Canada LTD, IT Security Evaluation Facility Domus IT Security Laboratory COACT Inc. Info. Gard Laboratories Atlan Laboratories CEAL: a Cygna. Com Solutions Laboratory Sixth CMT laboratory added in 2001

Applicability of FIPS 140 -2 n n n U. S. Federal organizations must use validated cryptographic modules Go. C departments are recommended by CSE to use validated cryptographic modules International recognition

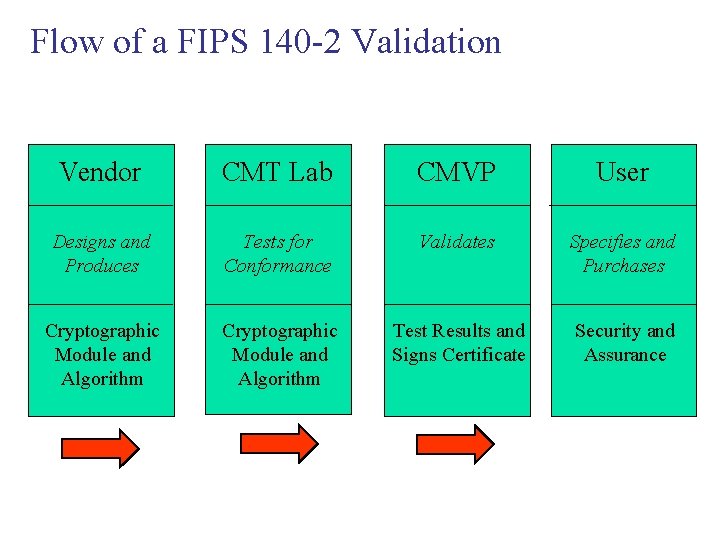
Flow of a FIPS 140 -2 Validation Vendor CMT Lab CMVP User Designs and Produces Tests for Conformance Validates Specifies and Purchases Cryptographic Module and Algorithm Test Results and Signs Certificate Security and Assurance

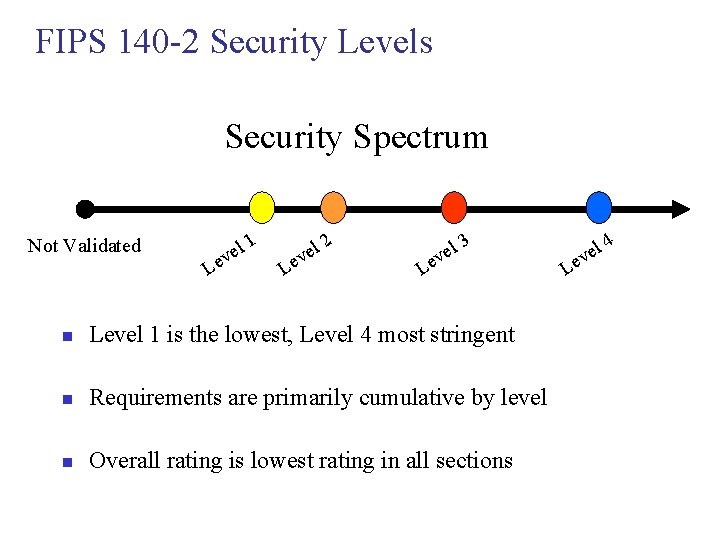
FIPS 140 -2 Security Levels Security Spectrum Not Validated Le l ve 1 el v Le 2 l 3 e v Le n Level 1 is the lowest, Level 4 most stringent n Requirements are primarily cumulative by level n Overall rating is lowest rating in all sections Le l ve 4

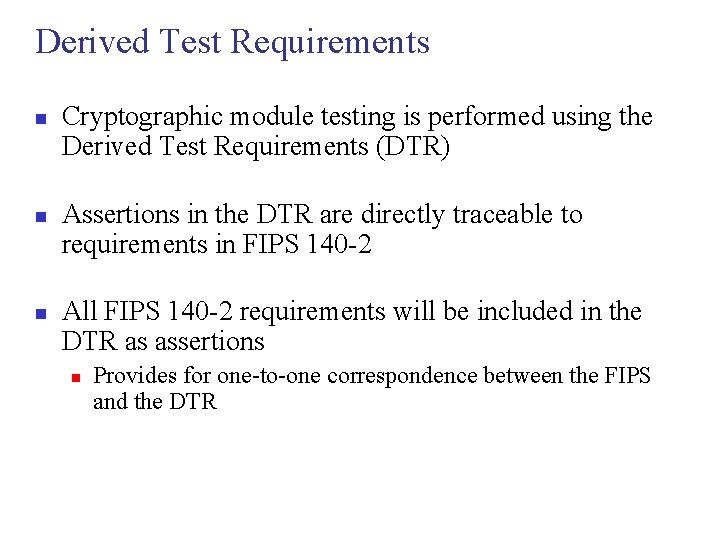
Derived Test Requirements n n n Cryptographic module testing is performed using the Derived Test Requirements (DTR) Assertions in the DTR are directly traceable to requirements in FIPS 140 -2 All FIPS 140 -2 requirements will be included in the DTR as assertions n Provides for one-to-one correspondence between the FIPS and the DTR

Derived Test Requirements n Each assertion will include requirements levied on the n n n (concluded) Cryptographic module vendor Tester of the cryptographic module Modules tested against FIPS 140 -2 will use the associated DTR

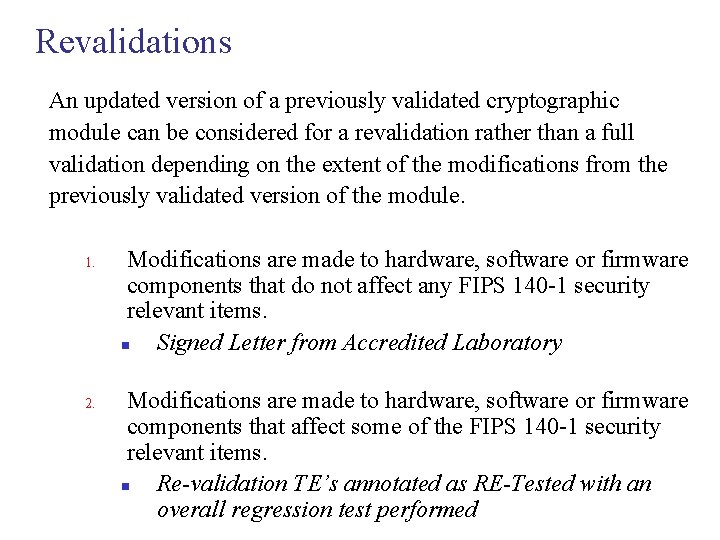
Revalidations An updated version of a previously validated cryptographic module can be considered for a revalidation rather than a full validation depending on the extent of the modifications from the previously validated version of the module. 1. 2. Modifications are made to hardware, software or firmware components that do not affect any FIPS 140 -1 security relevant items. n Signed Letter from Accredited Laboratory Modifications are made to hardware, software or firmware components that affect some of the FIPS 140 -1 security relevant items. n Re-validation TE’s annotated as RE-Tested with an overall regression test performed

CMVP Status n Continued record growth in the number of cryptographic modules validated n n n Over 200 Validations representing nearly 250 modules All four security levels of FIPS 140 -1 represented on the Validated Modules List Over forty participating vendors

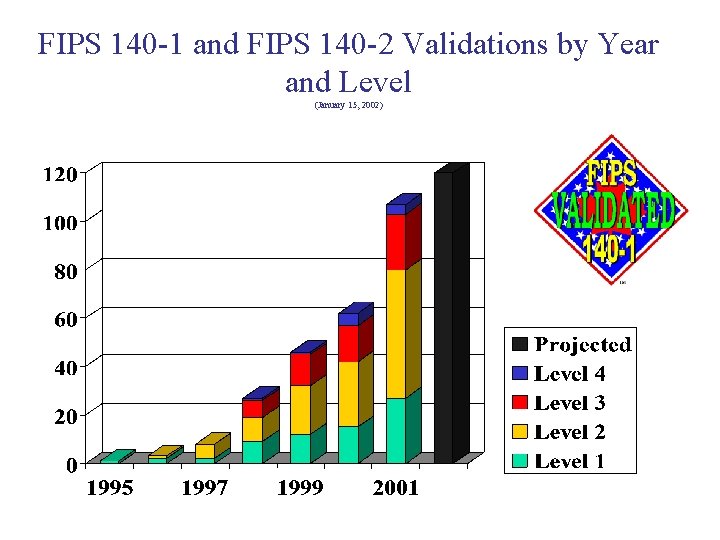
FIPS 140 -1 and FIPS 140 -2 Validations by Year and Level (January 15, 2002)

2001 Validation Milestones Certificate 200 December 18, 2001 • FIPS 140 -2 Signed 05/25/01 • FIPS 140 -2 DTR Available 11/15/01 • FIPS 140 -2 Validations Accepted Certificate 150 May 23, 2001

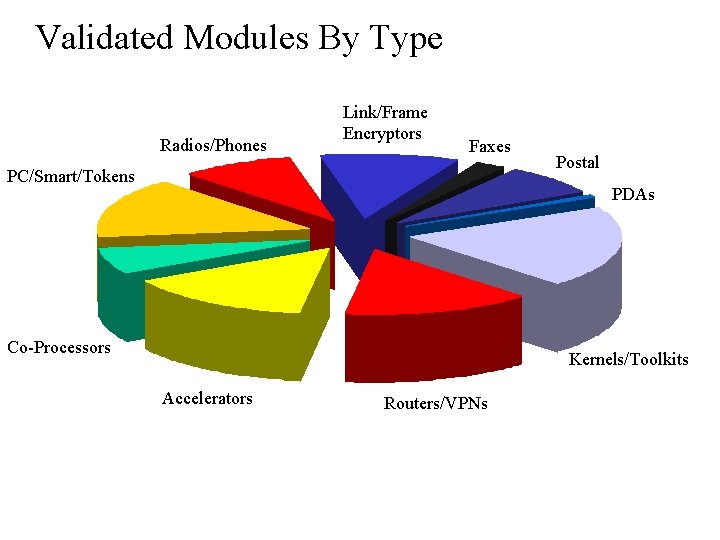
Validated Modules By Type Radios/Phones Link/Frame Encryptors Faxes PC/Smart/Tokens Postal PDAs Co-Processors Kernels/Toolkits Accelerators Routers/VPNs

FIPS 140 -2 - Testing Begins n n FIPS 140 -2 Testing officially began November 15, 2001 FIPS 140 -1 Testing ends May 25, 2002 Testing laboratories may submit FIPS 140 -1 validation test reports until May 25, 2002 After May 25, 2002 all validations and revalidations must be done against FIPS 140 -2

FIPS 140 -2 - Testing Begins … n n Agencies may continue to purchase, retain and use FIPS 140 -1 validated products after May 25, 2002. NIST has provided common algorithmic testing tool to Accredited Laboratories: n n Includes DES, Triple-DES and AES DSA and SHA-1 - to be integrated ECDSA available as separate tool – to be integrated RSA, SHA-{256, 384, 512}, DH, MQV - future

CMVP Status (concluded) n n End of FIPS 140 -1 testing and beginning of FIPS 140 -2 testing and validations with new implementations of FIPS 197 (AES) expected to cause unparalleled growth Increasing international recognition of the CMVP and FIPS 140 -2

Communications-Electronics Security Group (CESG) - UK • December 28, 2001 – CESG proposes the use of FIPS 140 as the basis for the evaluation of cryptographic products used in a number of UK government applications and encourages the setting up of accredited laboratories in the UK to perform these evaluations.

… Making a Difference n 164 Cryptographic Modules Surveyed (during testing) n n n 80 (48. 8%) Security Flaws discovered 158 (96. 3%) Documentation Errors 332 Algorithm Validations (during testing) (DES, Triple-DES, DSA and SHA-1) n 88 (26. 5%) Security Flaws n 216 (65. 1%) Documentation Errors n Areas of Greatest Difficulty n n Physical Security Self Tests Random Number Generation Key Management

Participating Vendors Alcatel Algorithmic Research, Ltd. Ascom Hasler Mailing Systems Attachmate Corp. Avaya, Inc. Baltimore Technologies (UK) Ltd. Blue Ridge Networks Certicom Corp. Chrysalis-ITS Inc. Cisco Systems, Inc. Cryptek Security Communications, LLC CTAM, Inc. Cylink Corporation Dallas Semiconductor, Inc. Datakey, Inc. Ensuredmail, Inc. Entrust Technologies Limited Eracom Technologies Group, Eracom Technologies Australia, Pty. Ltd. (January 15, 2002) F-Secure Corporation Fortress Technologies Francotyp-Postalia GTE Internetworking IBM Intel Network Systems, Inc. IRE, Inc. Kasten Chase Applied Research L-3 Communication Systems Litronic, Inc. M/A Com Wireless Systems Microsoft Corporation. Motorola, Inc. Mykotronx. Inc National Semiconductor Corp. n. Cipher Corporation Ltd. Neopost Industrie Neopost Ltd. Neopost Online Netscape Communications Corp. Net. Screen Technologies, Inc. Network Associates, Inc. Nortel Networks Novell, Inc. Oracle Corporation Pitney Bowes, Inc. Privy. Link Pte Ltd PSI Systems, Inc. Rainbow Technologies Red. Creek Communications Research In Motion RSA Data Security, Inc. Schlumberger. Sema Spyrus, Inc. Stamps. com Technical Communications Corp. Thales e-Security Time. Step Corporation Transcrypt International Tumbleweed Communications Corp. V-ONE Corporation, Inc.

http: //www. nist. gov/cmvp n n n n FIPS 140 -1 and FIPS 140 -2 Derived Test Requirements (DTR) Annexes to FIPS 140 -2 Implementation Guidance Points of Contact Laboratory Information Validated Modules List Special Publication 800 -23

ADDITIONAL BACKGROUND

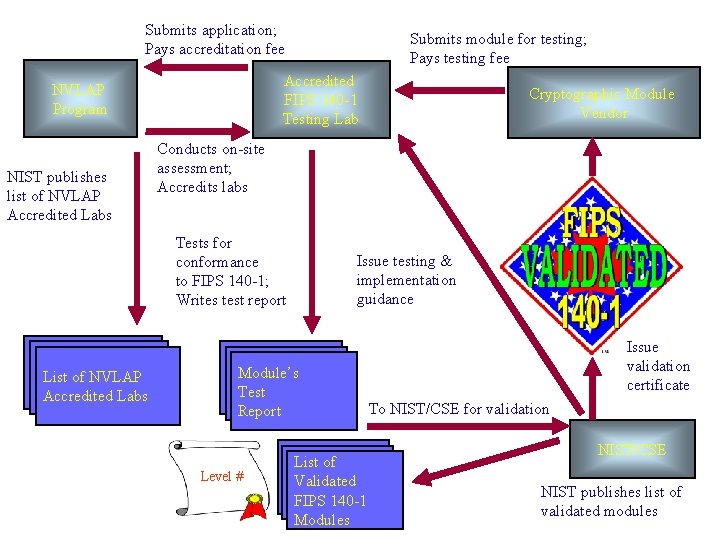
Submits application; Pays accreditation fee Accredited FIPS 140 -1 Testing Lab NVLAP Program NIST publishes list of NVLAP Accredited Labs Submits module for testing; Pays testing fee Conducts on-site assessment; Accredits labs Tests for conformance to FIPS 140 -1; Writes test report List of NVLAP Accredited Labs Cryptographic Module Vendor Issue testing & implementation guidance Module’s Test Report Level # List of Validated FIPS 140 -1 Modules Issue validation certificate To NIST/CSE for validation NIST/CSE NIST publishes list of validated modules

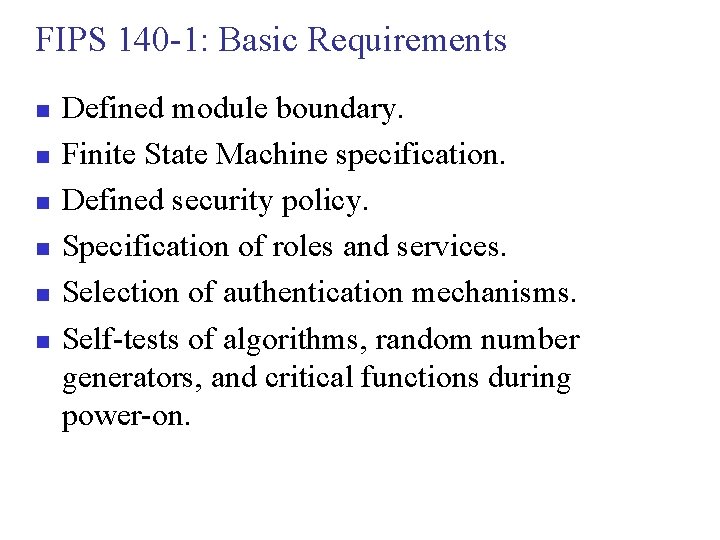
FIPS 140 -1: Basic Requirements n n n Defined module boundary. Finite State Machine specification. Defined security policy. Specification of roles and services. Selection of authentication mechanisms. Self-tests of algorithms, random number generators, and critical functions during power-on.

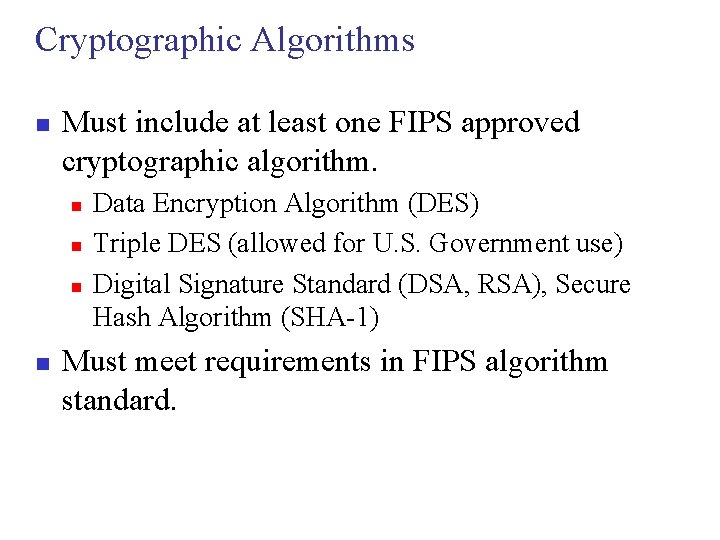
Cryptographic Algorithms n Must include at least one FIPS approved cryptographic algorithm. n n Data Encryption Algorithm (DES) Triple DES (allowed for U. S. Government use) Digital Signature Standard (DSA, RSA), Secure Hash Algorithm (SHA-1) Must meet requirements in FIPS algorithm standard.

FIPS 140 -1 Security Level 1 n n n Specification of the cryptographic module boundary. Production-grade equipment. Logical separation of roles and services but no required authentication. FIPS approved key management. Allows software cryptographic services on a single user general purpose computer.

FIPS 140 -1 Security Level 2 n n n Tamper evident coatings or seals, or pickresistant locks. Role-based authentication to determine if an operator is authorized to assume a specific role and perform a corresponding set of services. Allows software cryptography in evaluated multi-user timeshared systems.

FIPS 140 -1 Security Level 3 n n Tamper detection and response for covers and doors. Identity-based authentication. Stronger requirements for entering and outputting critical security parameters and cryptographic keys. Trusted path requirements for modules using trusted operating systems.

FIPS 140 -1 Security Level 4 n n n Envelope of protection around the entire cryptographic module. Environmental failure protection and testing. Formal modeling for software.

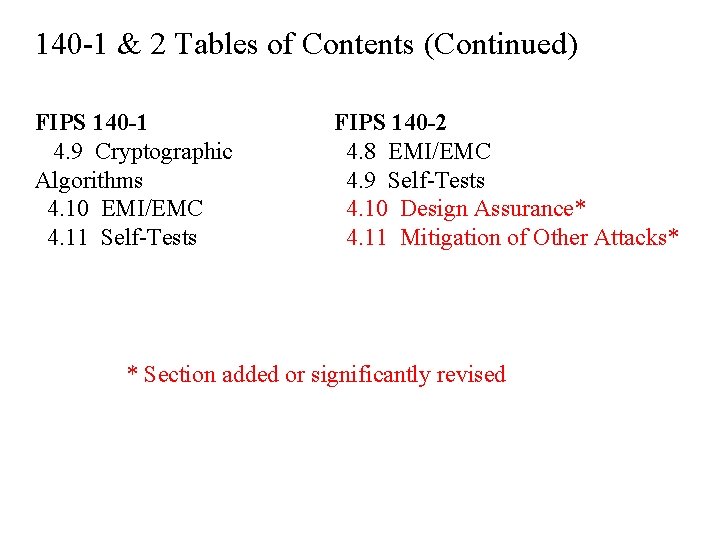
Differences Between FIPS 140 -1 and FIPS 140 -2 140 -1 & 2 Tables of Contents FIPS 140 -1 1. Overview 2. Glossary of Terms and Acronyms 3. Functional Security Requirements 4. 1 Cryptographic Modules 4. 2 Cryptographic Module Interfaces FIPS 140 -2 1. Overview 2. Glossary of Terms and Acronyms* 3. Functional Security Requirements 4. 1 Cryptographic Module Specification* 4. 2 Cryptographic Module Interfaces * Section added or significantly revised

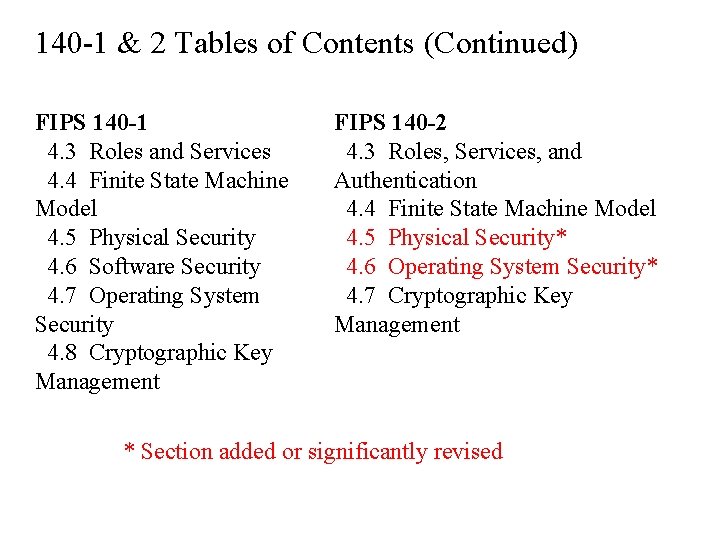
140 -1 & 2 Tables of Contents (Continued) FIPS 140 -1 4. 3 Roles and Services 4. 4 Finite State Machine Model 4. 5 Physical Security 4. 6 Software Security 4. 7 Operating System Security 4. 8 Cryptographic Key Management FIPS 140 -2 4. 3 Roles, Services, and Authentication 4. 4 Finite State Machine Model 4. 5 Physical Security* 4. 6 Operating System Security* 4. 7 Cryptographic Key Management * Section added or significantly revised

140 -1 & 2 Tables of Contents (Continued) FIPS 140 -1 4. 9 Cryptographic Algorithms 4. 10 EMI/EMC 4. 11 Self-Tests FIPS 140 -2 4. 8 EMI/EMC 4. 9 Self-Tests 4. 10 Design Assurance* 4. 11 Mitigation of Other Attacks* * Section added or significantly revised

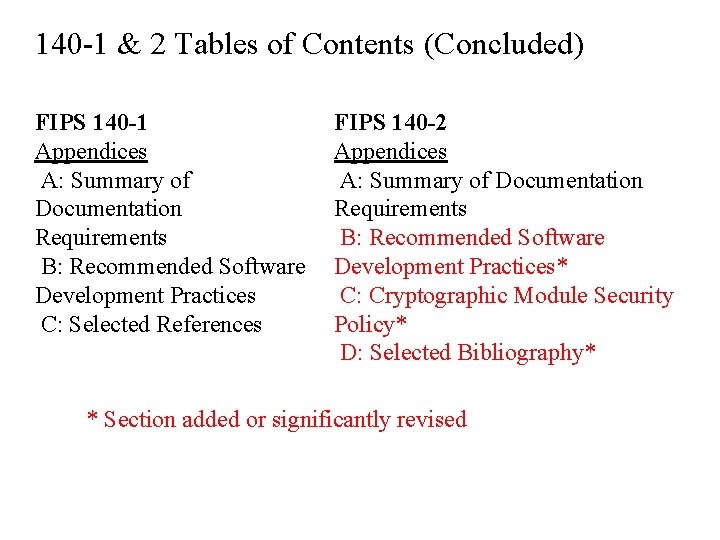
140 -1 & 2 Tables of Contents (Concluded) FIPS 140 -1 Appendices A: Summary of Documentation Requirements B: Recommended Software Development Practices C: Selected References FIPS 140 -2 Appendices A: Summary of Documentation Requirements B: Recommended Software Development Practices* C: Cryptographic Module Security Policy* D: Selected Bibliography* * Section added or significantly revised

FIPS 140 -2: Final Revisions n 4. 2 Cryptographic Module Interfaces n Security Levels 3 and 4 n n Physical ports for input/output of plaintext CSPs shall be physically separate from other ports Logical interfaces for input/output of plaintext CSPs shall be logically separate from all other interfaces n Requires implementation of a trusted path

FIPS 140 -2: Final Revisions (continued) n 4. 6 Operational Environment n Operating system definition expanded to operational environment n general purpose operational environment refers to n n Limited operational environment refers to n n n the use of a commercially-available general purpose operating system (i. e. , resource manager) n manages the software and firmware components within the cryptographic boundary a static non-modifiable virtual operational environment n with no underlying general purpose OS Requirements in FIPS 140 -2 do not apply Modifiable operational environment refers to n n n an operating environment that may be reconfigured to add/delete/modify functionality and/or may include general purpose OS capabilities Requirements in FIPS 140 -2 apply

FIPS 140 -2: Final Revisions (continued) n 4. 10 Design Assurance n Development n n Guidance n n Deleted requirements addressed in other sections of FIPS 140 -2 Deleted security requirements for the IT environment Functional Testing and Test Coverage n Deleted all requirements