The Assumed Breach Model A Practical Approach Manager


The Assumed Breach Model A Practical Approach

• Manager – Security Architecture • Heavily focused on Cloud/AWS • Experience includes moving from End User Support, to Sys Admin, to Consulting, to Information Security to Security Architecture

Agenda • Current Landscape • Strategy • Next Steps

Current Security Landscape • Checking Boxes • We play whack-a-mole with security controls and tools
Shiny New Toys…Tools • This is a firewall without a strategy
Primarily Reactive • We just collect logs to collect logs

What is assumed breach? • Simply put: A security strategy that assumes any given endpoint is breached to some extent and controls risk as such.

Strategy • • Access Control Choke Points Trust Zones Detection Capabilities

Principles • Empower Business • Keep It Simple
Access Control • What is being protected? • How do we protect it if we assume it is already breached?
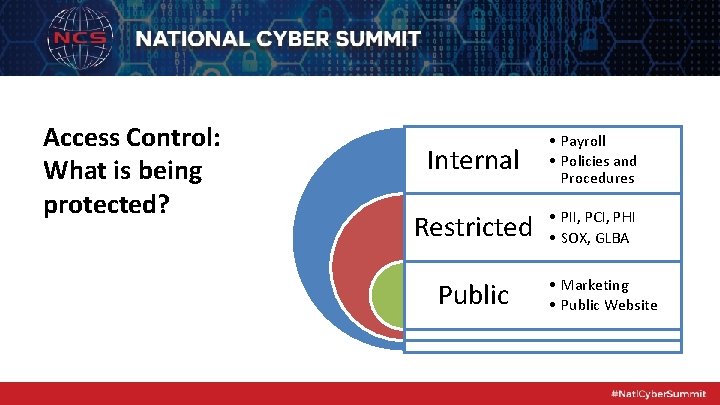
Access Control: What is being protected? Internal • Payroll • Policies and Procedures Restricted • PII, PCI, PHI • SOX, GLBA Public • Marketing • Public Website
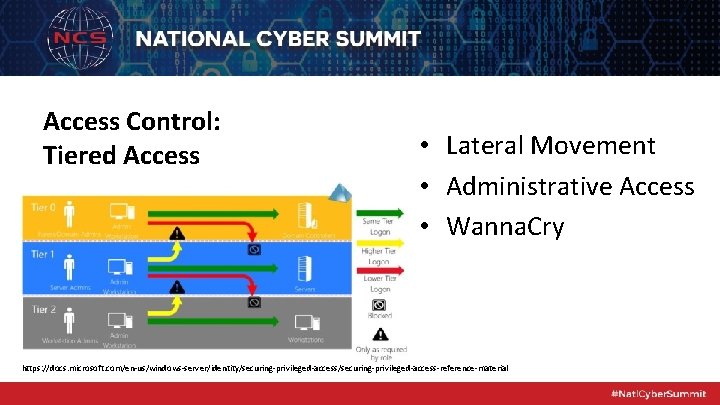
Access Control: Tiered Access • Lateral Movement • Administrative Access • Wanna. Cry https: //docs. microsoft. com/en-us/windows-server/identity/securing-privileged-access-reference-material

Choke Points • Trusted sources • Areas of known activity • Minimize surface areas for nonstandard things (i. e. front gate and not the walls) • Not a new concept

Choke Points

Trust Zones • More than network segmentation – We can have segmentation and still have a flat network • Must empower businesses – Too many hoops to jump through, at best users will be mad, worst case, they will find a way around
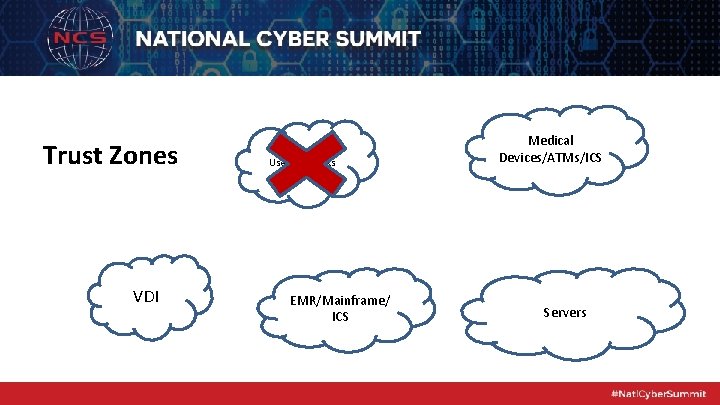
Trust Zones VDI User Networks EMR/Mainframe/ ICS Medical Devices/ATMs/ICS Servers

Detection Strategy • Identify the needles before building the haystack • Minimize attack surfaces • Focus on ‘all hands on deck’ alerts • Review alerts vs reports

Detection Strategy • Don’t try to think like an attacker • Stop trying to prevent the latest and greatest 0 day – just assume it is already there

Next Steps • Access Control – Minimize perimeter – Control changes – Tiered accounts for administration

Next Steps • Choke Points – – Bring the battle to you Know what normal looks like Tiered Accounts Reduce the noise

Next Steps • Trust Zones – Segment your network – Know what is supposed to talk to each other – This should be transparent to users – Keep it simple, but not flat

Next Steps • Detection Capabilities – Use guides (see references) – Know what normal is, be able to detect what isn’t – Reduce the noise
• References • • Don’t Think like an attacker – Mitre ATT&CK – https: //attack. mitre. org/wiki/Main_Page – Known IOCs - https: //github. com/Neo 23 x 0/sigma – Threat Hunter Playbook https: //github. com/Cyb 3 r. Ward 0 g/Threat. Hunter-Playbook Strategy: – http: //threatexpress. com/2018/01/threat-mitigation-strategies-observations-recommendations/ James Tubberville – http: //www. andrewalaniz. com/2017/12/10 -immutable-laws-assumed-breach/ - Andrew Alaniz – 10 Immutable Laws of Assumed Breach – https: //www. slideshare. net/Joe. Vest 1/using-ioc-to-design-and-control-threat-activities-during-a-red -team-engagement - Joe Vest – Using IOCs to control threats – https: //technet. microsoft. com/en-us/library/hh 278941. aspx - Microsoft - 10 Immutable Laws of Security Detection: – https: //blogs. technet. microsoft. com/jepayne/2015/11/26/tracking-lateral-movement-part-onespecial-groups-and-specific-service-accounts/ - Jessica Payne – Tracking Lateral Movement – http: //www. andrewalaniz. com/2017/12/assumed-breach-model-practical-approach-part-1/ Andrew Alaniz – Assumed Breach Model – http: //www. andrewalaniz. com/2016/10/windows-event-forwarding-collector-resources/ Resources for capturing Windows Events
- Slides: 24