The Case for Tripwire Nick Chodorow Sarah Kronk









- Slides: 14

The Case for Tripwire® Nick Chodorow Sarah Kronk Jim Moriarty Chris Tartaglia

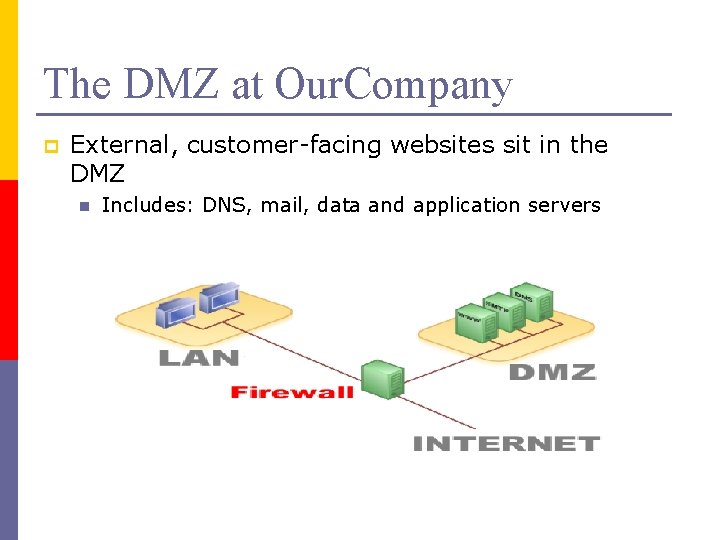
The DMZ at Our. Company p External, customer-facing websites sit in the DMZ n Includes: DNS, mail, data and application servers

The DMZ and Risk p Internal Risk n n p Botched migration of software Patch application gone awry External Risk n n DMZ is exposed to the Internet Intruders could modify, remove, or add files to the servers resulting in a multitude of issues

Is the solution?

What is p The most popular host-based IDS for Linux n p Also popular with Windows Change monitoring and analysis tool n p ? Establishes control over both authorized and unauthorized changes on servers Provides enterprises with … n n n High availability Compliance with regulations from internal and external policies More effective systems security

What can p Detect n n p Provides change detection across network servers, routers, switchers, firewalls, ect. Captures all changes (malicious and authorized) Reconcile n p do? Rapidly determines which files have been changed Report n n Audit Logs Real-Time notification (e-mail)

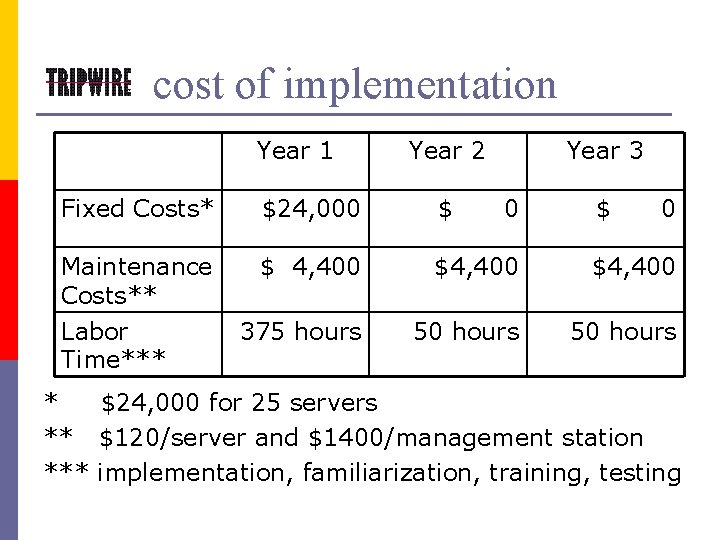
cost of implementation Year 1 Year 2 Year 3 Fixed Costs* $24, 000 $ Maintenance Costs** $ 4, 400 $4, 400 375 hours 50 hours Labor Time*** 0 $ 0 * $24, 000 for 25 servers ** $120/server and $1400/management station *** implementation, familiarization, training, testing

Management Buy-In p Problem n n p High initial cost and man-hours Management not concerned with internal risk What sold Management? n The ability to monitor the DMZ 24/7 from illicit activity … and then be able to recover quickly

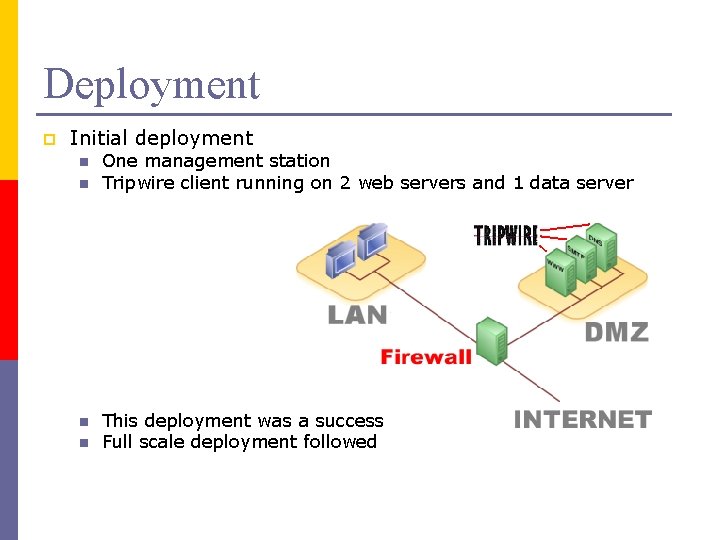
Deployment p Initial deployment n n One management station Tripwire client running on 2 web servers and 1 data server This deployment was a success Full scale deployment followed

concerns p Too many false positives n n p Due to mis-configuration Server group less likely to promptly address real issues Do Tripwire vulnerabilities exist? n 2004 – Format String Vulnerability p n 2001 – Symbolic link attack p n When an e-mail report was created, a local user could execute arbitrary code that runs as the same rights as the user running the file check (usually root or sys admin) On Linux and Unix, Tripwire opens insecure temporary files with predictable names in publicly-writable directories. Using a symbolic link attack, a local intruder may overwrite or create arbitrary files on machines running tripwire. Others ? ? ?

Alternative IDS Products p Symantec IDS n n n “Only true real-time monitoring services in the Managed Security Services industry “ Host-Based Centralized Console Management p n Price varies upon support p p Can view Network-Based IDS in same console Different levels of service can be purchased Why was Symantec IDS not chosen? n Our. Company already uses Symantec Anti-Virus … did not want a single vendor security solution

Alternative IDS Products (Open Source) p Samhain -n n Host-Based Centralized-Monitoring Web-Based Management Console Tamper Resistant p n p PGP-Signed database and configuration files Terms under GNU General Public License FCheck -n n n http: //www. la-samhna. de/samhain/ http: //www. geocities. com/fcheck 2000/fcheck. html PERL script creates “snapshot” of system in known state Monitors machines against “snapshot” and reports inconsistencies Terms under GNU General Public License

Alternative IDS Products (Open Source) p AIDE -n n p Stands for Advanced Intrusion Detection Environment Similar capabilities as Tripwire Billed as a free replacement for Tripwire Terms under GNU General Public License Integrit -- http: //sourceforge. net/projects/integrit n n n p http: //sourceforge. net/projects/aide Simple, secure alternative to Tripwire and AIDE Small memory footprint Terms under GNU General Public License Why NONE of these products were chosen? n n Management at Our. Company does not consider Open Source an option at this time No support plan available on these products

Questions ? ? ?